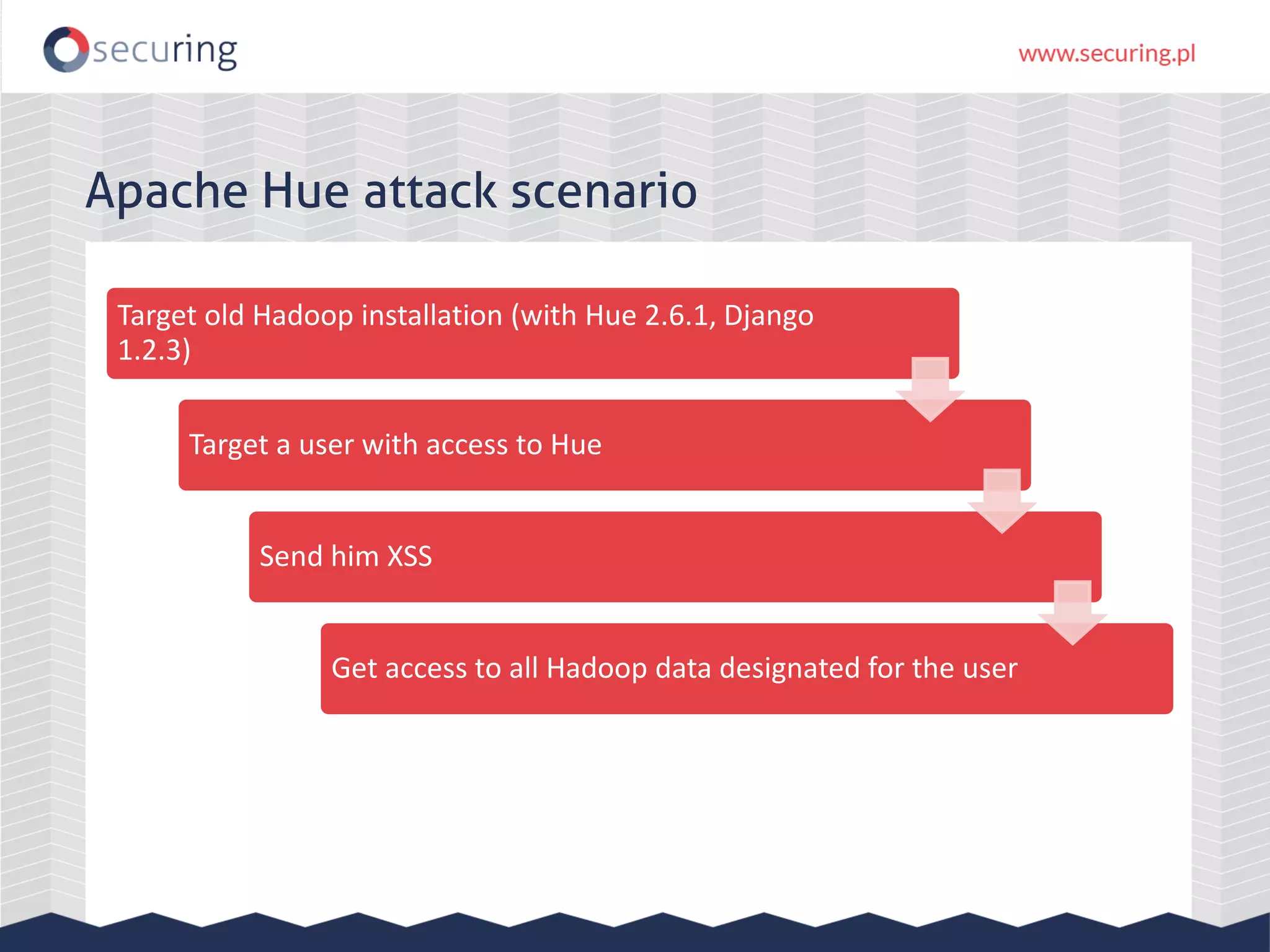
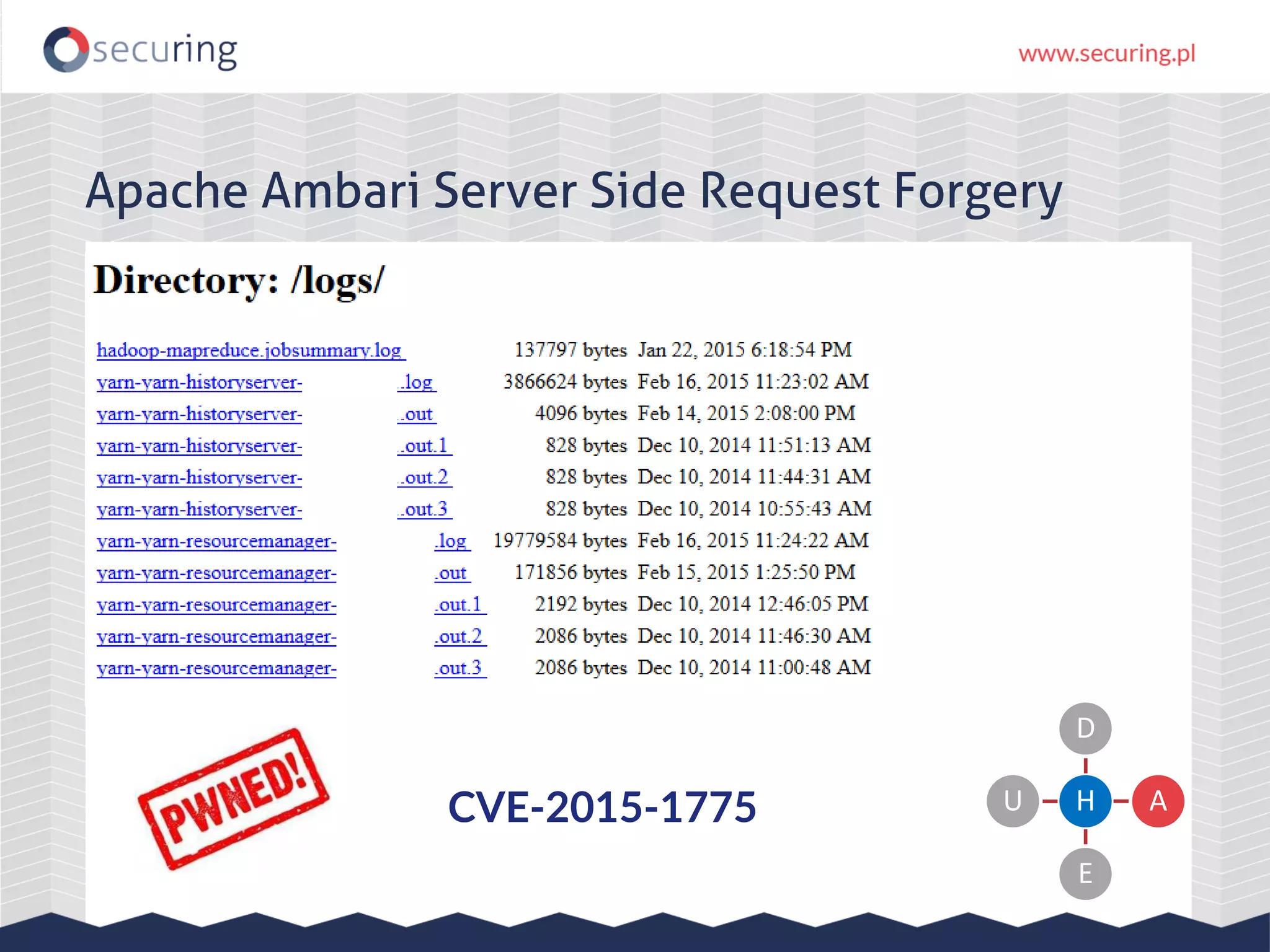
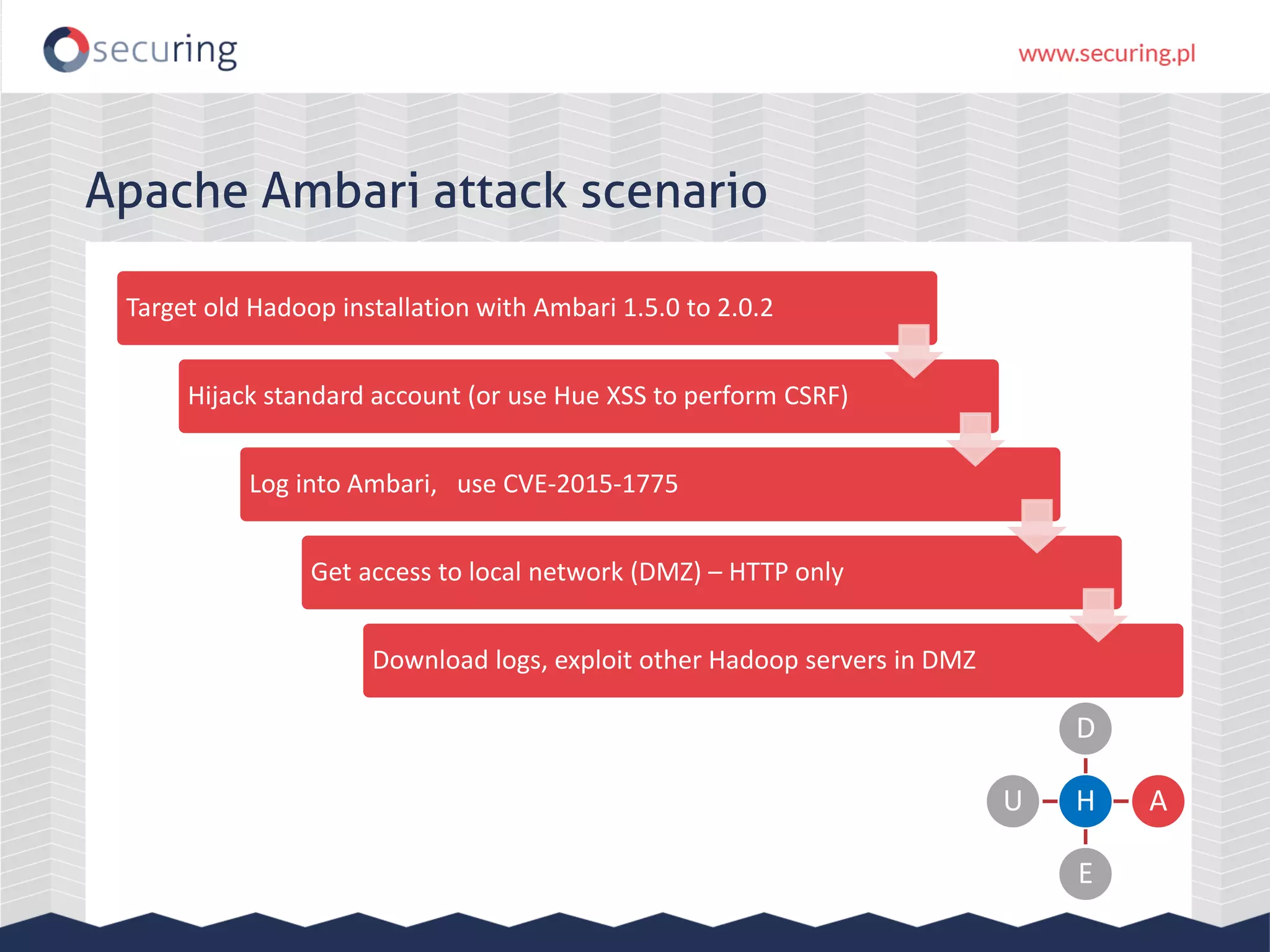
