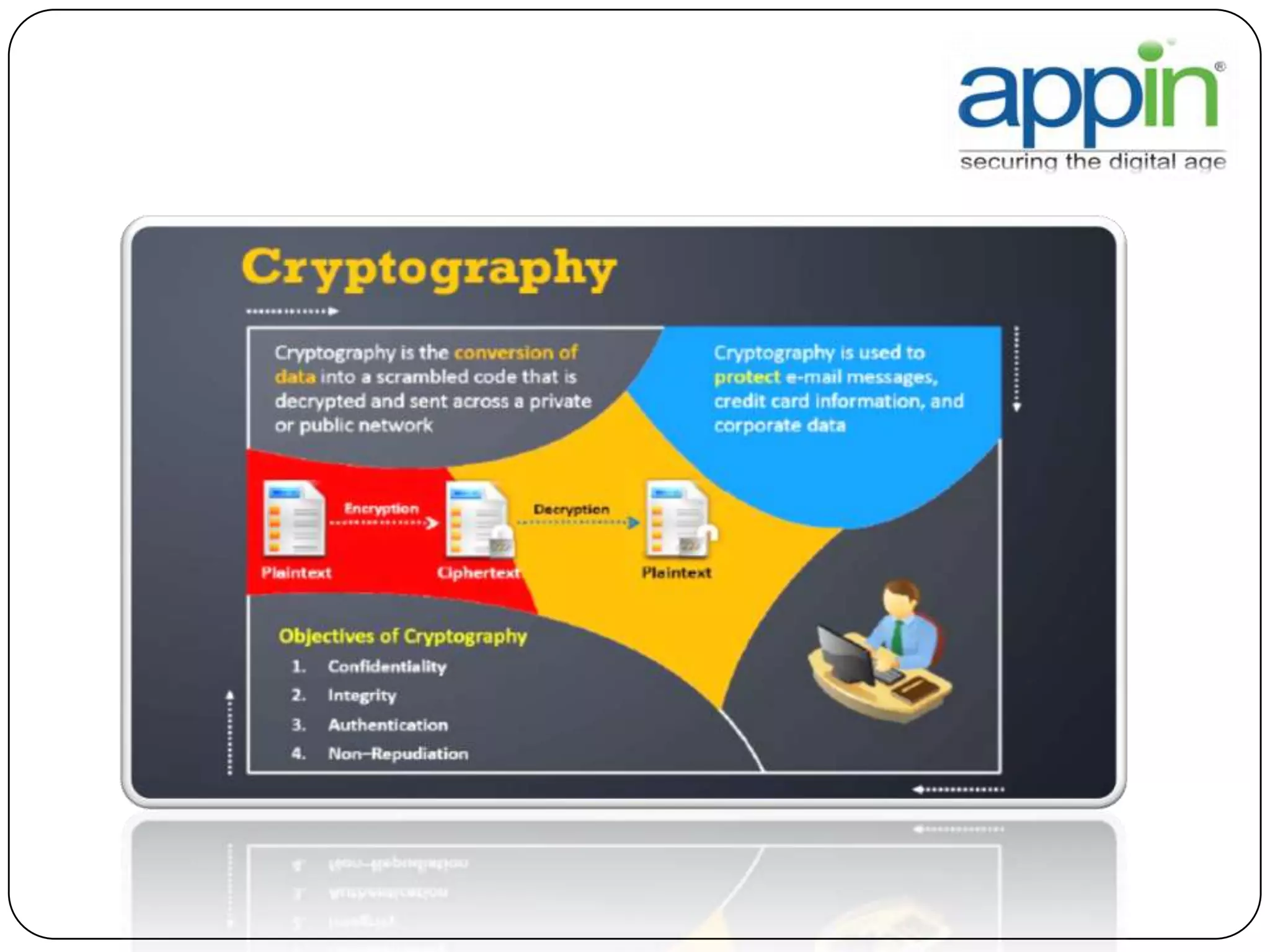
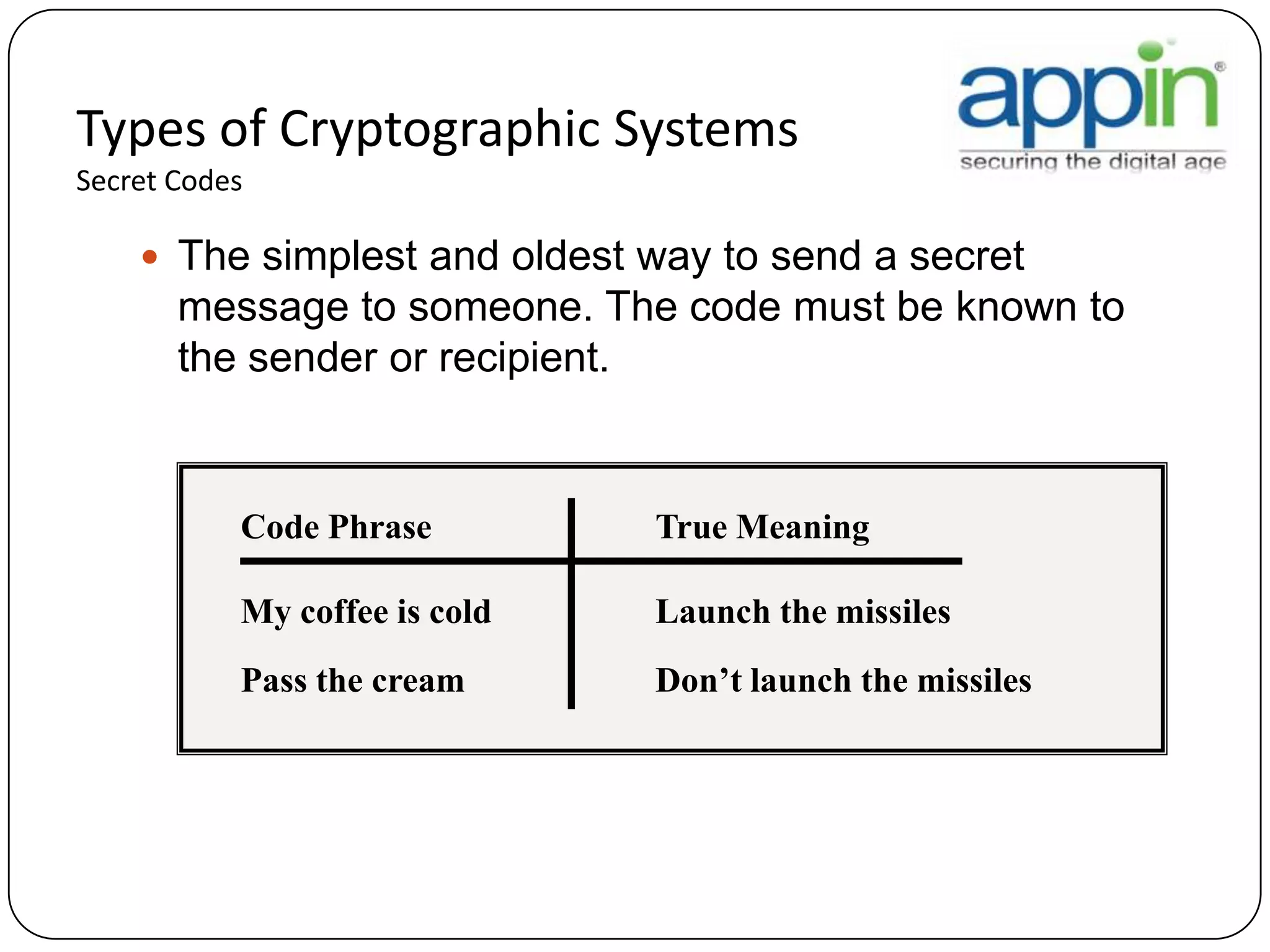
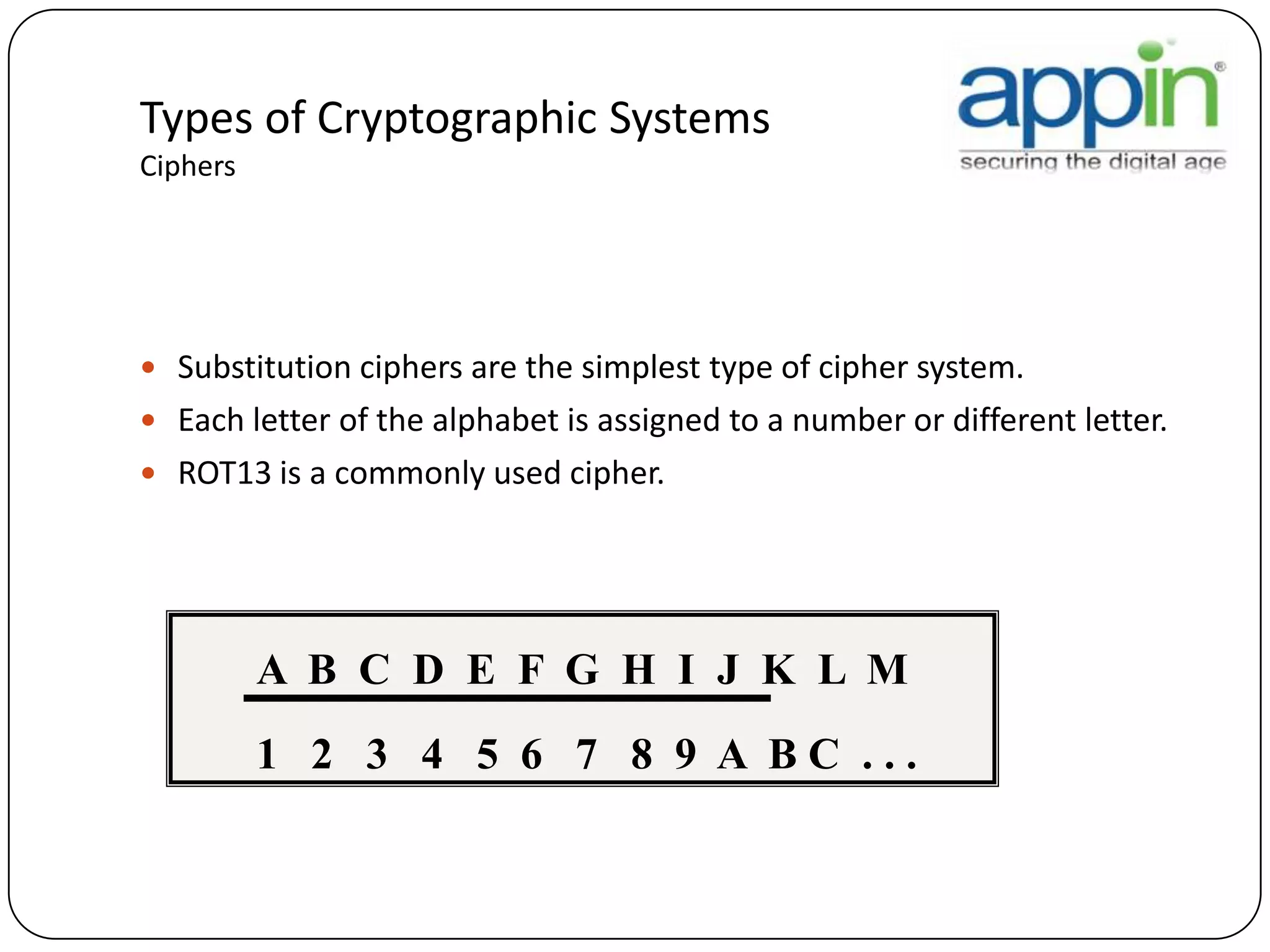
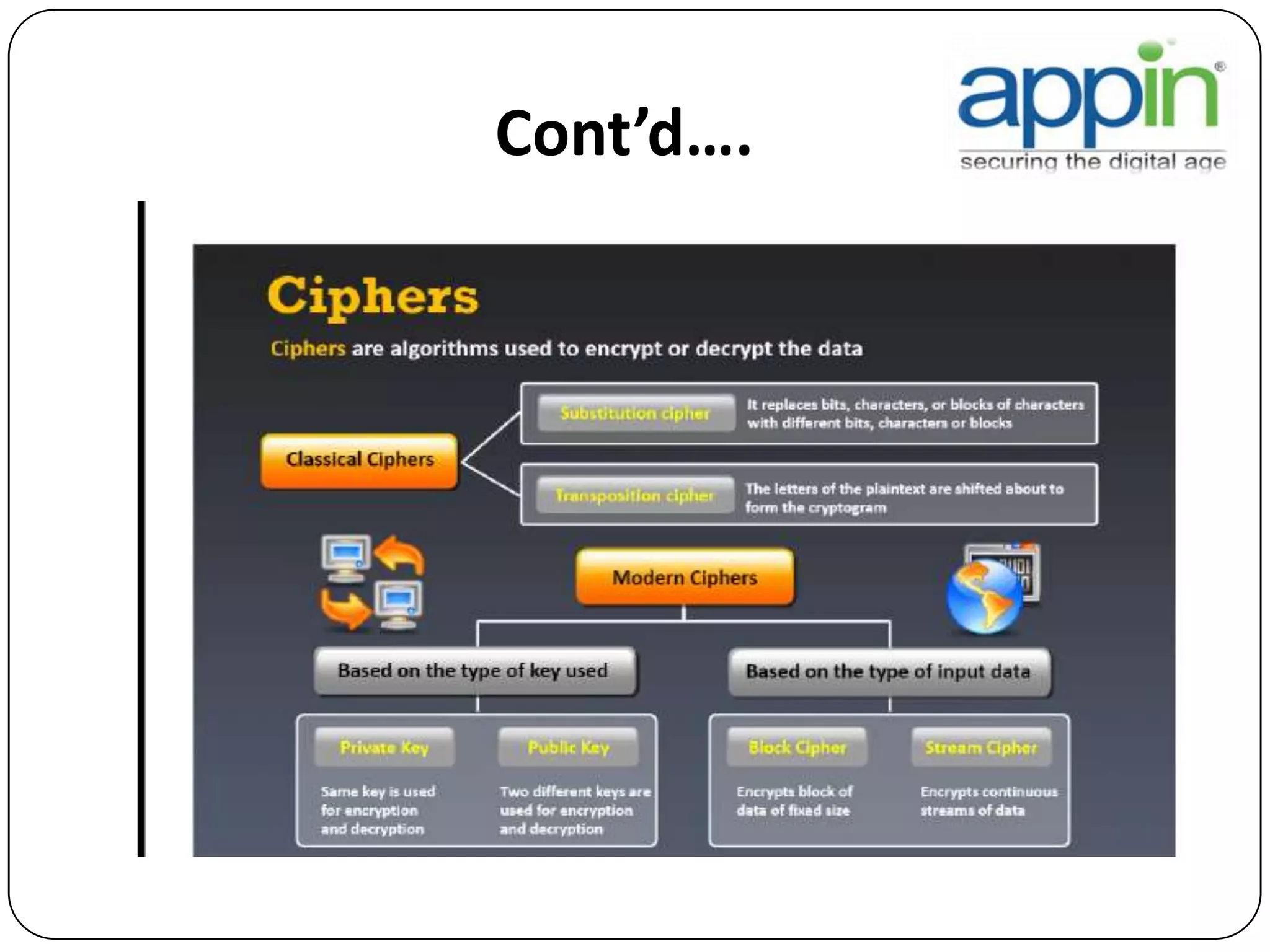
