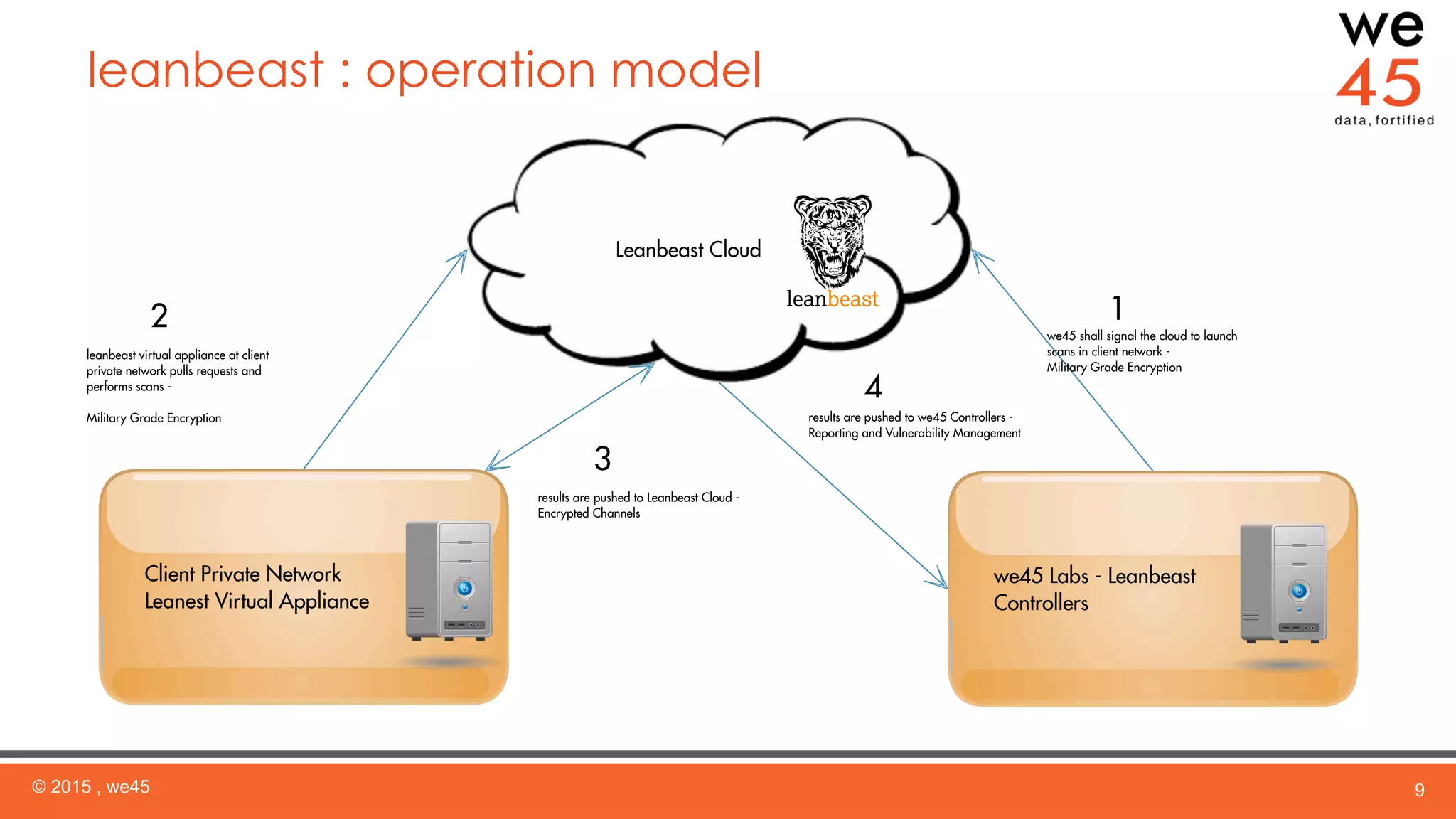
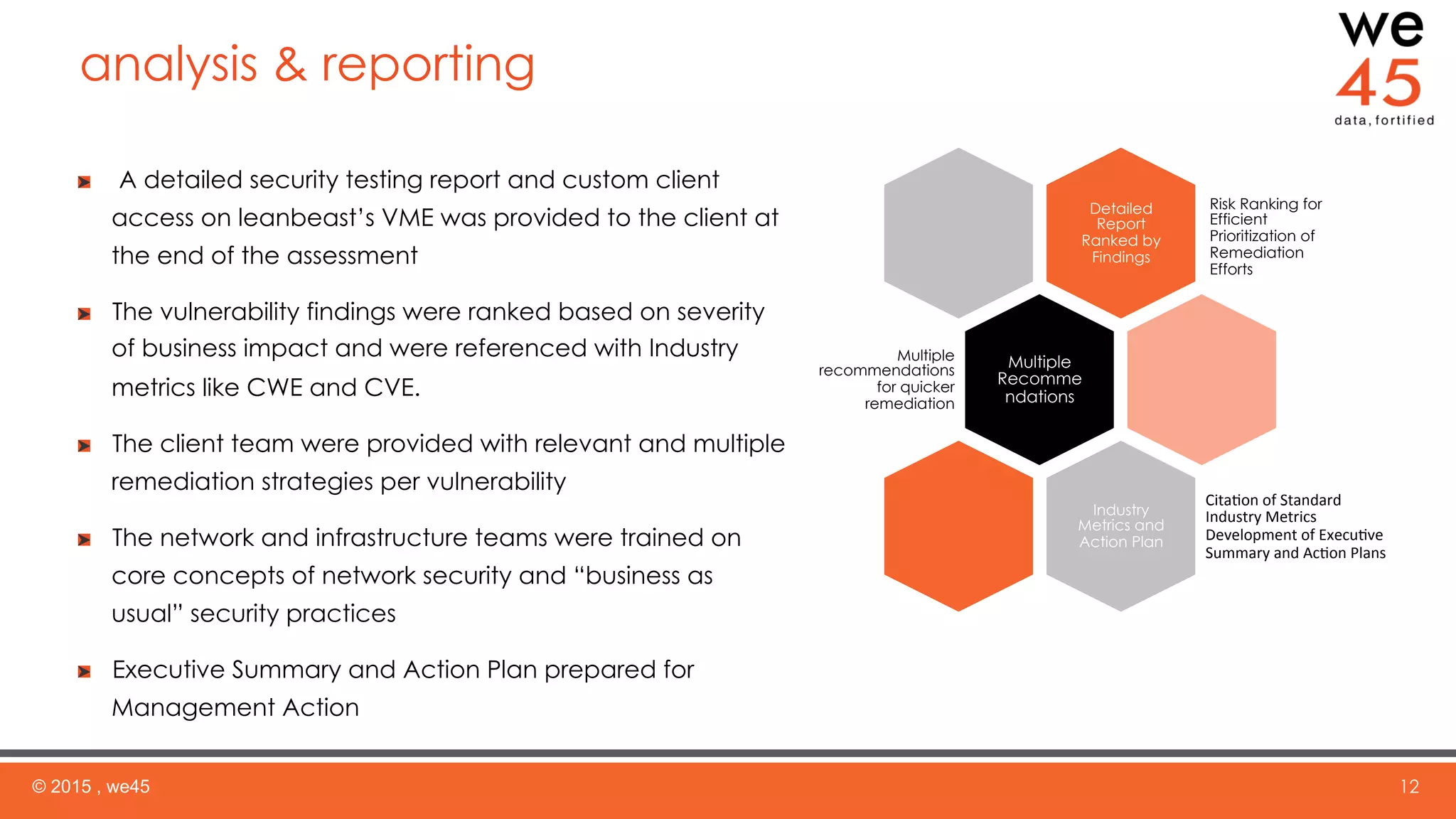
The document summarizes a security assessment conducted by we45 for a cloud-based email encryption company. we45 used their "Leanbeast" appliance to conduct reconnaissance, vulnerability scanning, and penetration testing of the client's AWS infrastructure. Several major vulnerabilities were found, including remote code execution on an ElasticSearch server and authentication flaws exposing customer data. we45 provided a detailed report of findings prioritized by risk level and recommended remediation strategies to improve the client's security posture.