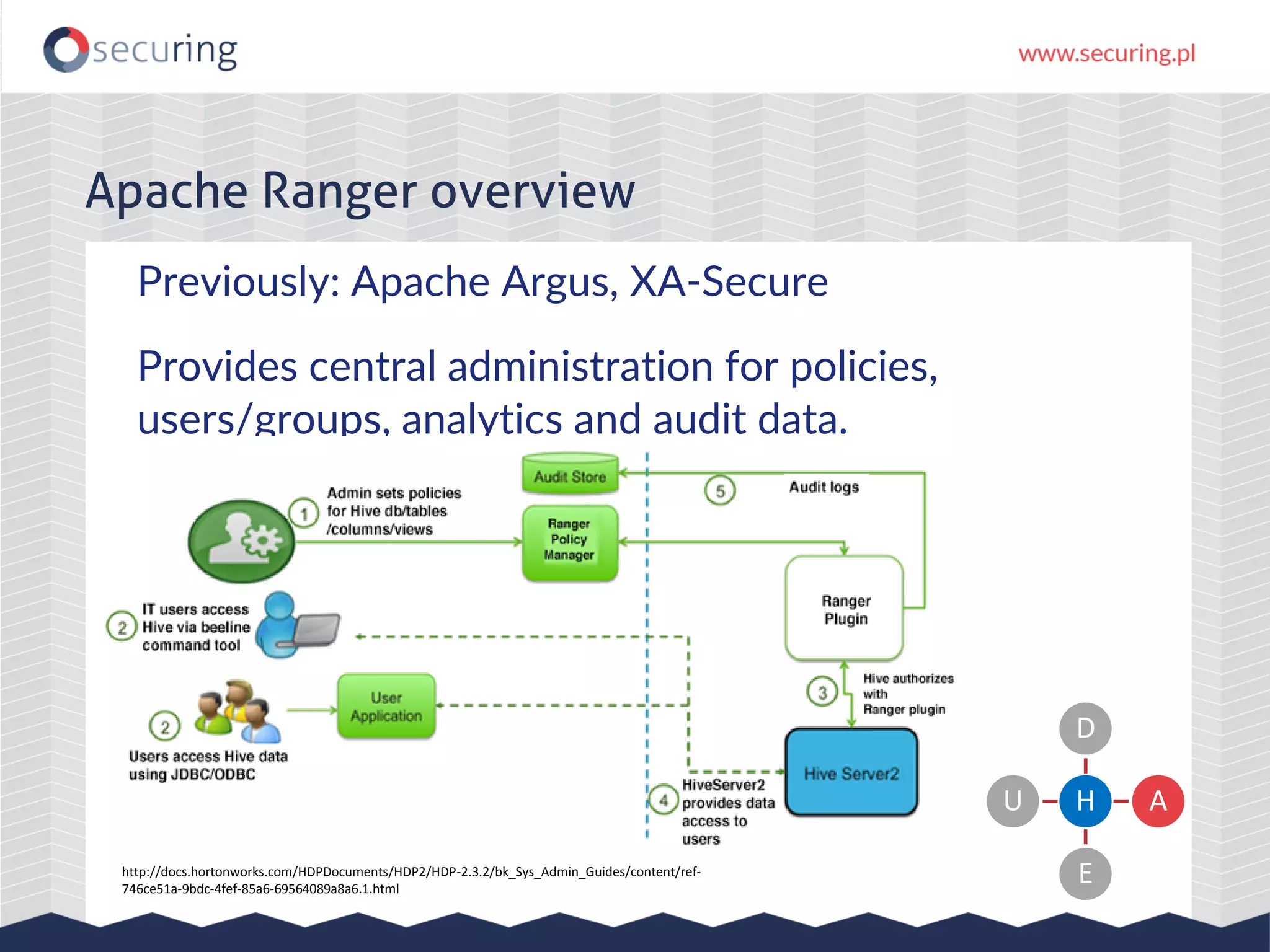
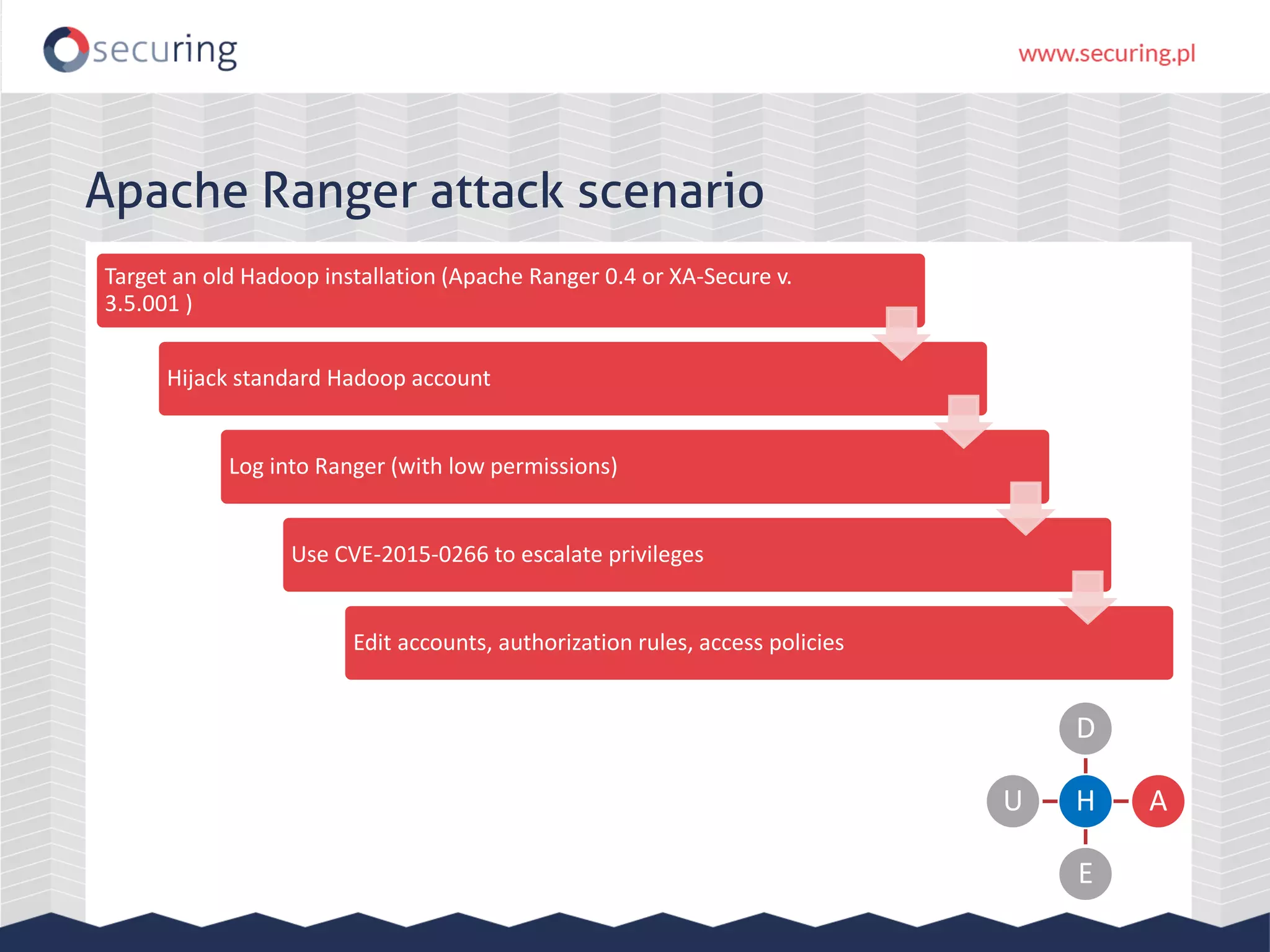
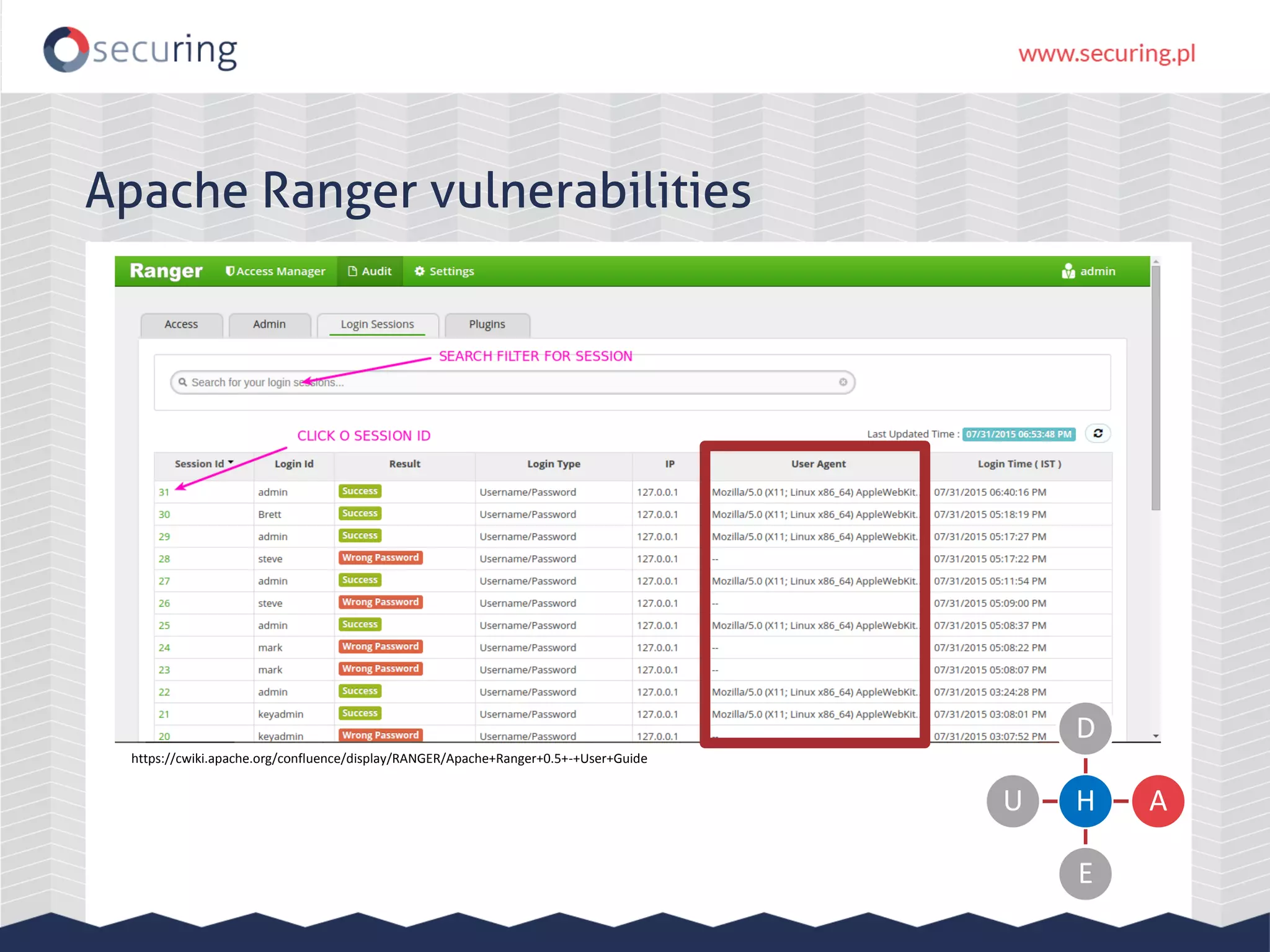
