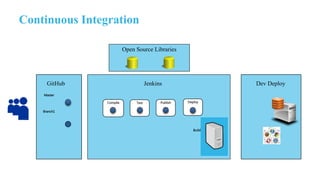
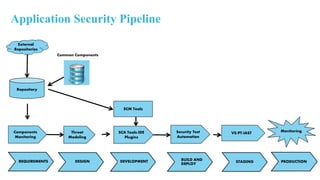
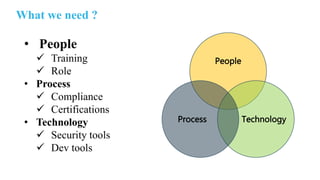
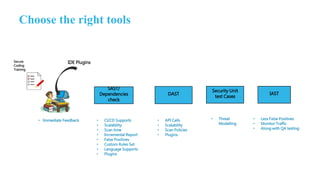
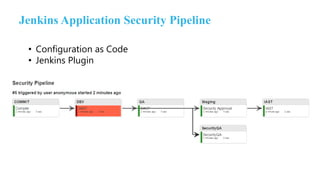
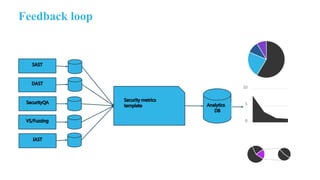
The document outlines the implementation of an application security pipeline in Jenkins, emphasizing continuous integration and various security approaches. It discusses the importance of training, process compliance, and technology in developing secure software, referencing frameworks like BSIMM and OWASP SAMM. It highlights the need for security tools, secure coding practices, and integration of feedback mechanisms in the CI/CD process.