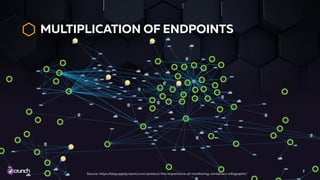
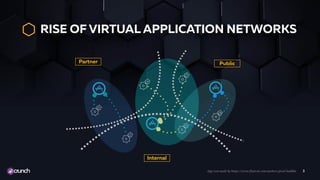
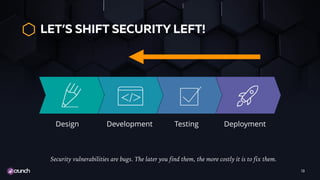
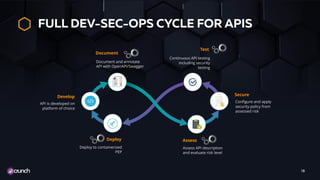
The document emphasizes the necessity of automating API security within the evolving landscape of application development. It advocates for integrating security into the DevOps process, shifting security measures to earlier stages of development to reduce vulnerabilities and costs. Key strategies include using automated scans, threat modeling, and a policy-as-code approach to enhance the security posture across the development lifecycle.