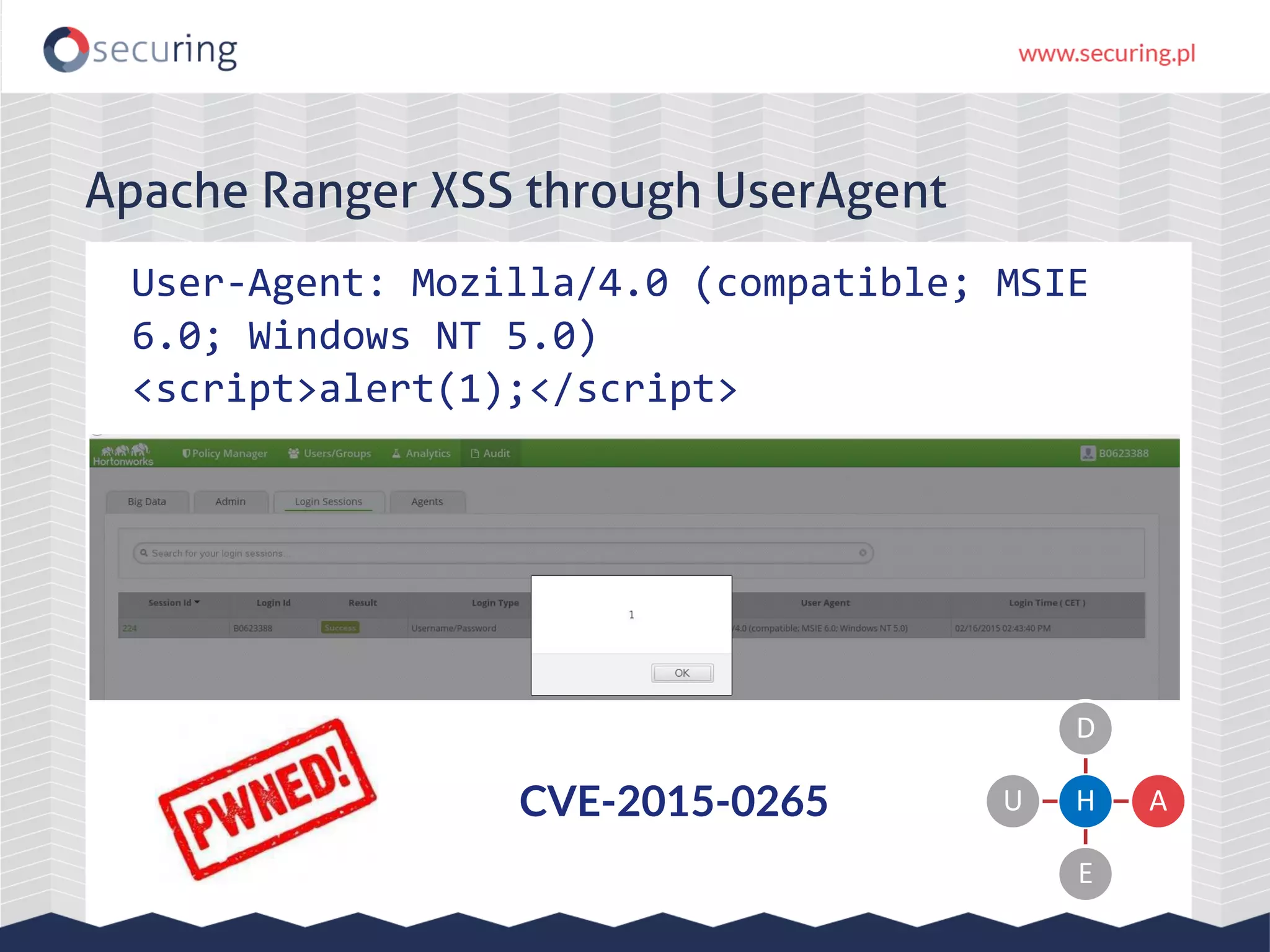
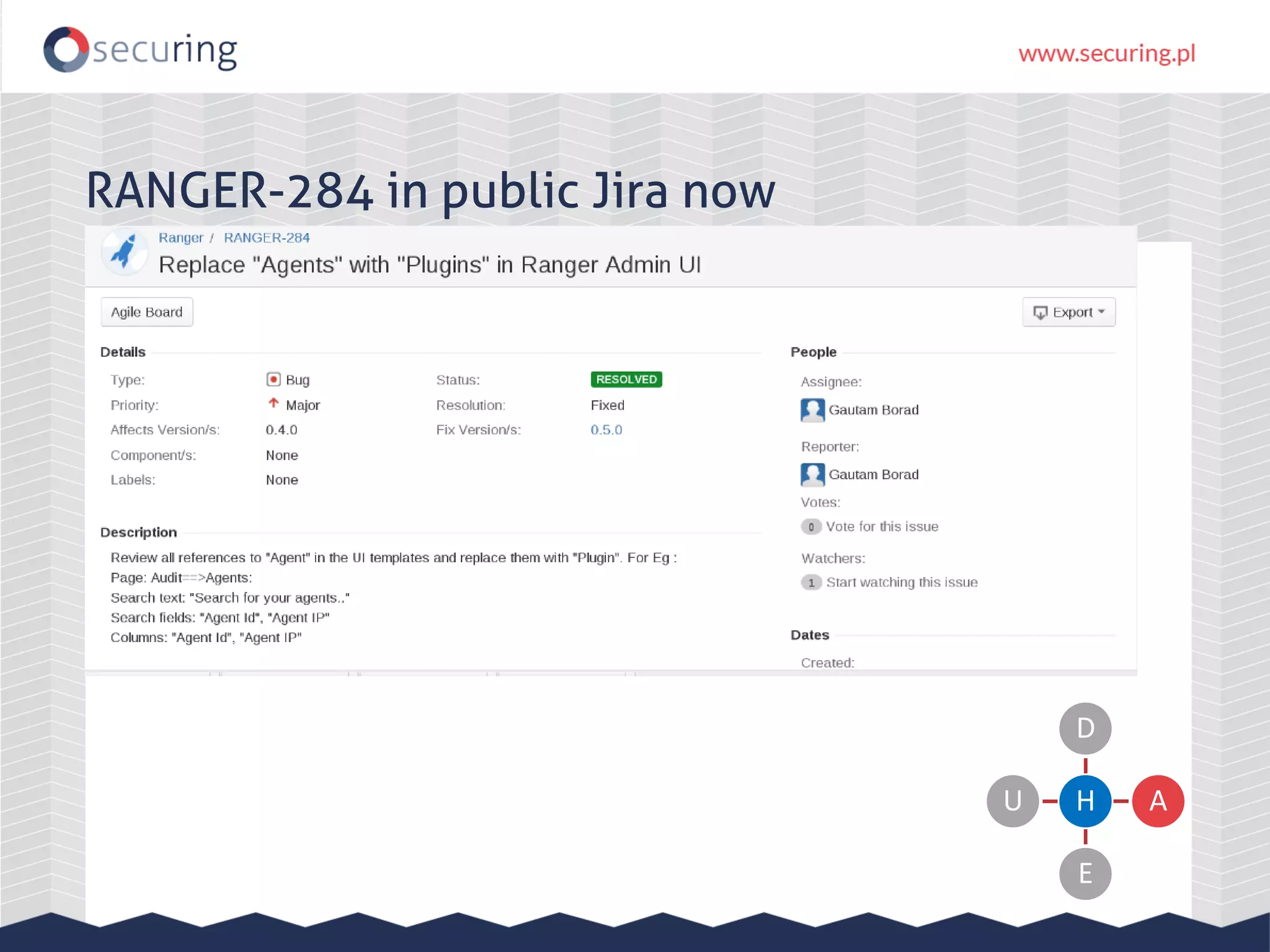
