This document presents a new method for finding the fuzzy critical path in a project network using type-2 discrete fuzzy numbers and type reduction. The key steps are:
1. Represent the time span of each activity as a type-2 discrete fuzzy number.
2. Use type reduction and the center of gravity to calculate the earliest start time, latest finish time, and total slack fuzzy time for each activity.
3. Identify the fuzzy critical path as the path(s) with a total slack time of 0 based on the center of gravity calculations.
An example application of the method on a sample network is provided to demonstrate the approach. The proposed method allows identification of the fuzzy critical path when activity
![International Journal of Research in Advent Technology, Vol.7, No.1, January 2019
E-ISSN: 2321-9637
Available online at www.ijrat.org
256
Type –Reduction Method on Fuzzy Critical Path
P.Balasowandari1
and Dr. V.Anusuya2
1
Research Scholar, PG and Research Department of Mathematics,
Seethalakshmi Ramaswami college, Tiruchirapalli-2
2
Associate Professor, PG and Research Department of Mathematics,
Seethalakshmi Ramaswami college, Tiruchirapalli-2
Email: balasowandari@gmail.com anusrctry@gmail.com
Abstract- In this paper, we propose a new method to find the fuzzy critical path in a acyclic project network
using type reduction method. Type-2 discrete fuzzy numbers and its complement are used to identify the fuzzy
critical path. An illustrative example is also included to demonstrate our proposed method.
Keywords: Fuzzy critical path, type-2 discrete fuzzy number, acyclic project network, centre of gravity.
1. INTRODUCTION [8],[10],[11]
Critical path method is a network-based
method that provides assistance in planning and
controlling complicated projects in real world
applications. The objective of the critical path
method(CPM) is to locate critical activities on the
critical path so that resources may be concentrated
on these activities in order to shorten the project
length time. CPM enables the decision maker adopt
a better strategy of optimizing the time and the
available resources to ensure the speedy
completion and the standard of the project.
This paper analyzes the critical path in a
general project network with fuzzy activity times.
Several type-reduction methods for type-2 fuzzy
sets have been proposed. Coupland and john[4]
proposed a type reduction method for type-2 fuzzy
sets. We propound centre of gravity under type
reduction method for fuzzy numbers to find a fuzzy
critical path. The time span of each activity in a
fuzzy project network is represented by type – 2
discrete fuzzy number.
The organization of the paper is as
follows: In section 2 some basic concepts are
discussed. section 3 gives some properties of total
slack fuzzy time. Section 4 gives the network
terminology. An algorithm to find the fuzzy critical
path is discussed in section 5.The proposed
algorithm is illustrated through a numerical
example in section 6.
2. BASIC CONCEPTS
2.1. Type-2 discrete fuzzy number [1],[2]
Let X be a non-empty finite set, which is referred as the universal set. A type-2 fuzzy set A
~
, is
characterized by a type-2 membership function IIXuxA
:),(~ ]1,0[, IXxwhere
),/),();,((
~
~ IJuXxuxuxAisthatIJuand xAx where 1),(0 ~ uxA
A
~
can also be expressed as IJ
x
uuP
ux
ux
A x
Ux
x
Xx Ju
A
x
/)(
),(
),(~ ~
, where denotes union
all admissible x and u. For, discrete universe of discourse is replaced by .
2.2.Complement of type-2 discrete fuzzy number
The complement of the type-2 fuzzy set houses a fuzzy membership function given in the following
formula:
Xx
Ju
x
x
u
uf
A
x
)1(
)(
~](https://image.slidesharecdn.com/paperid-71201925-191010093758/85/Paper-id-71201925-1-320.jpg)
![International Journal of Research in Advent Technology, Vol.7, No.1, January 2019
E-ISSN: 2321-9637
Available online at www.ijrat.org
257
2.3 Centroid measure [9]
If A
~
is a type-2 fuzzy set in the discrete case, the centroid of A
~
can be defined as follows:
R
j
jA
R
j
jAj
Rxxx
JJJ
A
x
xx
fff
C
R
RxRxx
1
1
11
~
)(
)(
)]()....().([..... 21
2211
Where
R
j j
Ju
x
x
u
uf
A
jx
j
1
)(
~
2.4 centre of gravity
The centre of gravity of a fuzzy set A
~
is represented as
R
i
iA
R
i
iAi
x
xx
Af
1
1
)(
)(
)
~
(
where
R
i
iiA xxA
1
)(
~
2.5. Notations:
tij= The activity between node i and j.
j
ESF =The earliest starting fuzzy time of node j.
i
LFF = The latest finishing fuzzy time of node i.
ijTSF = The total slack fuzzy time of tij.
pn= the nth
fuzzy path.
P = the set of all fuzzy paths in a project network
F(pn)= The total slack fuzzy time of path pn in a
project network.
3. PROPERTIES [5],[6],[7]
Property :3.1 (Forward pass calculation)
To calculate the earliest starting fuzzy time in
the project network, set the initial node to zero for
starting (ie) )0.0,0.0,0.0,0.0(1
ESF
,,},{max NjijTSFESFESF ijjij
i=number of preceding nodes.( j
ESF =The earliest
starting fuzzy time of node j).
