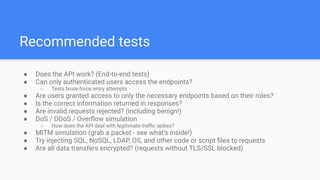
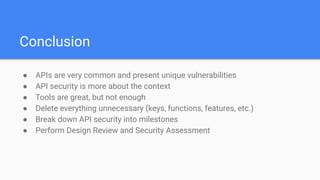
The document outlines essential practices for API security, emphasizing the importance of investing in security measures due to the vulnerabilities associated with APIs. Key recommendations include implementing strong authentication and access controls, ensuring data validation, and performing regular security assessments. It also highlights common risks, the significance of reducing attack surfaces, and the need for thorough documentation and monitoring.