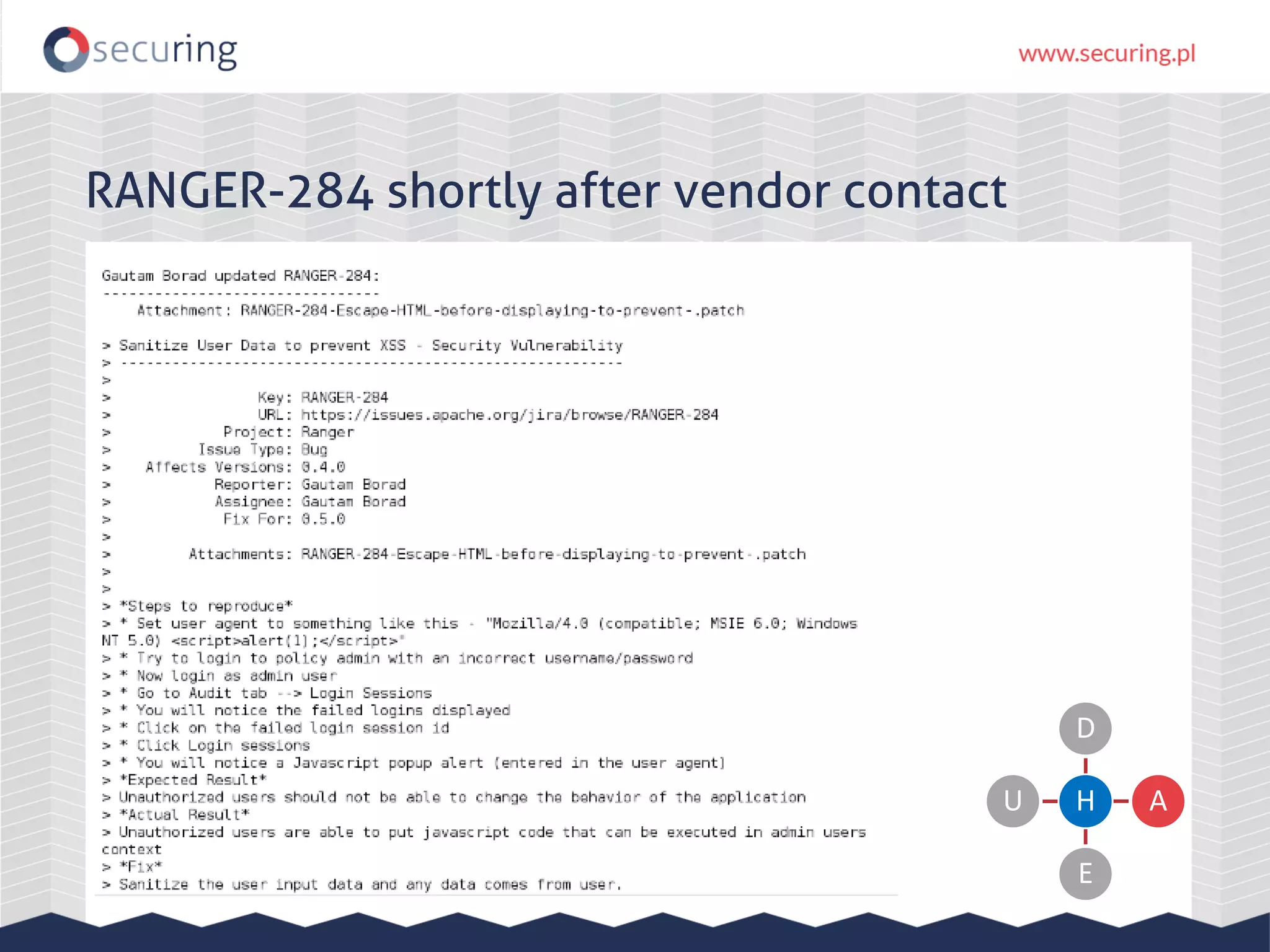
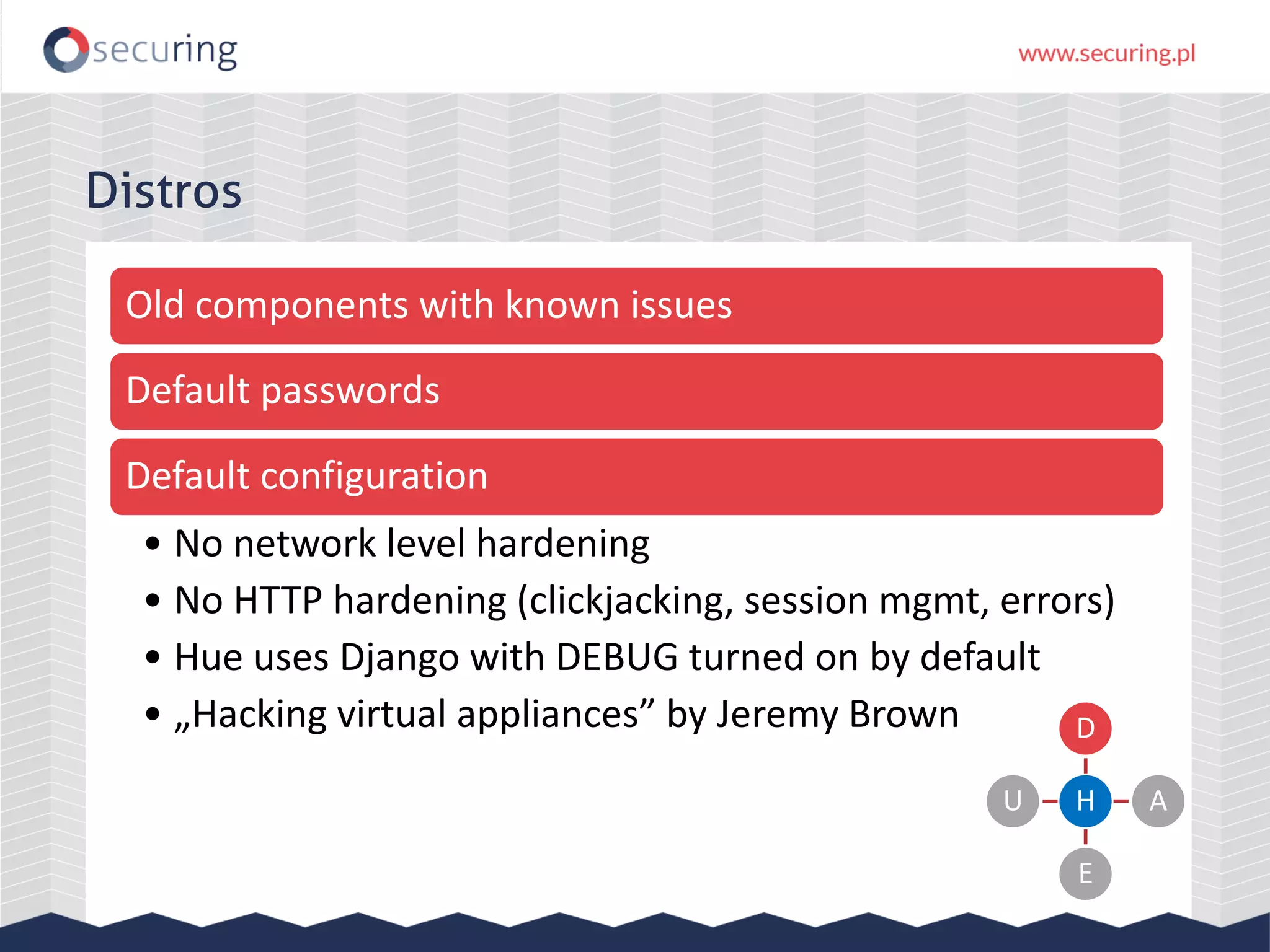
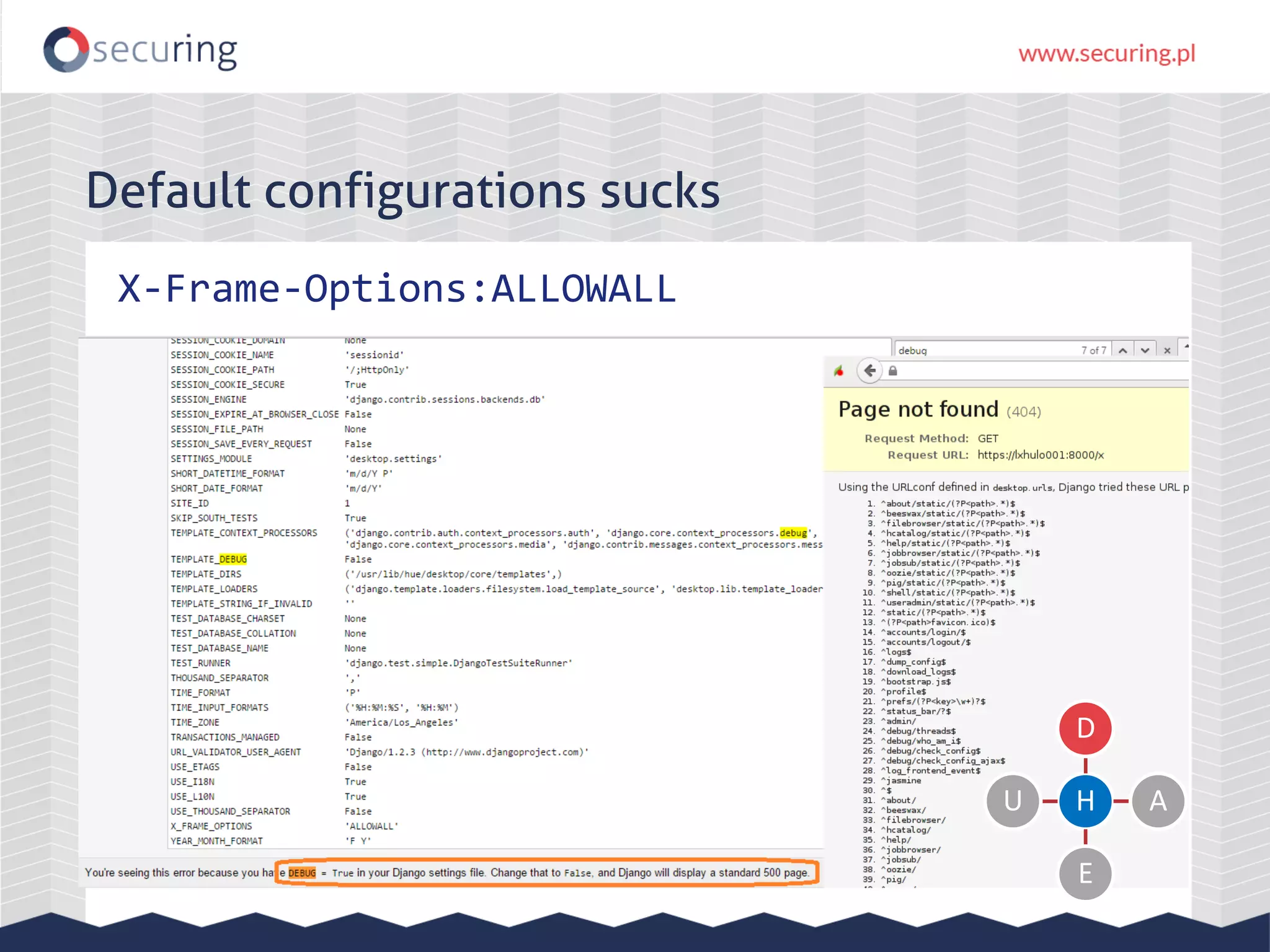
