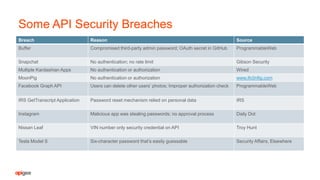
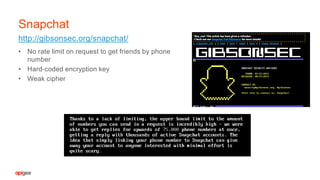
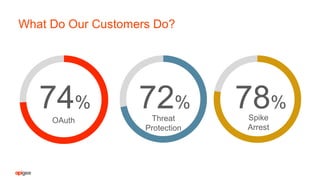
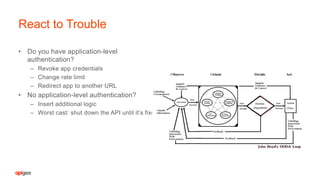
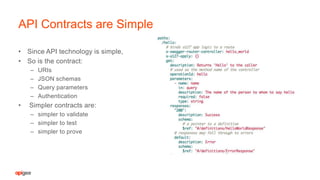
The document discusses API security fundamentals and how to effectively secure APIs. It notes that many past API breaches were due to a lack of authentication on APIs, no rate limiting of requests, and other basic security issues. It emphasizes that every system with a URI has an API and outlines steps like applying authentication, authorization, rate limiting, validating requests to prevent attacks. The document argues that APIs with well-defined contracts that specify URIs, input/output formats and authentication models are easier to securely implement and test compared to more complex, dynamic APIs.