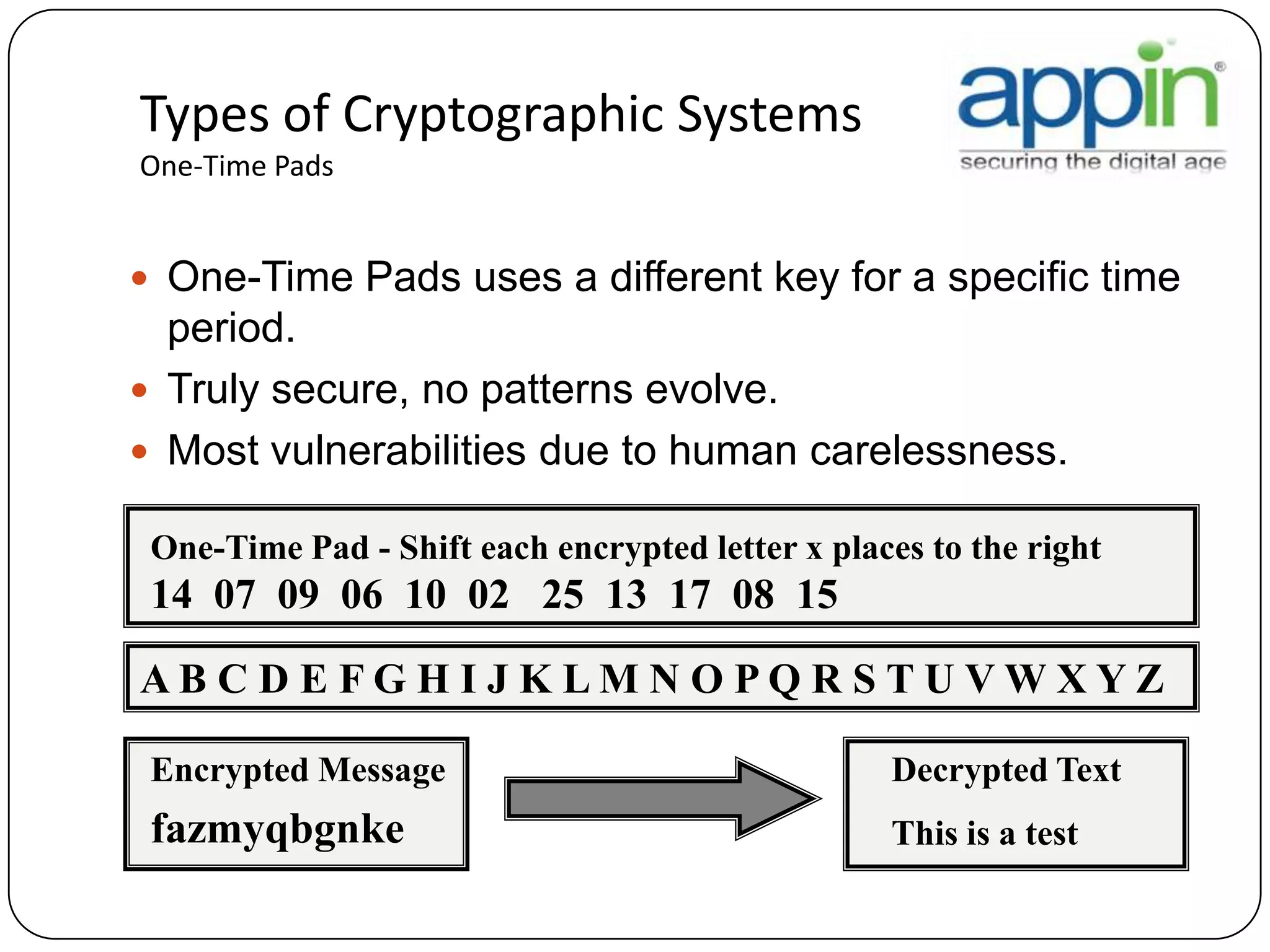
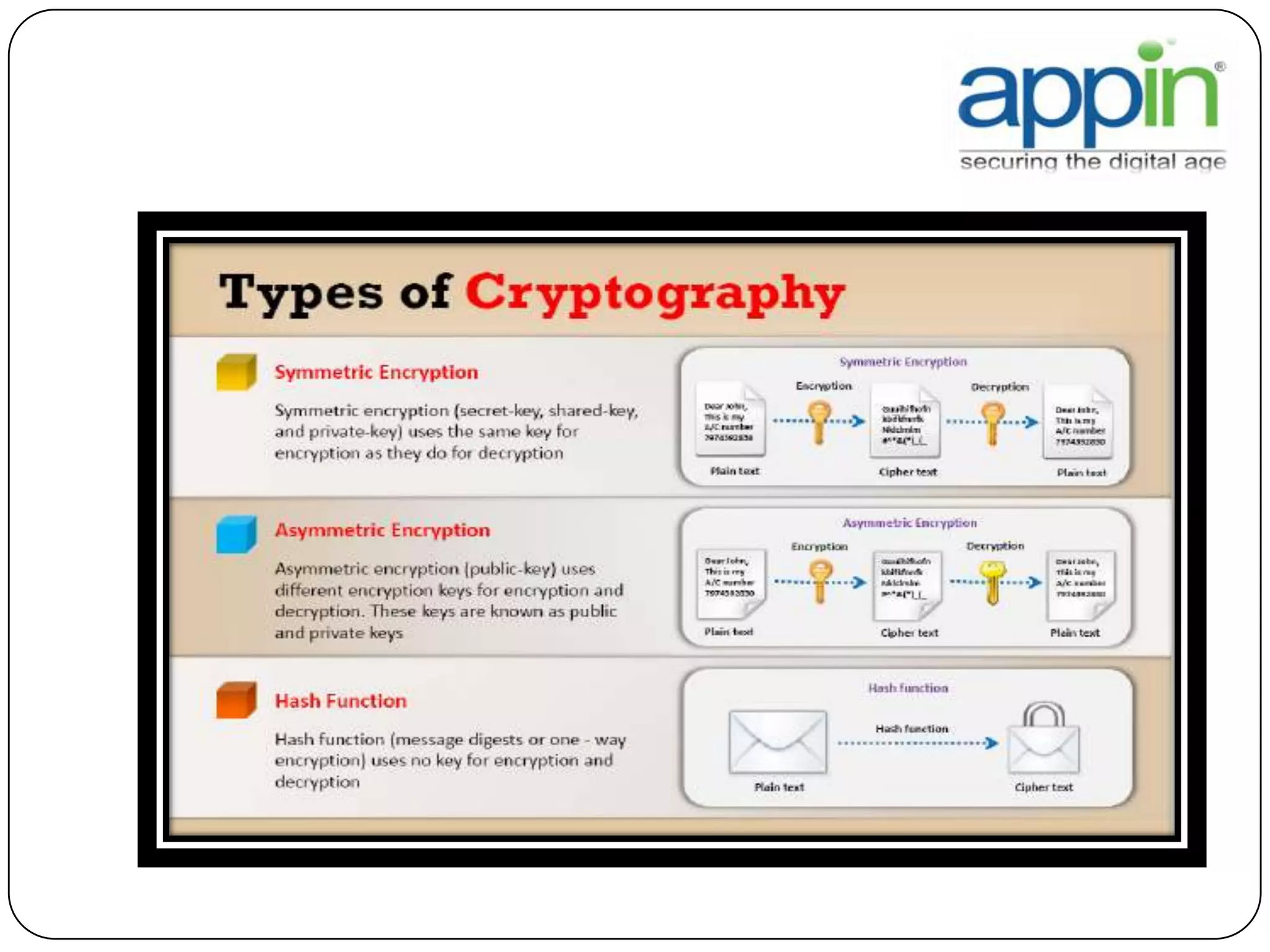
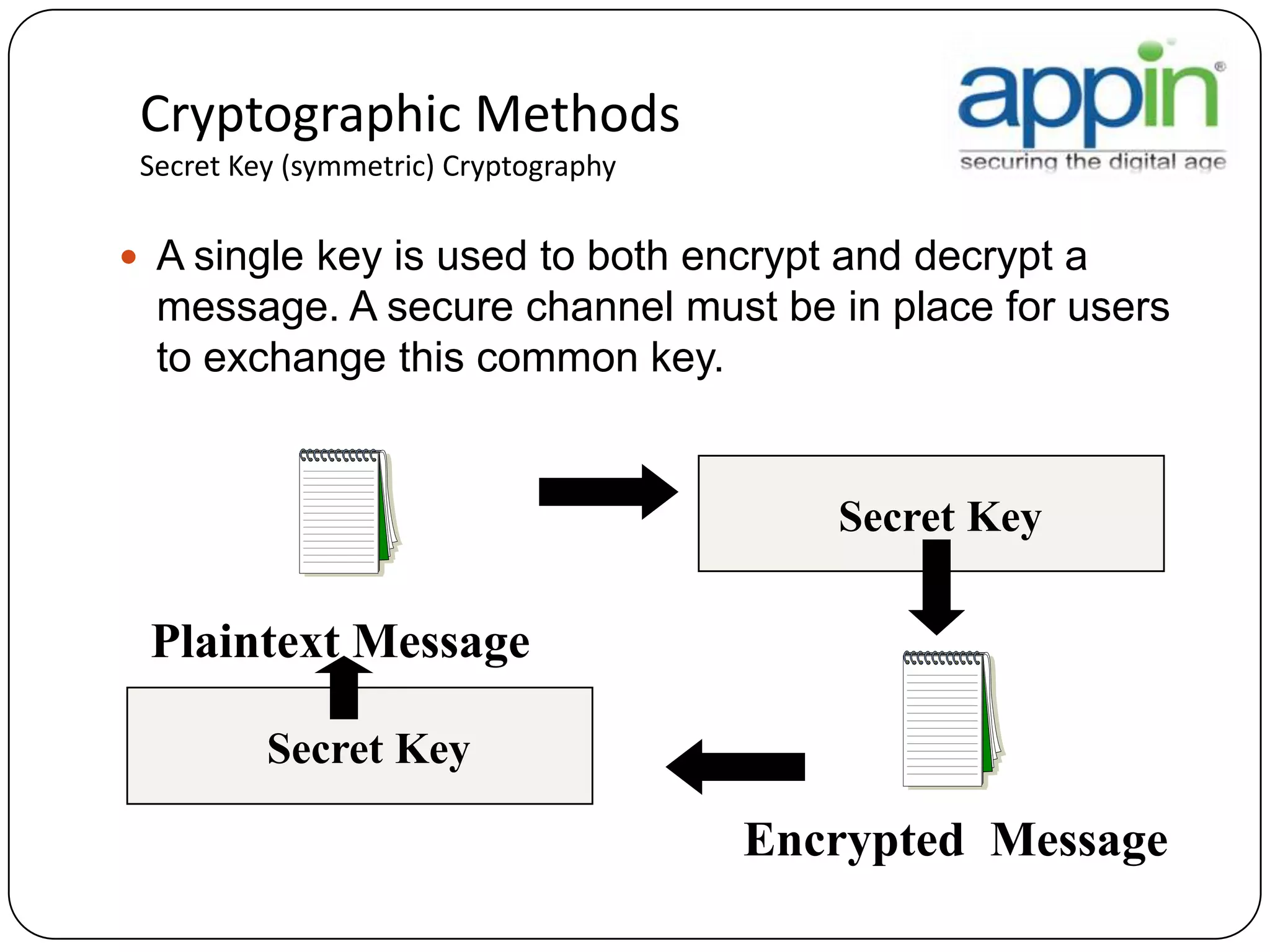
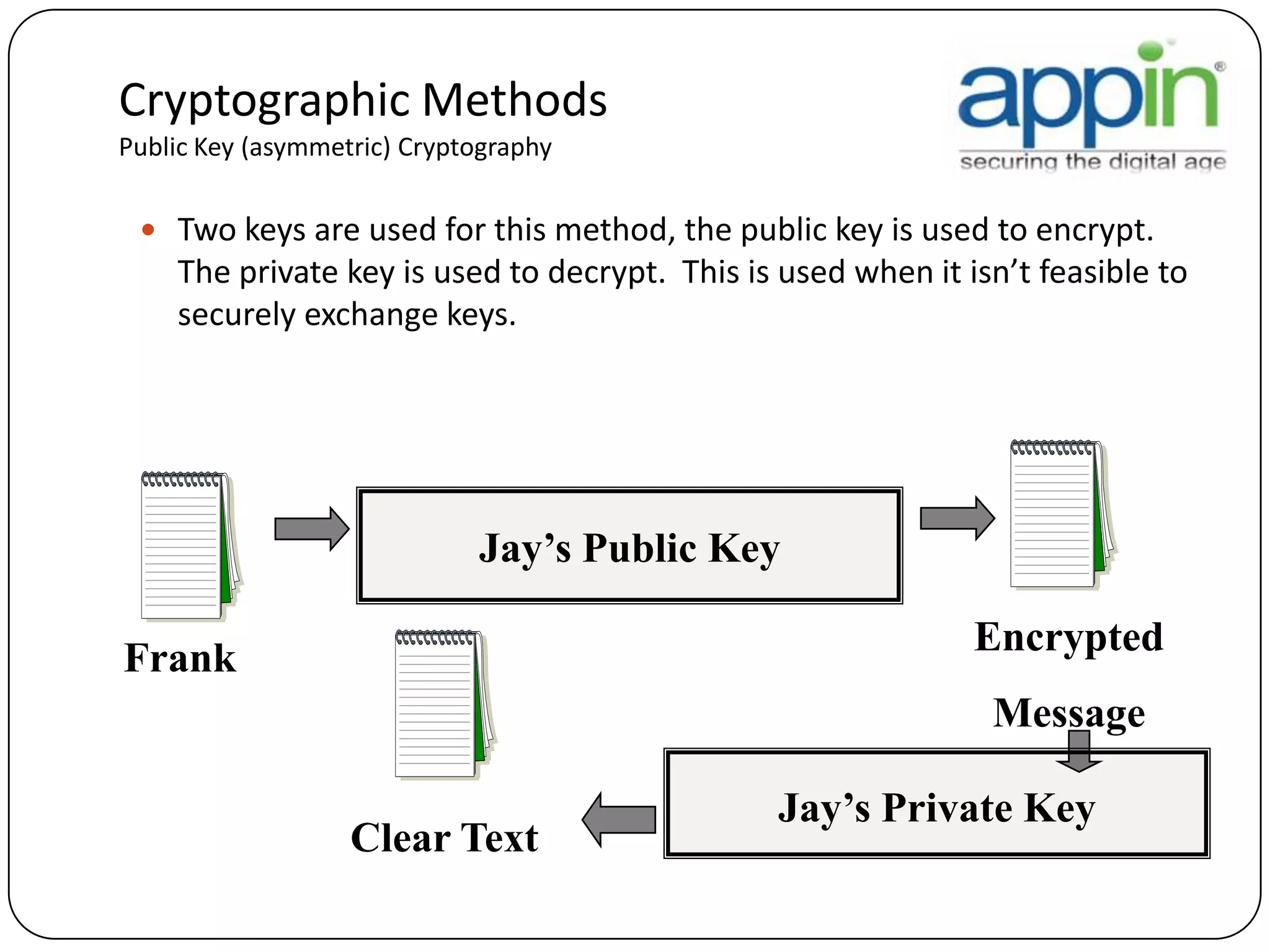
