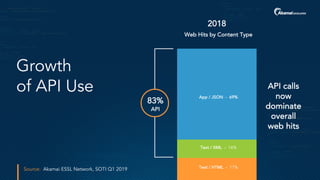
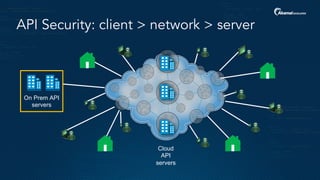
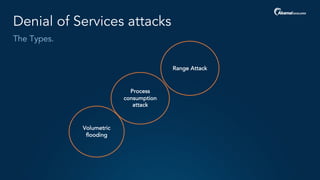
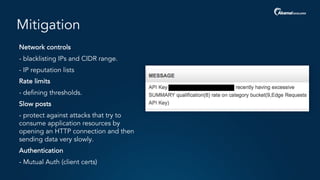
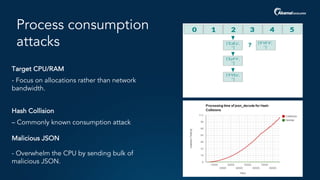
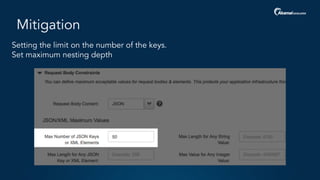
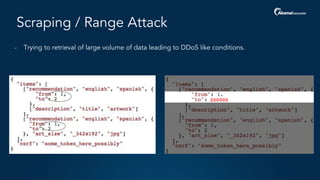
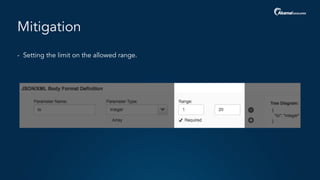
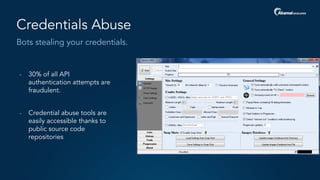
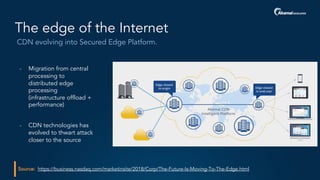
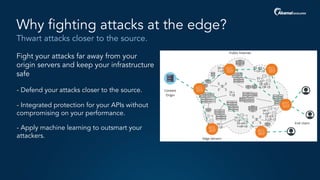
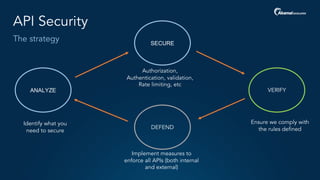
The document outlines a five-step plan for securing APIs, highlighting the increasing vulnerability of APIs to various attacks, including DDoS and SQL injection. It emphasizes the importance of API security practices such as credential management, bot detection, and leveraging edge technologies for enhanced protection. The document concludes with a timeline for assessing and implementing an API protection strategy within a specified timeframe.