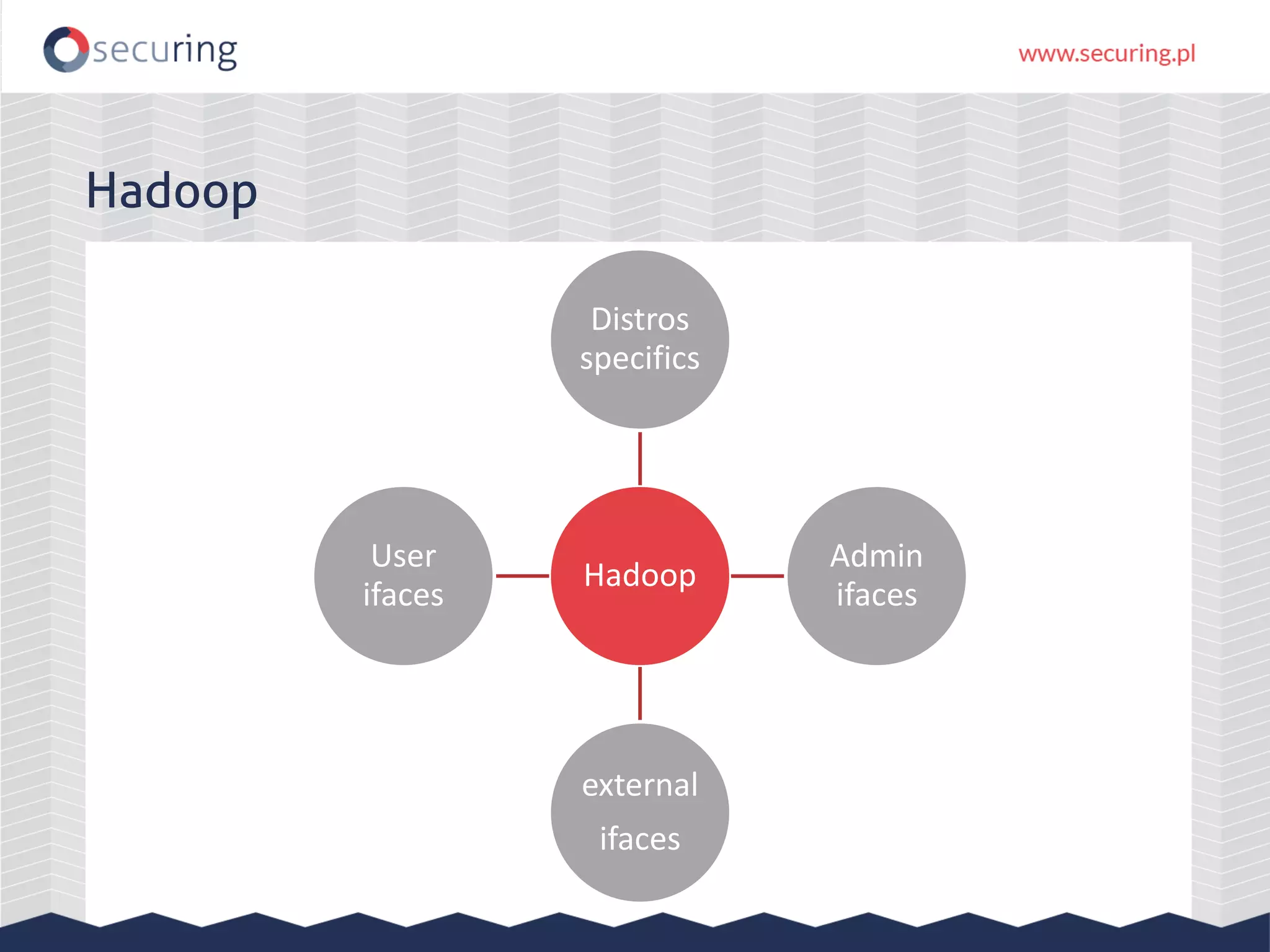
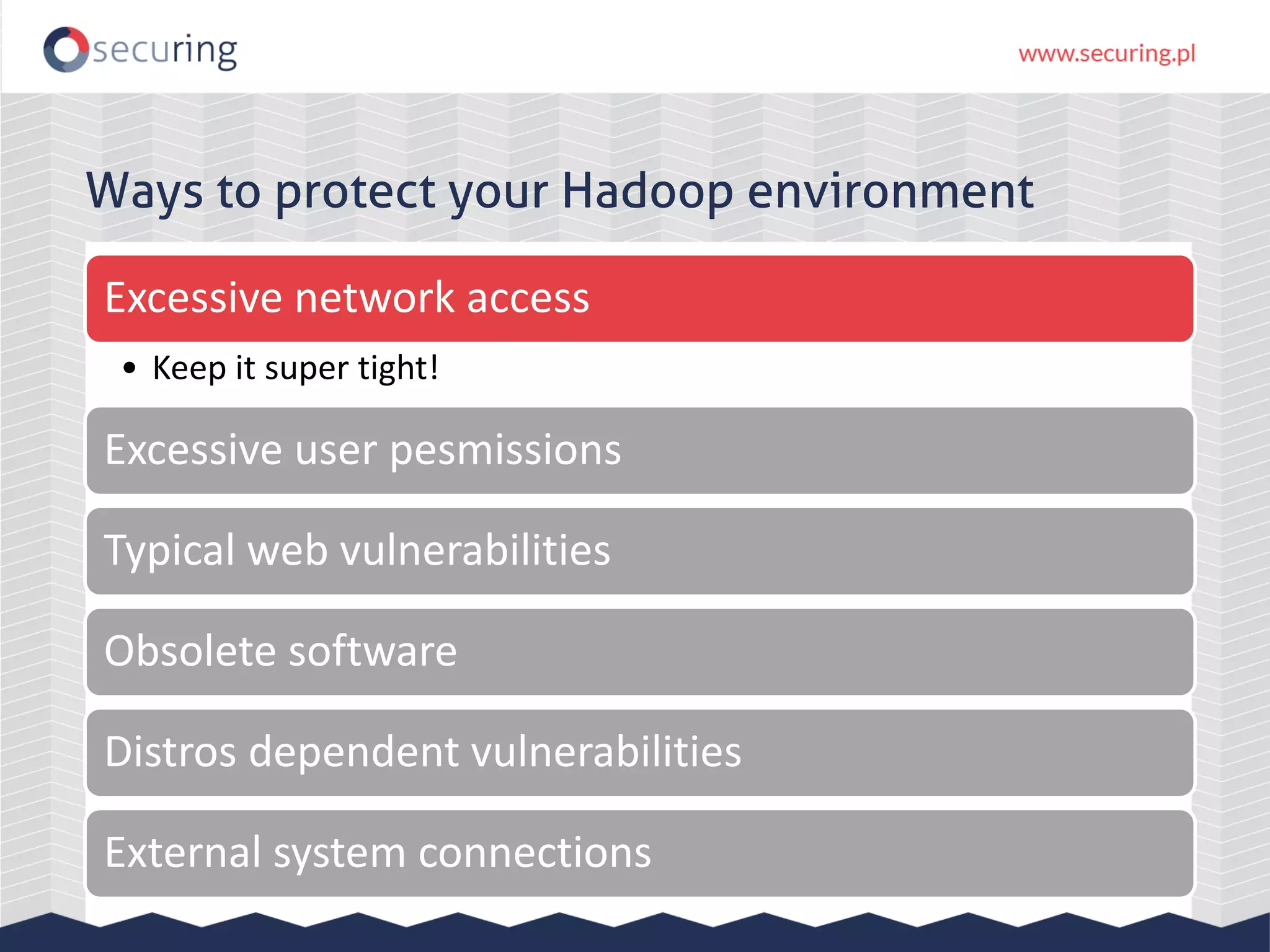
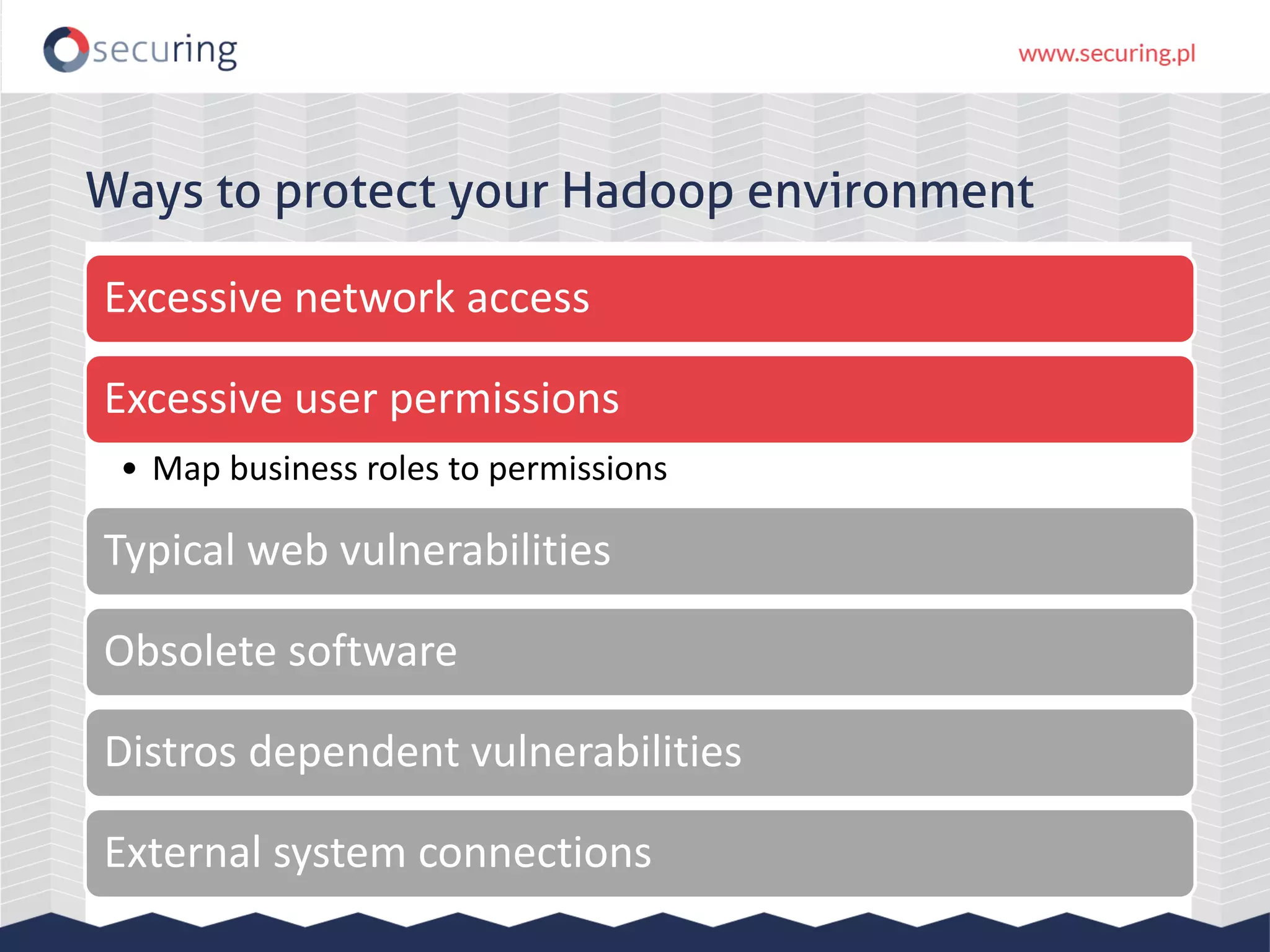
