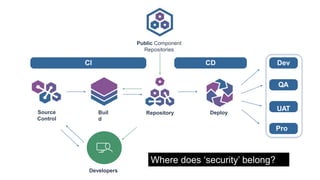
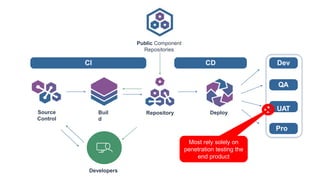
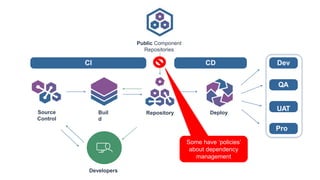
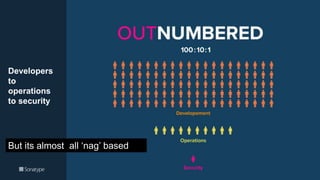
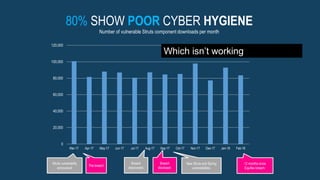
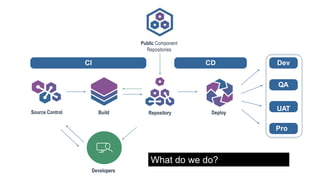
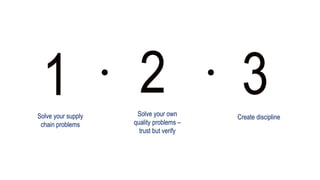
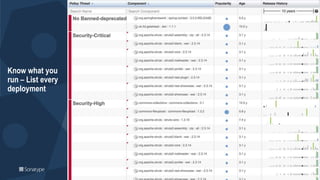
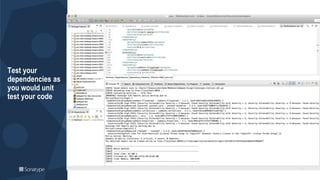
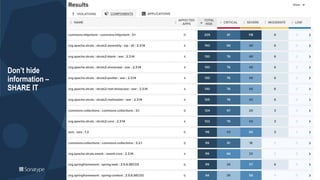
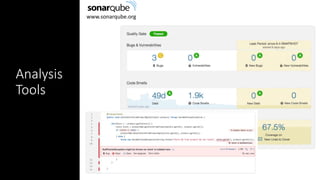
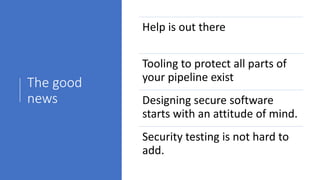
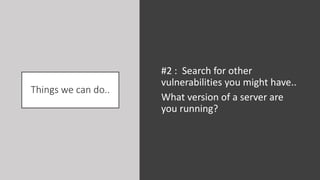
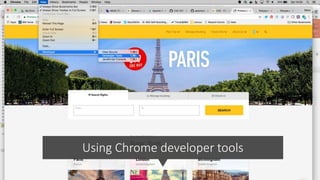
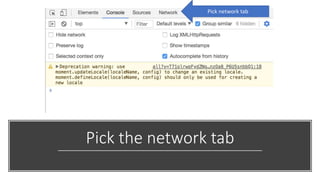
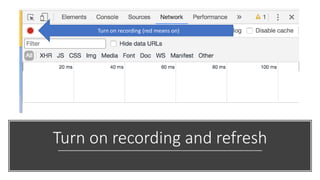
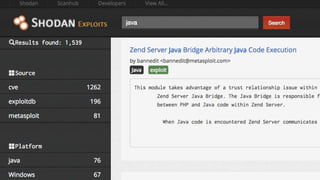
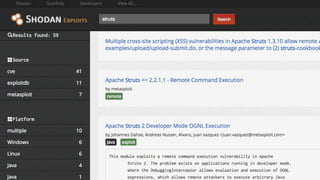
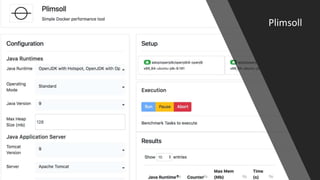
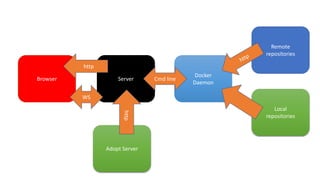
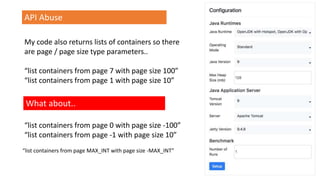
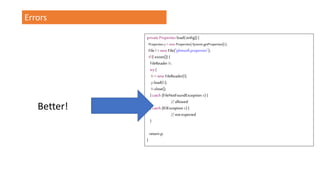
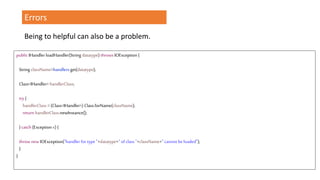
The document outlines a workshop focused on Java application security, discussing the economic impact of cybercrime and common vulnerabilities. Key topics include the tactics used by attackers, the importance of secure application design, and a taxonomy of software security errors. It emphasizes the need for developers to validate input, understand vulnerabilities, and improve development processes to reduce the risk of exploitation.




































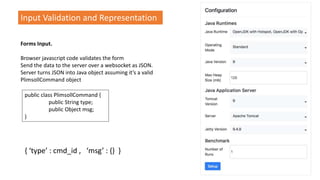
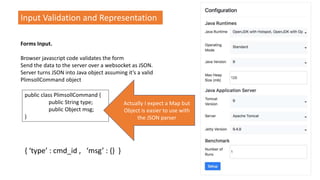
![Input Validation and Representation
Forms Input.
Browser javascript code validates the form
Send the data to the server over a websocket as JSON.
Server turns JSON into Java object assuming it’s a valid
PlimsollCommand object
public class PlimsollCommand {
public String type;
public Object msg;
}
What would happen if the
JSON data was actually a list?
{ ‘type’ : cmd_id , ‘msg’ : [ ‘a’ , ‘bad’ , ‘thing’ ] }](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-74-320.jpg)

