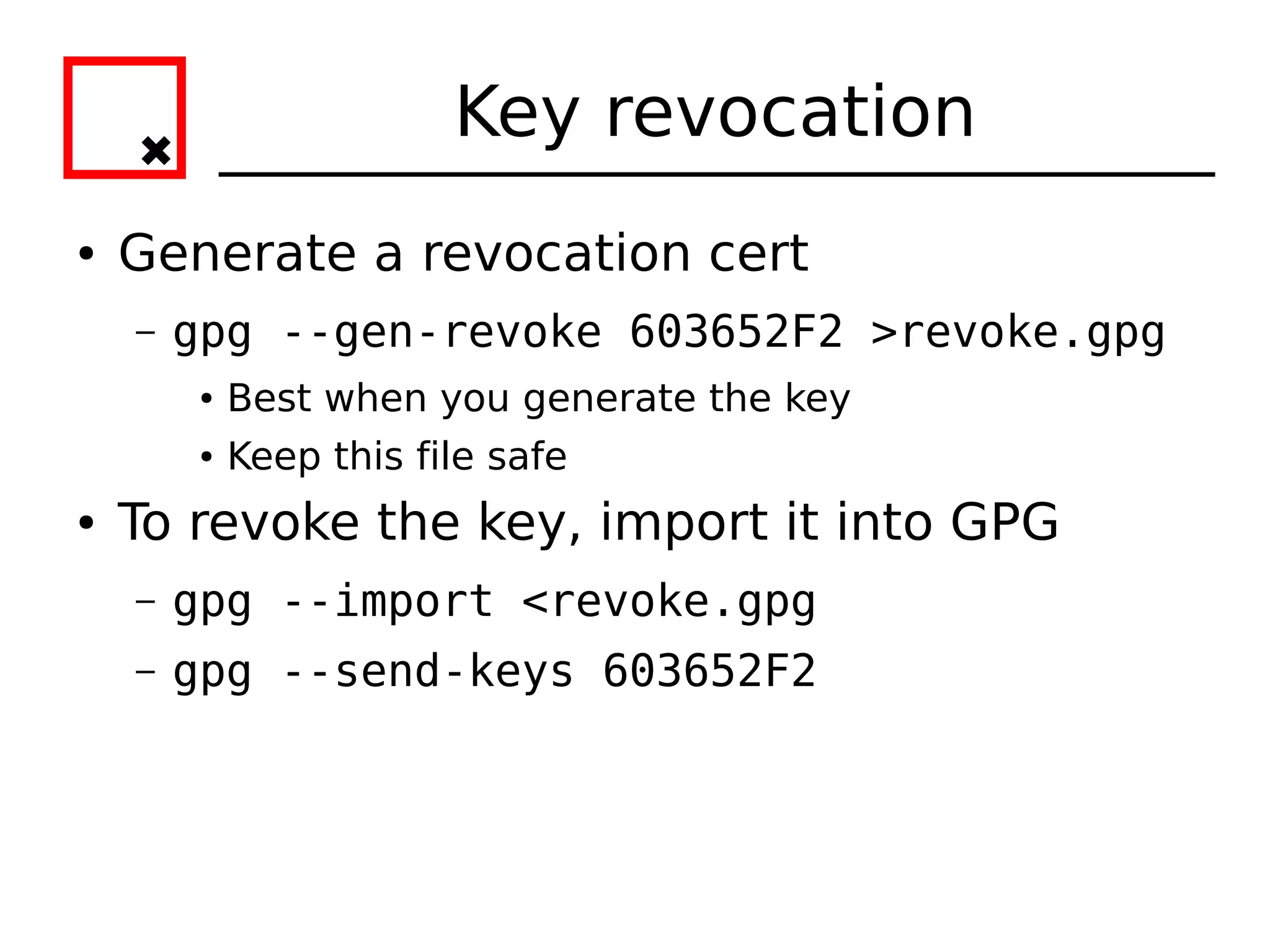
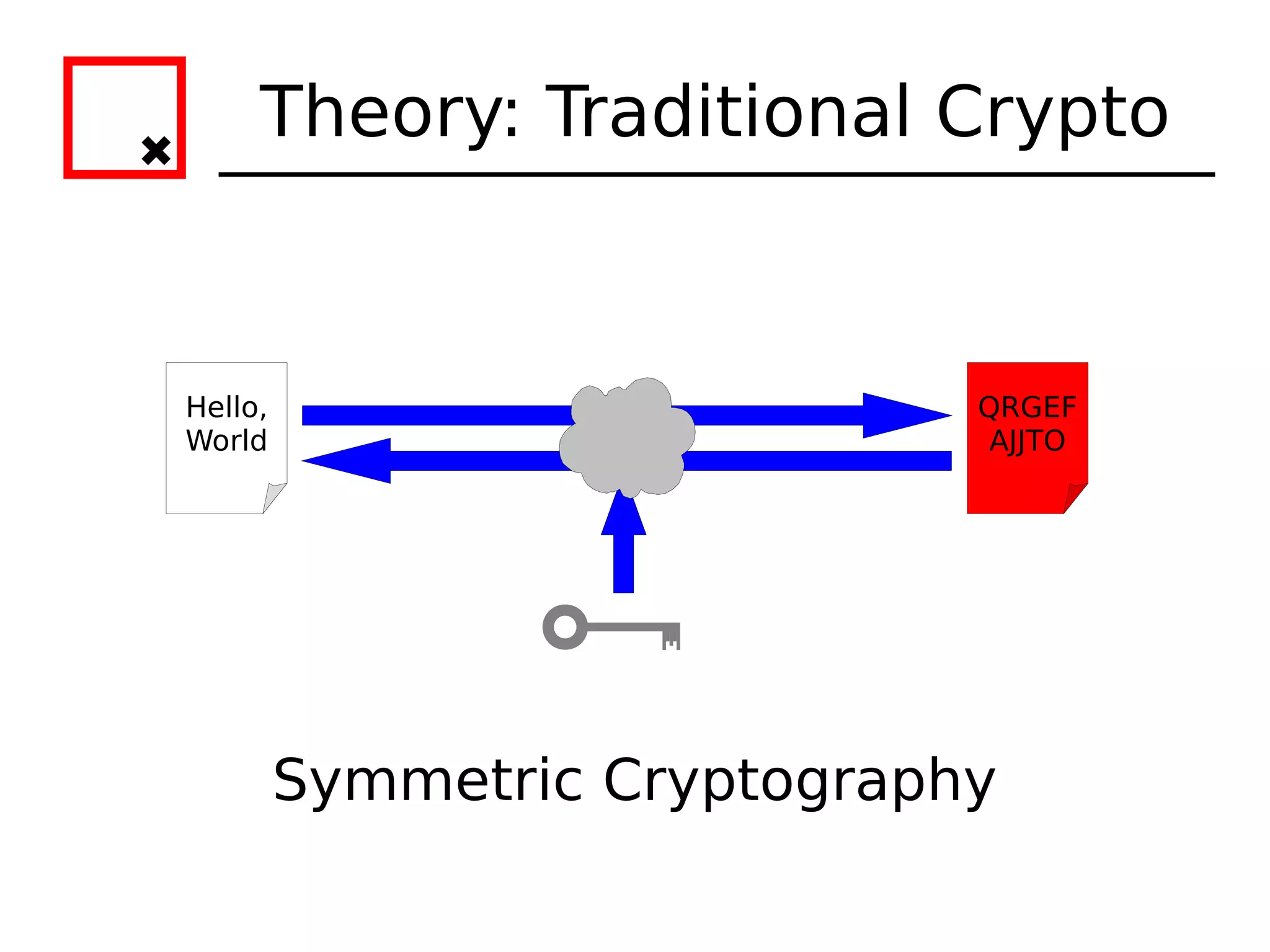
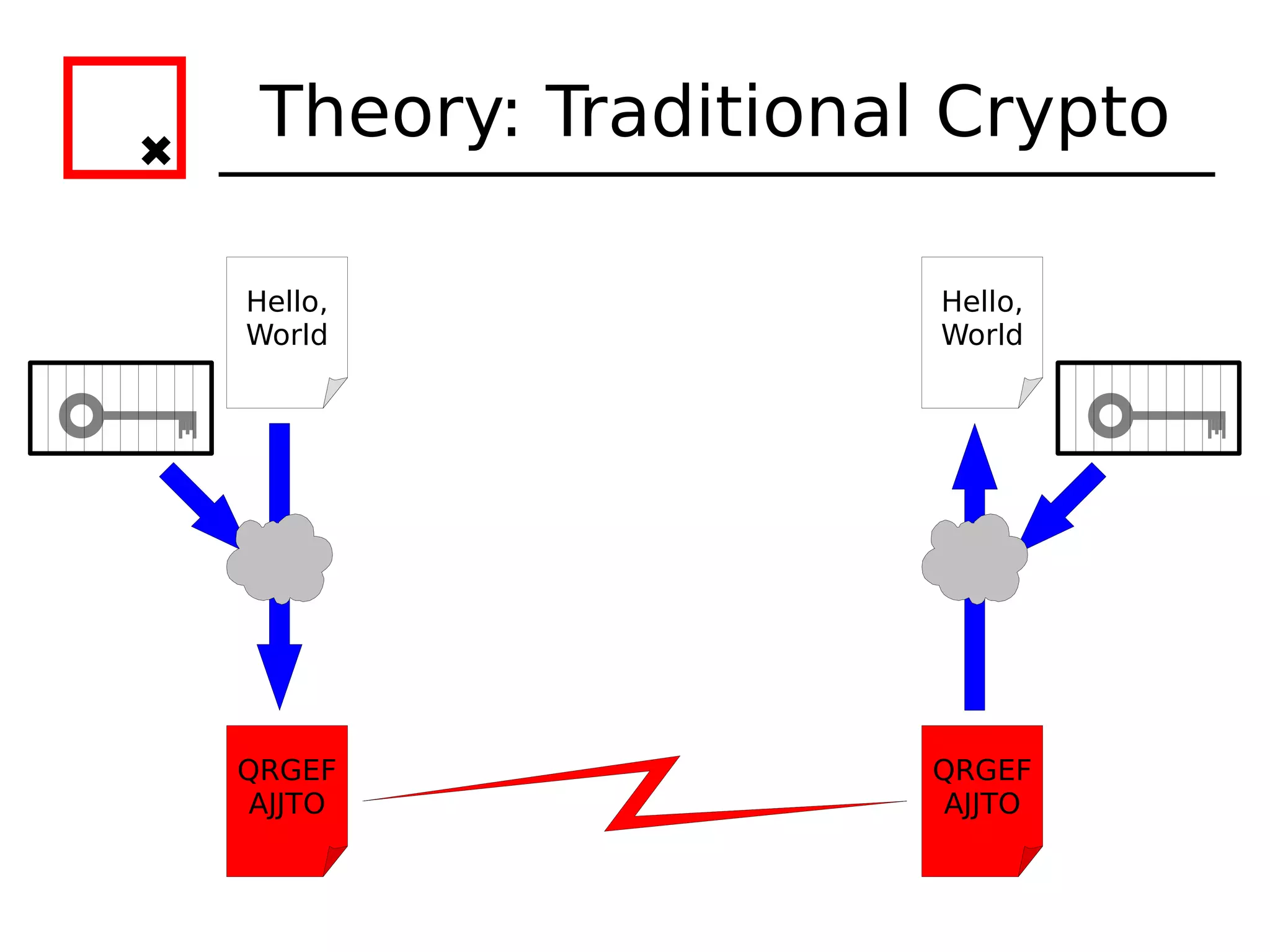
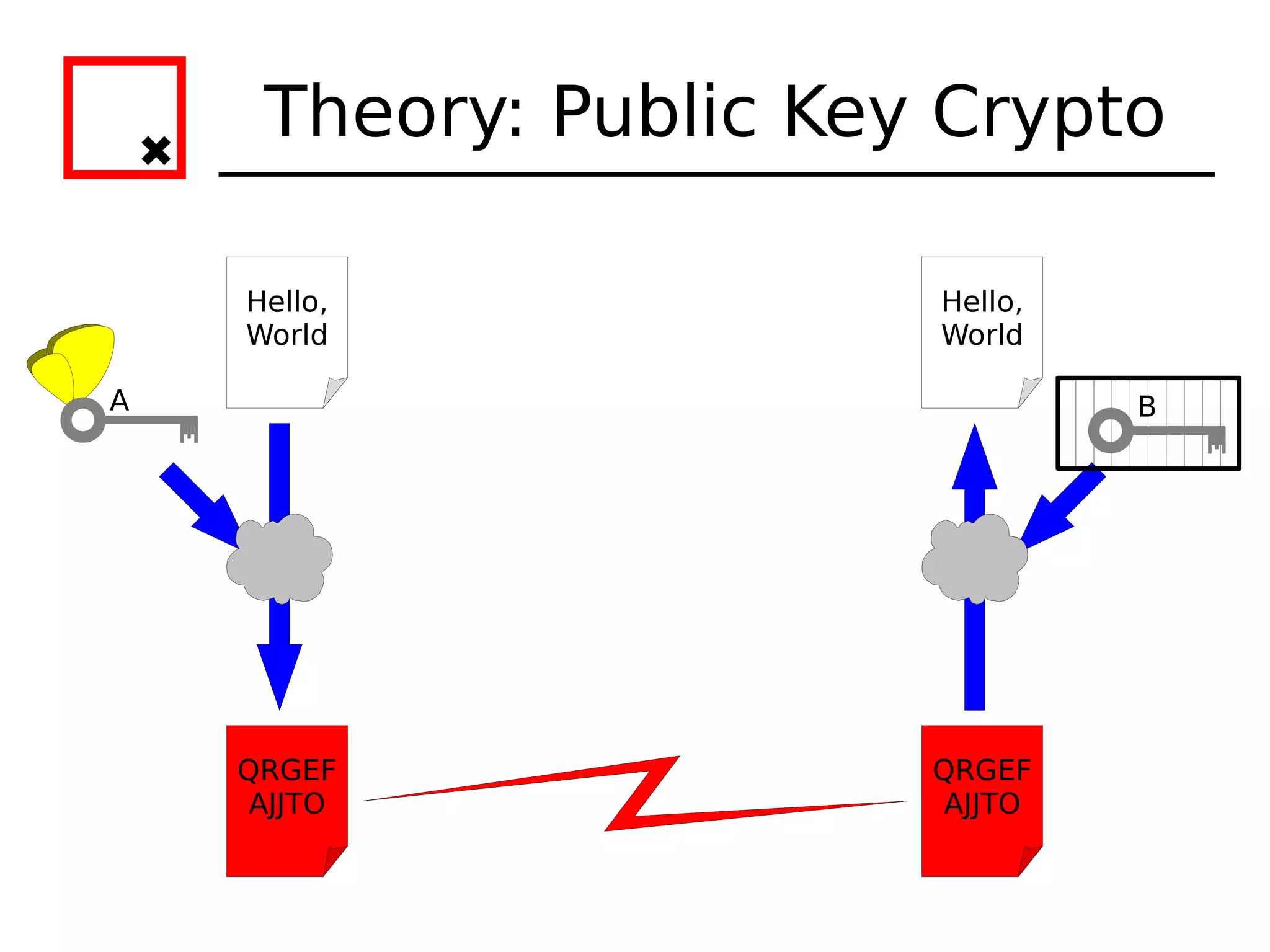
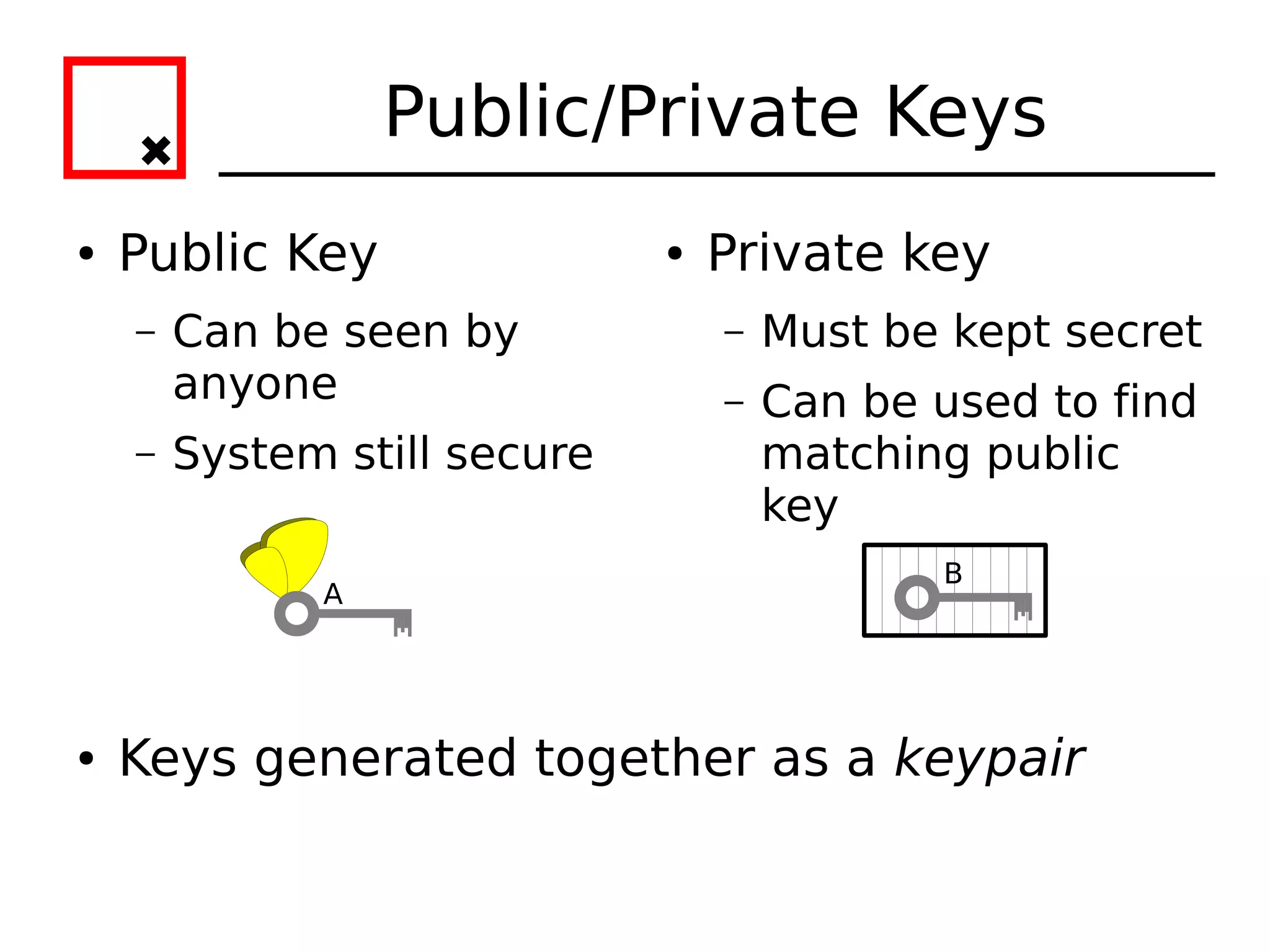
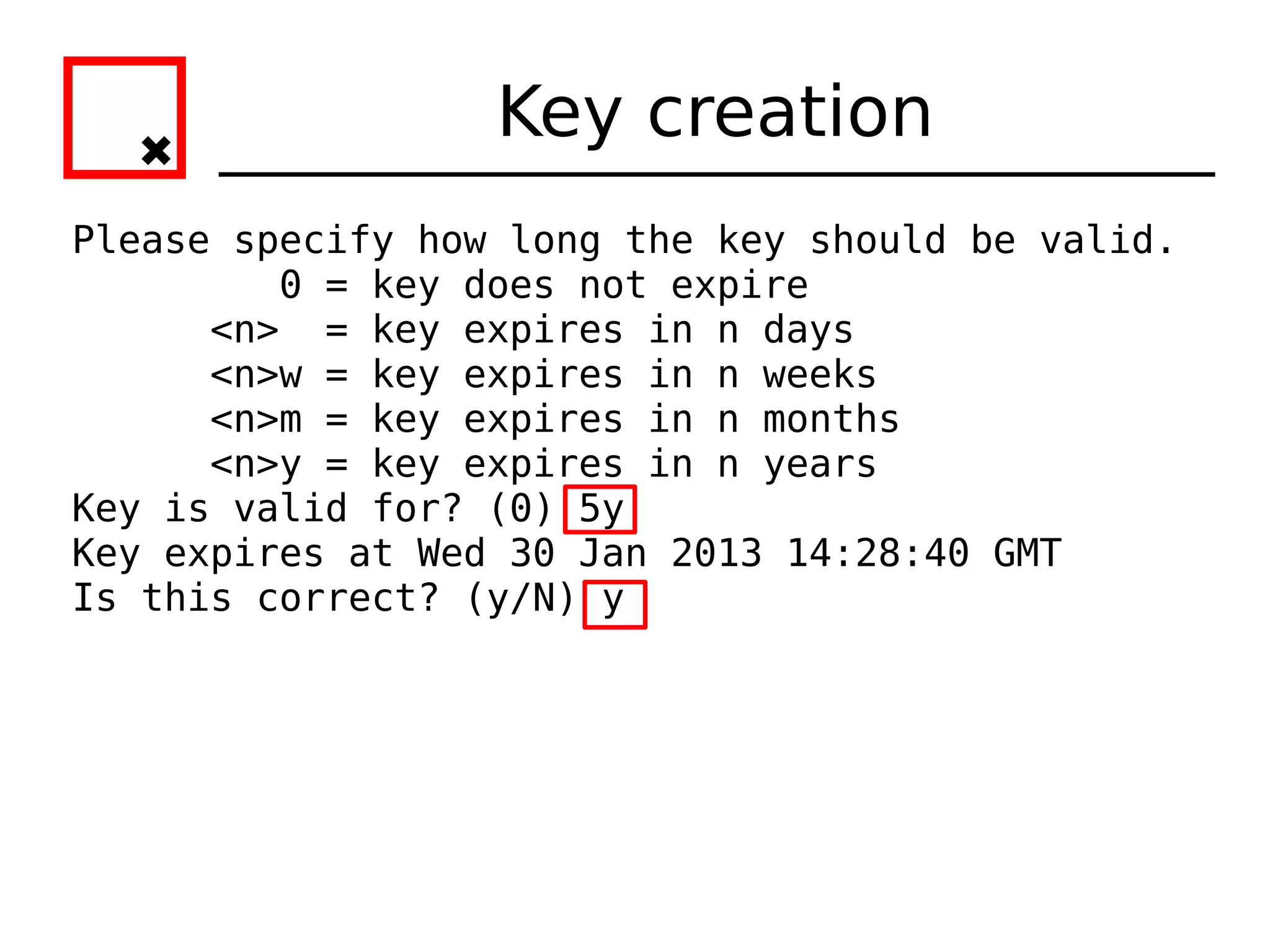
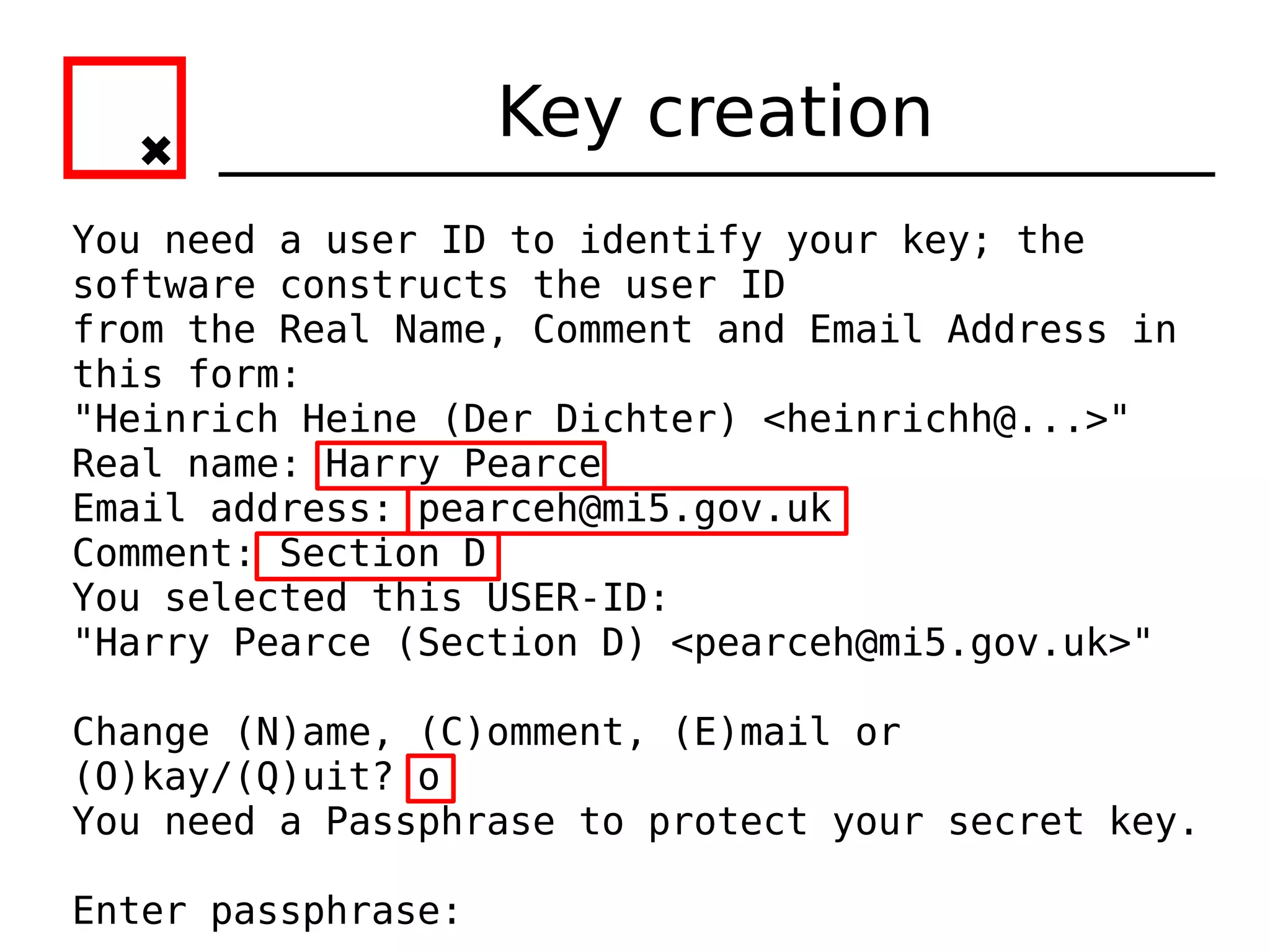
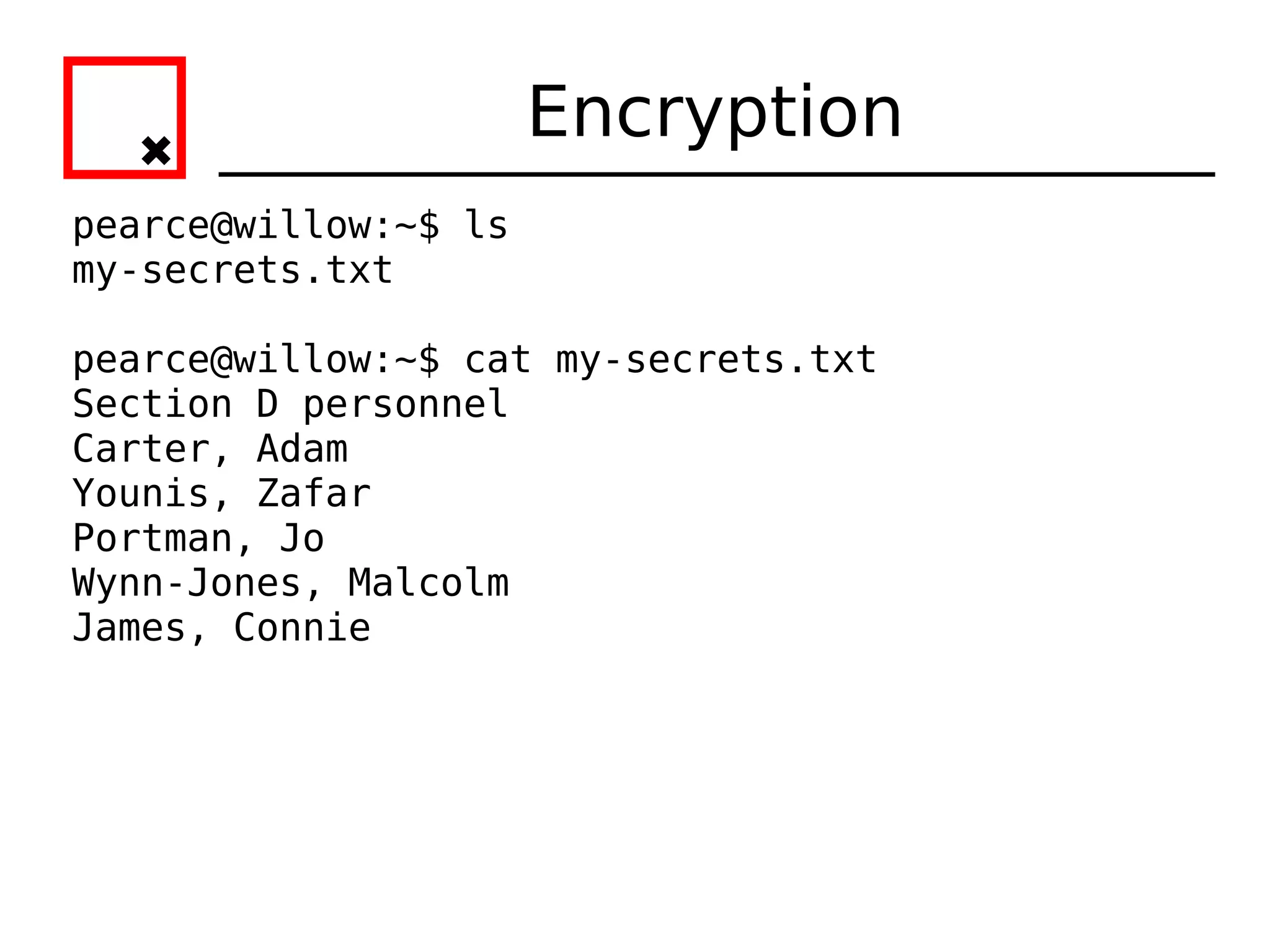
