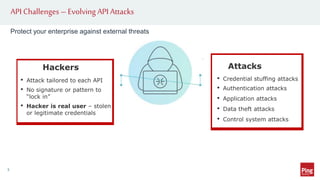
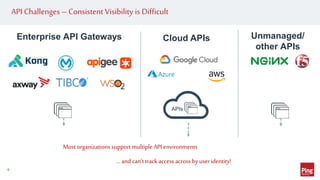
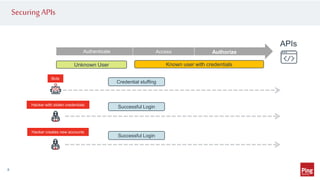
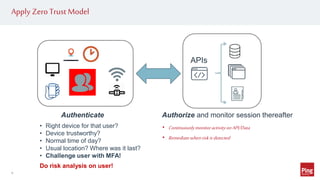
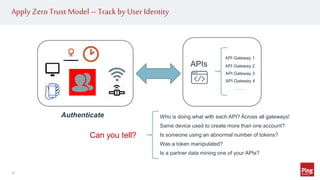
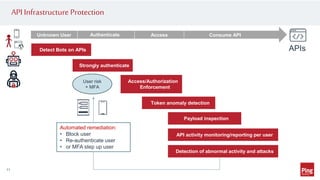
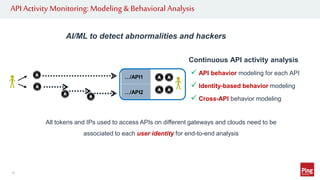
Hackers are exploiting APIs to steal data and access accounts by using valid credentials obtained through phishing, purchase, or partnerships. This poses a challenge as hackers can blend in with real users while maliciously accessing API services. To protect APIs, organizations need visibility into activity across all API gateways and clouds on a per user identity basis. They should also implement authentication, authorization, monitoring for abnormal behavior using machine learning, and automated remediation when risks are detected. Applying a zero trust model with these strategies can help secure APIs.