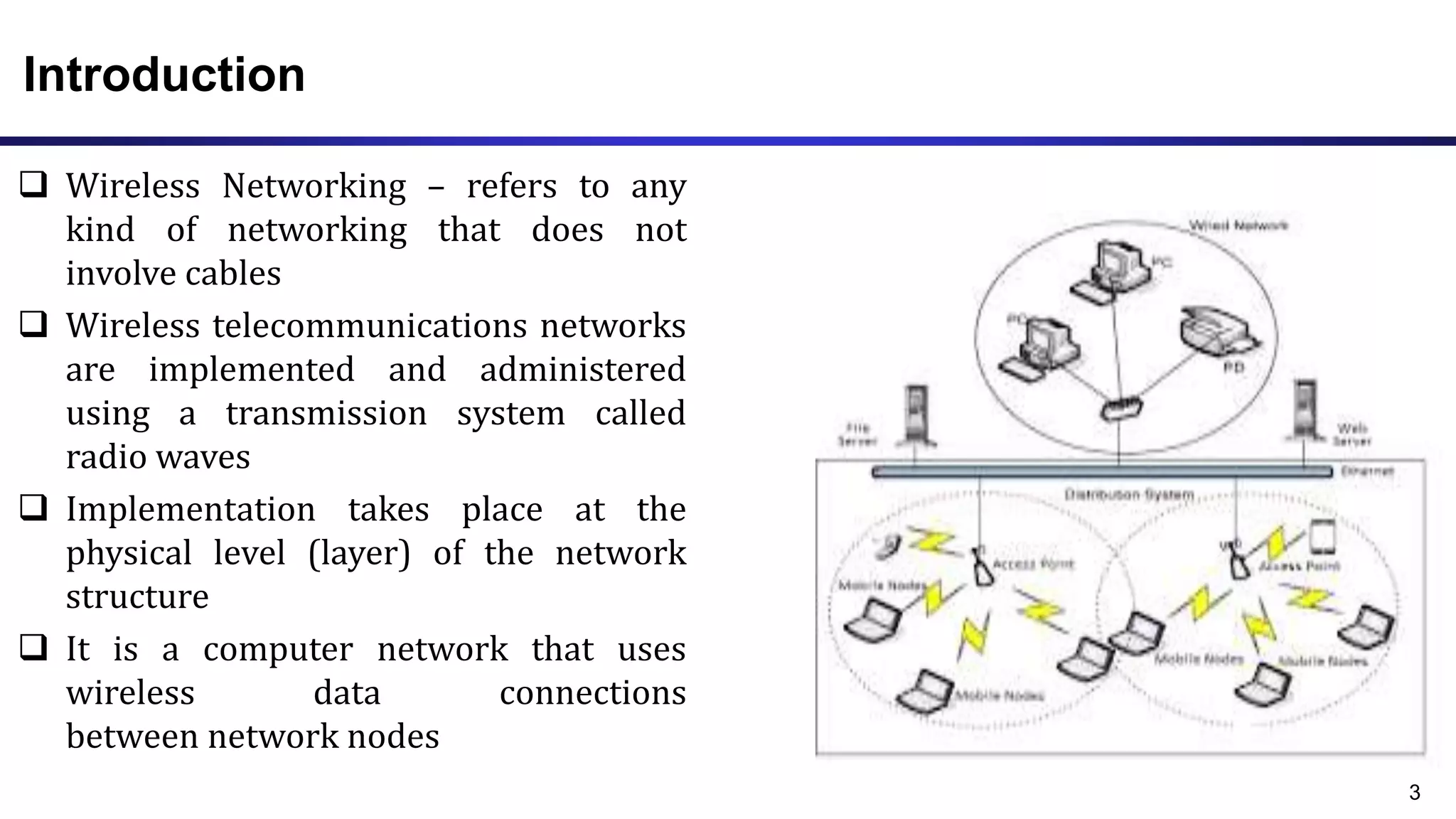
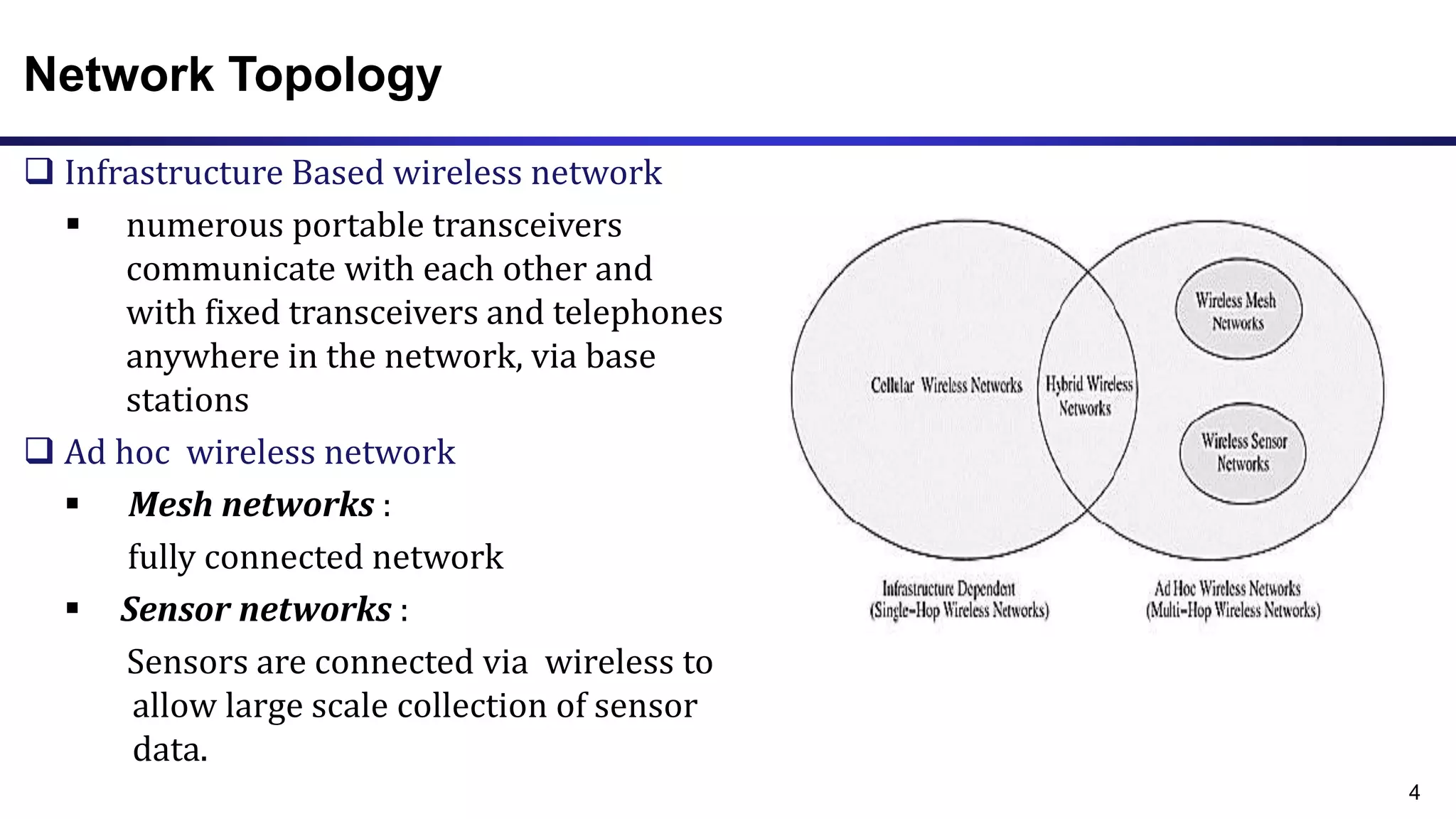
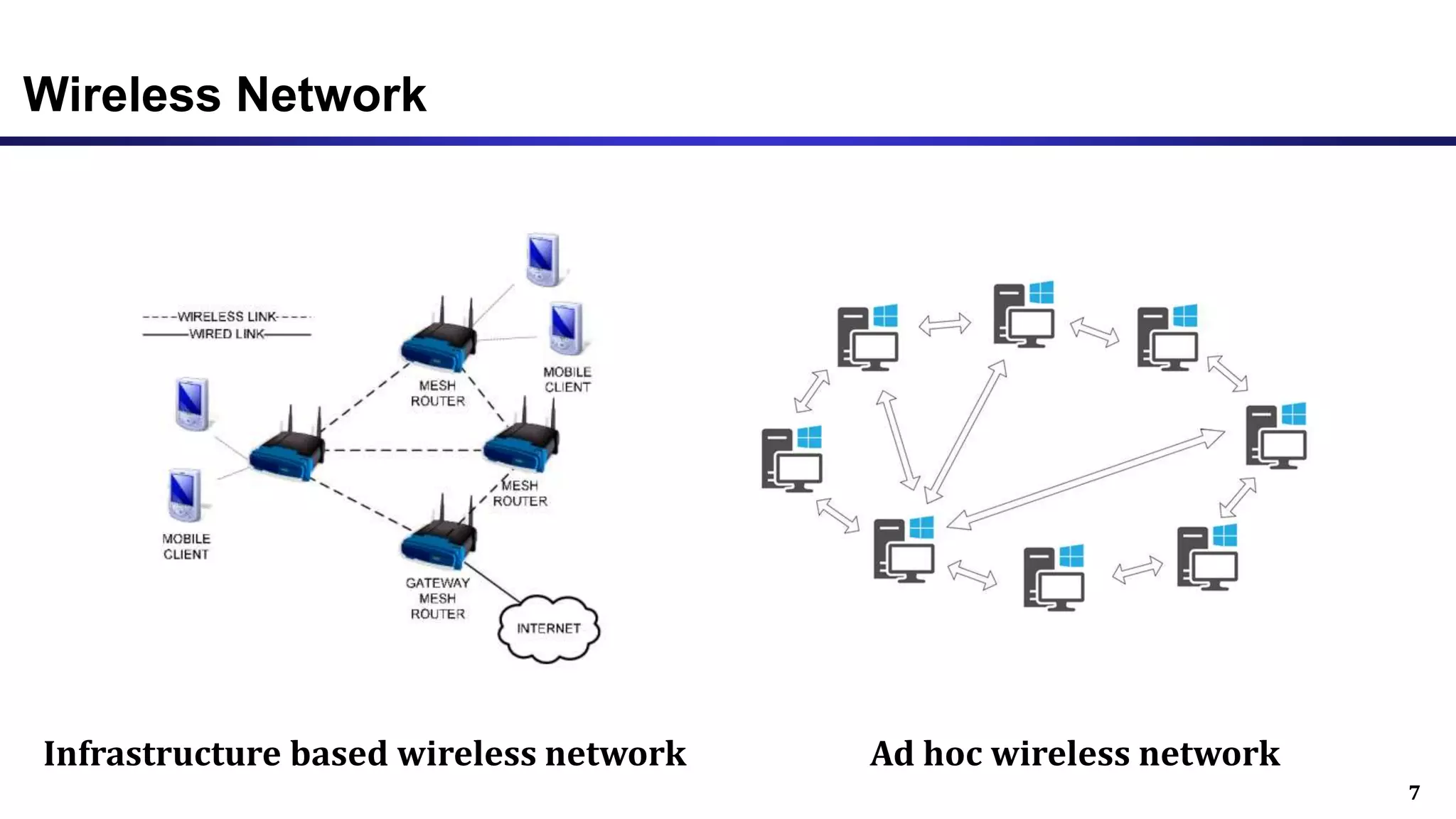
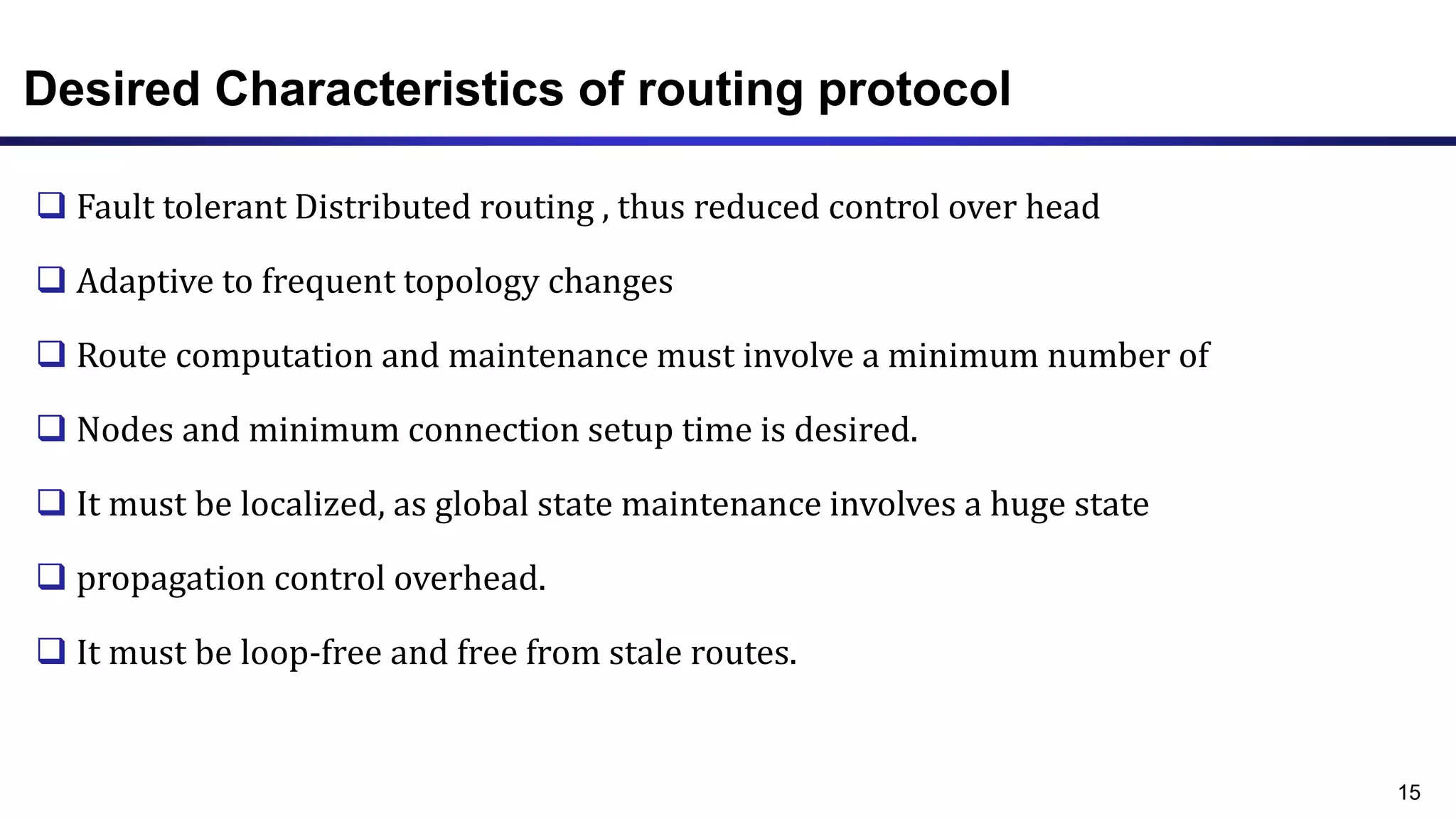
