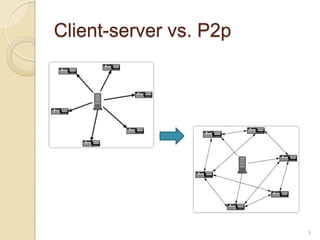
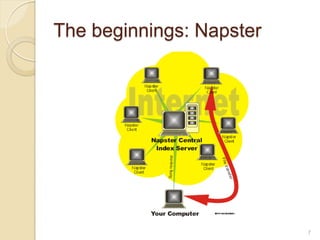
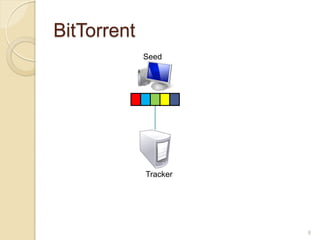
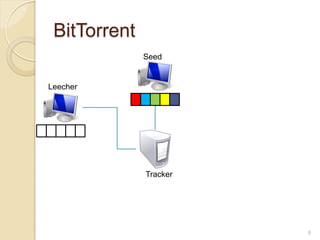
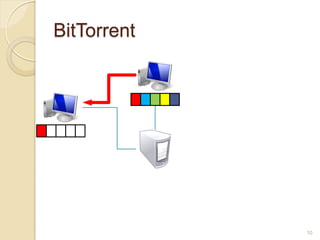
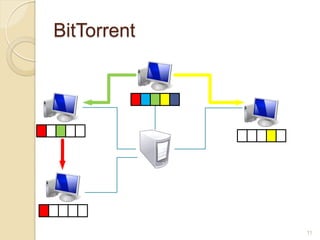
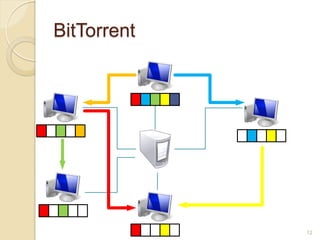
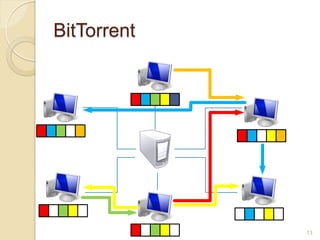
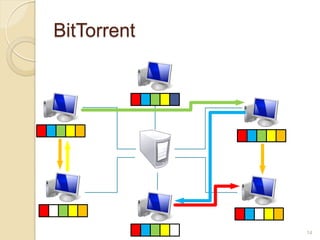
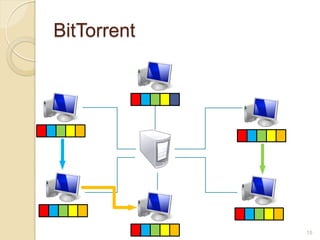
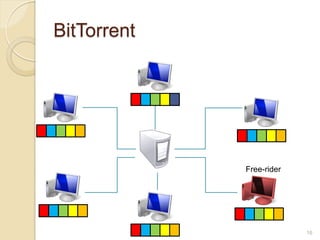
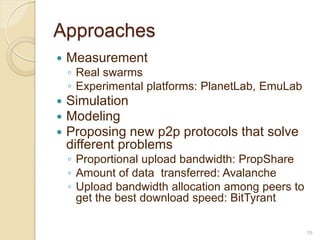
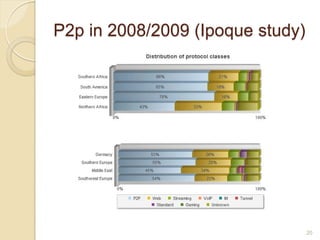
This document discusses the past, present, and future of peer-to-peer (P2P) networks. It describes how P2P networks emerged to help alleviate load on servers and make use of the interconnectivity between nodes. Popular early P2P file sharing applications like Napster, Gnutella, and BitTorrent are discussed. While P2P file sharing declined due to legal issues, P2P protocols now see growing use for media streaming, communication, and within data centers. The document predicts P2P will continue evolving with technologies like IPv6 and play an increasing role in areas like social networks and peer production.