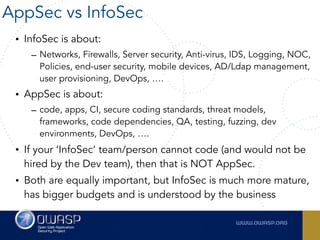
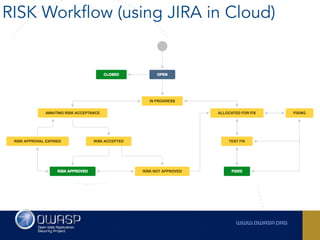
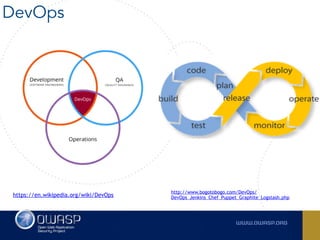
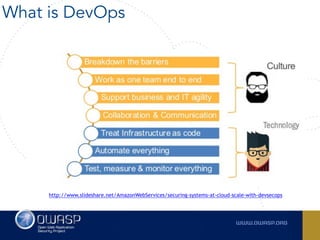
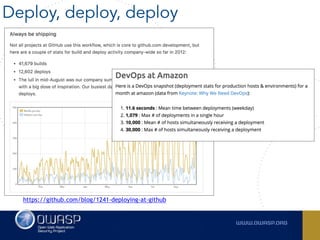
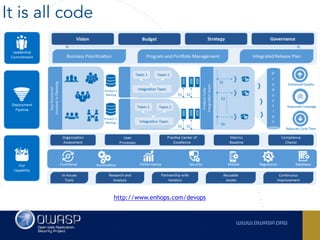
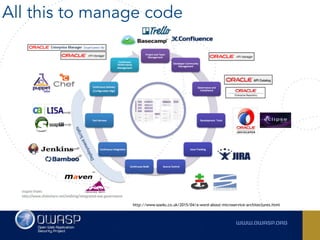
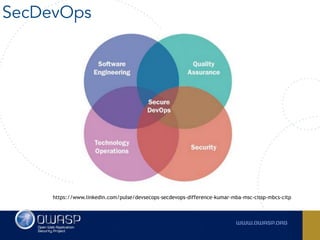
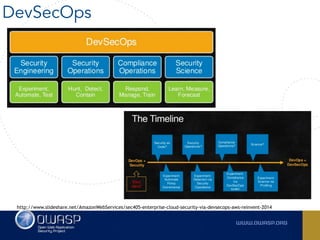
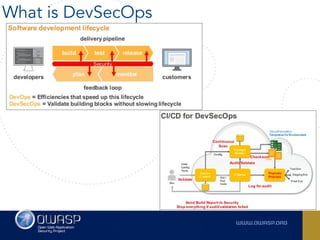
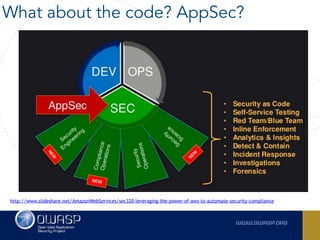
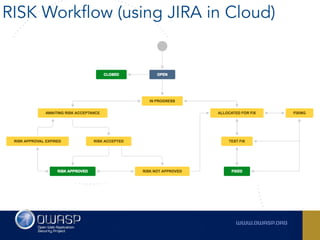
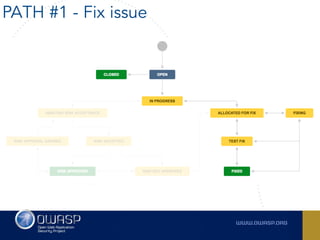
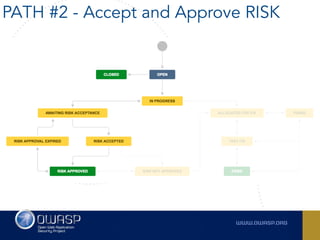
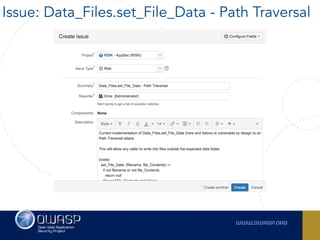
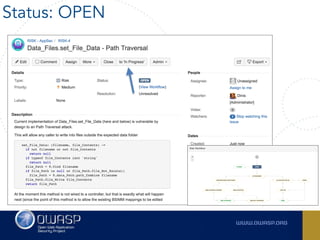
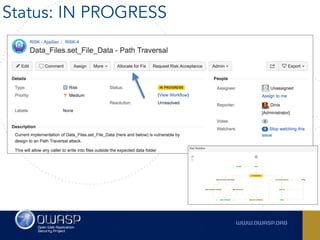
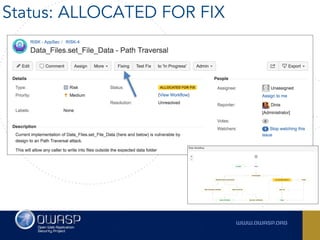
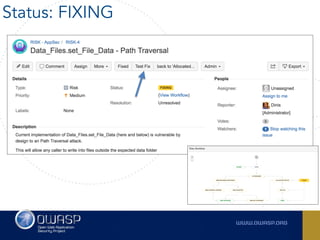
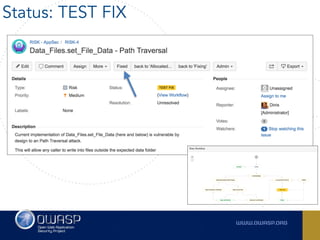
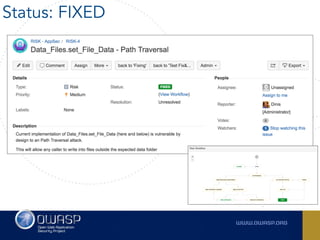
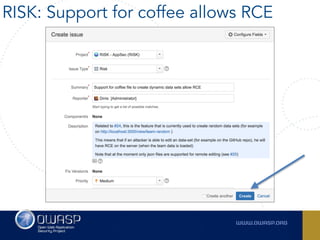
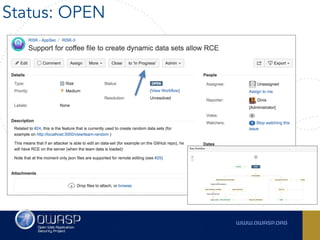
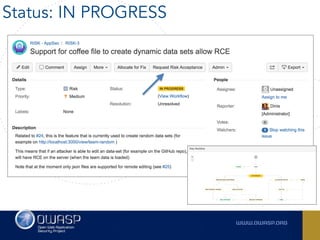
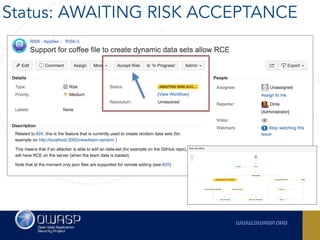
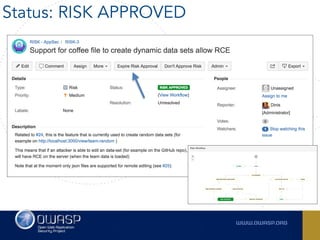