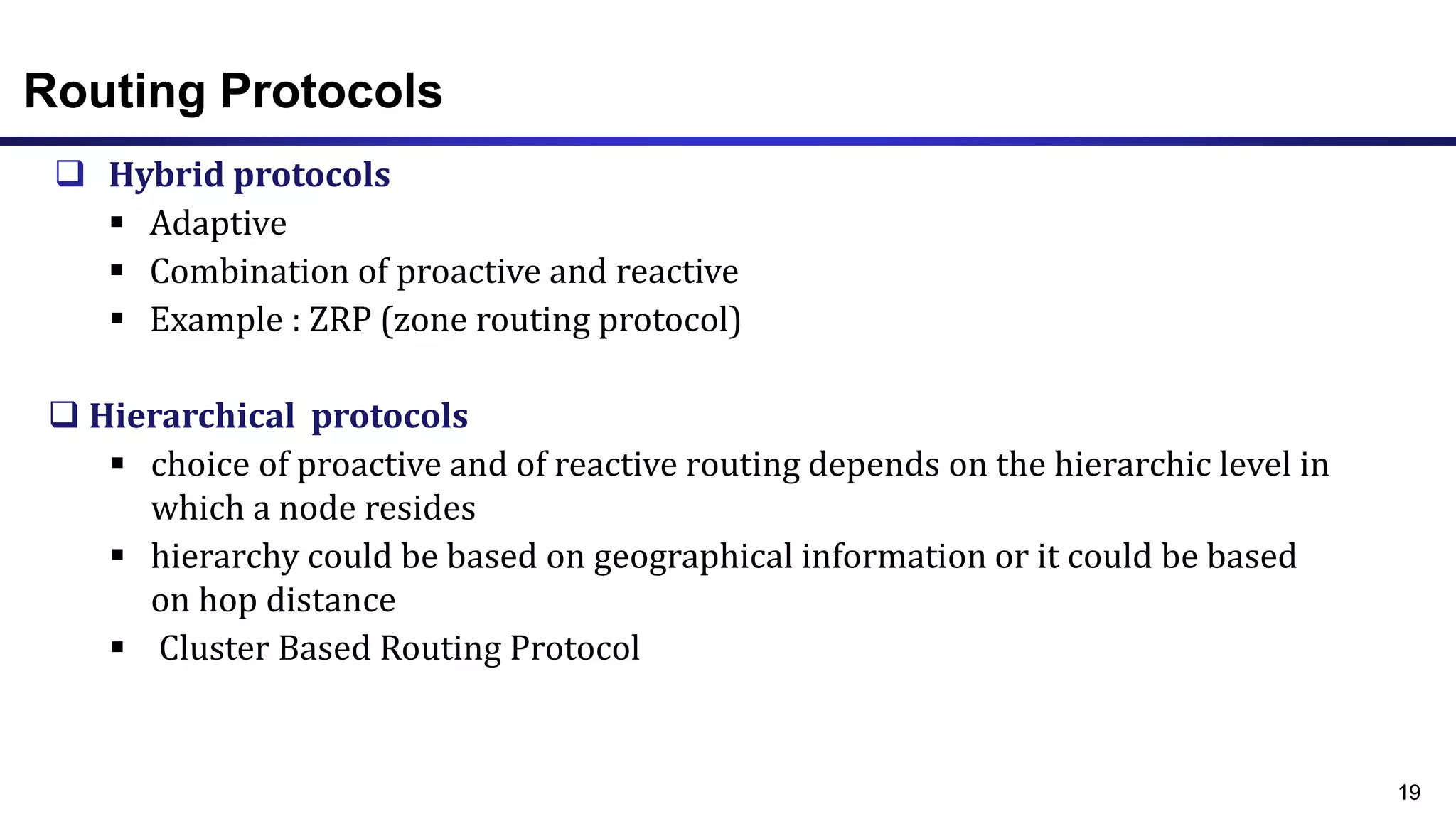
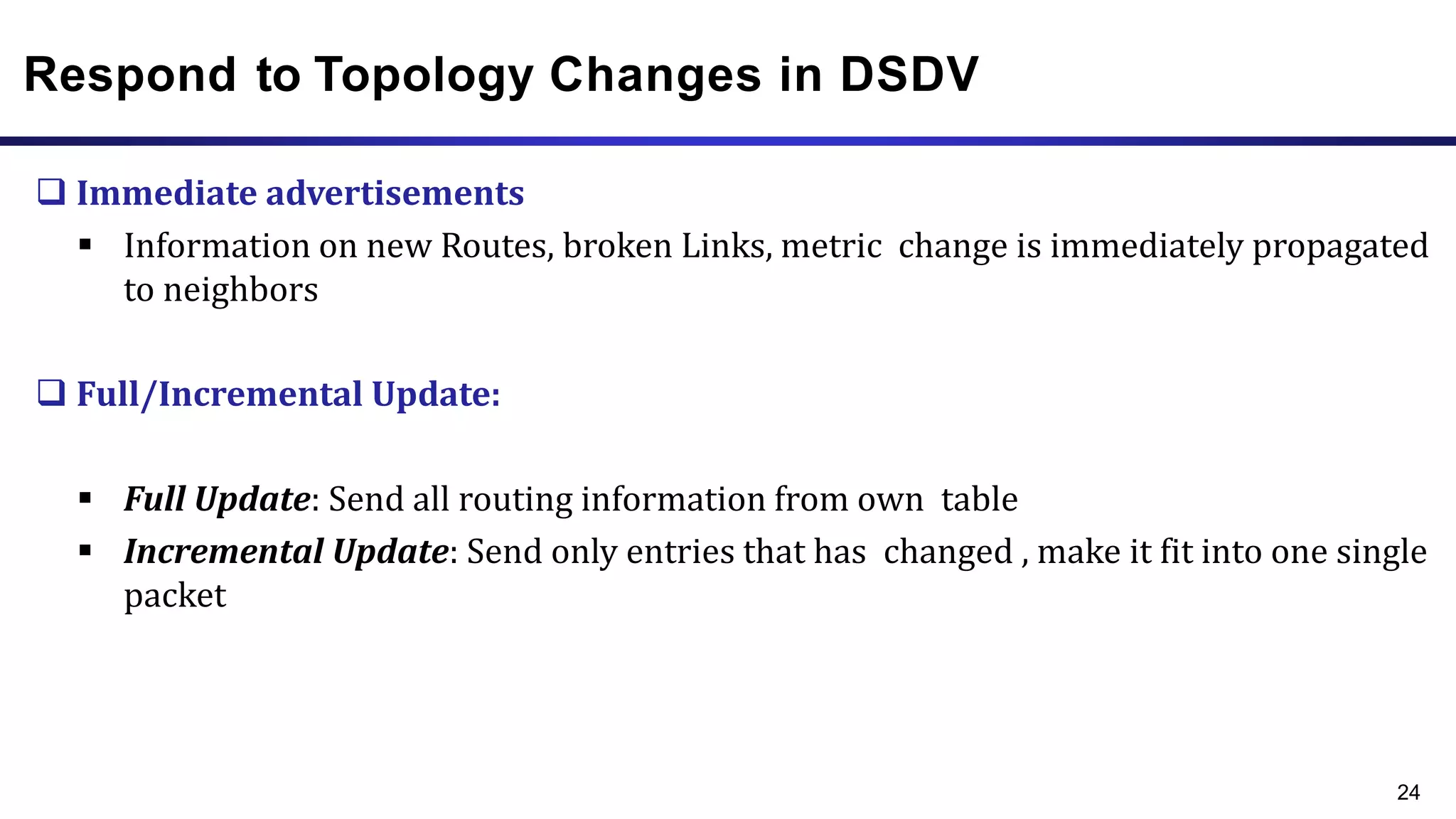
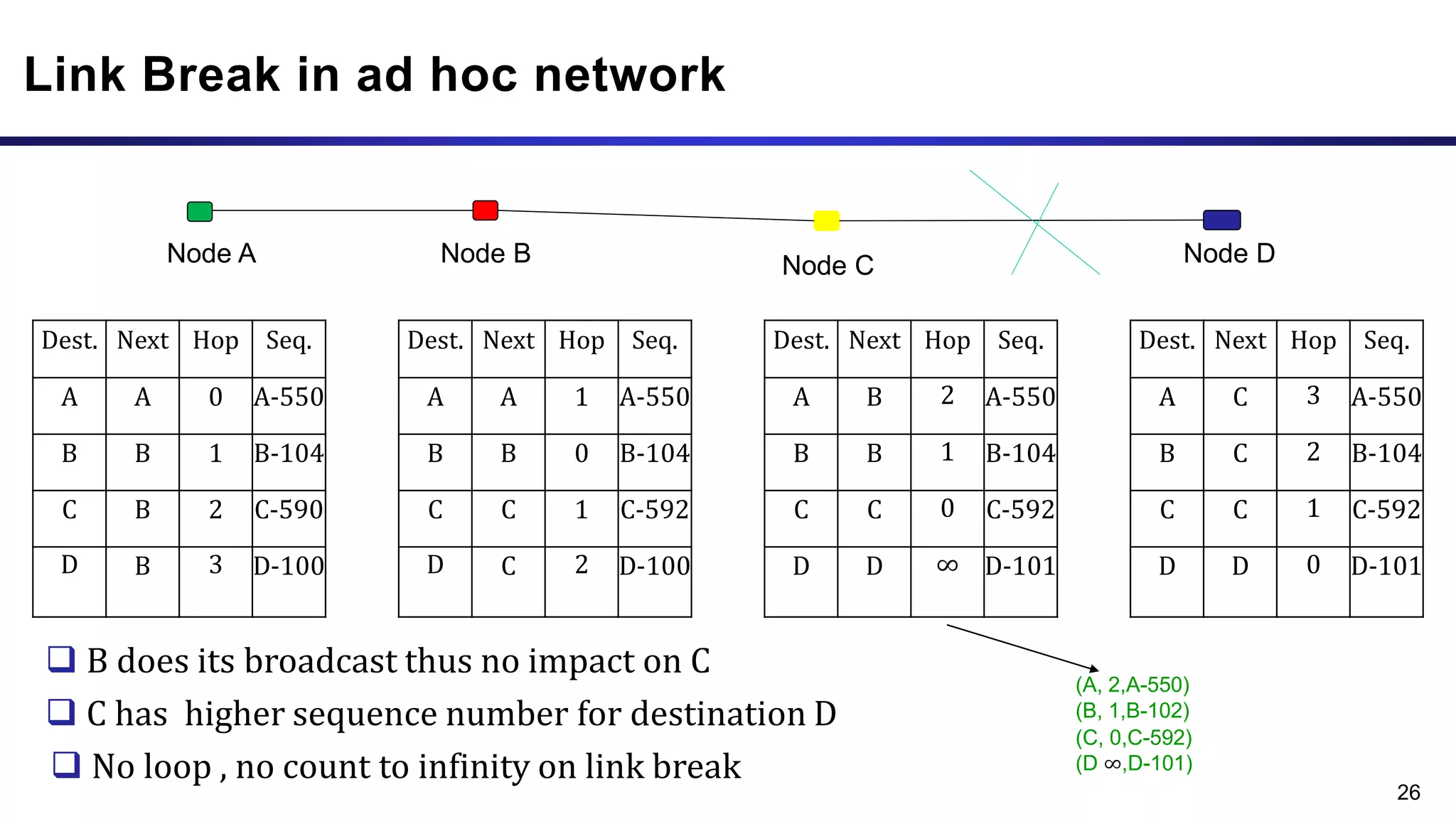
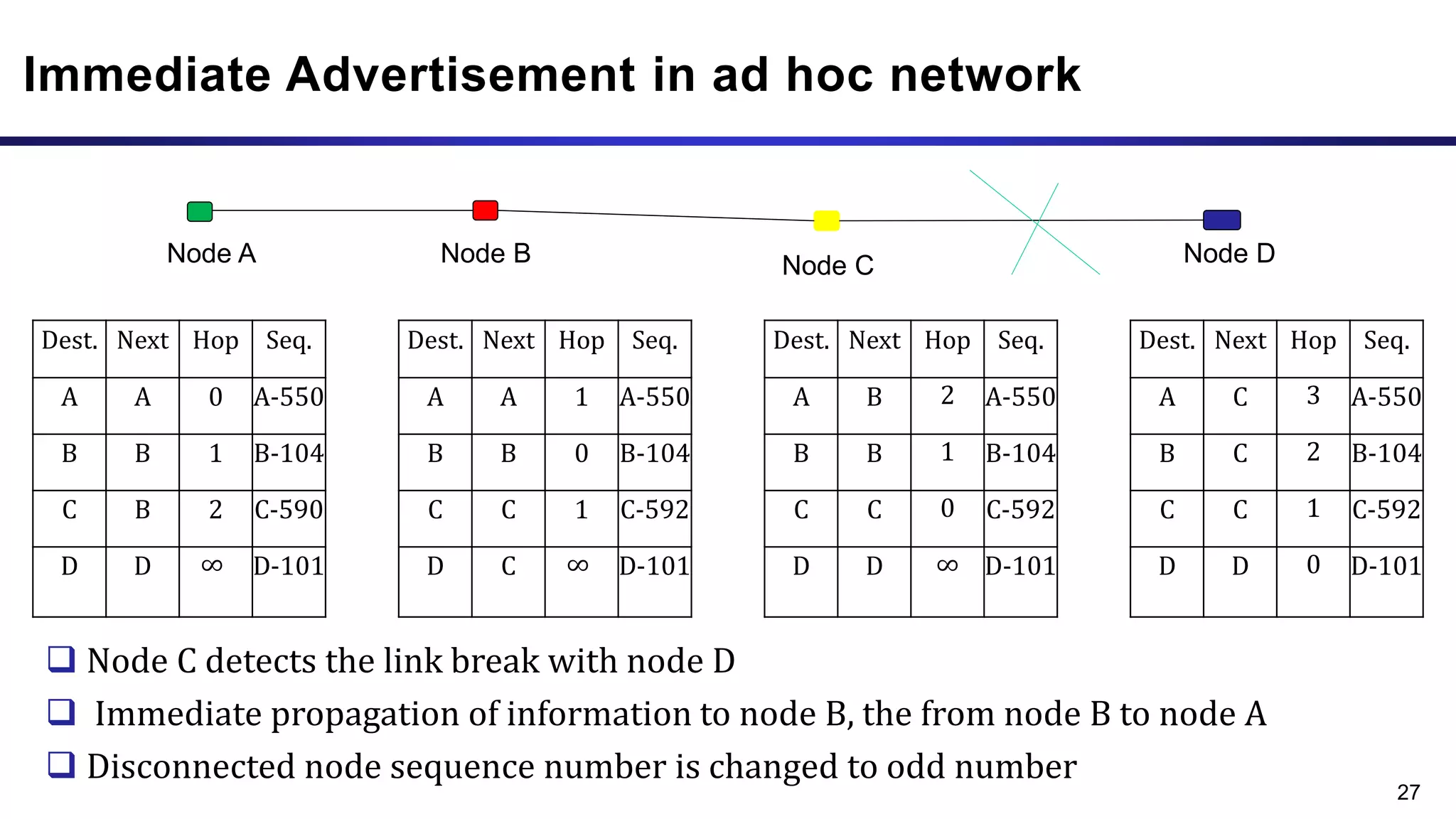
