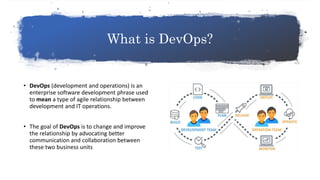
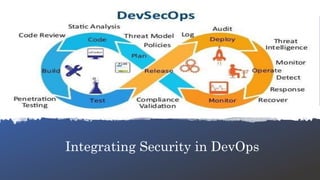
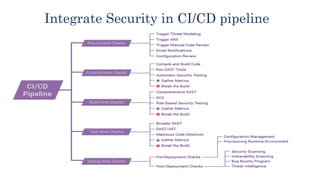
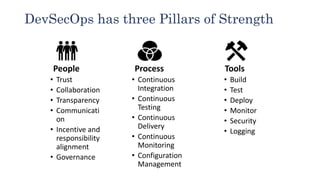
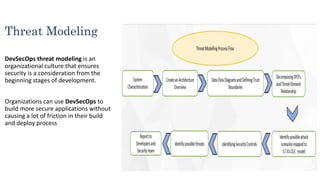
The document provides an overview of DevSecOps, which integrates security into the DevOps process, promoting a culture of shared security responsibility among all team members. It emphasizes the need for early security integration in software development and outlines best practices and tools for maintaining security throughout the software lifecycle. Additionally, it discusses the importance of security champions and various testing methodologies like SAST and DAST to improve application security.