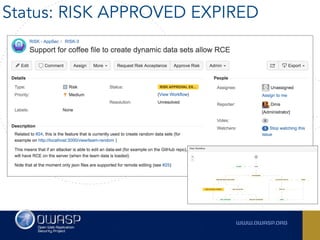
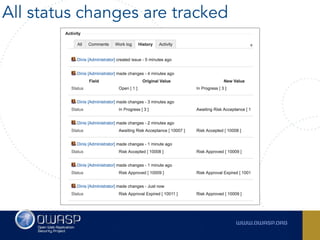
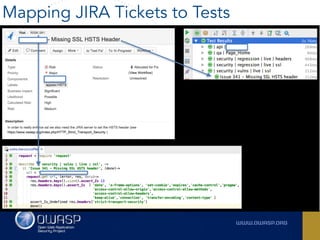
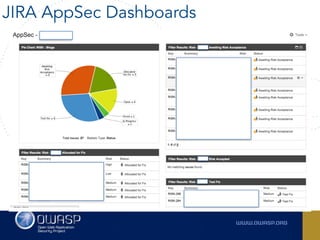
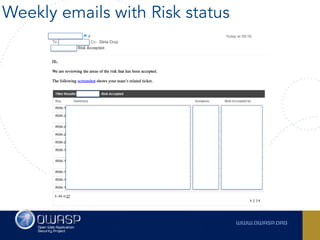
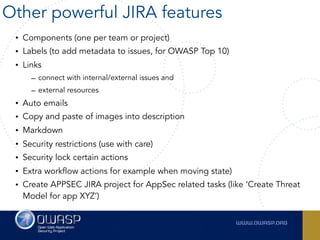
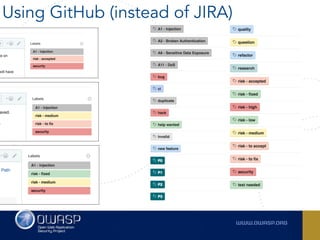
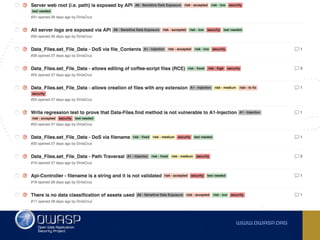
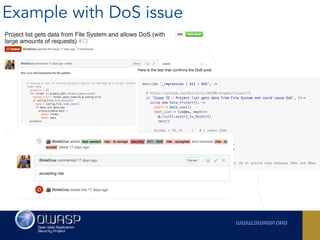
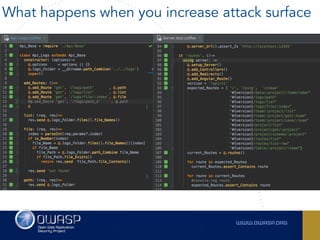
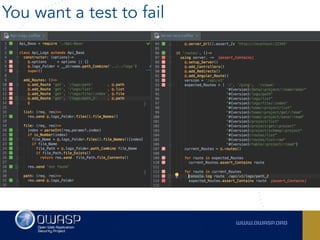
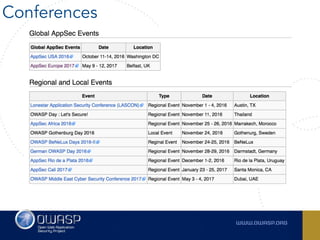
The document outlines the SecDevOps Risk Workflow, emphasizing the integration of application security (appsec) within development processes to manage risks effectively. It stresses the importance of aligning security practices with business goals, creating workflows using tools like Jira, and promoting a culture of security within development teams. Additionally, it advocates for direct involvement of developers in security measures, leveraging threat modeling, and ensuring timely issue management through clear paths of risk acceptance and resolution.