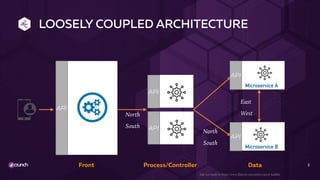
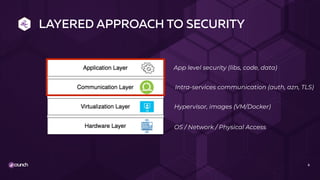
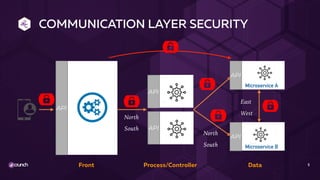
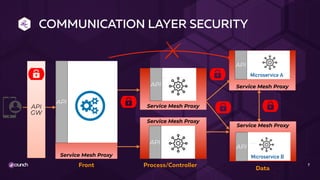
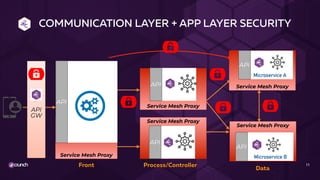
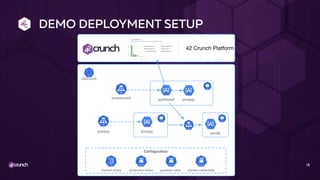
The document discusses API security in a distributed architecture, emphasizing the need for a layered security approach, particularly for microservices deployed on Kubernetes. It highlights crucial security principles such as zero trust architecture, the importance of API threat protection, and the role of an API gateway and service mesh in enforcing communication and application-level security. Additionally, it details various vulnerabilities specific to API-based applications and presents the evolution of security practices, advocating for automated, scalable solutions integrated into the API lifecycle.