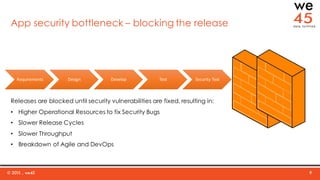
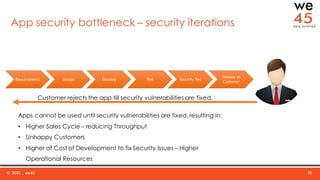
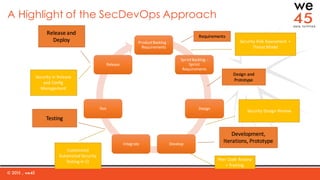
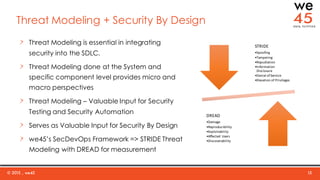
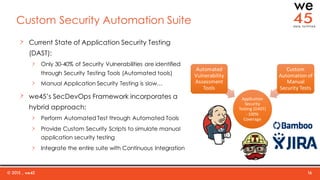
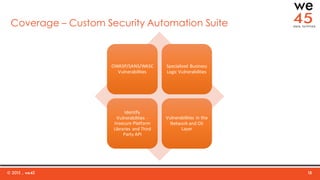
The document discusses the importance of integrating security into DevOps practices through the we45 SecDevOps framework to enhance application delivery efficiency. It highlights current challenges faced due to security vulnerabilities, which create bottlenecks in the software development lifecycle, impeding throughput and customer satisfaction. The framework employs a combination of threat modeling, automated security testing, and continuous integration to ensure security is effectively incorporated throughout the development process.