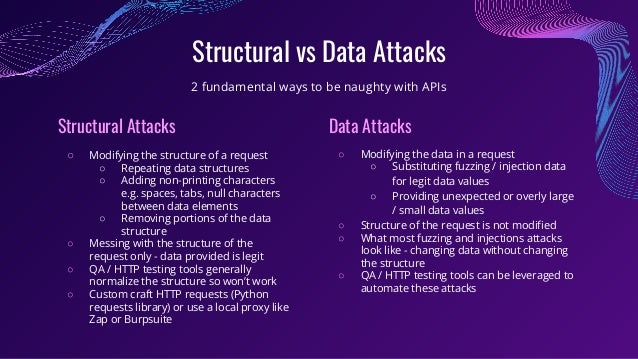
The document explores the vulnerabilities and security concerns associated with APIs, highlighting that APIs are increasingly targeted by attackers due to the rich data they handle. It defines categories of API security threats, presents tactics for both attackers and defenders, and emphasizes the importance of robust testing, monitoring, and posture management to mitigate risks. Key takeaways underline the necessity for organizations to address gaps in their API security frameworks and ensure proactive measures against common attack types.