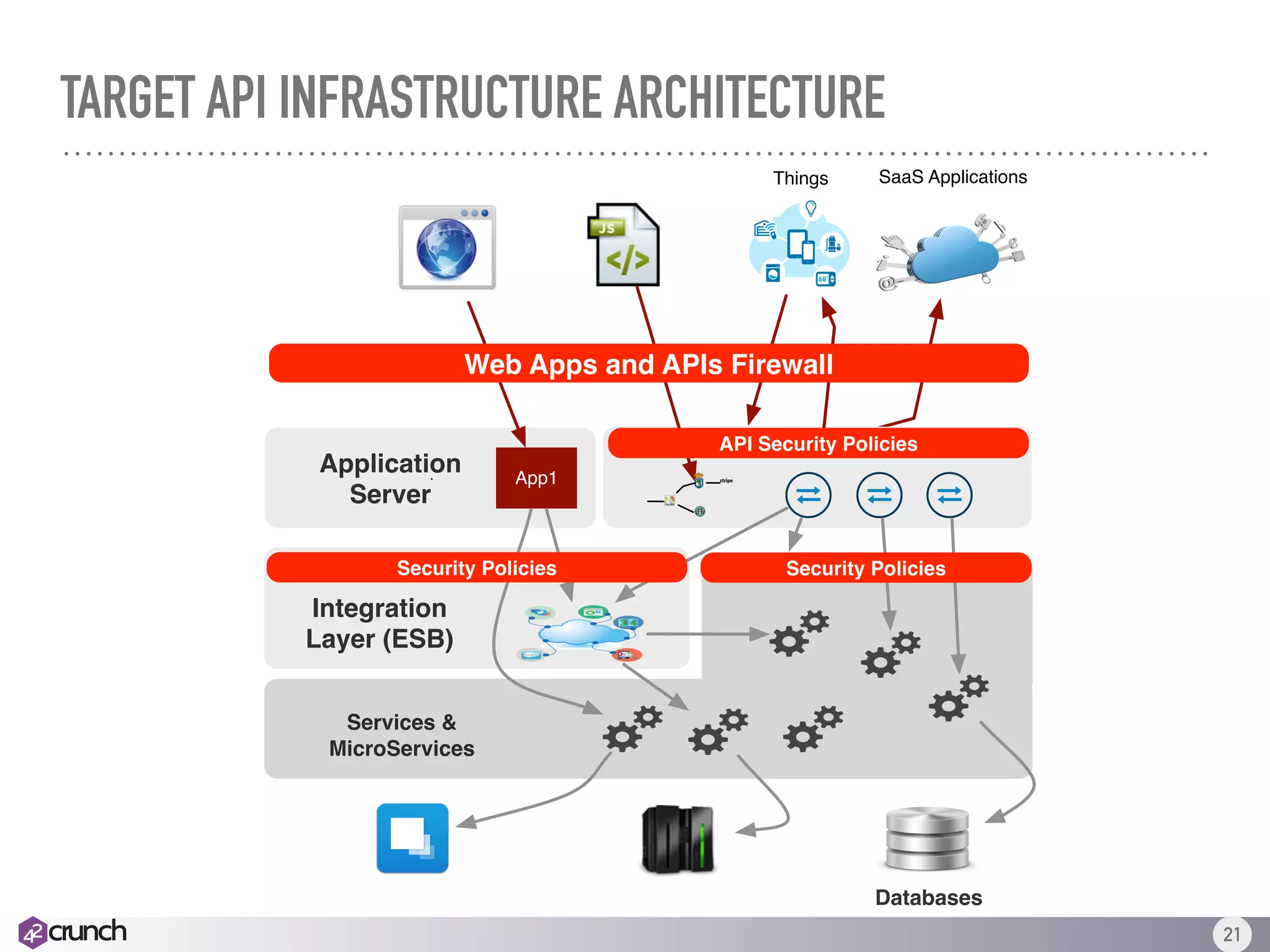
The document outlines the essential aspects of API security, highlighting the need for a layered approach that encompasses multiple security goals such as integrity, confidentiality, and availability. It emphasizes the shift from traditional security perimeters to decentralized API-centric infrastructures and the importance of integrating security measures throughout the development lifecycle (DevSecOps). Recommendations for comprehensive API security policies, including robust authentication and authorization mechanisms, are provided to address emerging threats and facilitate continuous innovation.