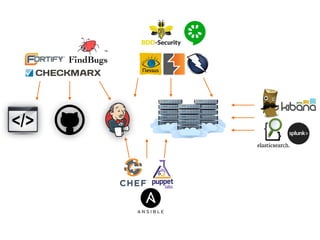
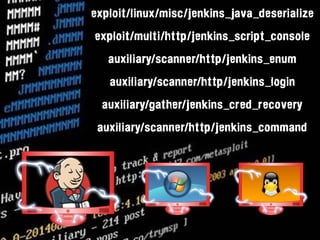
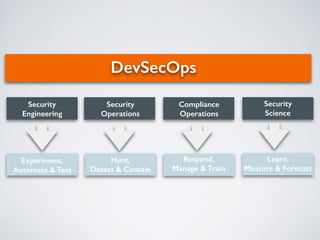
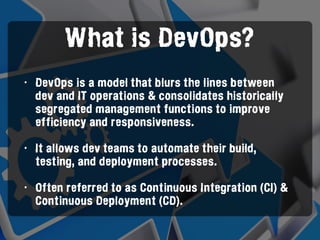
The document discusses the concept of DevSecOps, highlighting its role in merging development and security to improve operational efficiency and responsiveness through automation and collaboration. It details various authentication, input validation, session management, and access control verification requirements aligned with the ASVS 2014 web application standard. Additionally, it emphasizes that while tools and automation are vital, fostering a culture of security is essential for successful DevSecOps implementation.












![Recipe
mysql_service 'default' do
version '5.7'
bind_address '0.0.0.0'
port '3306'
data_dir '/data'
initial_root_password 'Ch4ng3me'
action [:create, :start]
end](https://image.slidesharecdn.com/devsecops-160704215126/85/SecDevOps-The-Operationalisation-of-Security-14-320.jpg)
![class mysql (
root_password => 'Ch4ng3me',
port => '3306',
) {
package { 'mysql-server':
ensure => present,
}
service { 'mysql':
ensure => running,
}
[...]
}
Recipe](https://image.slidesharecdn.com/devsecops-160704215126/85/SecDevOps-The-Operationalisation-of-Security-15-320.jpg)