![Input Validation and Representation
public classDockerCommandLineDriver{
privatestaticfinalStringDEFAULT_EXEC ="/usr/local/bin/docker";
privateStringdocker;
privatebooleanerror;
privateFileoutputFile;
privateListresults=newLinkedList();
staticenumCMD{
active,images,containers
};
privatestaticfinalString[]cmds =newString[]{ "ps-a", "images","containerls -a"};
public DockerCommandLineDriver(){
this(DEFAULT_EXEC);
}
public DockerCommandLineDriver(Stringdriver){
docker= driver;
outputFile= newFile("/tmp/docker.out");
}](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-78-320.jpg)
![Input Validation and Representation
public classDockerCommandLineDriver{
privatestaticfinalStringDEFAULT_EXEC ="/usr/local/bin/docker";
privateStringdocker;
privatebooleanerror;
privateFileoutputFile;
privateListresults=newLinkedList();
staticenumCMD{
active,images,containers
};
privatestaticfinalString[]cmds =newString[]{ "ps-a", "images","containerls -a"};
public DockerCommandLineDriver(){
this(DEFAULT_EXEC);
}
public DockerCommandLineDriver(Stringdriver){
docker= driver;
outputFile= newFile("/tmp/docker.out");
}
DockerCommandLineDrivercld = newDockerCommandLineDriver();
…
Listl= cld.run(CMD.active);
if(cld.hasError()==false){
System.out.println(l);
}](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-79-320.jpg)
![Input Validation and Representation
DockerCommandLineDrivercld = newDockerCommandLineDriver();
…
Listl= cld.run(CMD.active);
if(cld.hasError()==false){
System.out.println(l);
}
public Listrun(CMDcmd) {
Stringcmdline =cmds[cmd.ordinal()];
cmdline =docker +""+cmdline;
String[]parts=cmdline.split(" ");
ProcessBuilder pb=new ProcessBuilder(parts);
pb.redirectErrorStream(true);
pb.redirectOutput(ProcessBuilder.Redirect.to(outputFile));
try{
Process p=pb.start();
intresult =p.waitFor();
error=result !=0;
} catch (IOException | InterruptedException e) {
error=true;
}
return saveResults();
}](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-80-320.jpg)
![What’s wrong with this code?