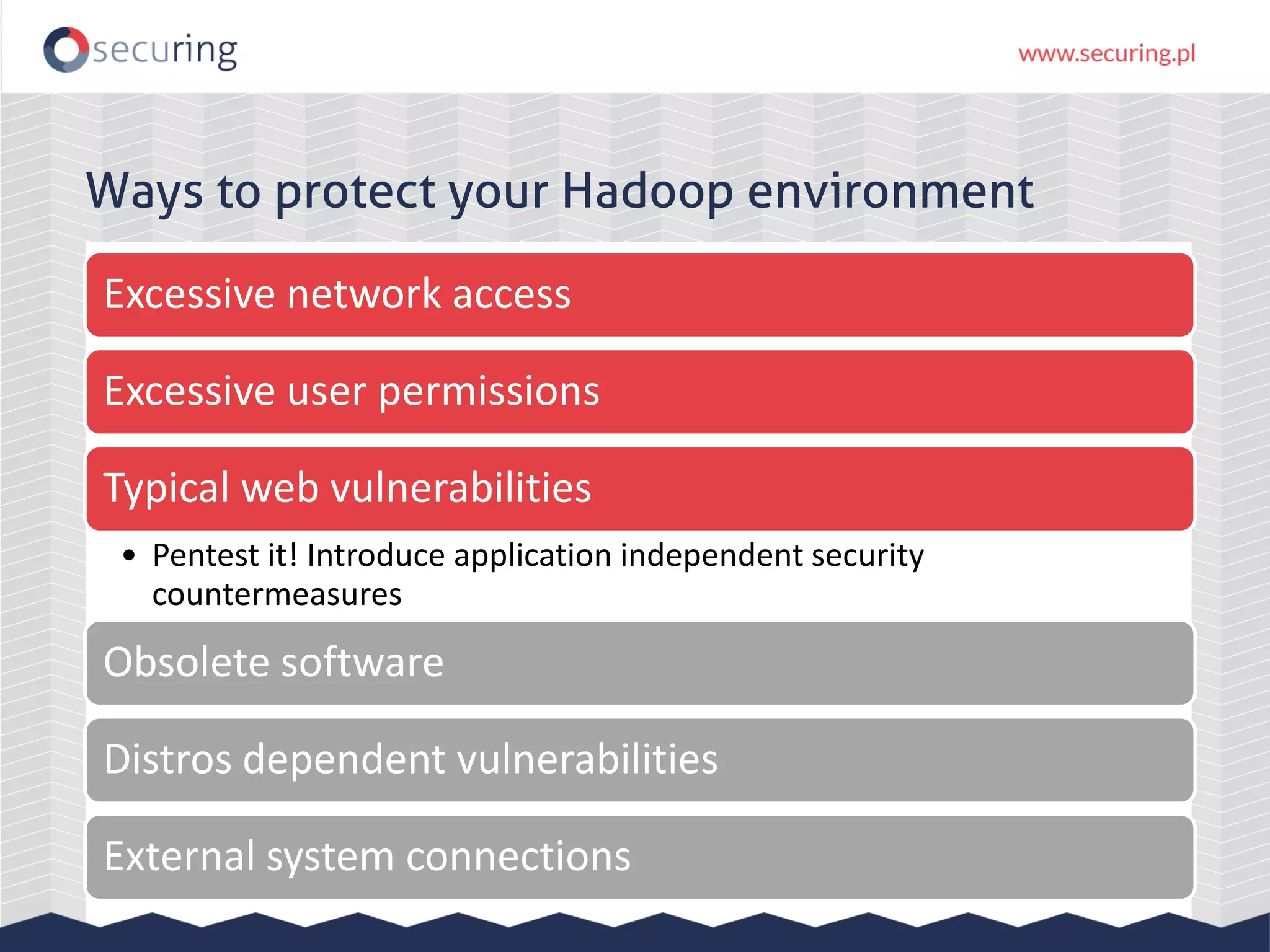
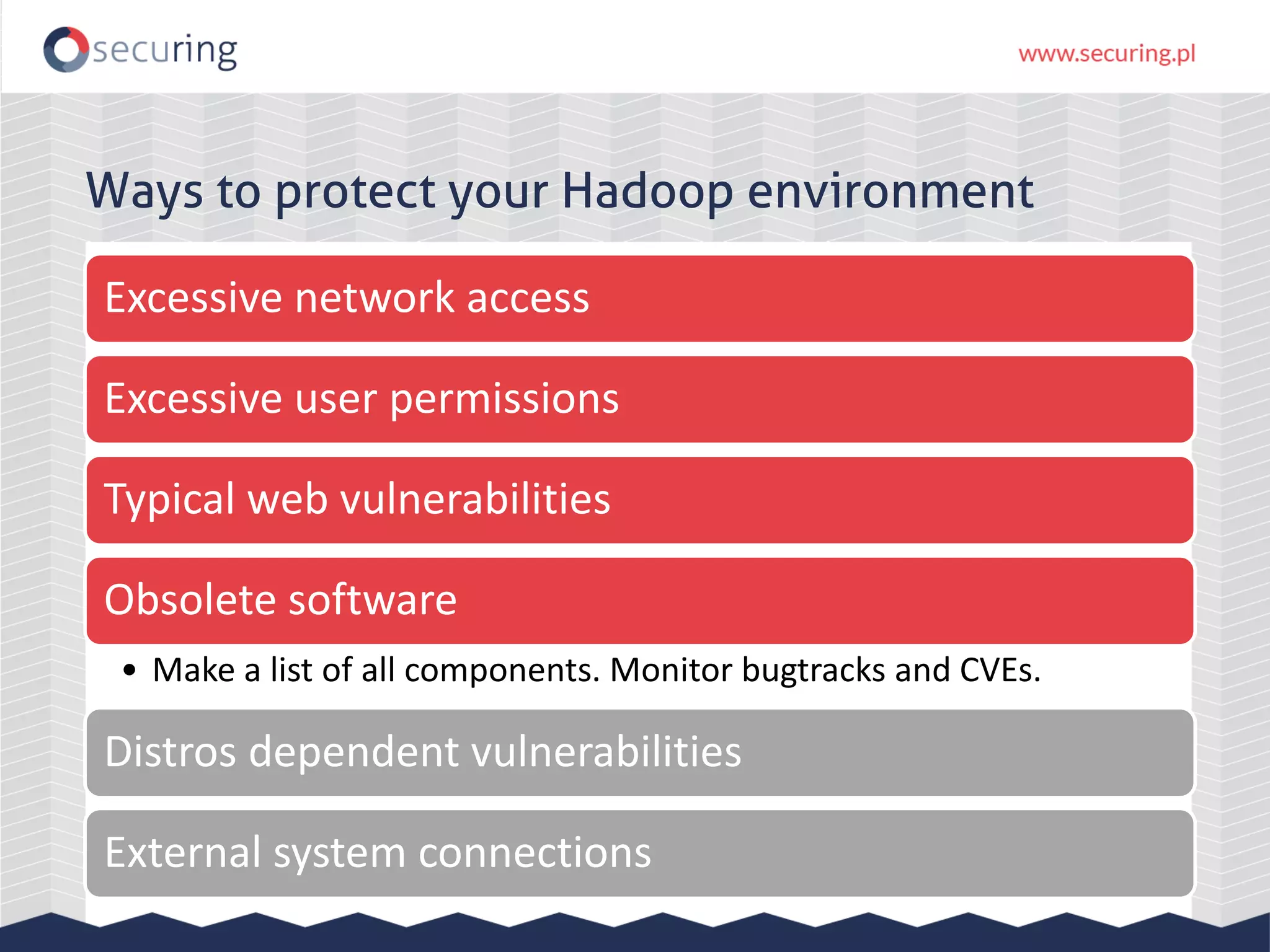