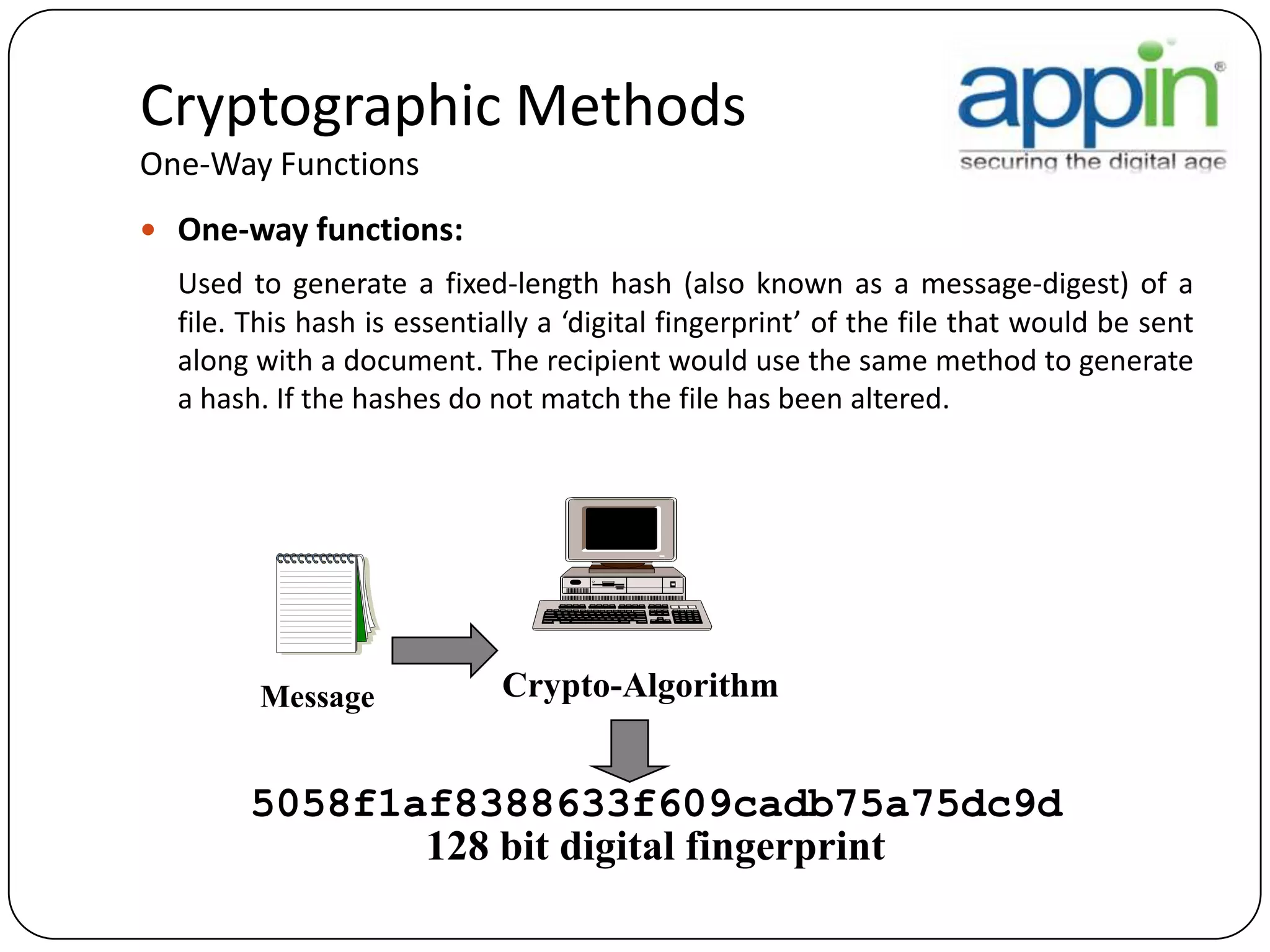
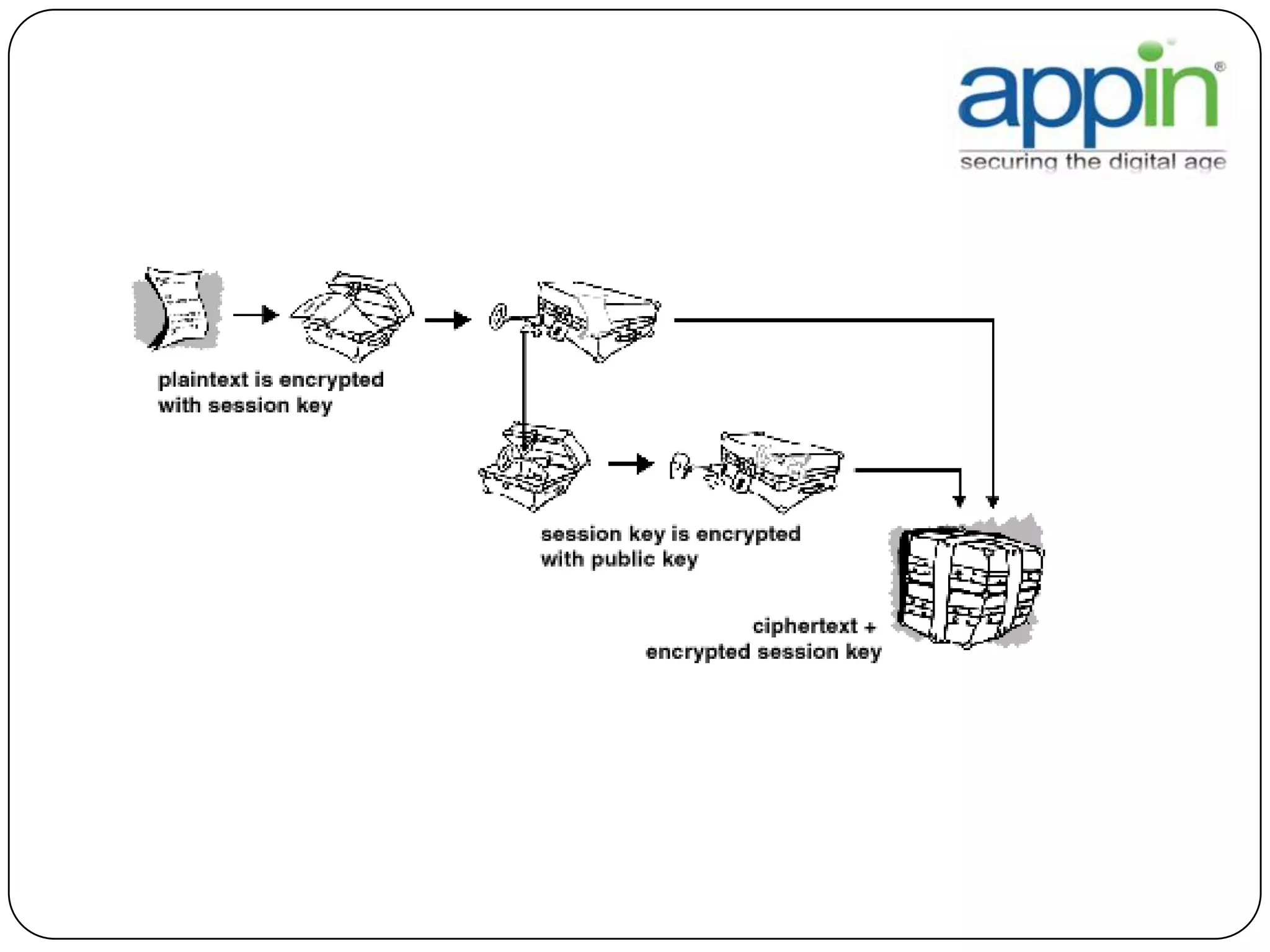
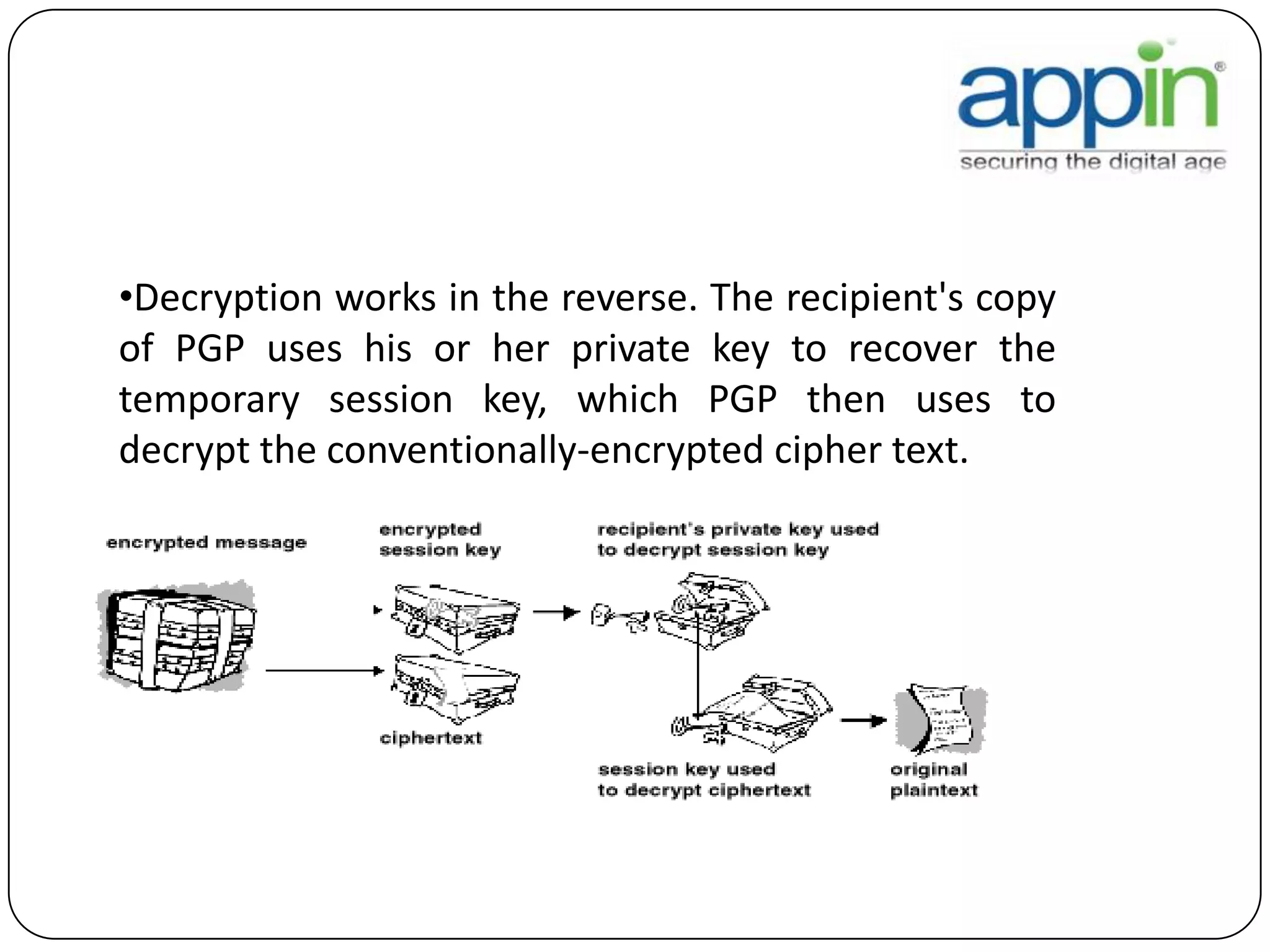
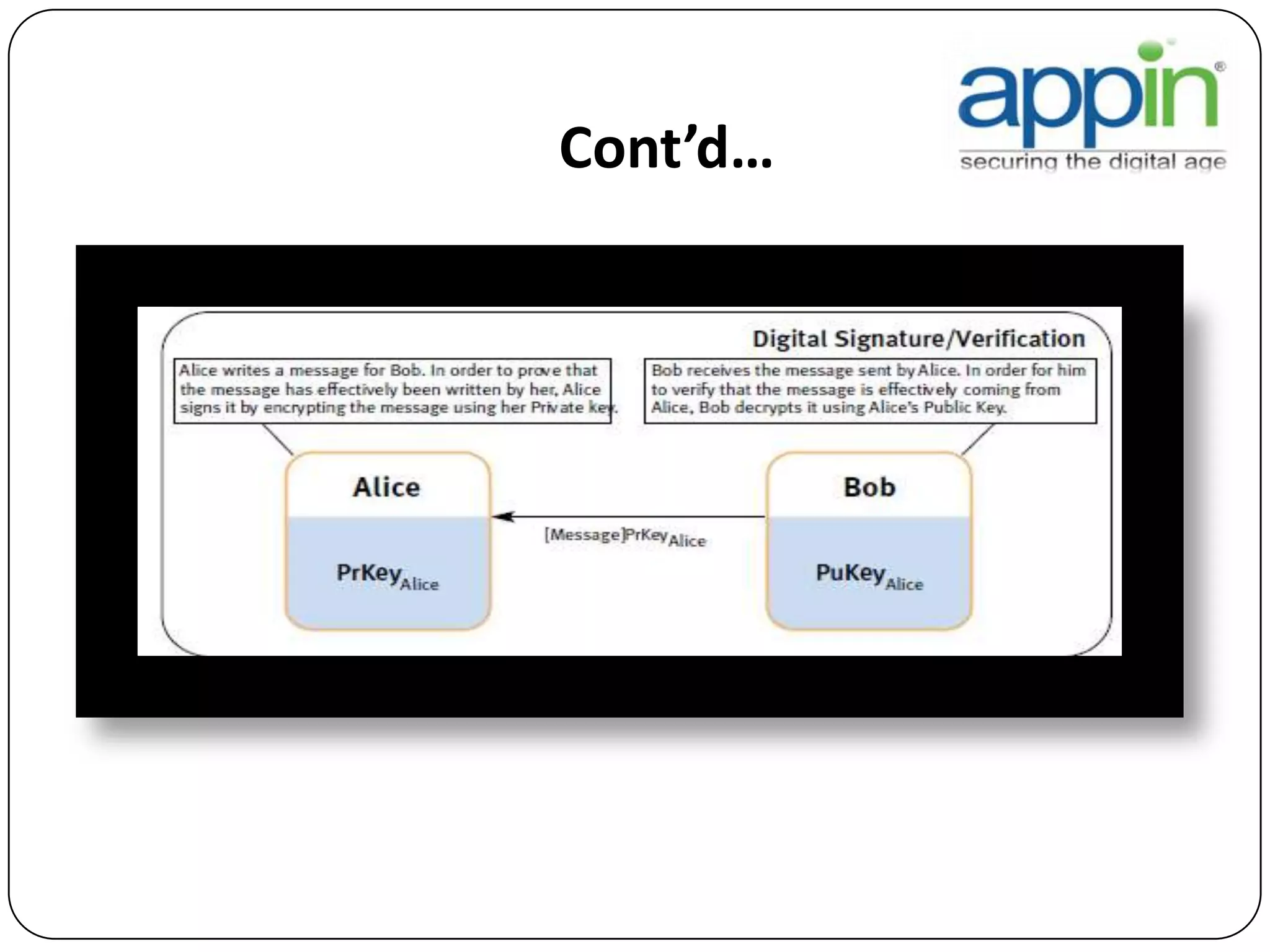
