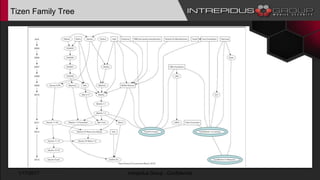
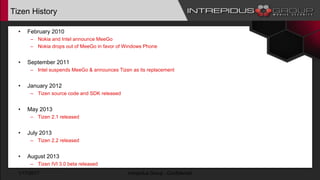
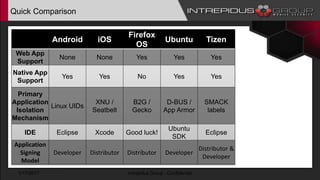
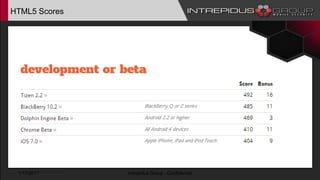
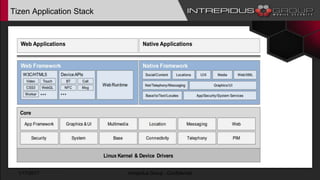
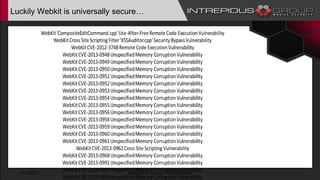
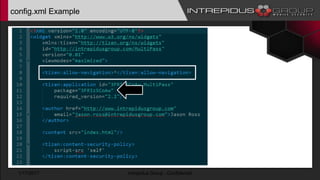
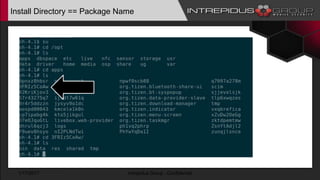
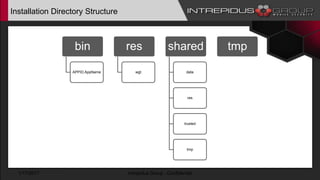
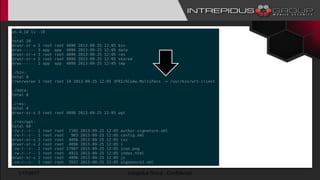
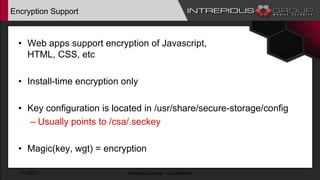
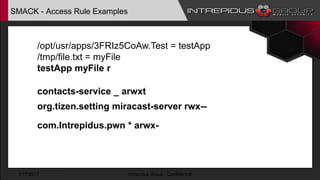
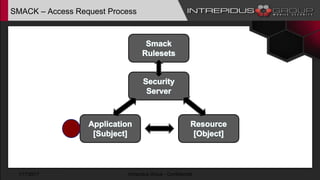
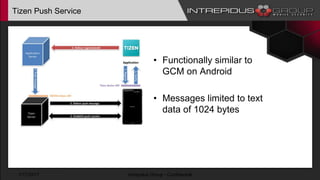
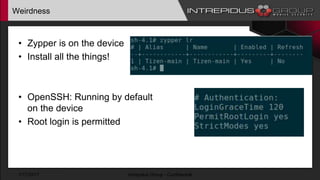
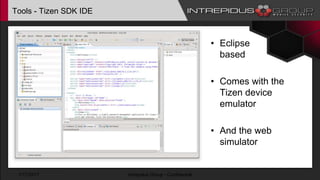
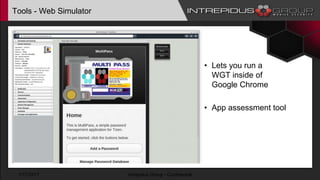
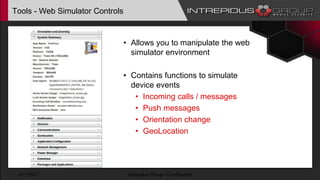
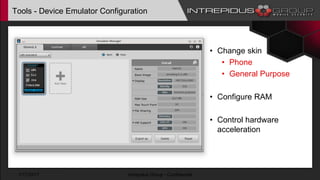
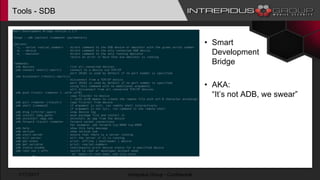
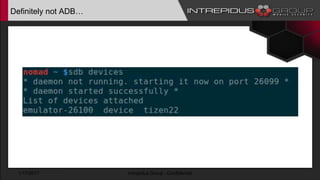
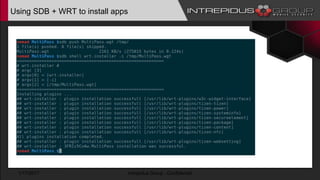
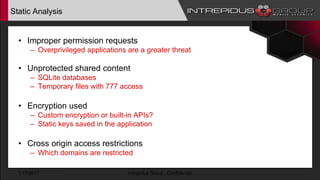
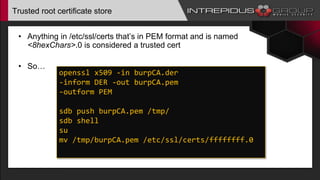
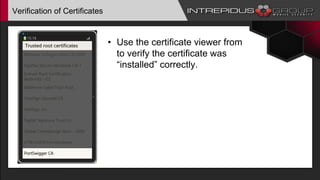
The document provides an overview of Tizen, an open-source mobile operating system developed by the Tizen Association with support from major companies like Samsung and Intel. It discusses Tizen's security model, application types, assessment methodologies, and predictions for its future market adoption. The document details the technical aspects of Tizen—including its application stack, encryption support, and security vulnerabilities—and emphasizes its potential to compete against established mobile operating systems like Android.