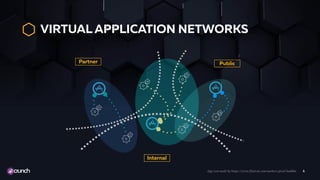
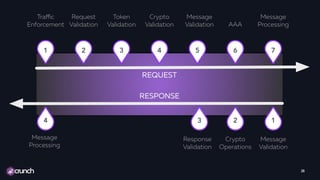
The document outlines essential guidelines for API security, emphasizing the need for comprehensive inventory and governance of APIs to protect against threats. It details risk-based security measures, advocating for automation and early integration of security policies throughout the API lifecycle. The paper also addresses critical aspects such as authentication, cryptography, and data validation to ensure the integrity and confidentiality of APIs.