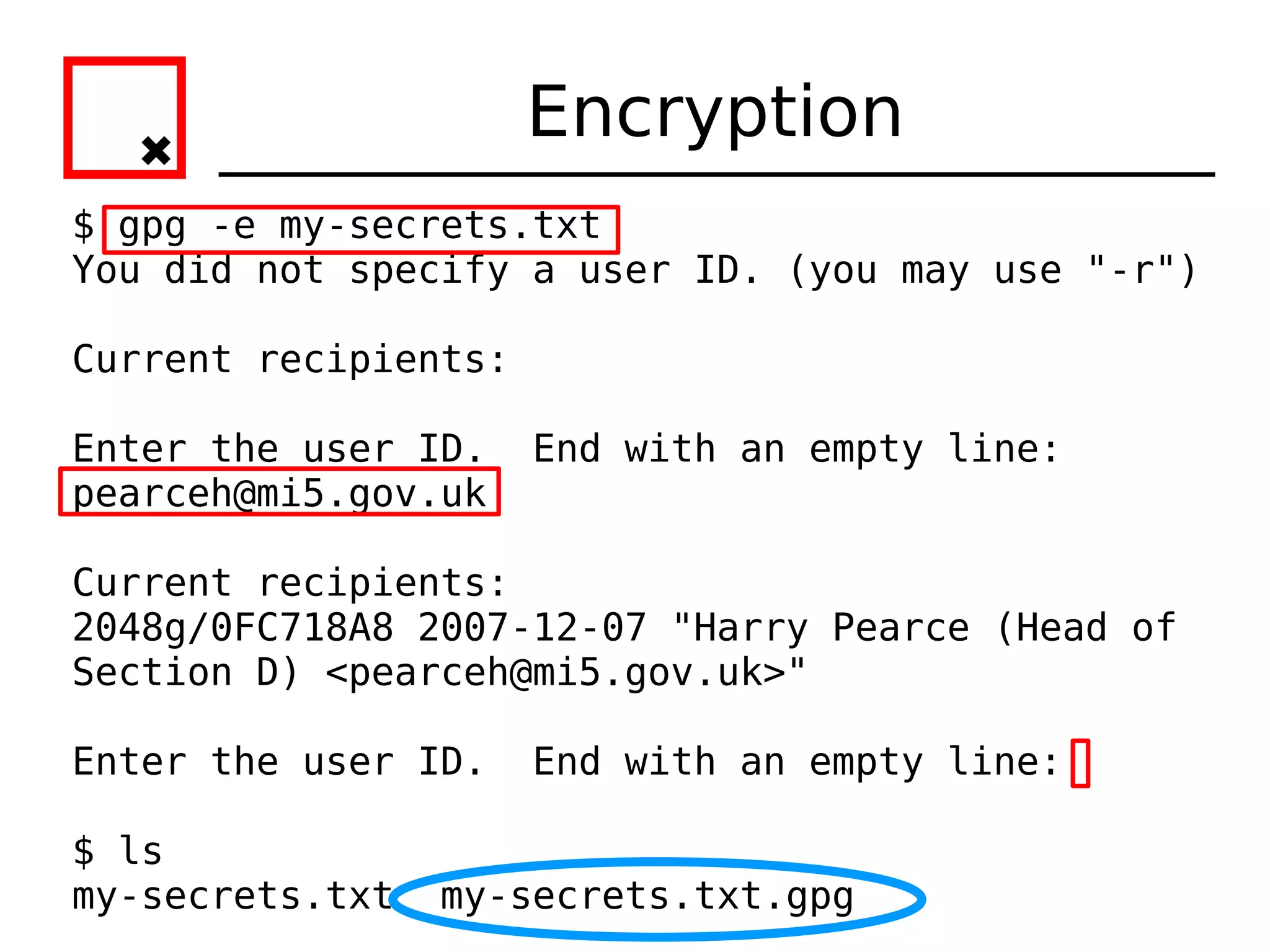
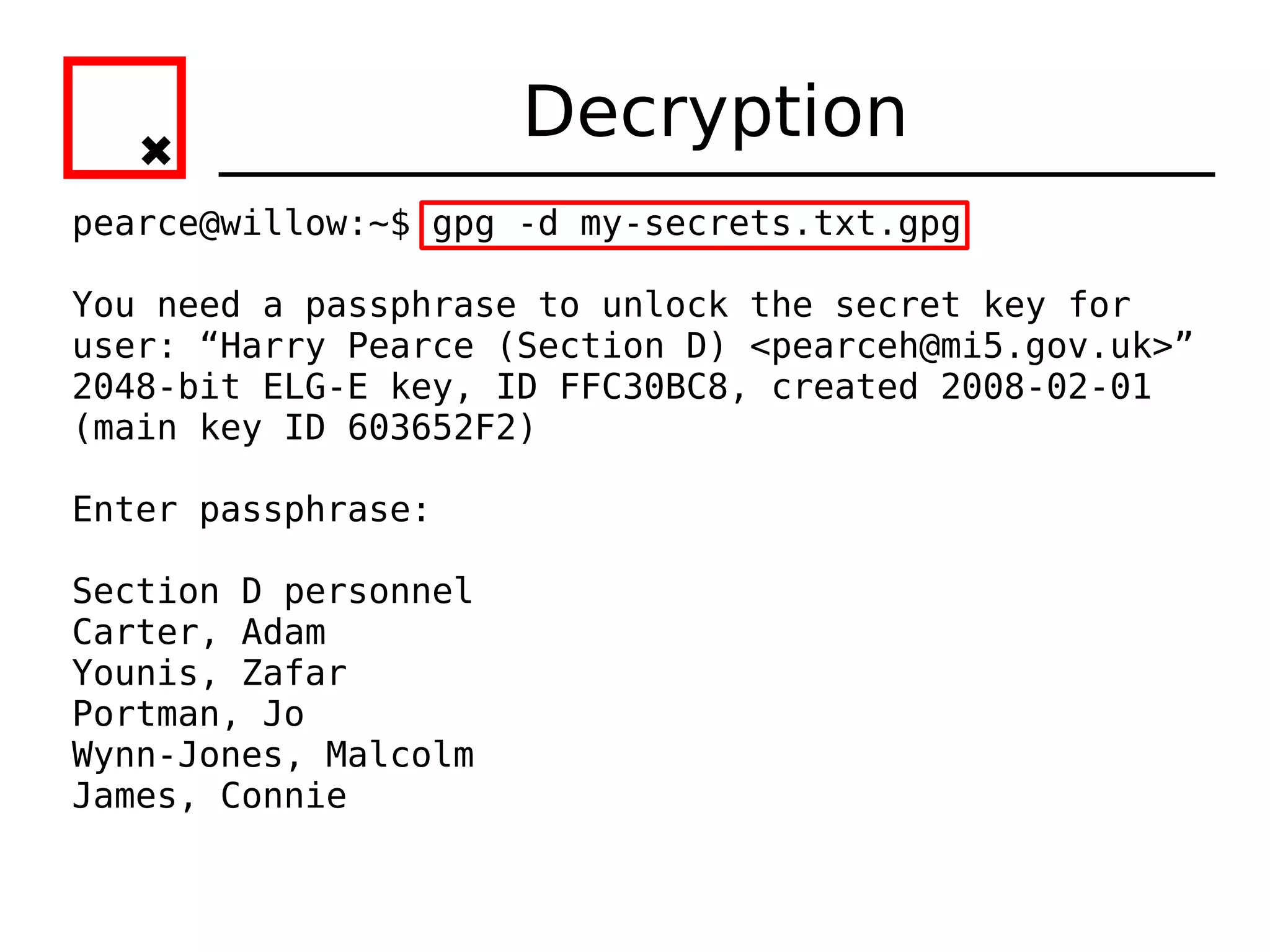
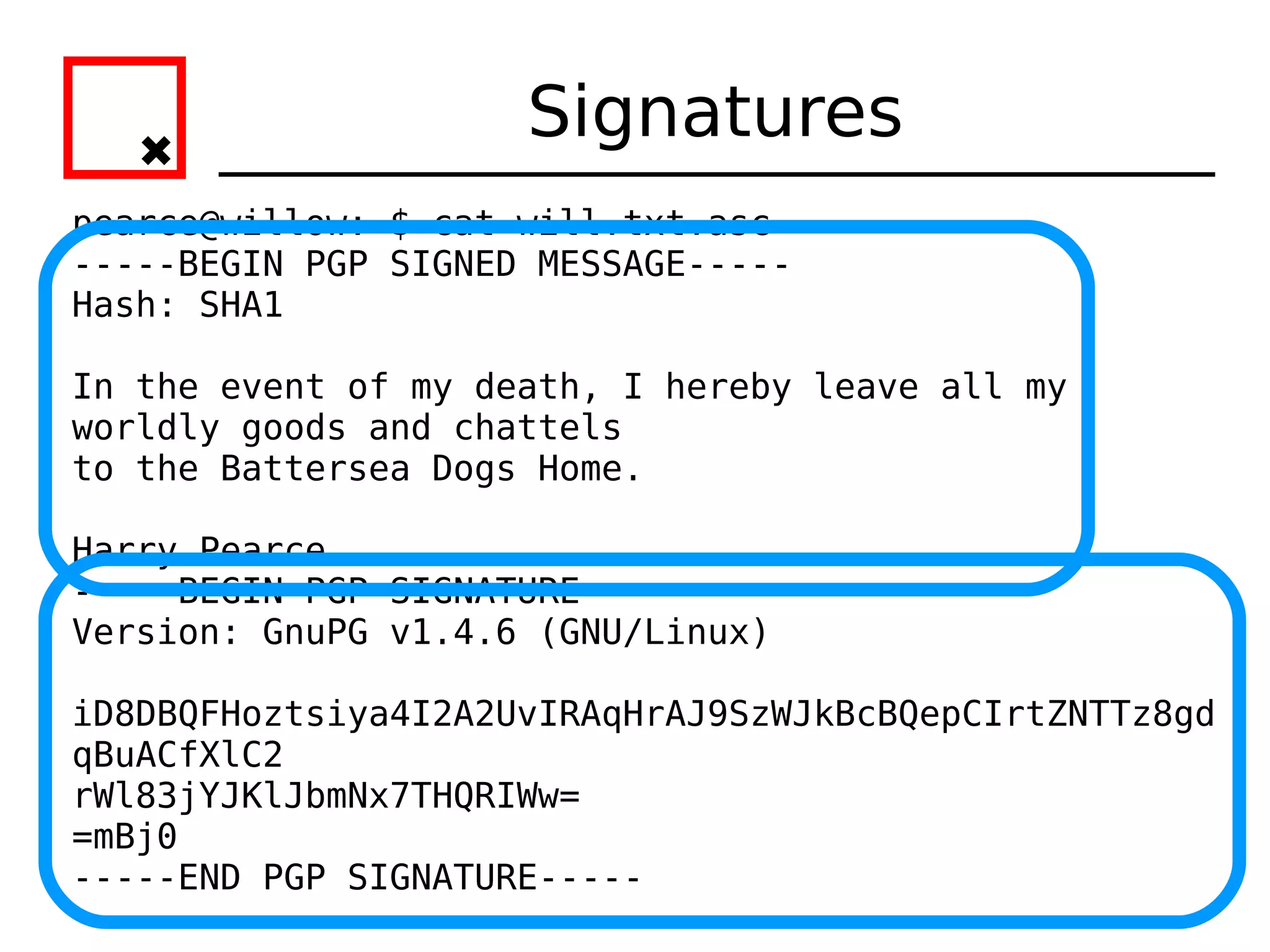
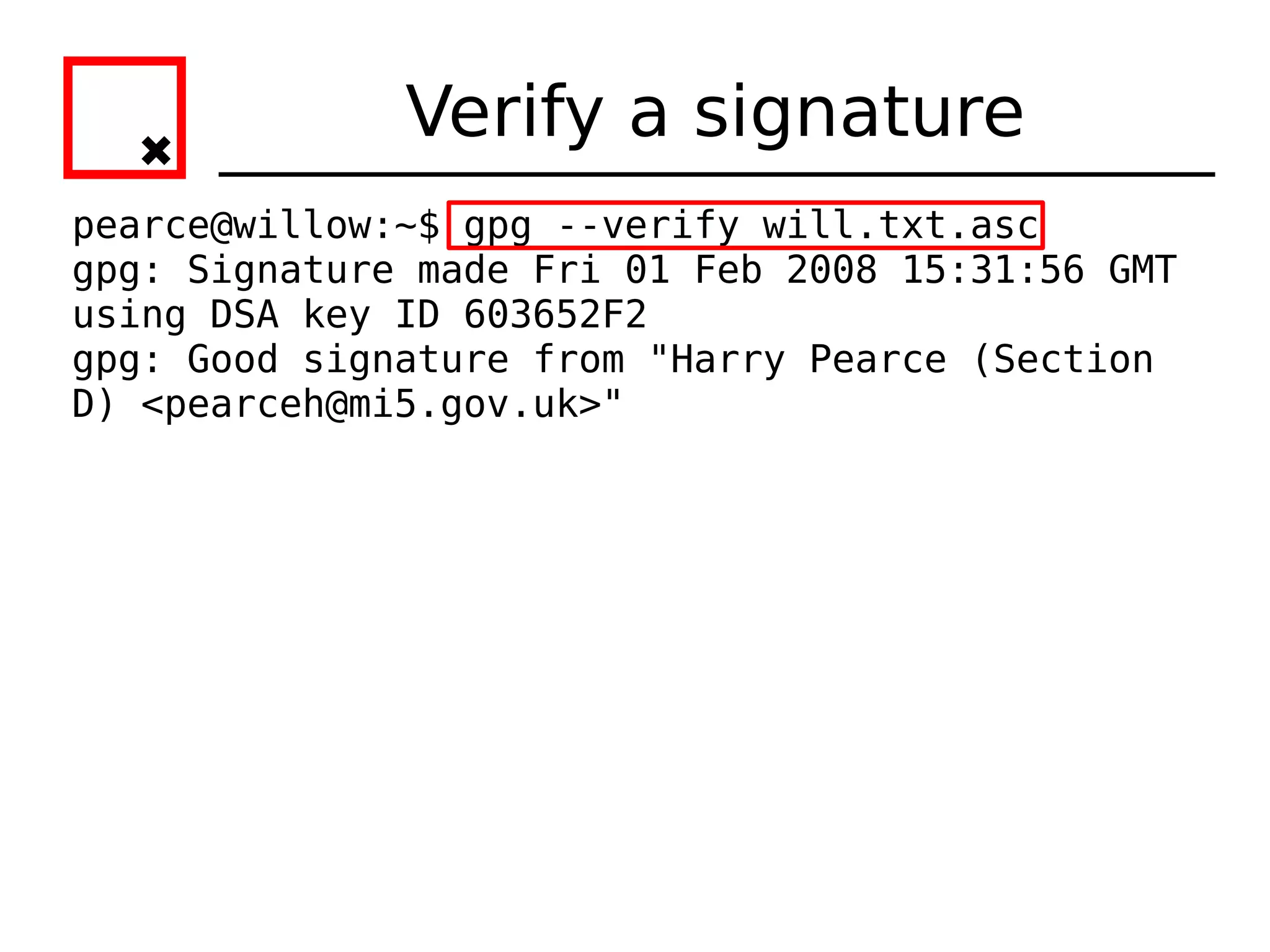
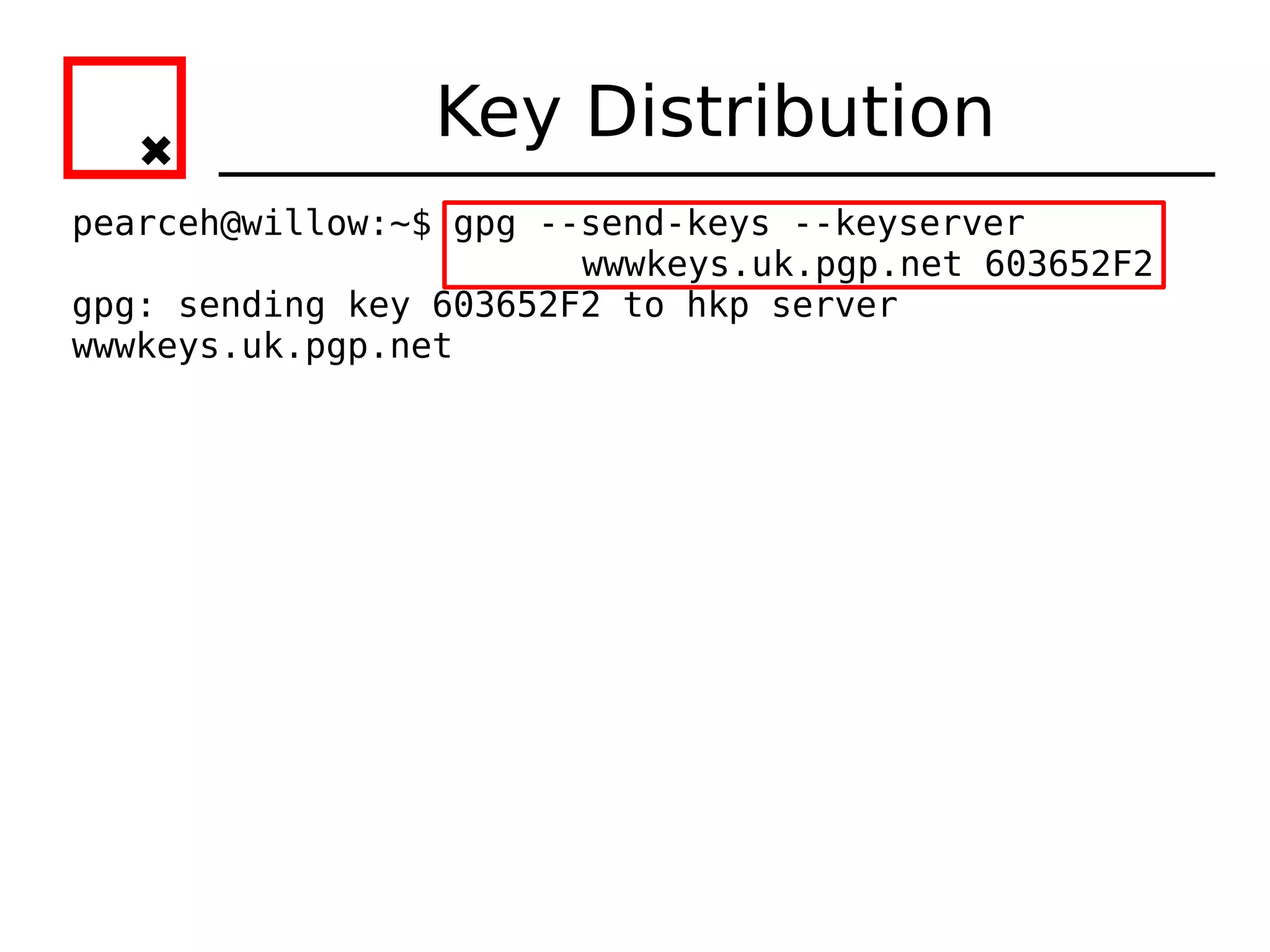
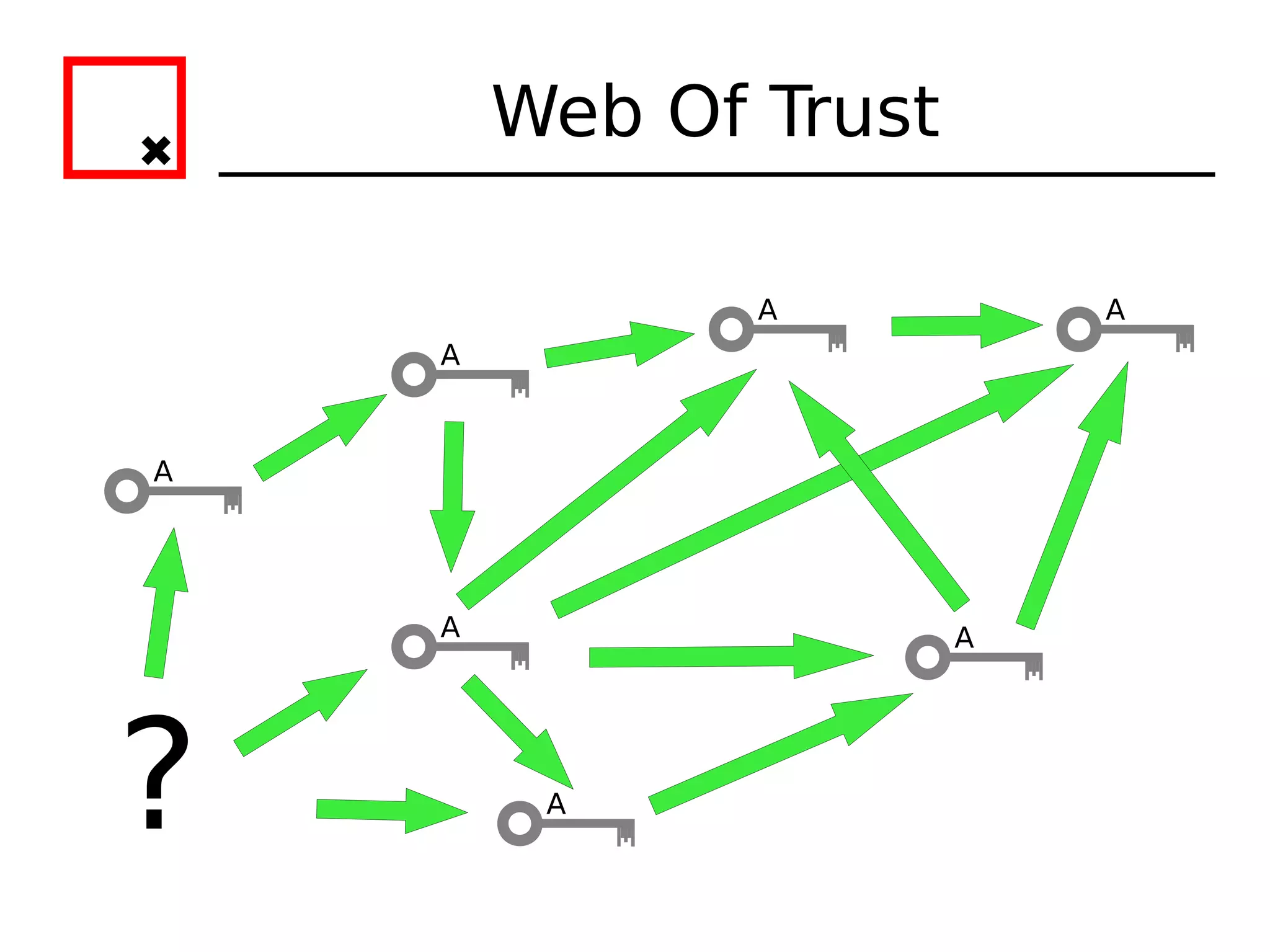
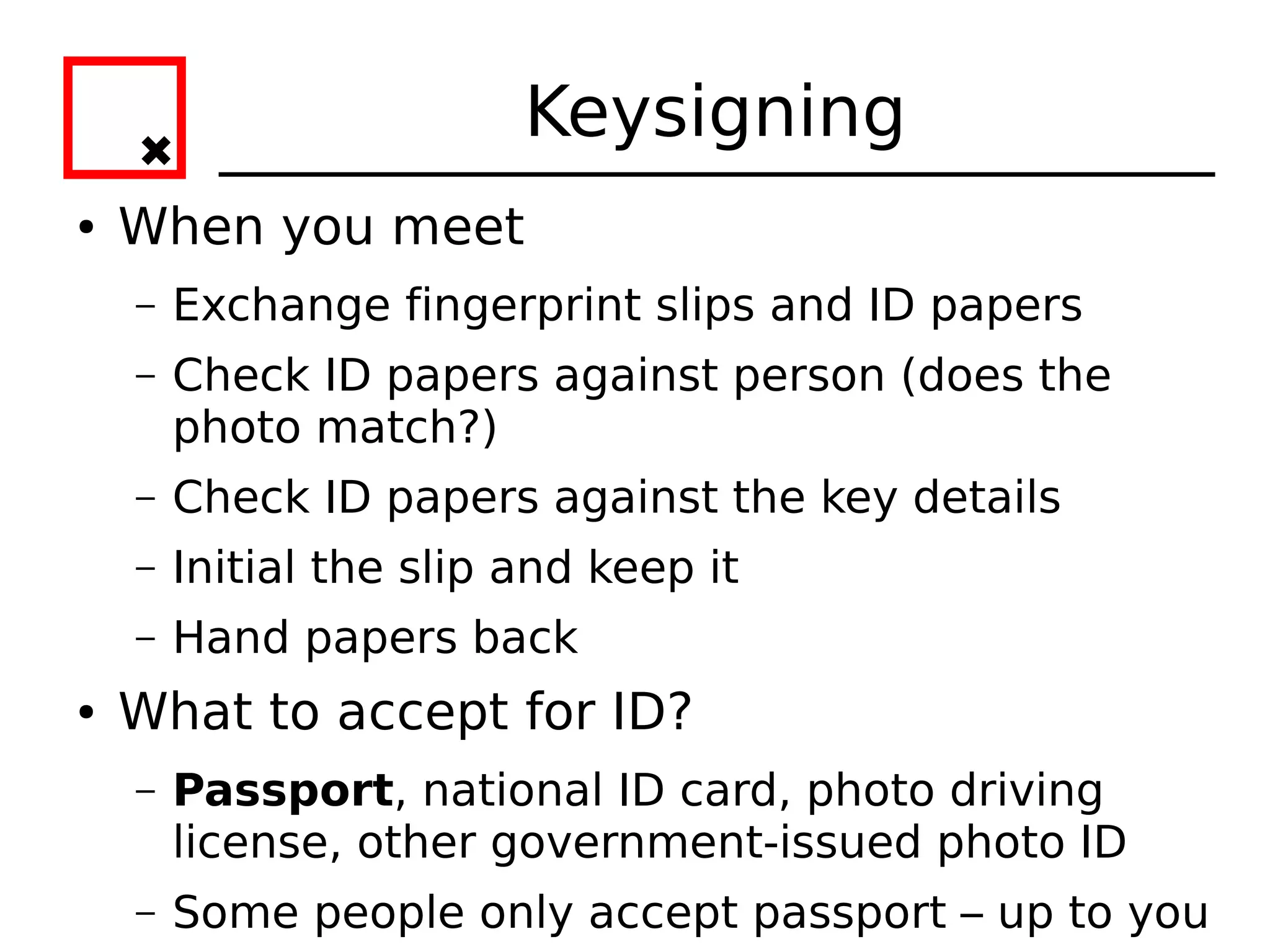
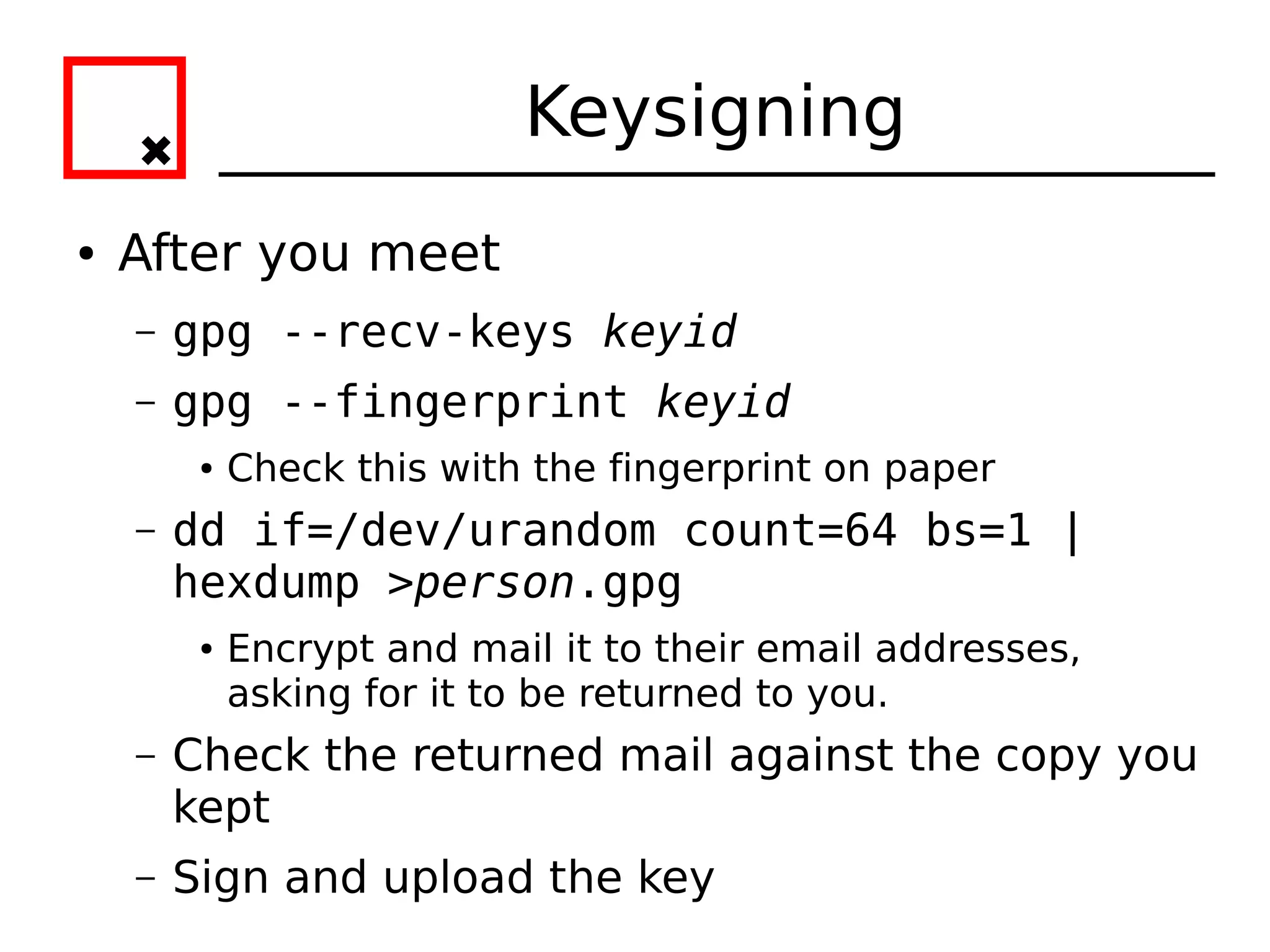
