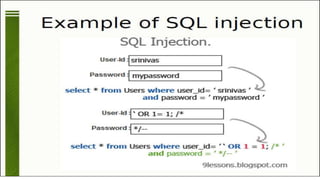
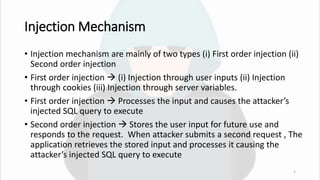
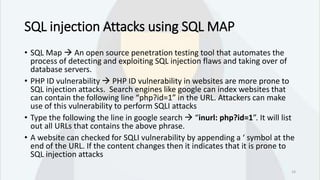
SQL injection is a critical web application vulnerability that allows attackers to execute arbitrary SQL commands through non-validated user inputs, potentially compromising sensitive data like usernames and passwords. The document covers the history of SQL injection attacks, including notable incidents involving companies like Starbucks and Sony, and discusses various types of SQL injection and their detection and prevention methods. Tools like SQLMap are mentioned for penetration testing, highlighting the importance of sanitizing inputs and implementing strong security measures.