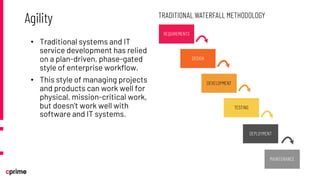
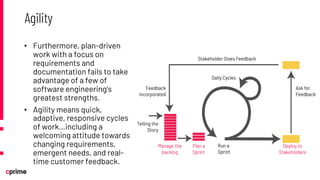
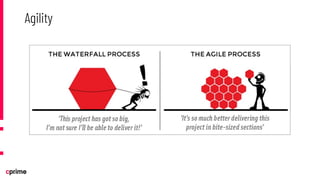
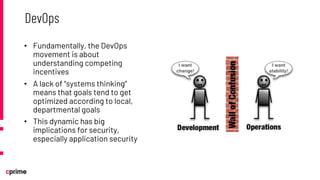
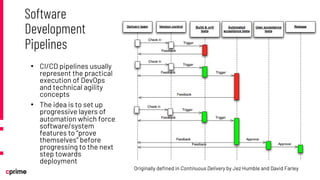
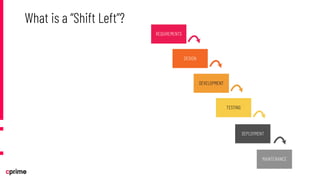
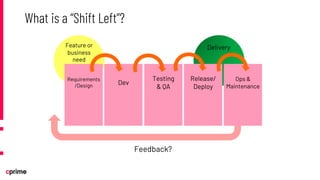
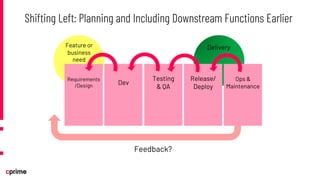
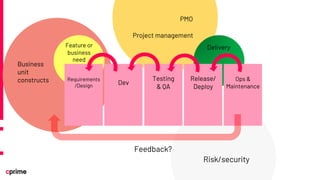
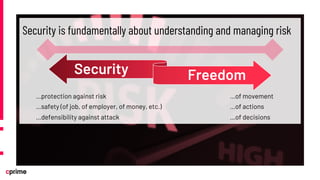
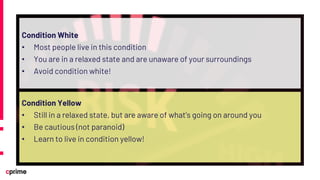
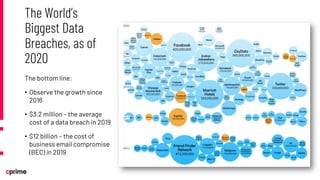
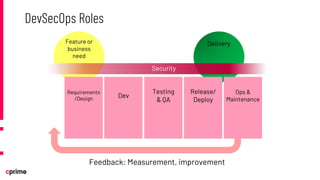
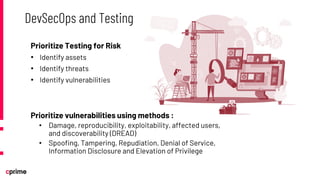
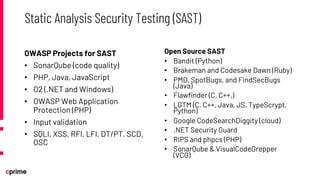
The document discusses the principles and practices of DevSecOps. It begins with an agenda that covers DevSecOps prerequisites, foundations, roles and responsibilities, and practical tips. It discusses concepts like shifting security left, continuous integration/delivery pipelines, and the importance of collaboration across roles. It provides overviews of risk management, static and dynamic testing, feature toggles, and recommends DevSecOps training and tools from Cprime. The presentation aims to help organizations adopt DevSecOps practices to improve security and deployment processes.