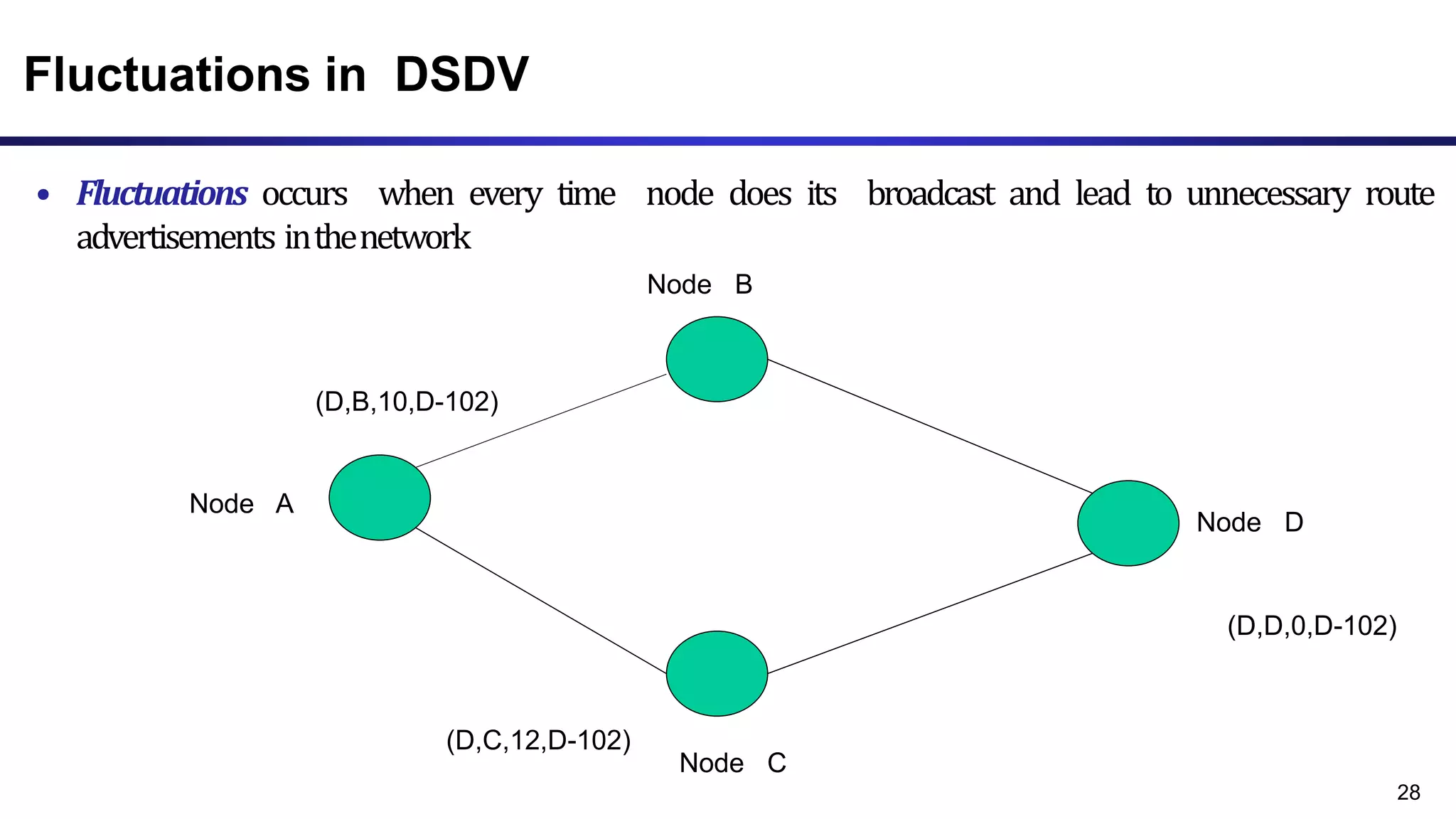
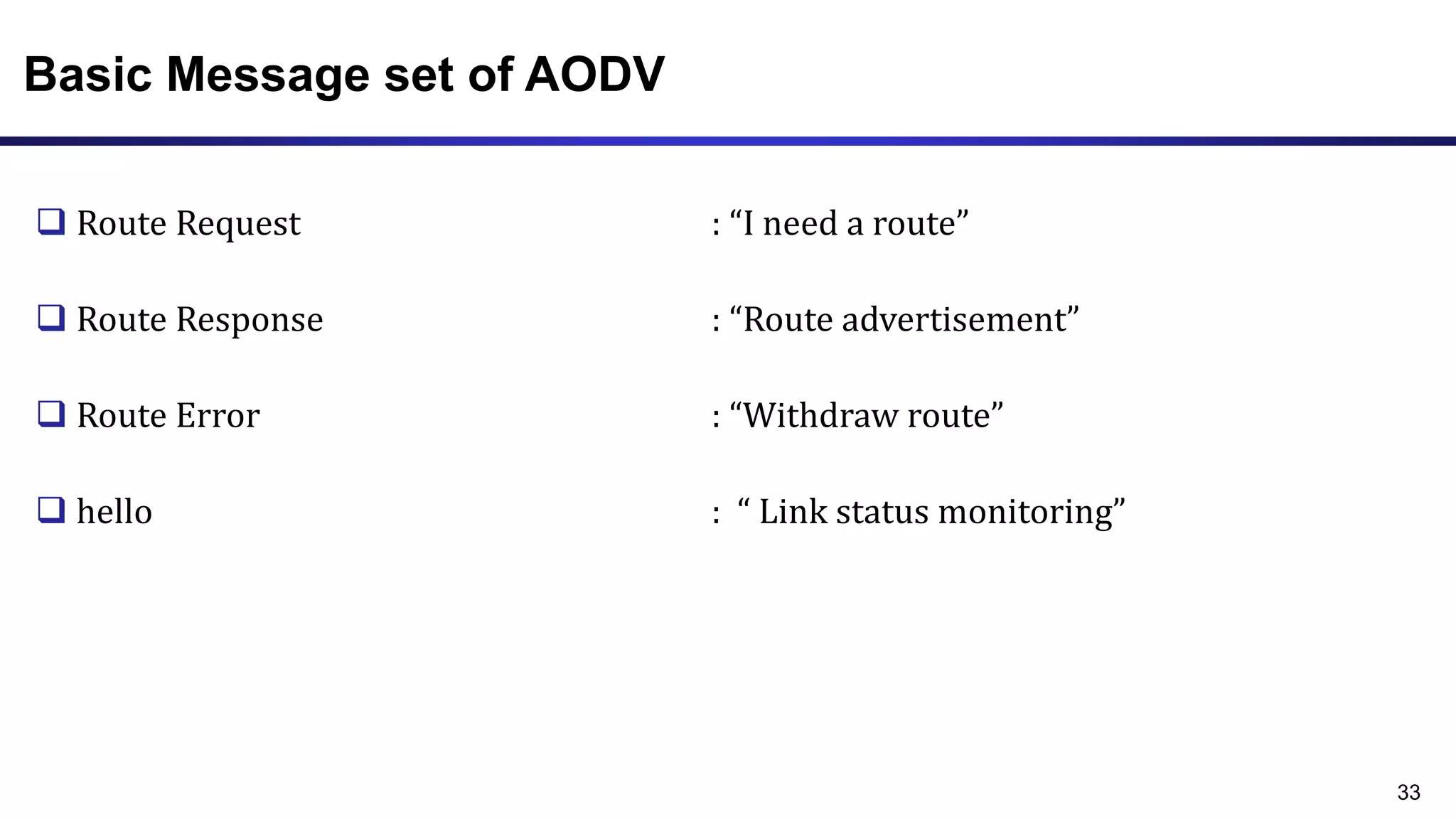
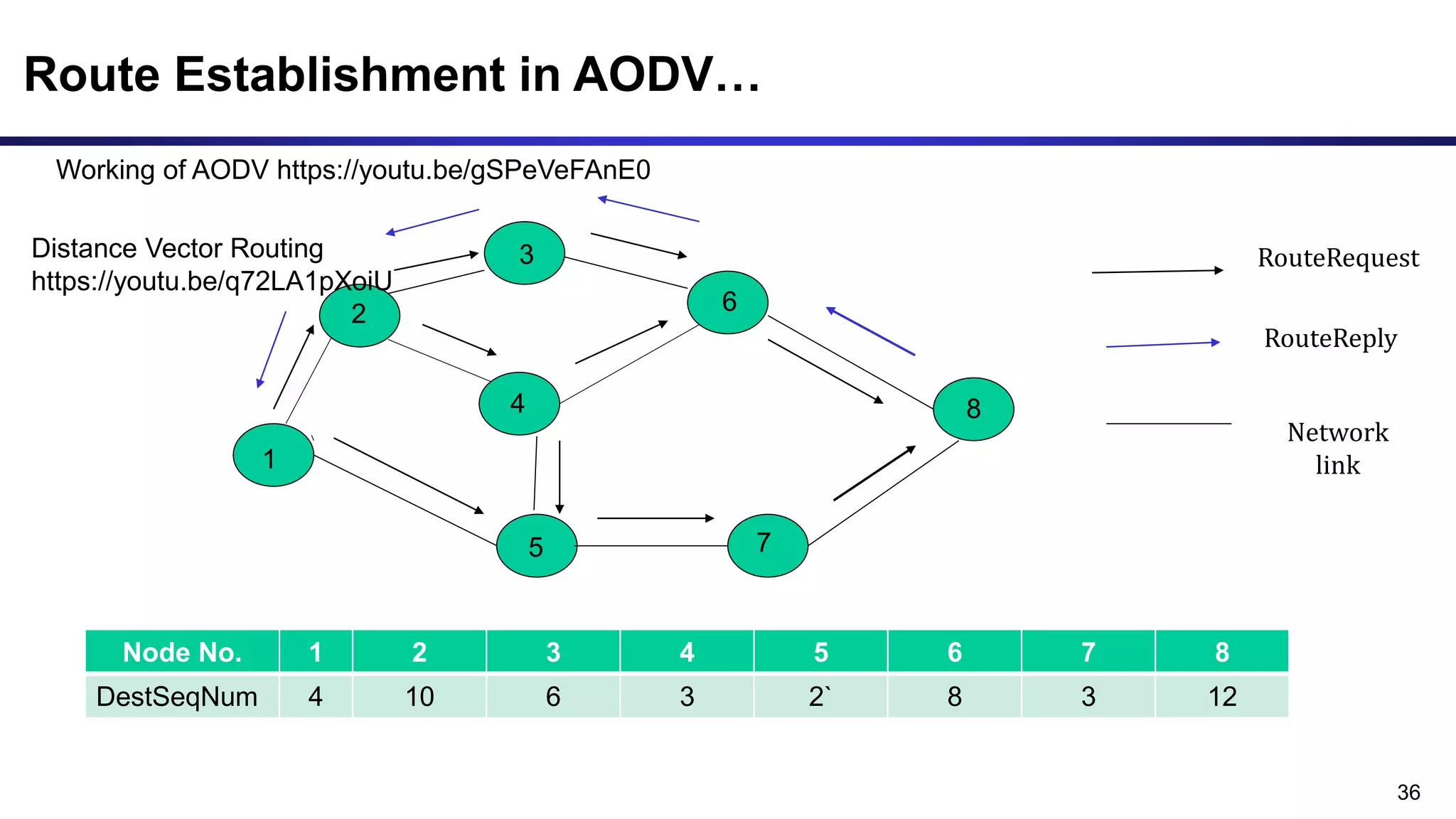
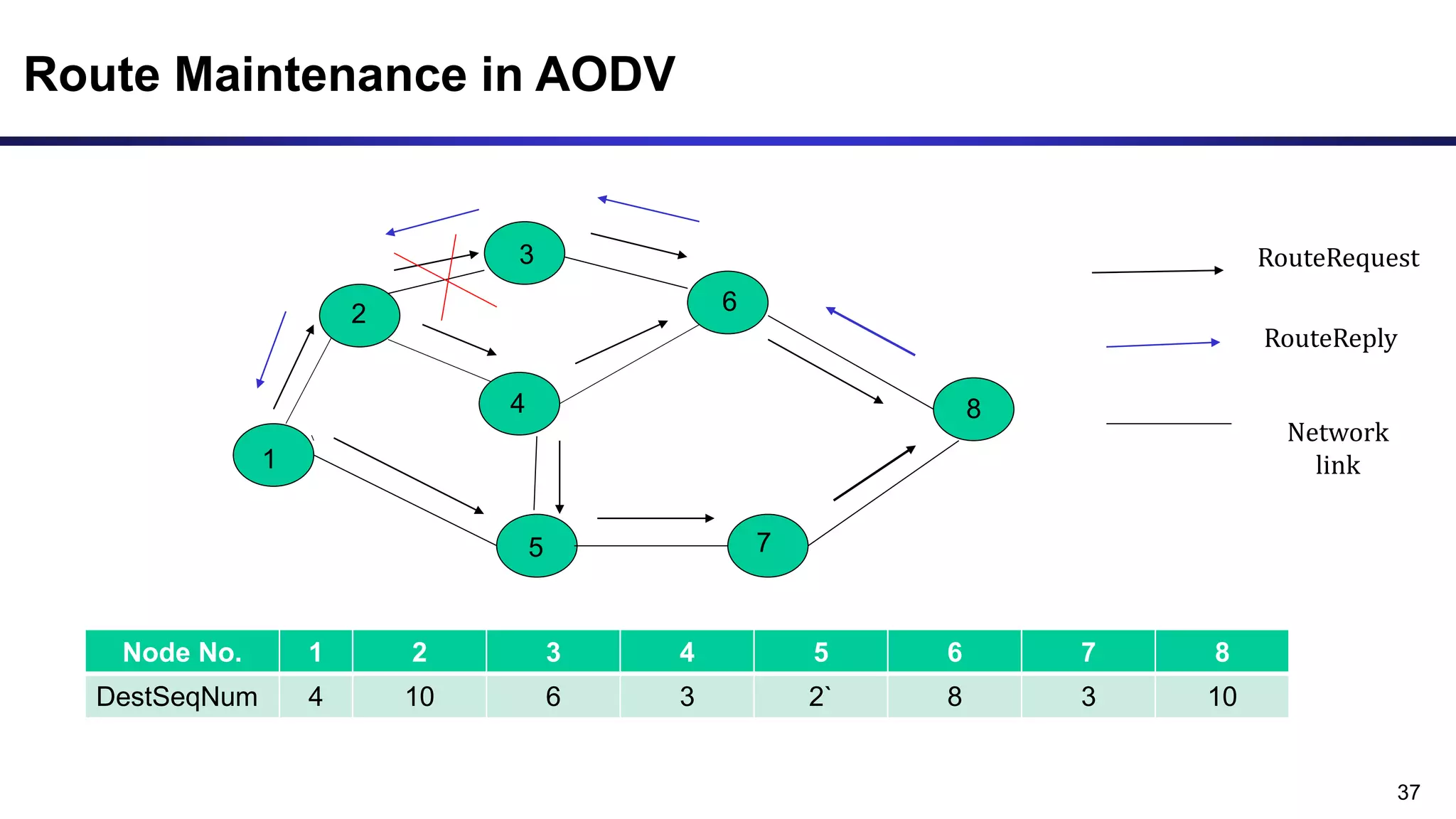
