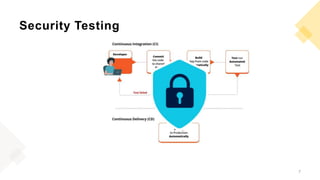
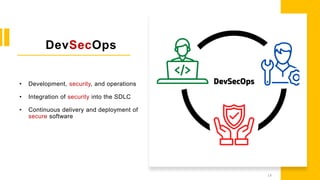
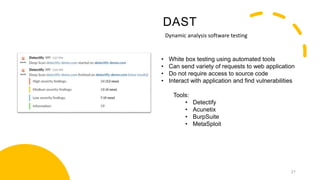
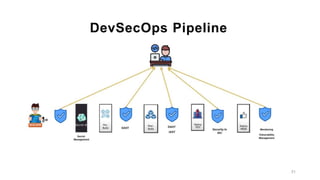
The document discusses the transition from DevOps to DevSecOps, emphasizing the importance of integrating security throughout the software development lifecycle. It highlights challenges in DevOps, such as inadequate security practices and delayed delivery, while outlining a DevSecOps methodology that includes tools and practices for enhanced security. Key benefits of adopting DevSecOps include faster delivery, improved security posture, and compliance.