public classDockerCommandLineDriver{
privatestaticfinalStringDEFAULT_EXEC ="/usr/local/bin/docker";
privateStringdocker;
privatebooleanerror;
privateFileoutputFile;
privateListresults=newLinkedList();
staticenumCMD{
active,images,containers
};
privatestaticfinalString[]cmds =newString[]{ "ps-a", "images","containerls -a"};
public DockerCommandLineDriver(){
this(DEFAULT_EXEC);
}
public DockerCommandLineDriver(Stringdriver){
docker= driver;
outputFile= newFile("/tmp/docker.out");
}
Input Validation and Representation](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-81-320.jpg)
![This field is never validated.
• Does it really point to a docker executable?
• What would happen if it was set to some
• other executable?
• Could simply run a version check on it!
public classDockerCommandLineDriver{
privatestaticfinalStringDEFAULT_EXEC ="/usr/local/bin/docker";
privateStringdocker;
privatebooleanerror;
privateFileoutputFile;
privateListresults=newLinkedList();
staticenumCMD{
active,images,containers
};
privatestaticfinalString[]cmds =newString[]{ "ps-a", "images","containerls -a"};
public DockerCommandLineDriver(){
this(DEFAULT_EXEC);
}
public DockerCommandLineDriver(Stringdriver){
docker= driver;
outputFile= newFile("/tmp/docker.out");
}
“docker –version”
Input Validation and Representation](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-82-320.jpg)
![Even if the field was validated
during construction it can still be
changed afterwards.
Relying on constructor validation
only is also poor practise.
public classDockerCommandLineDriver{
privatestaticfinalStringDEFAULT_EXEC ="/usr/local/bin/docker";
privateStringdocker;
privatebooleanerror;
privateFileoutputFile;
privateListresults=newLinkedList();
staticenumCMD{
active,images,containers
};
privatestaticfinalString[]cmds =newString[]{ "ps-a", "images","containerls -a"};
public DockerCommandLineDriver(){
this(DEFAULT_EXEC);
}
public DockerCommandLineDriver(Stringdriver){
docker= driver;
outputFile= newFile("/tmp/docker.out");
}
(Re)validate just before usage
Input Validation and Representation](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-83-320.jpg)
![What about this field?
Set to “/tmp/docker.out” ?
public classDockerCommandLineDriver{
privatestaticfinalStringDEFAULT_EXEC ="/usr/local/bin/docker";
privateStringdocker;
privatebooleanerror;
privateFileoutputFile;
privateListresults=newLinkedList();
staticenumCMD{
active,images,containers
};
privatestaticfinalString[]cmds =newString[]{ "ps-a", "images","containerls -a"};
public DockerCommandLineDriver(){
this(DEFAULT_EXEC);
}
public DockerCommandLineDriver(Stringdriver){
docker= driver;
outputFile= newFile("/tmp/docker.out");
}
Input Validation and Representation](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-84-320.jpg)
![With serialisation vulnerabilities I
may be able to get the code to
overwrite a critical file somewhere
else.
