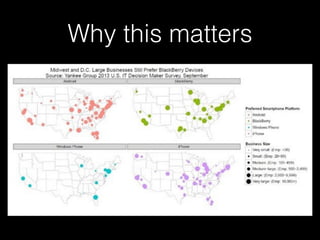
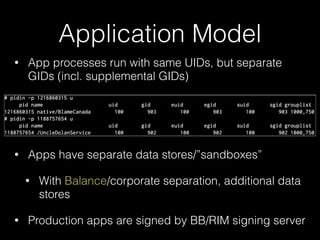
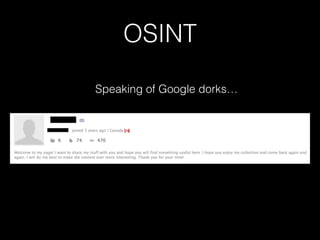
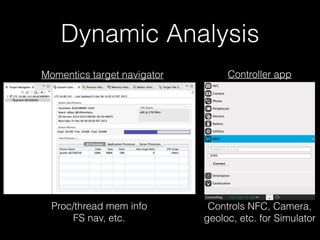
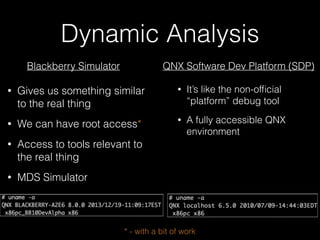
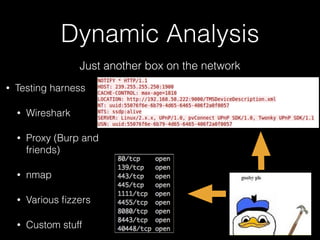
The document discusses methodology for analyzing the security of the BlackBerry 10 mobile operating system. It outlines approaches taken such as gathering publicly available information through search engines and previous research papers, performing dynamic analysis using the BlackBerry Simulator and development tools, and examining log files and network traffic for insights. The presentation focuses on methodology rather than specific findings.
























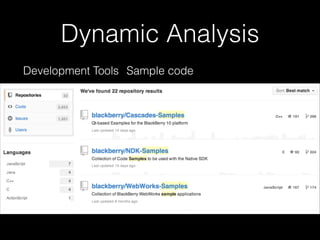


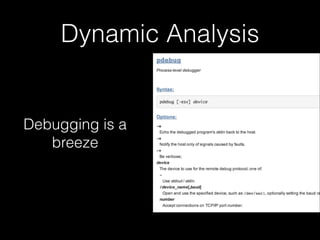
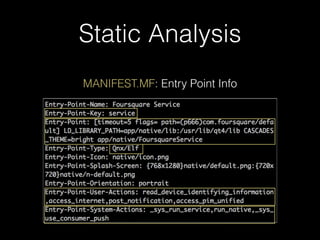
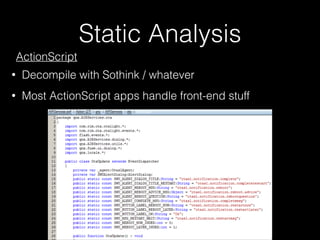
![Dynamic Analysis
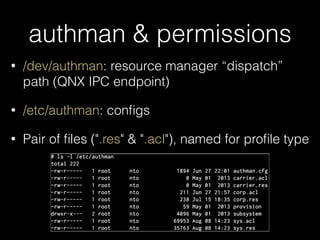
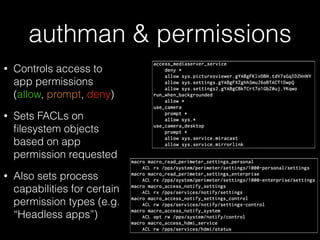
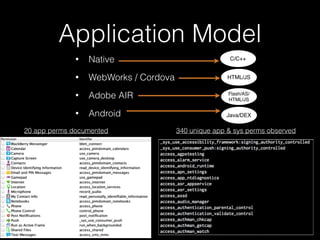
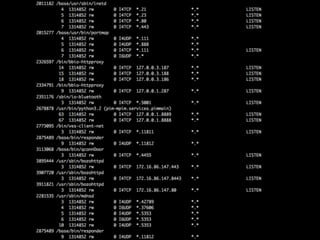
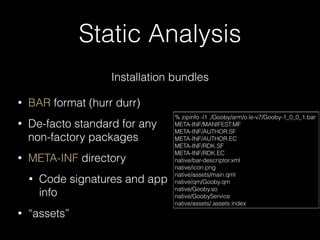
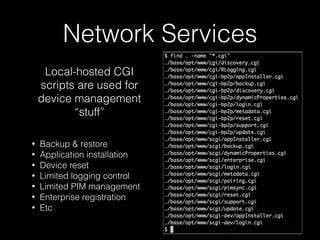
• Unsurprisingly, logs => info
• slogger (app event logger) and slogger2 (system event logger)
• Readable on simulator with sloginfo and slog2info
• slog* devices not readable on device :(
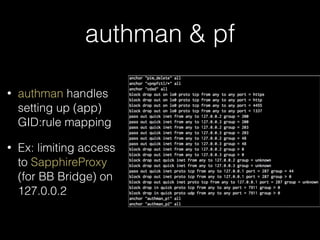
Dec 07 16:14:20.041 sys.pim.contacts.gYABgGsAOuzqCT1fu5Zx4sqrJdY.28930195 default 9000 [ServiceManager] refreshing accounts list
Dec 07 16:14:20.042 sys.pim.contacts.gYABgGsAOuzqCT1fu5Zx4sqrJdY.28930195 default 9000 Calling AccountServicePrivate::accounts
for service "contacts"
Dec 07 16:14:20.042 sys.pim.contacts.gYABgGsAOuzqCT1fu5Zx4sqrJdY.28930195 default 9000 Calling AccountServicePrivate::accounts
Dec 07 16:14:20.044 sys.pim.messages.gYABgJ8jn83Ok_NEWYplPYozt5w.3567740 default 9000 MNH(93): handleAccountUpdated
accountId 4
Dec 07 16:14:20.045 sys.pim.messages.gYABgJ8jn83Ok_NEWYplPYozt5w.3567740 default 9000 Calling AccountServicePrivate::account
for AccountKey = 4
Dec 07 16:14:20.052 sys.pim.messages.gYABgJ8jn83Ok_NEWYplPYozt5w.3567740 default 9000 GET 0x13
Dec 07 16:14:20.052 sys.pim.messages.gYABgJ8jn83Ok_NEWYplPYozt5w.3567740 default 9000 URL Buffer: http://127.0.0.1:8888/
accounts/4
!
Dec 07 16:14:20.066 sys.pim.contacts.gYABgGsAOuzqCT1fu5Zx4sqrJdY.28930195 default 9000 GET 0x1
Dec 07 16:14:20.066 sys.pim.contacts.gYABgGsAOuzqCT1fu5Zx4sqrJdY.28930195 default 9000 URL Buffer: http://127.0.0.1:8888/
accounts
!
Dec 07 16:14:20.072 sys.pim.messages.gYABgJ8jn83Ok_NEWYplPYozt5w.3567740 default 9000 Curl Easy perform
Dec 07 16:14:20.080 sys.pim.contacts.gYABgGsAOuzqCT1fu5Zx4sqrJdY.28930195 default 9000 Curl Easy perform
Dec 07 16:14:20.081 menu_service.2830447 menu_svc_logs 0 MS PIMCORE: command: GET method: /accounts URL:http://
127.0.0.1:8888/accounts
Dec 07 16:14:20.082 phone.3567743 phone 0 [ I][18][PlatformContact:lookupByPhoneNu| 107] ContactService returns 0](https://image.slidesharecdn.com/noapologyrequired-bb10-cansecwest2014-140314093752-phpapp02/85/No-Apology-Required-Deconstructing-BB10-47-320.jpg)
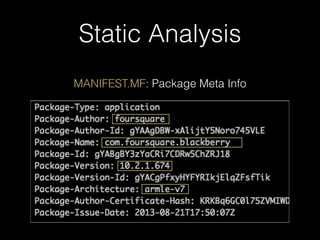
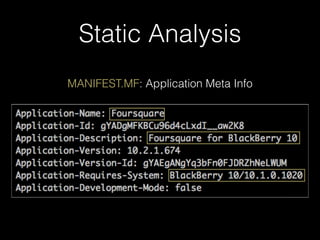
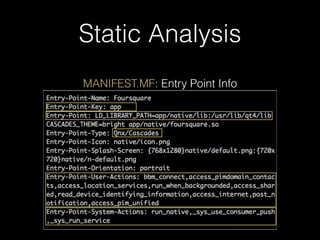
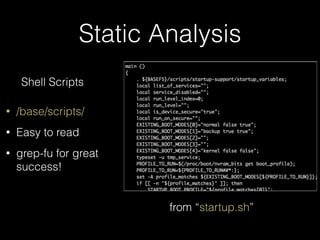


