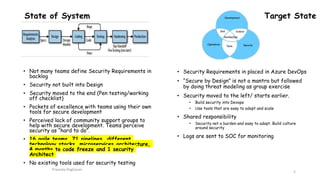
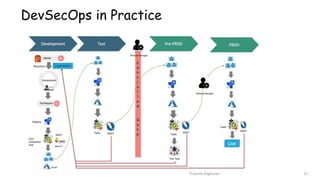
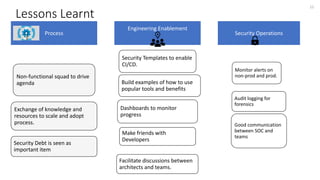
This document discusses implementing DevSecOps at scale. It begins with an introduction and agenda. It then discusses the motivations for DevSecOps, including moving security left and making it a shared responsibility. Next, it describes the current state as lacking security requirements, testing, and tools. The target state involves integrating security earlier using tools like SonarQube and ZAP. It outlines DevSecOps practices like threat modeling, security testing in pipelines, and monitoring. Challenges include aligning teams, reducing wait times, and configuring tools across projects. Lessons learned center around process engineering, knowledge sharing, and establishing security operations.