The document provides an overview of practical cryptography and the GPG/PGP encryption tools. It discusses symmetric and public key cryptography theory. It then demonstrates how to use GPG/PGP to generate keys, encrypt and decrypt files, digitally sign documents, verify signatures, and distribute public keys through a key server. It also discusses how the web of trust model works to validate identities through in-person key signing after carefully verifying a user's identity.






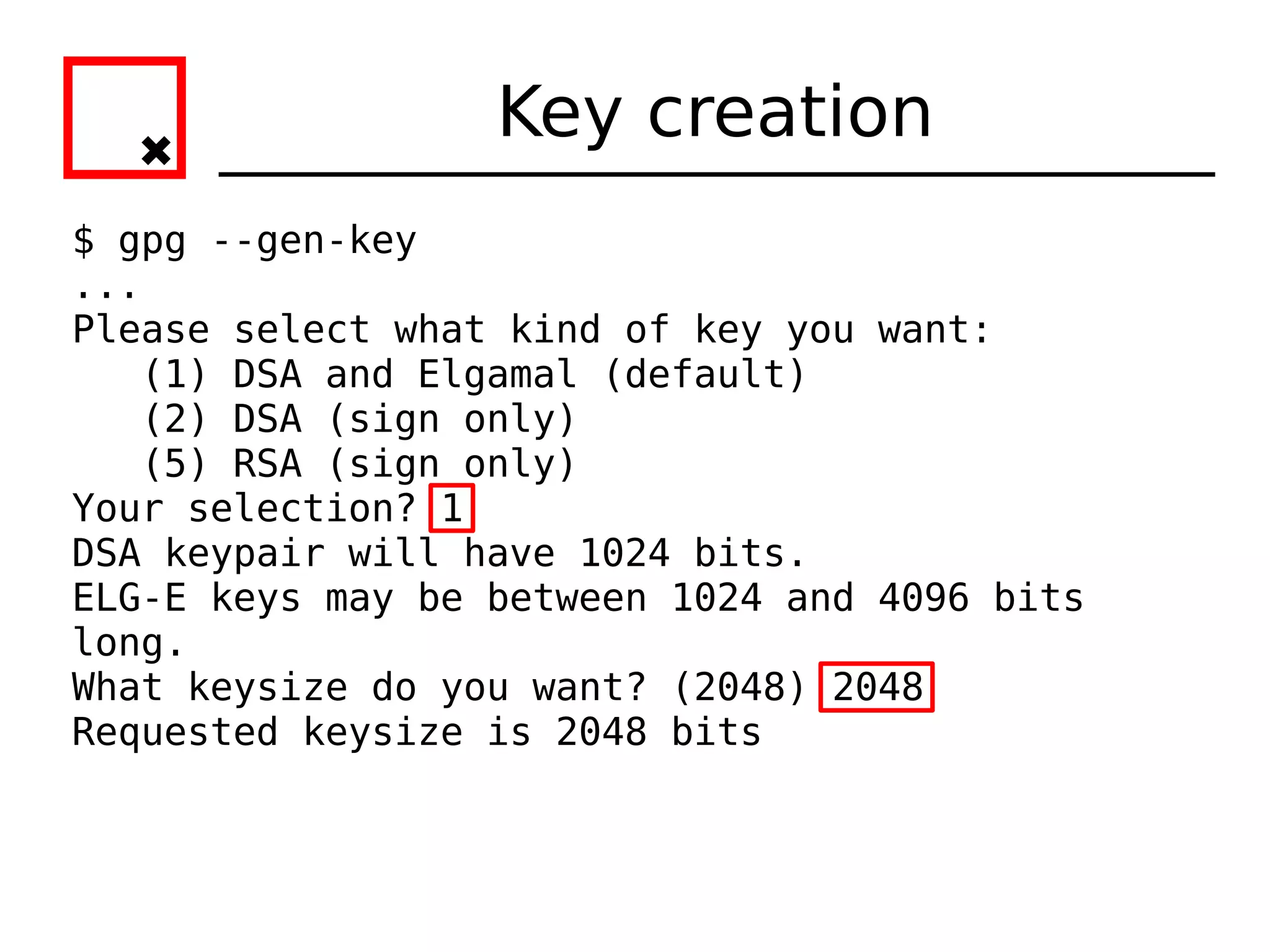
![Key creation
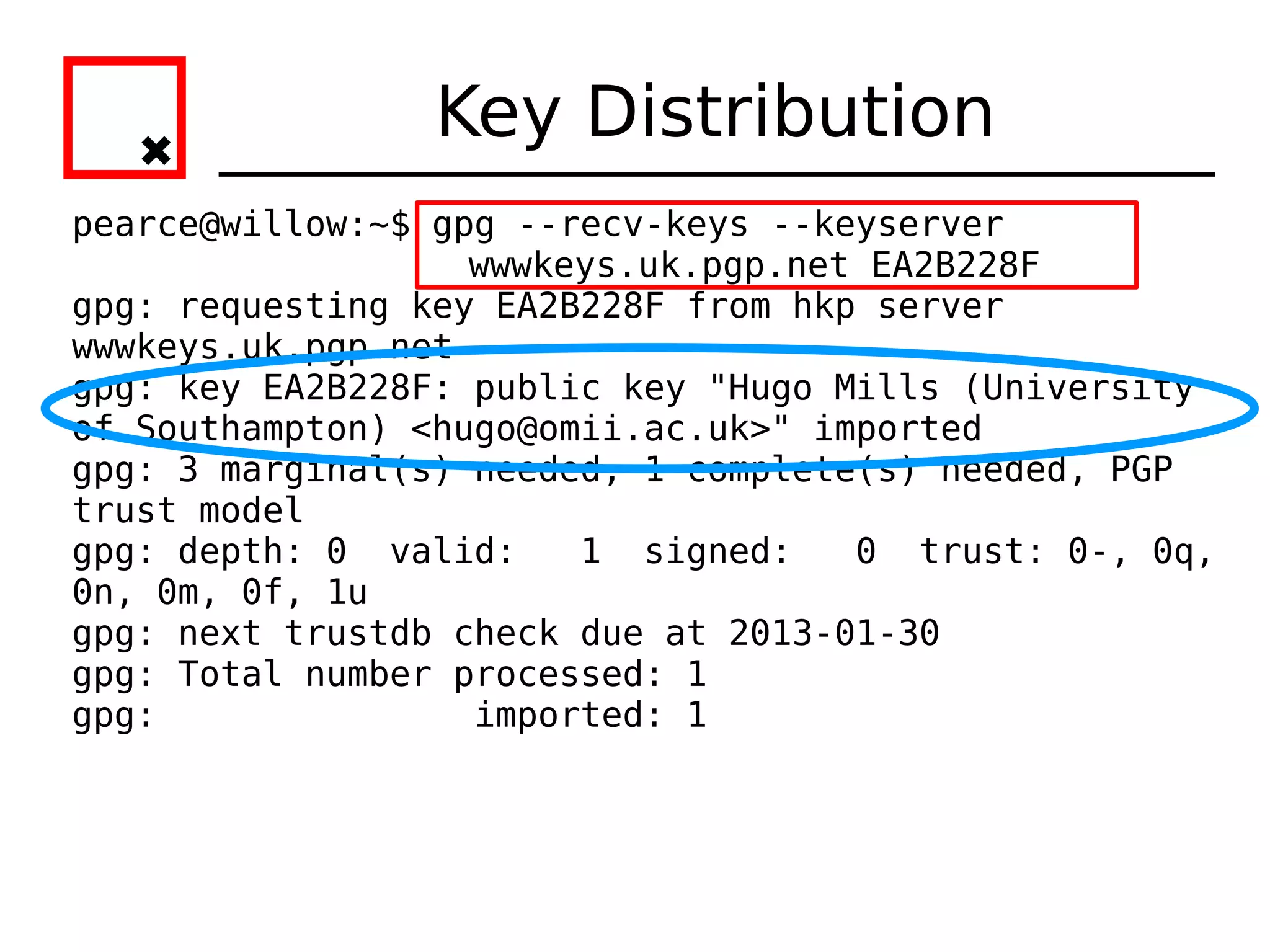
gpg: key 603652F2 marked as ultimately trusted
