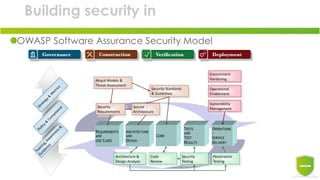
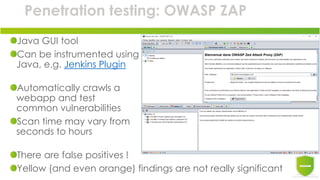
This document discusses including security in DevOps initiatives. It recommends integrating security tools and practices into the software development lifecycle (SDLC) to build security in from the start. This includes running automated vulnerability scanning tools like ZAP and sqlmap in CI/CD pipelines. It also recommends code reviews, security testing, environment hardening, and keeping dependencies up-to-date. The goal is to shift security left and automate security practices to continuously test and deploy more secure software.