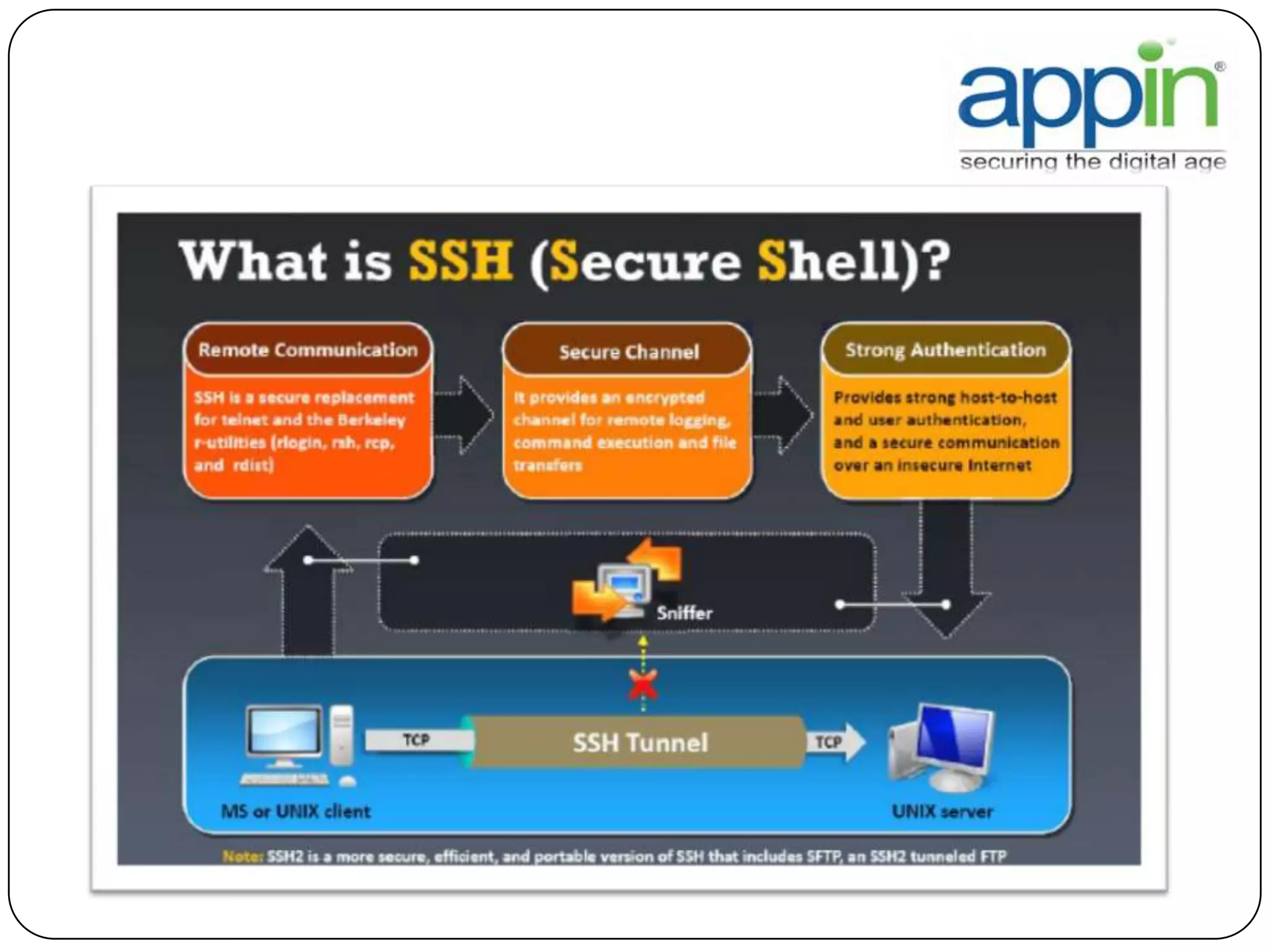
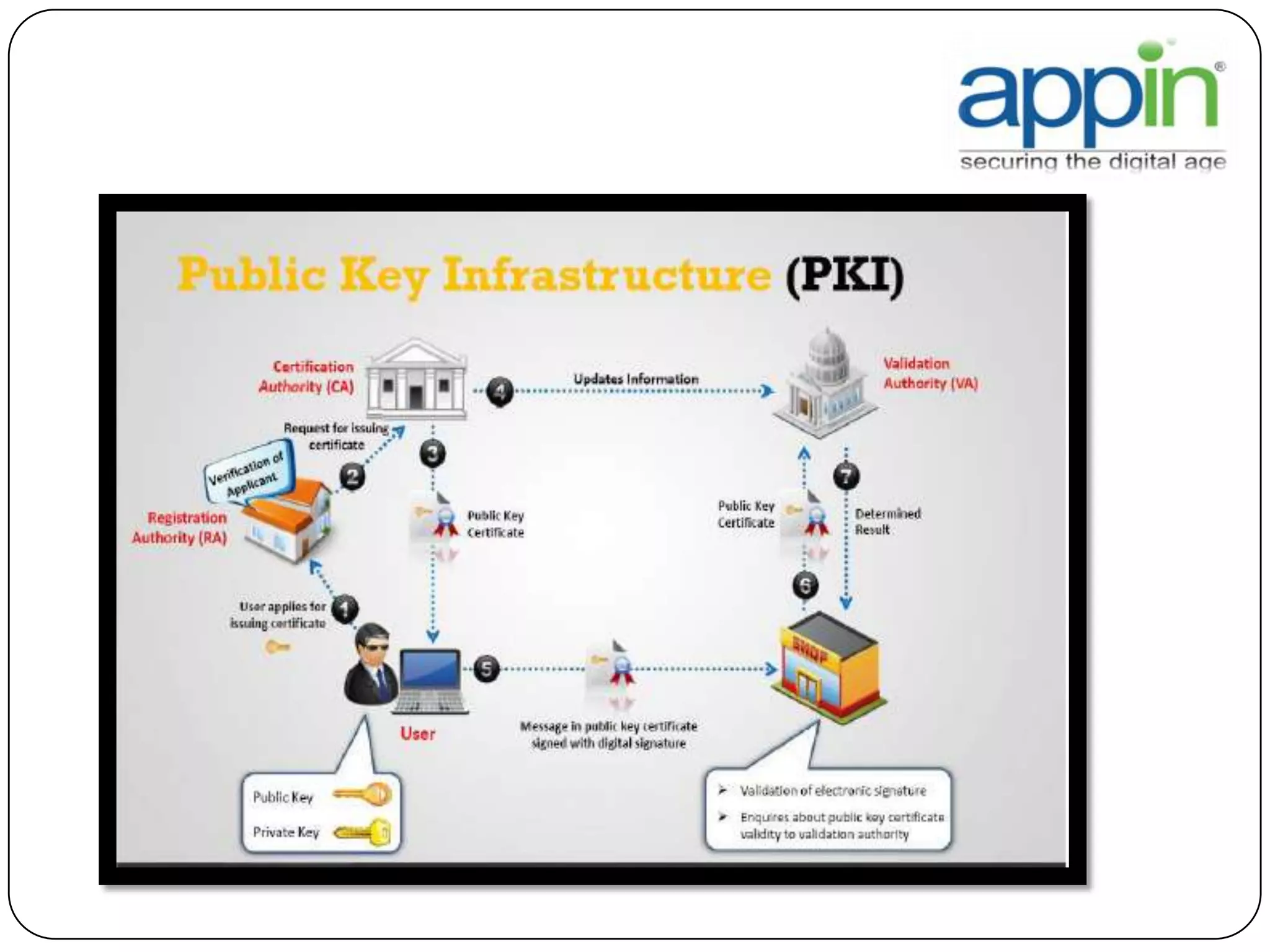
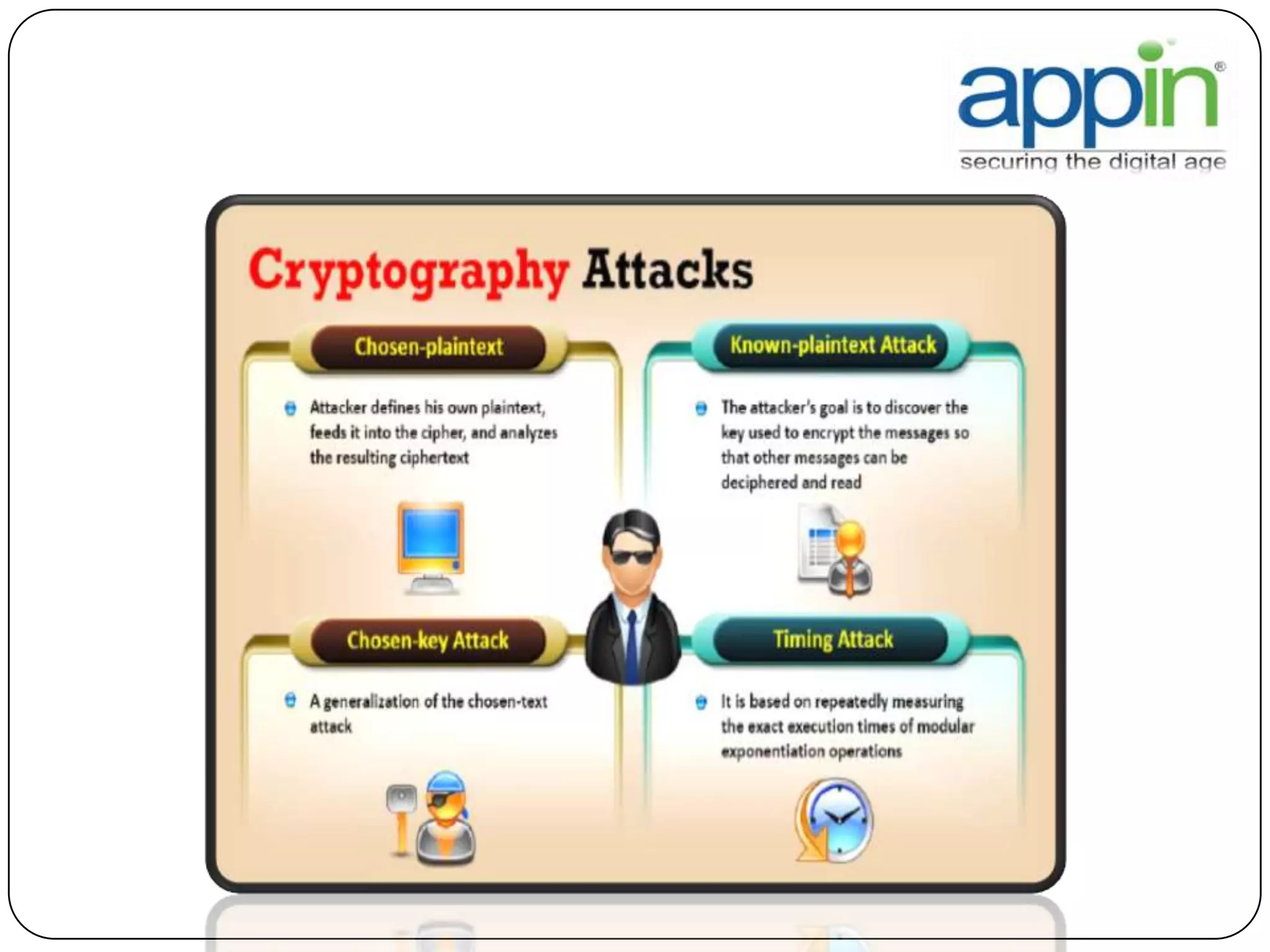
Cryptography is used to securely communicate private information and can be implemented using secret codes, ciphers, one-time pads, and cryptographic methods like symmetric and asymmetric encryption. Pretty Good Privacy (PGP) is an encryption package that uses asymmetric encryption with two keys - a private key and a public key. A message encrypted with the public key can only be decrypted with the corresponding private key, allowing secure communication between parties. PGP first compresses, encrypts with a randomly generated session key, and then encrypts the session key with the recipient's public key to securely transmit an encrypted message.