public and secret key created and signed.
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1u
gpg: next trustdb check due at 2013-01-30
pub 1024D/603652F2 2008-02-01 [expires: 2013-01-30]
Key fingerprint = 628B 640D A7A6 4F98 D746 E355 8B26 B823 6036 52F2
uid Harry Pearce (Head of Section D) <pearceh@mi5.gov.uk>
sub 2048g/FFC30BC8 2008-02-01 [expires: 2013-01-30]
All done, keypair created.](https://image.slidesharecdn.com/crypto-hlug-120704204314-phpapp01/75/Crypto-hlug-18-2048.jpg)




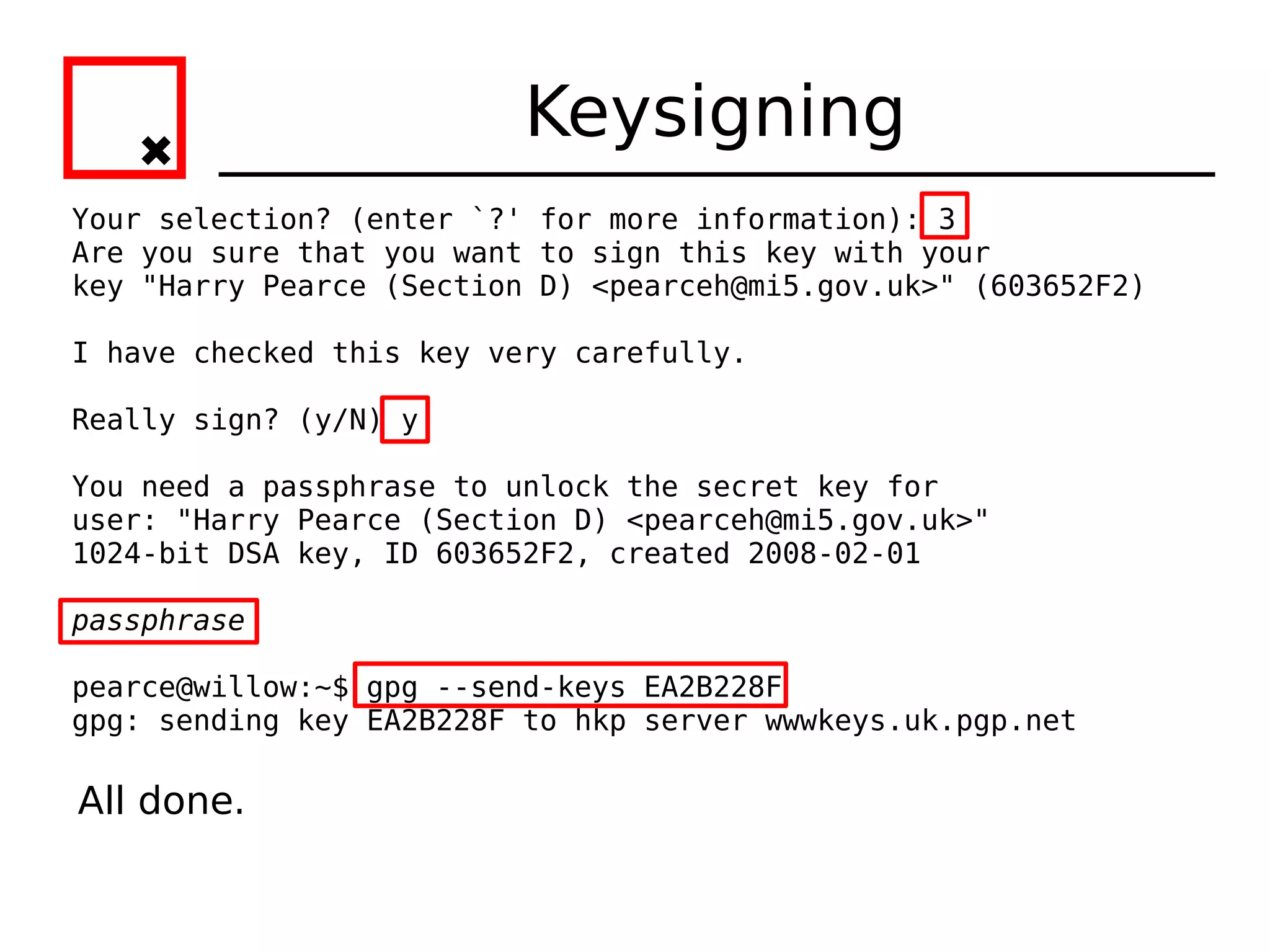
![Keysigning
pearce@willow:~$ gpg --ask-cert-level --sign-key EA2B228F
[...]
pub 1024D/EA2B228F created: 2007-09-06 expires: 2009-09-05
usage: SC
trust: unknown validity: unknown
Primary key fingerprint: 8995 11CC 3CA7 690C C09E 43B3 420D F030
EA2B 228F
Hugo Mills (University of Southampton) <hugo@omii.ac.uk>
This key is due to expire on 2009-09-05.
How carefully have you verified the key you are about to sign
actually belongs
to the person named above? If you don't know what to answer,
enter "0".
(0) I will not answer. (default)
(1) I have not checked at all.
(2) I have done casual checking.
(3) I have done very careful checking.](https://image.slidesharecdn.com/crypto-hlug-120704204314-phpapp01/75/Crypto-hlug-33-2048.jpg)