If I modify both the exe and file
fields I can control what data gets
written to your system
Remember constructors are not
called during deserialization. The
data is simply inserted.
public classDockerCommandLineDriver{
privatestaticfinalStringDEFAULT_EXEC ="/usr/local/bin/docker";
privateStringdocker;
privatebooleanerror;
privateFileoutputFile;
privateListresults=newLinkedList();
staticenumCMD{
active,images,containers
};
privatestaticfinalString[]cmds =newString[]{ "ps-a", "images","containerls -a"};
public DockerCommandLineDriver(){
this(DEFAULT_EXEC);
}
public DockerCommandLineDriver(Stringdriver){
docker= driver;
outputFile= newFile("/tmp/docker.out");
}
Input Validation and Representation](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-85-320.jpg)



















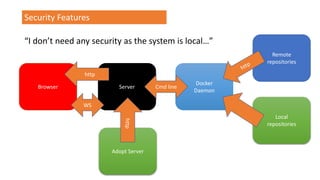
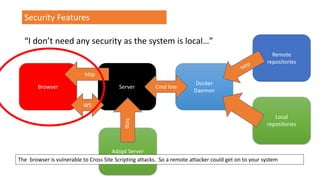
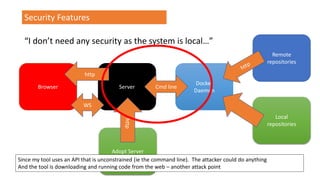
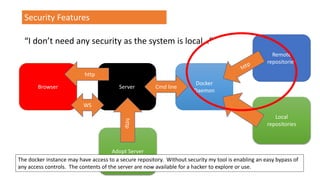

![Security Features
Trusting the end user not to tamper with the data
Cookie[] cookies =
request.getCookies();
for (int i =0; i< cookies.length; i++) {
Cookie c = cookies[i];
if (c.getName().equals("role")) {
userRole = c.getValue();
}
}](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-119-320.jpg)
![Security Features
Trusting the end user not to tamper with the data
Cookie[] cookies =
request.getCookies();
for (int i =0; i< cookies.length; i++) {
Cookie c = cookies[i];
if (c.getName().equals("role")) {
userRole = c.getValue();
}
}
Does encryption solve this?](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-120-320.jpg)
![Security Features
Trusting the end user not to tamper with the data
Cookie[] cookies =
request.getCookies();
for (int i =0; i< cookies.length; i++) {
Cookie c = cookies[i];
if (c.getName().equals("role")) {
userRole = c.getValue();
}
}
No!
XSS attacks often replace
encrypted cookies etc with
ones from another session
that has the required
privileges.
You must have additional
privilege management
processes in play](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-121-320.jpg)


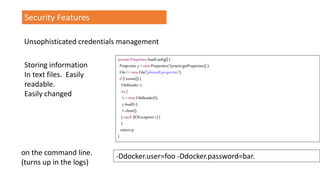
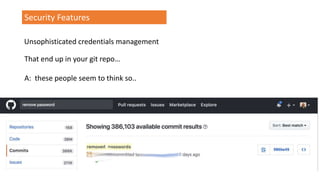
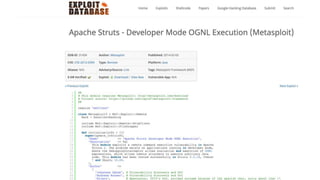
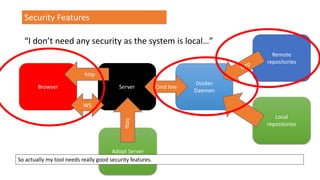
![TrustManager[] trustAllCerts = new TrustManager[]{
new X509TrustManager() {
public X509Certificate[] getAcceptedIssuers() {
return null;
}
public void checkClientTrusted(
X509Certificate[] certs, String authType) {
}
public void checkServerTrusted(
X509Certificate[] certs, String authType) {
}
public boolean isClientTrusted( X509Certificate[] cert) {
return true;
}
public boolean isServerTrusted( X509Certificate[] cert) {
return true;
}
}}
Security Features
Deliberate weakening of security
protocols](https://image.slidesharecdn.com/devoxxworkshopfinal-180509060123/85/Java-application-security-the-hard-way-a-workshop-for-the-serious-developer-127-320.jpg)