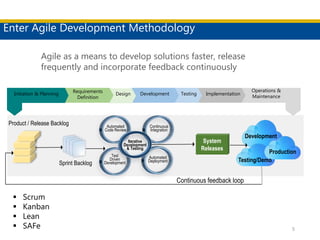
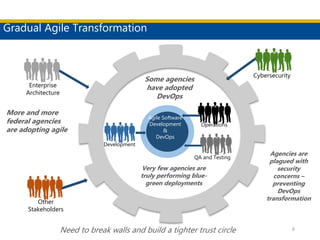
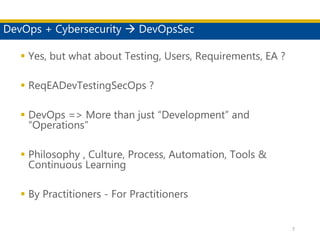
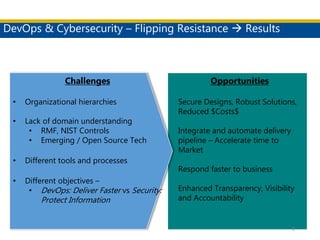
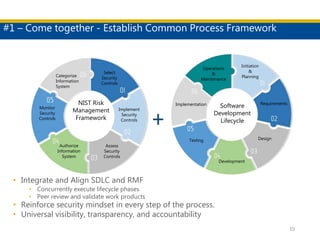
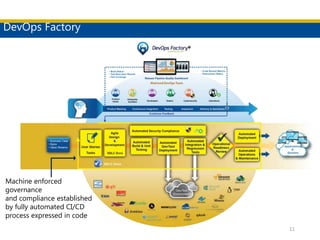
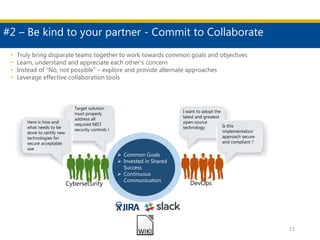
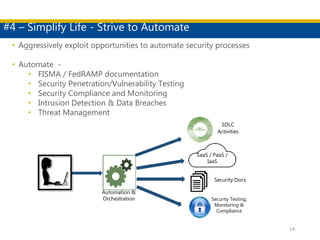
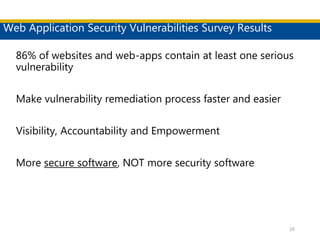
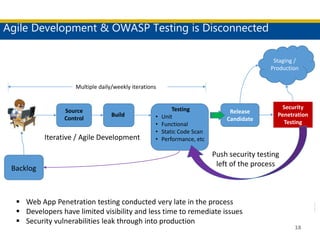
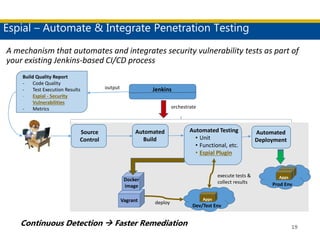
This document discusses succeeding in the marriage of cybersecurity and DevOps. It outlines five keys to a successful marriage: 1) establish a common process framework; 2) commit to collaboration; 3) design for security from inception; 4) strive to automate security processes; and 5) continuously learn and innovate. The document provides examples of how tools like Espial can help automate and integrate security testing into the development pipeline to enable continuous detection and faster remediation of vulnerabilities.