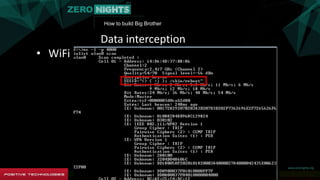
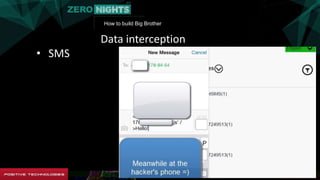
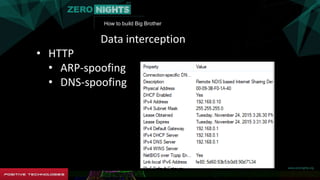
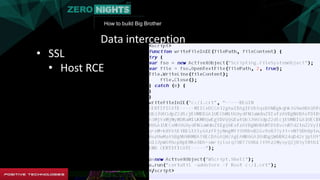
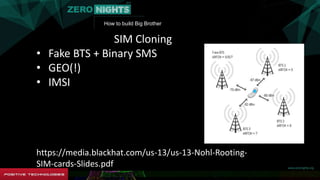
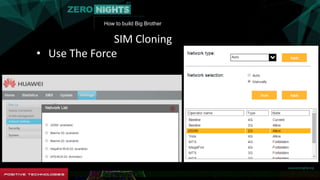
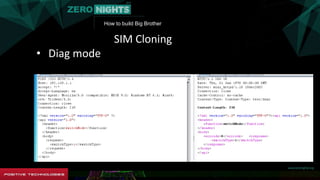
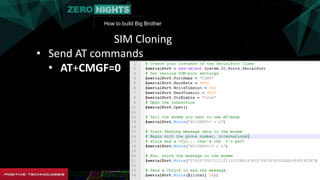
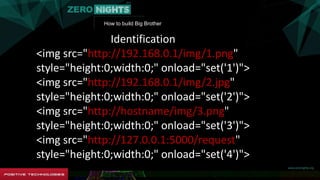
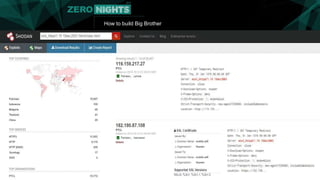
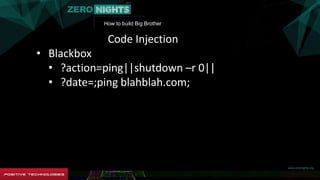
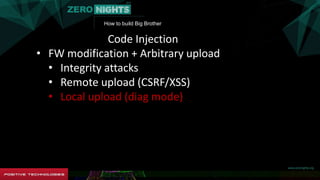
The document describes how to build surveillance capabilities ("Big Brother") using vulnerabilities in internet-connected devices. It details steps like identifying devices using techniques like WHOIS lookups and fingerprinting, injecting code by exploiting firmware vulnerabilities or uploading modified firmware, intercepting data in transit, cloning SIM cards, infecting device operating systems, and creating advanced persistent threats between compromised devices. It provides examples of exploited vulnerabilities and references other researchers in the area. The goal is mass surveillance of users, with acknowledgment that many are unaware of the privacy and security risks.















![How to build Big Brother
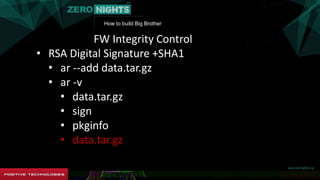
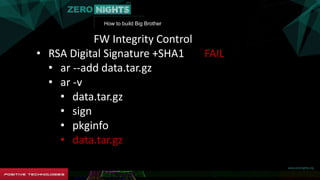
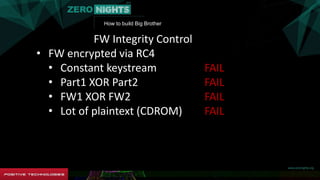
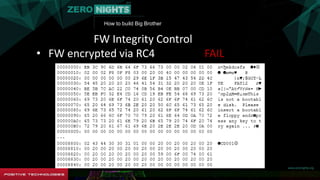
FW Integrity Control
• RSA Digital Signature +SHA1
• AR: !<arch>:
• FW
• pkginfo: <7742526>
• Sign=RSA(SHA1(FW[0..7742526]))](https://image.slidesharecdn.com/znblack-151202112244-lva1-app6892/85/3G-4G-31-320.jpg)