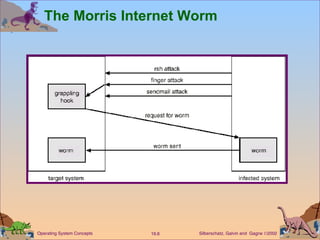
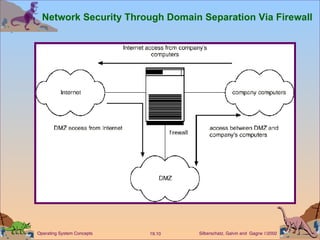
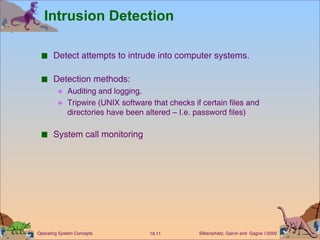
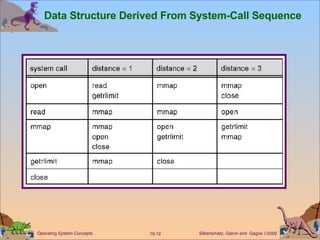
This document discusses various security issues related to computer systems and networks. It covers authentication methods, threats like Trojan horses and viruses, intrusion detection techniques, and encryption standards. It also describes security classifications from the Department of Defense and how Windows NT implements configurable security policies ranging from minimal to discretionary protection.