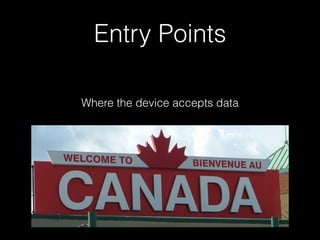
![IPC
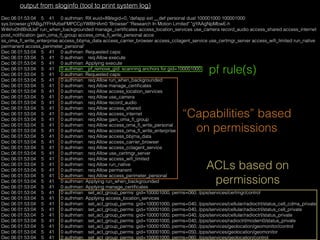
• Numerous IPC endpoints available
• QNX channels particularly
caught our eye
• Wrote some horrible IPC
scanners / fuzzers
• Problem: not always sure WTF is
on the other end of a channel
(or able to attach to channel but
unable to send)
• Also DoS’d/froze device multiple
times during mass channel
scans
$ ./scanchan.py 643092
Could not find platform independent libraries <prefix>
Consider setting $PYTHONHOME to <prefix>[:<exec_prefix>]
[+] PID: 643092 - Connected to channel: 2
[-] PID: 643092 - Error for channel 6: [Errno 1] Operation not permitted
$ ./fchan1.py 1019928 16
[+] PID: 1019928 - Connected to channel: 16
(48, b"AAAAAAAAAAAAAAAA(coid, b'Hello!')n c
x01x00x00x00x00x00x00x00x03x00x00x00x02x0
0x00x00Ox00x00x00sx16x00x00x00|x01x00|
x00x00_x00x00|x02x00|x00x00_x01x00d
x00x00S(x01x00x00x00N(x02x00x00x00u
x04x00x00x00argsux06x00x00x00…](https://image.slidesharecdn.com/noapologyrequired-bb10-cansecwest2014-140314093752-phpapp02/85/No-Apology-Required-Deconstructing-BB10-65-320.jpg)









![Questions / Contact
• https://twitter.com/quine
zach@n0where.org
zach@duosecurity.com
• https://twitter.com/bnull
[NO_EMAIL_PROVIDED]
<--shameless plug](https://image.slidesharecdn.com/noapologyrequired-bb10-cansecwest2014-140314093752-phpapp02/85/No-Apology-Required-Deconstructing-BB10-79-320.jpg)