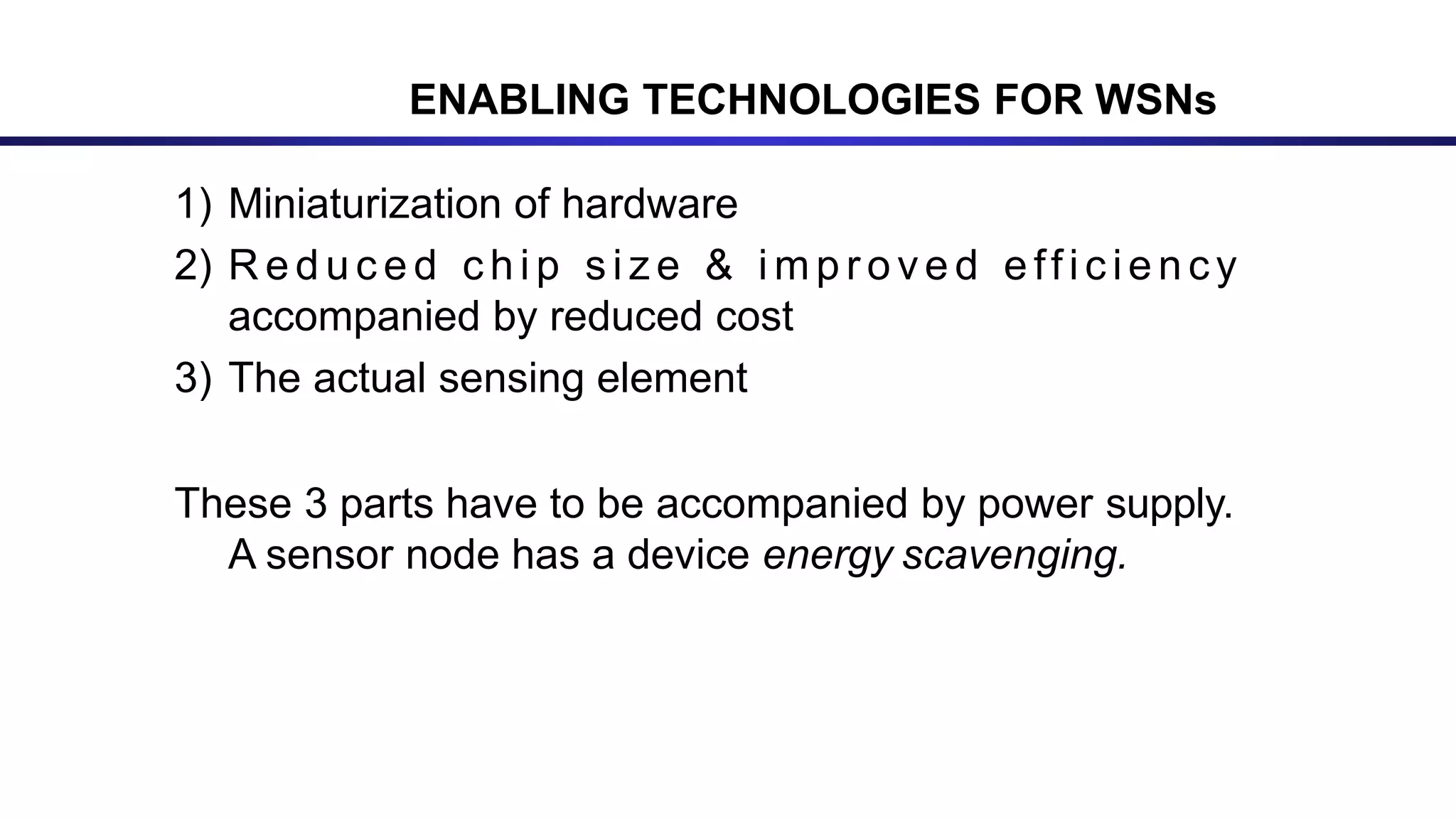
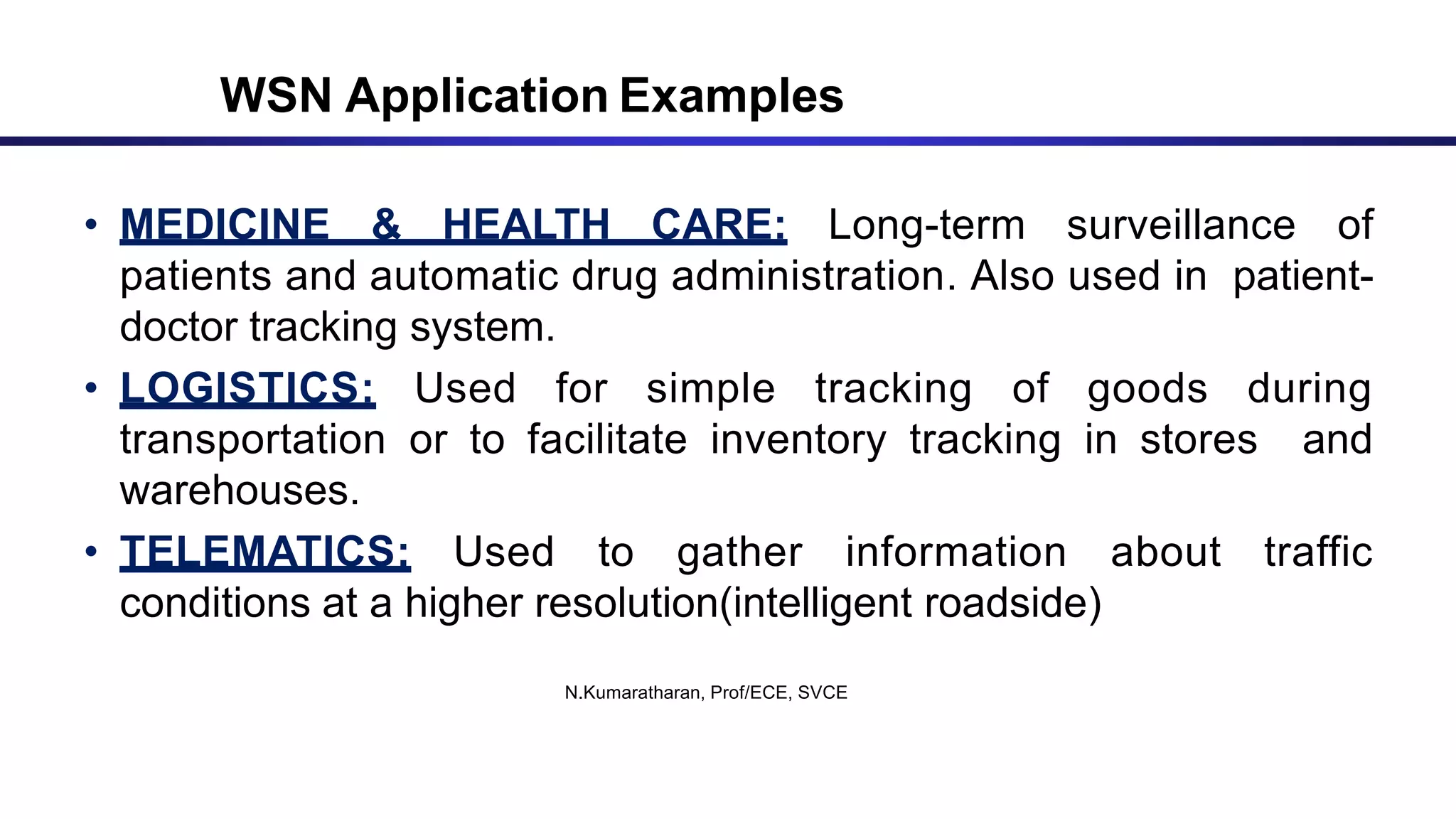
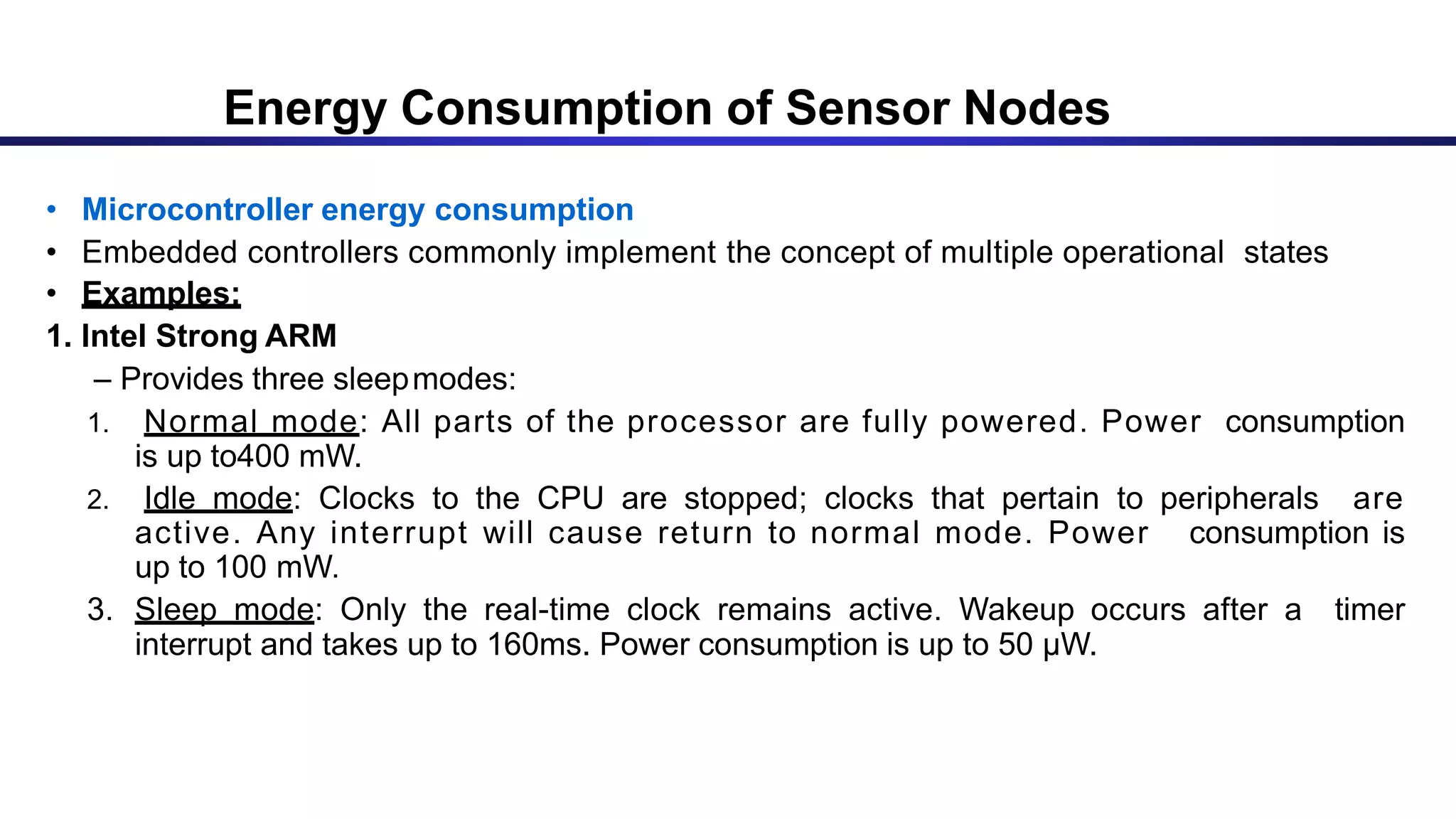
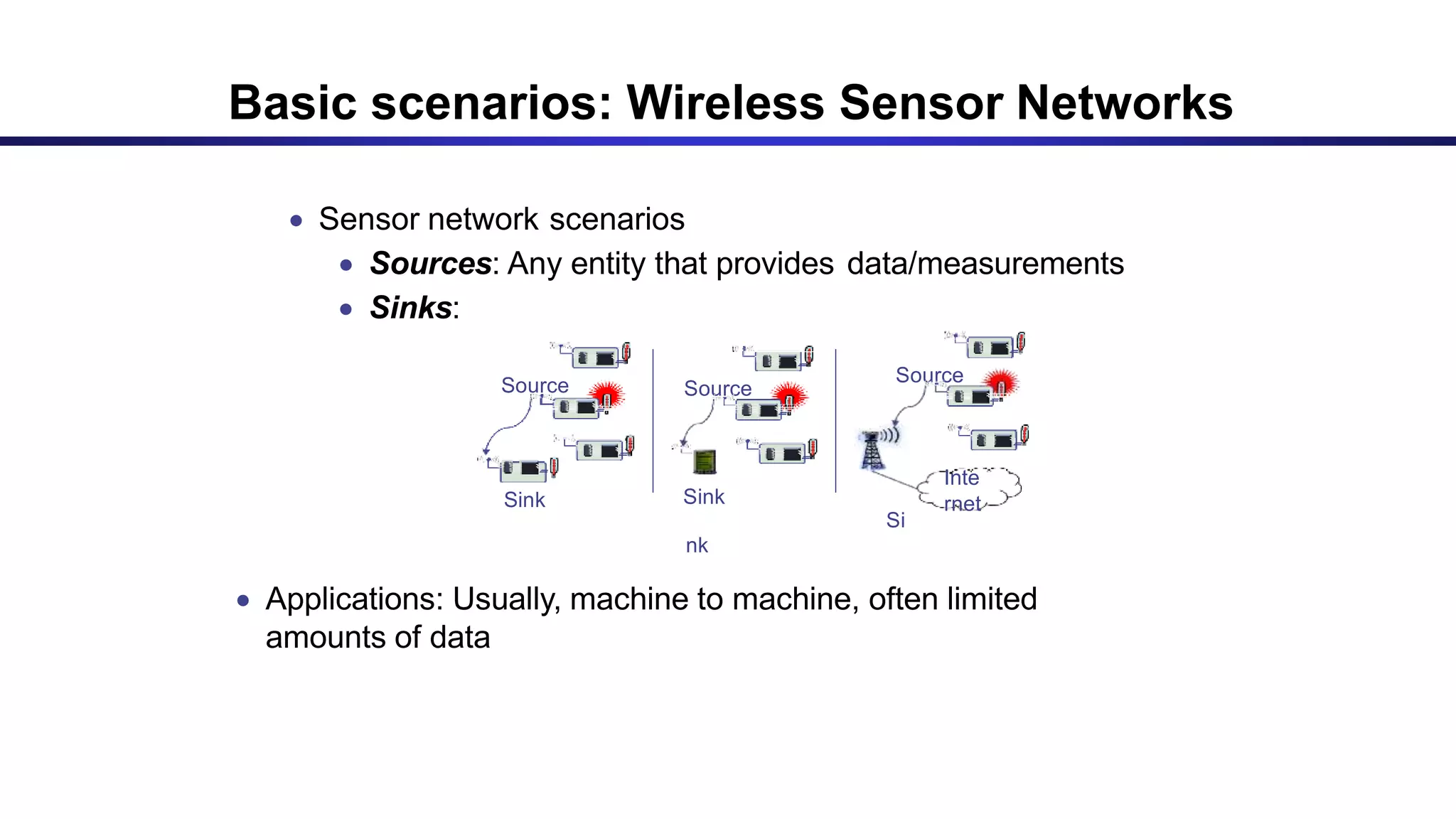
