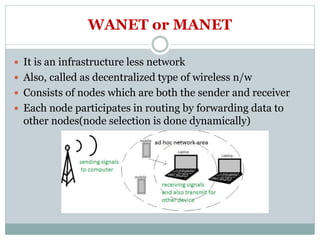
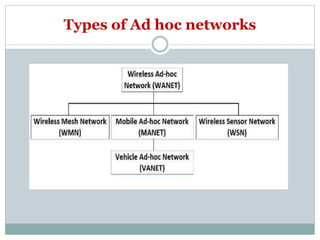
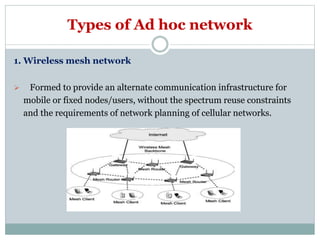
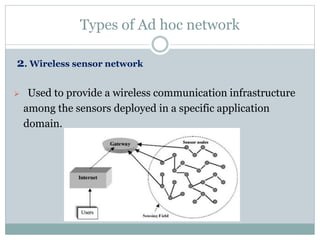
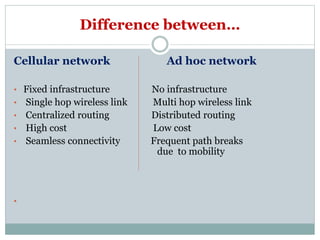
The document discusses key concepts related to ad hoc and wireless sensor networks. It defines ad hoc networks as infrastructureless, decentralized wireless networks where nodes can act as both senders and receivers and dynamically route data through other nodes. It covers routing algorithms, single vs multi-hop communication, unicast vs broadcast vs multicast transmission, and compares ad hoc networks to cellular networks and WANETs/MANETs. Application areas like military, emergency response, and wireless sensor networks are also mentioned.