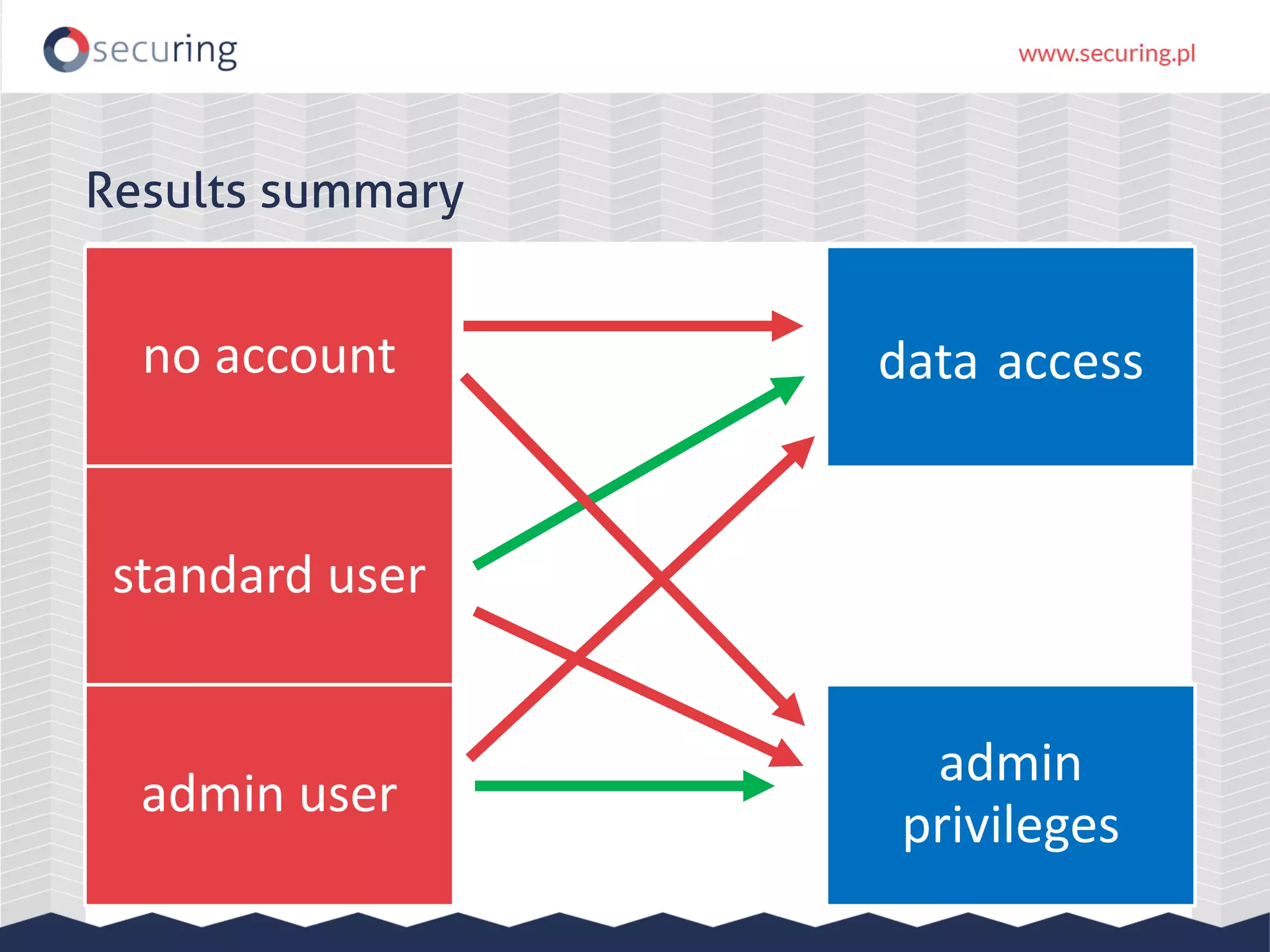
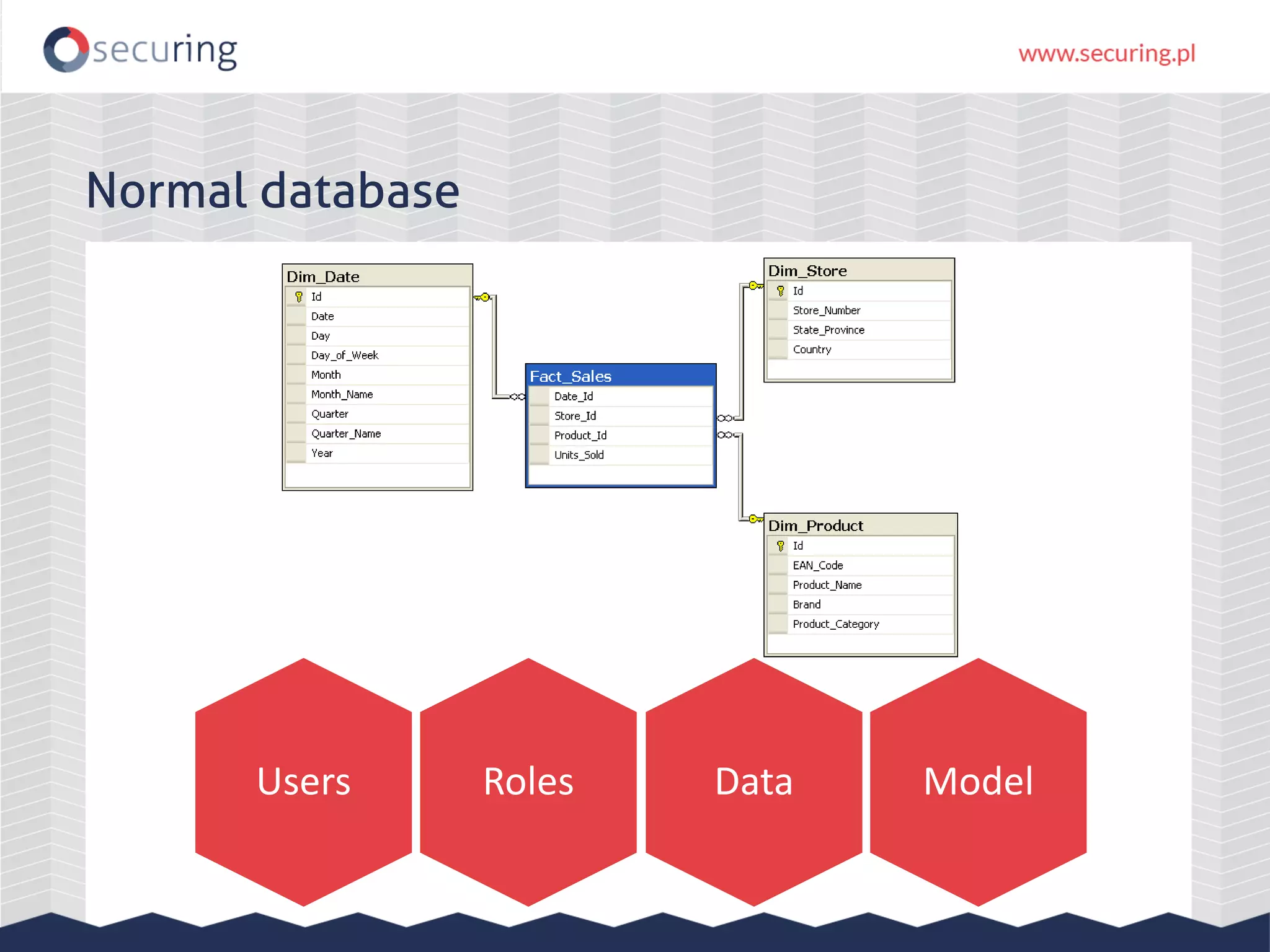
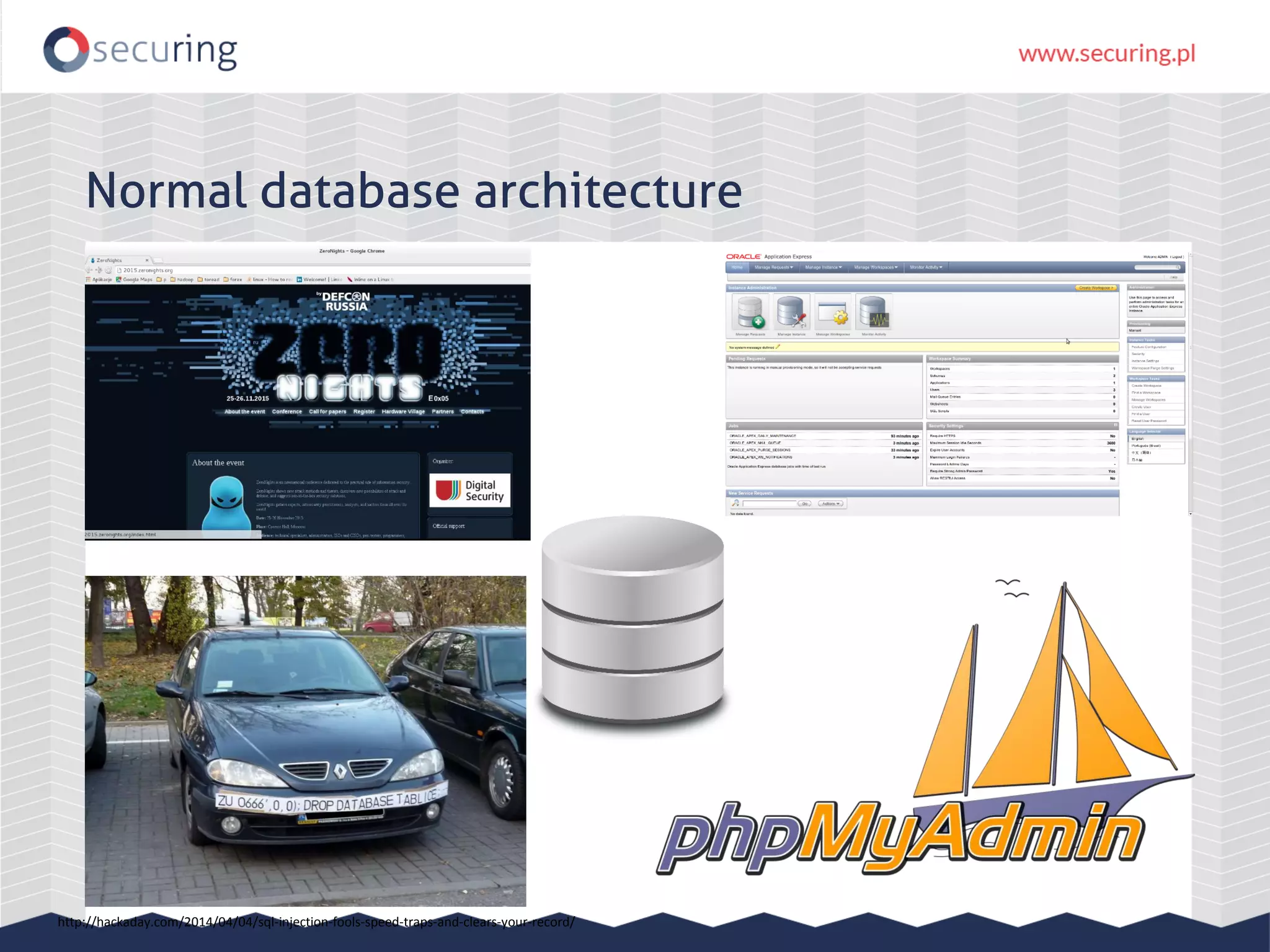