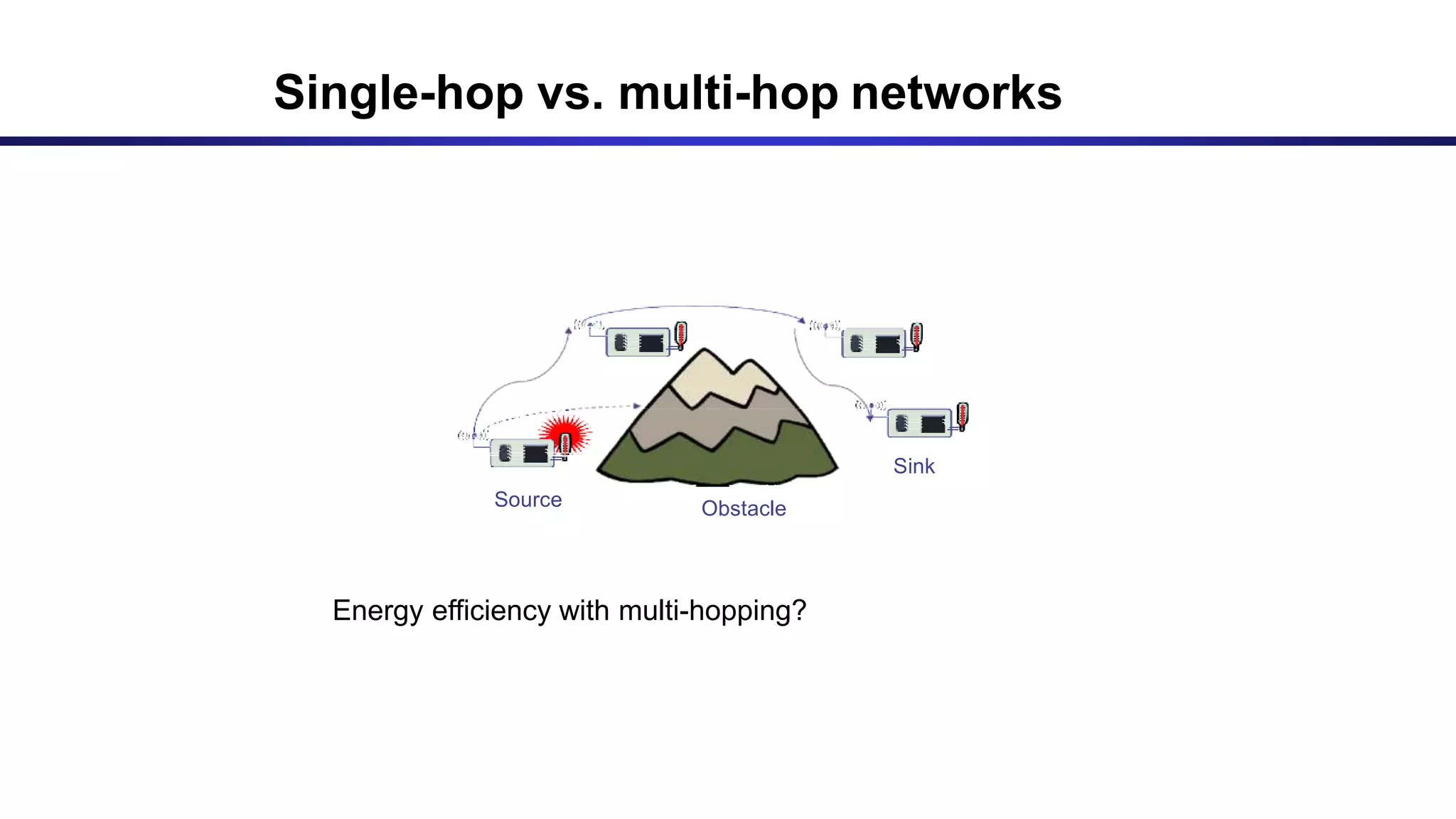
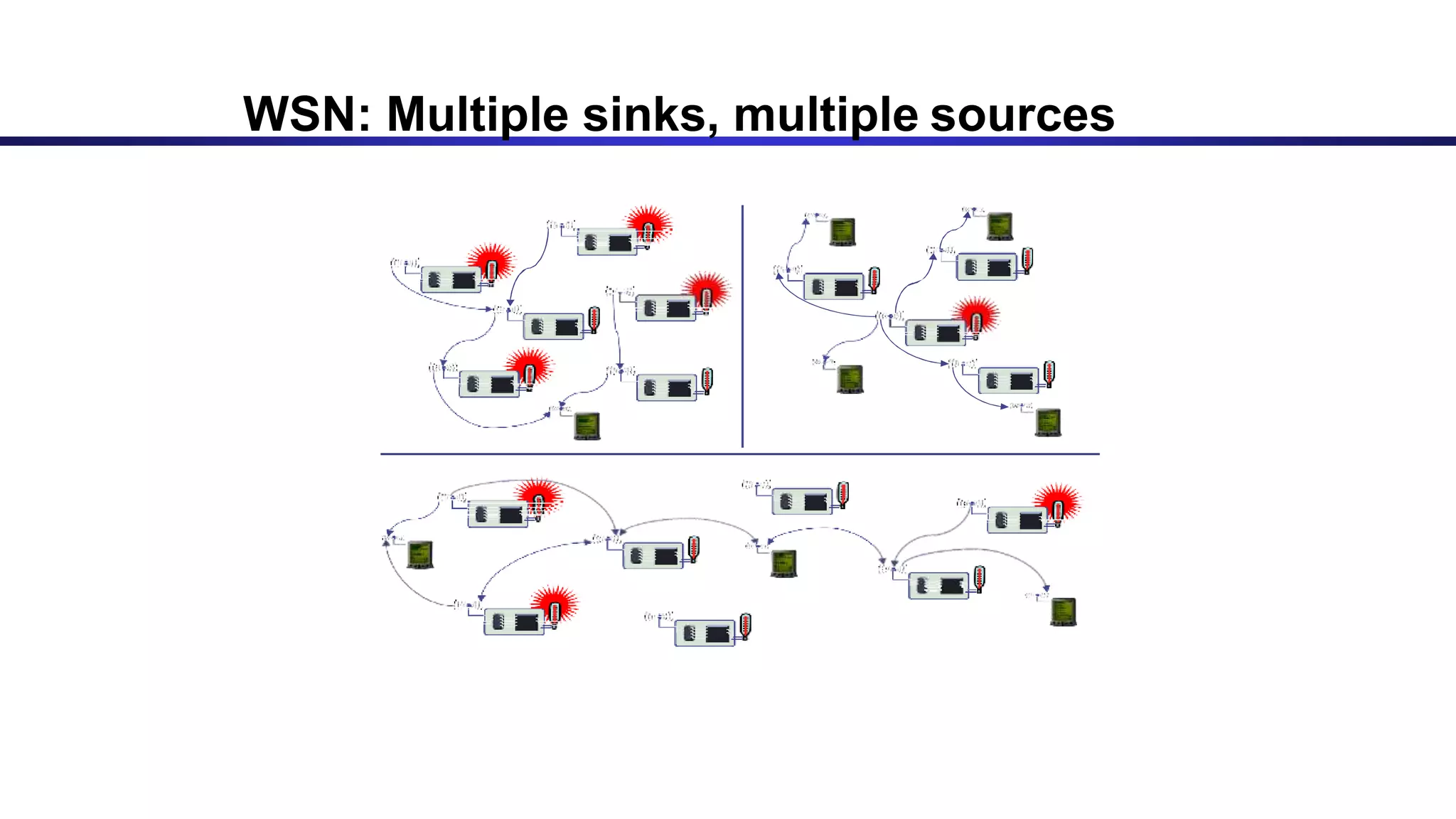
The document discusses ad hoc and sensor networks. It begins with an introduction and outline that describes key topics like features and issues of ad hoc wireless networks, types of networks, routing protocol classifications and examples of table driven and on-demand routing protocols. The document then provides more detailed descriptions of topics like infrastructure versus ad hoc networks, challenges in designing routing protocols, characteristics of good routing protocols, examples of DSDV and AODV routing protocols, and message types used in AODV.