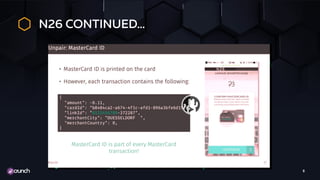
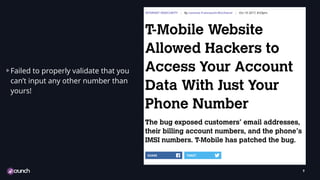
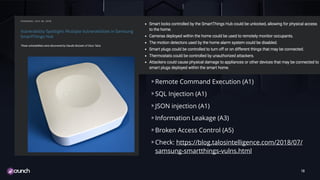
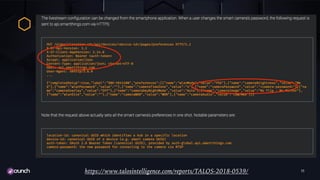
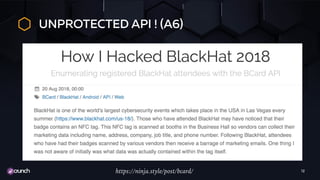
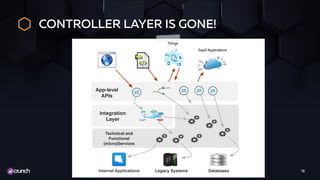
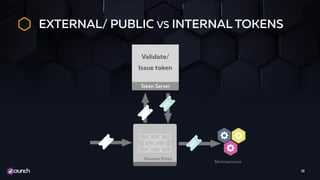
The document discusses the evolution of API security, highlighting the OWASP Top 10 vulnerabilities for 2010 and 2017, and emphasizes how different types of attacks, like injection and broken authentication, can affect APIs. It underscores the importance of validating inputs, using OAuth correctly, and implementing security measures such as API gateways and vulnerability scanning to protect APIs. Additionally, it outlines best practices for managing security throughout the development lifecycle and includes resources for further learning.