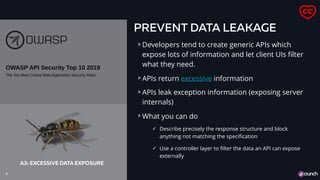
The document discusses the OWASP API Security Top 10 project which aims to raise awareness of common API vulnerabilities. It highlights some frequent issues like input validation problems, insecure configurations, and data/exception leakage. The document also demonstrates examples of these vulnerabilities using a vulnerable demo API called Pixi.








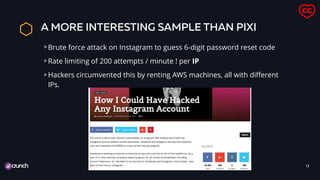

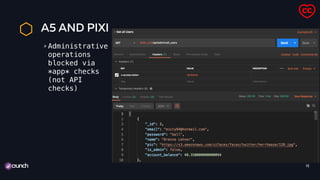
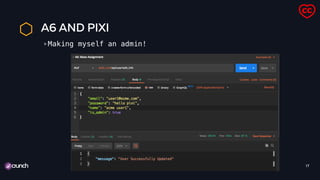





![A10 AND PIXI
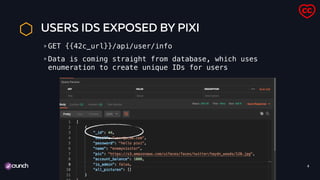
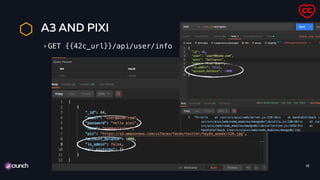
Leaking information in logs
26
pixiapp | token
"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VyIjp7Il9pZCI6MzMsImVtYWlsIjoiaGFja2VyQGdldG1l
mluIiwicGFzc3dvcmQiOiJoZWxsb3BpeGkiLCJuYW1lIjoiaW52b2x2ZWRwbHVzIiwicGljIjoiaHR0cHM6Ly9zMy5
bWF6b25hd3MuY29tL3VpZmFjZXMvZmFjZXMvdHdpdHRlci90aGlhZ292ZXJuZXR0aS8xMjguanBnIiwiaXNfYWRtaW
iOmZhbHNlLCJhY2NvdW50X2JhbGFuY2UiOjUwLCJhbGxfcGljdHVyZXMiOltdfSwiaWF0IjoxNTY4MjE2OTc3fQ.Ld
9xT1Q2JqbrnPBe395kFrny3vgg9BKxRQ-OTa6f6U"
pixiapp | owaspbrokenwebapps
pixiapp | my user {"user":{"_id":
33,"email":"hacker@getme.in","password":"hellopixi","name":"involvedplus","pic":"https://
s3.amazonaws.com/uifaces/faces/twitter/thiagovernetti/
128.jpg","is_admin":false,"account_balance":50,"all_pictures":[]},"iat":1568216977}
pixiapp | user id 33](https://image.slidesharecdn.com/owasptop10bytheexample-190927210812/85/OWASP-API-Security-Top-10-Examples-26-320.jpg)