Ranking value is utilized to identify the maximum
value.
Earliest finishing fuzzy time = Earliest starting
fuzzy time (+) Fuzzy activity time.
Property 3.2. (Backward pass calculation)
To calculate the latest finishing time in the project
network set ESFnLFFn
.
,,},)({min NiniSETLFFLFF ijjjj
j = number of succeeding nodes. Ranking value is
utilized to identify the minimum value.
Latest starting fuzzy time= Latest finishing Fuzzy
time (-) Fuzzy activity time.
Property 3.3.
For the activity tij, i<j
Total fuzzy slack:
))()(( ijijij
SFTESFLFFSFT (or)
,))()(( iijj
ESFSFTLFF ;1 nji
,, Nji
Property 3.4.
1
,
( )n ij
i j n
i j pk
F p SFT
, ,Ppk np denotes
the number of possible paths in a network from
source node to the destination node, k=1 to m.
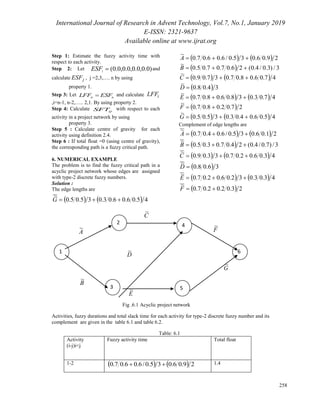
4. NETWORK TERMINOLOGY
A directed acyclic project network consisting
of six nodes and seven edges are considered. Each
edge in this network is assigned by type-2 discrete
fuzzy numbers. Then the set of all possible paths
are denoted by P. The fuzzy critical path is
identified from P.
5. Algorithm (for finding critical path) [3]](https://image.slidesharecdn.com/paperid-71201925-191010093758/85/Paper-id-71201925-2-320.jpg)
![International Journal of Research in Advent Technology, Vol.7, No.1, January 2019
E-ISSN: 2321-9637
Available online at www.ijrat.org
259
1-3 3/)3.0/4.0(26.07.07.05.0 0
2-4 47.06.08.07.037.09.0 1.4
3-4 34.08.0 2.0
3-5 47.03.038.06.08.07.0 0
4-6 27.02.08.07.0 1.4
5-6 45.06.04.03.035.05.0 0
Table: 6.2
Activity
(i-j)i<j
Fuzzy activity time Total float
1-2 21.06.035.0/6.04.07.0 1.55
1-3 3/)7.0/4.0(24.07.03.05.0 0
2-4 43.06.02.07.033.09.0 1.55
3-4 36.08.0 2.1
3-5 43.03.032.06.02.07.0 0
4-6 23.02.02.07.0 1.55
5-6 45.06.06.03.035.05.0 0
The path 1-3-5-6 is identified as a fuzzy critical path by type reduction method from the possible
paths P = {(1-2-4-6),(1-3-5-6),(1-3-4-6)}
5. CONCLUSION
In this paper, we have proposed type reduction
process to identify fuzzy critical path in a acyclic
project network using type-2 discrete fuzzy
numbers and its complement. The same fuzzy
critical path is obtained in both cases.
REFERENCES
[1] Anusuya V and.Sathya R, (2014) Fuzzy
shortest path by Type reduction International
Journal of Fuzzy Mathematical Archive,
vol. 4,pp.11-18.
[2] Anusuya V and Balasowandari P ,(Feb-
016)Fuzzy critical path with type-2 trapezoidal
fuzzynumbers, National conference on Graph
Theory, Fuzzy Graph Theory, and their
applications, Jamal Academic Research
Journal: An interdisciplinary Special Issue,
pp.171-176.
[3] Chanas S and Zielinski , (2001) Critical path
analysis in the network with fuzzy activity
times, Fuzzy Sets and Systems, vol.122,pp.
195-204.
[4] Coupland S and John R , (2008) “ A fast
geometric methods for defuzzification of type-
2 fuzzy sets,” IEEE Int. Conf. Fuzzy
systems ., Vol.16,no.4,pp.924-941..
[5] Elizabeth S. and Sujatha L, (2013),Fuzzy
critical path problem for project network,
International journal of pure and applied
mathematics , vol. 85,pp. 223-240.
[6] Liang G.S and Chenhan T, (2004) Fuzzy
critical path project network, Information and
Management sciences, Vol. 15,pp. 29-40.
[7] Nasution S.H, (1994)Fuzzy critical path method,
IEEE Trans. System Man Cybernetics, vol. 24,pp.
48-57.
[8] O’Brien J.J, 1993,CPM in Construction
Management, New York, Mc-Graw-Hill,.
[9] Sugeno,M,. 1977 “Fuzzy measures and fuzzy
integrals-a survey”, In Gupta, saridis and Gaines,
,pp.89-102.
[10]Zadeh L.A., (1965) Fuzzy sets, Information
and Control, vol.8, ,pp.138-353.
[11]Zadeh L.A., (1975), (1976)The concepts of a
linguistic variable and its application to
approximate reasoning part 1, 2, 3,
Information Sciences, vol.8, 199-249;vol. 9,pp.
43-58.](https://image.slidesharecdn.com/paperid-71201925-191010093758/85/Paper-id-71201925-4-320.jpg)