Embed presentation
Download as PDF, PPTX



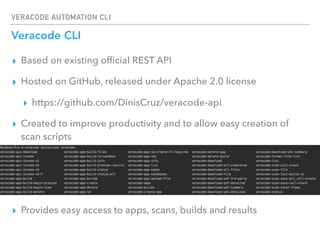

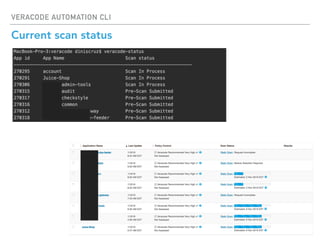
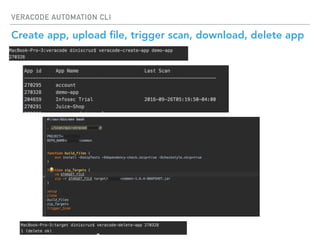


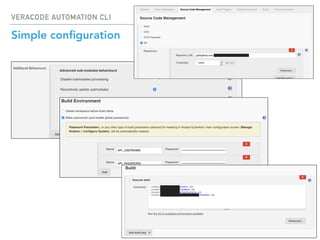
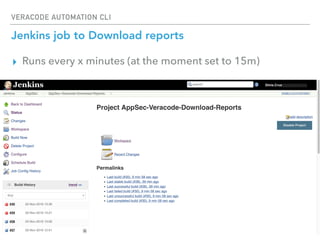

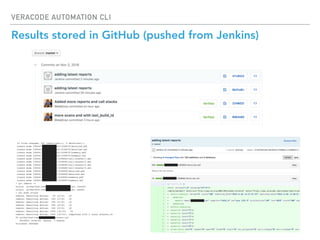




The Veracode Automation CLI is designed to automate application security scans and integrate them into CI/CD processes using Jenkins. It offers features such as listing applications, managing builds, and triggering scans, all while leveraging existing REST APIs. The CLI is hosted on GitHub and aims to improve productivity by simplifying scan script creation and results management.