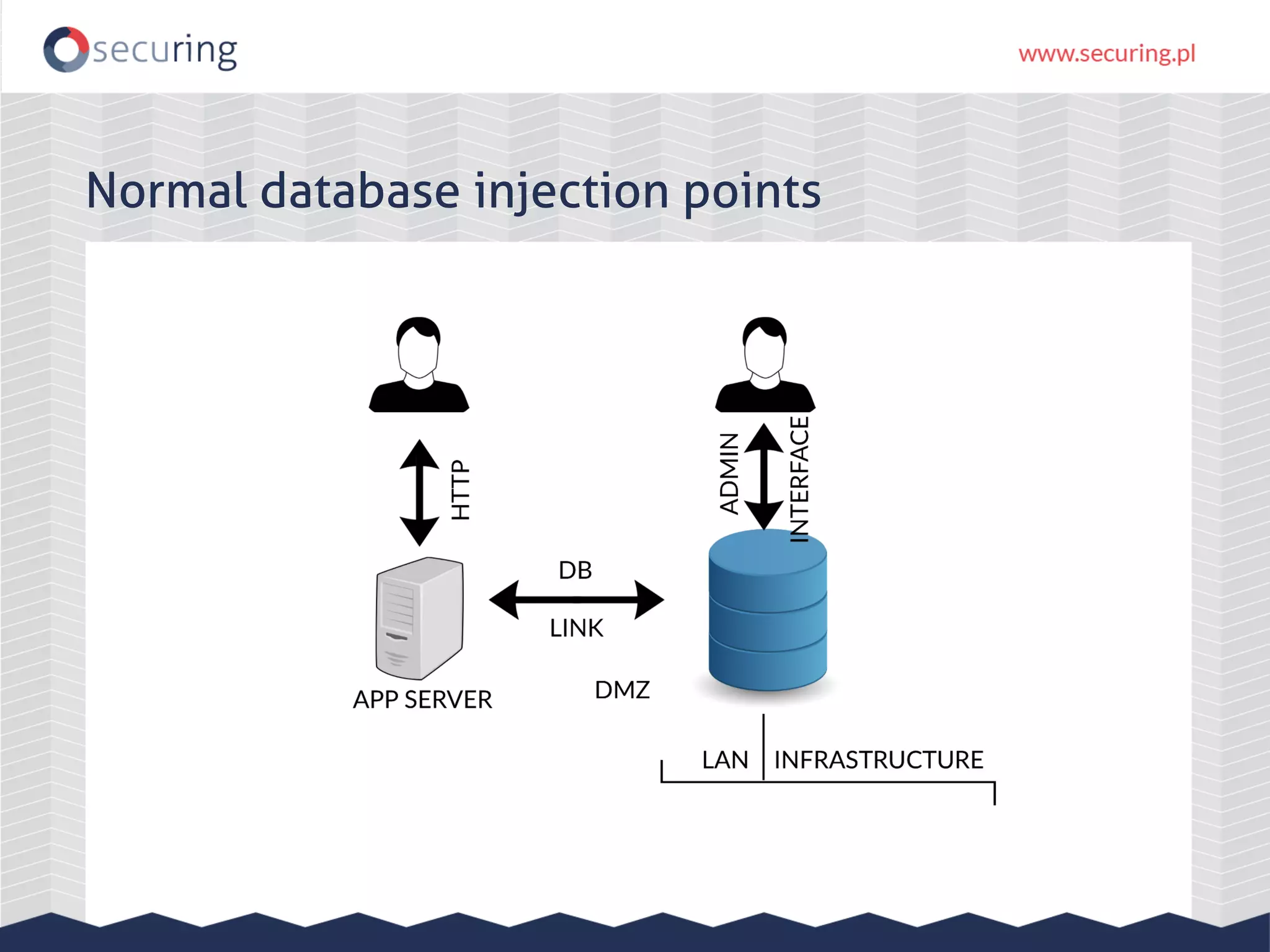
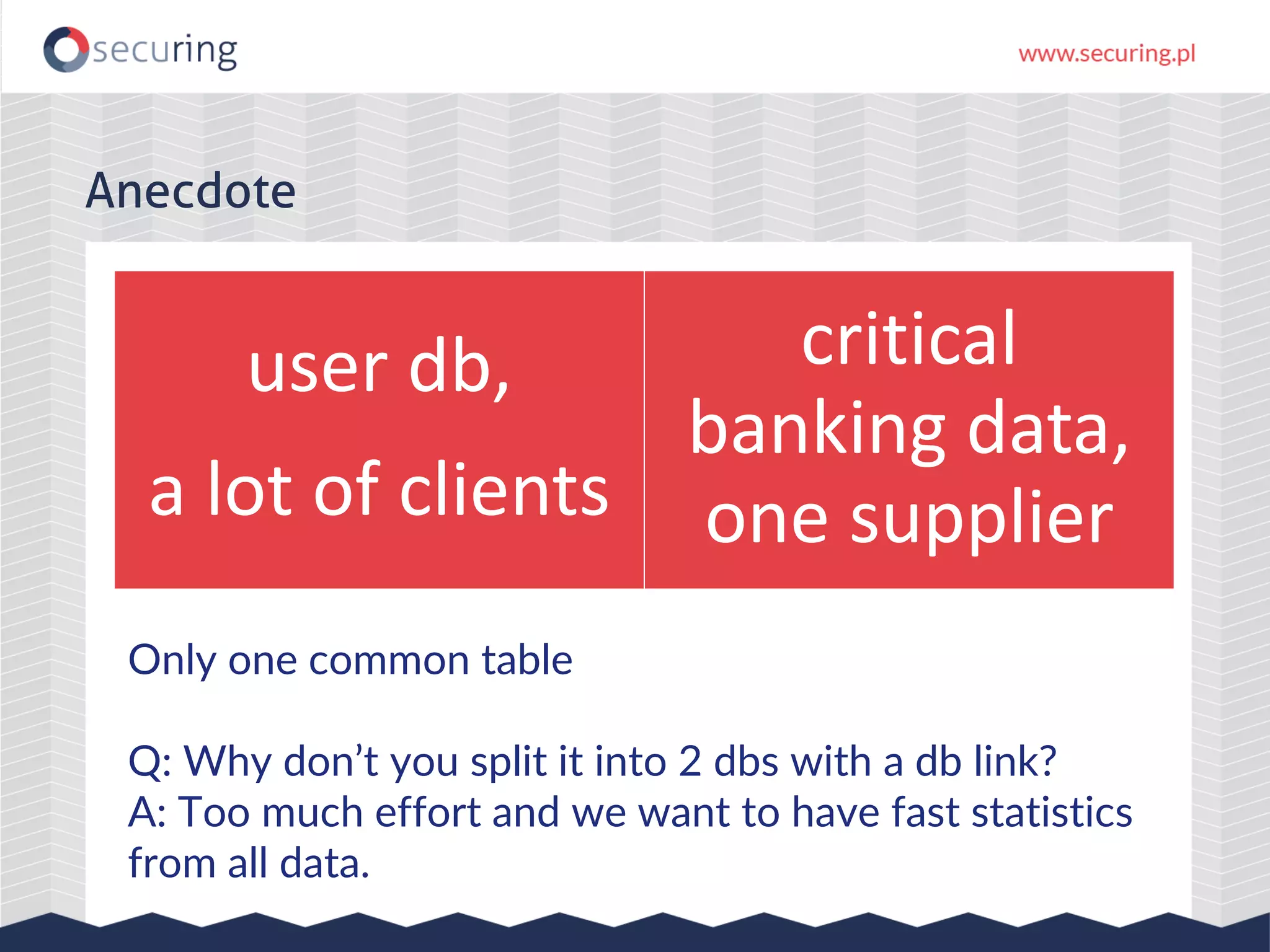
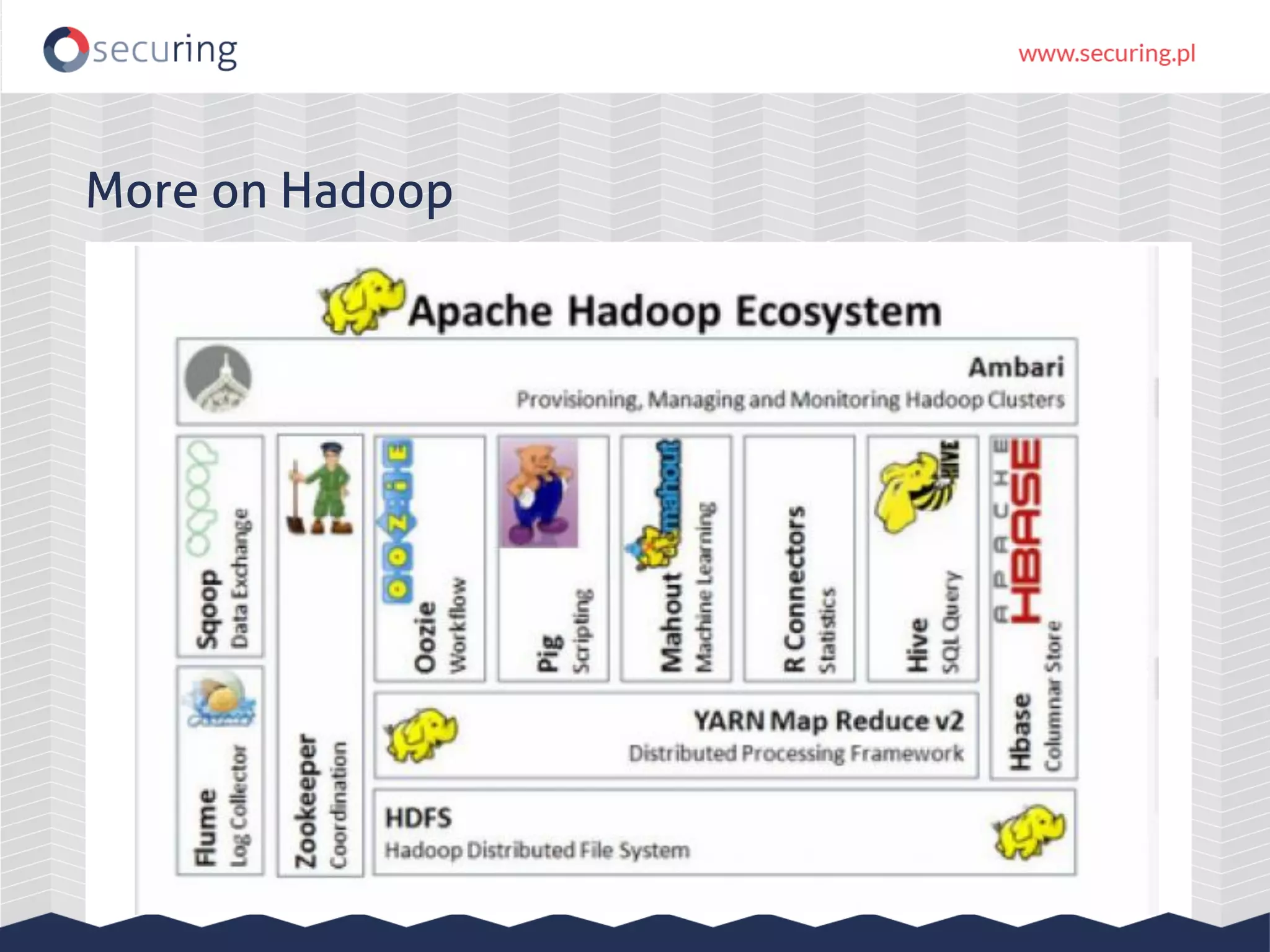
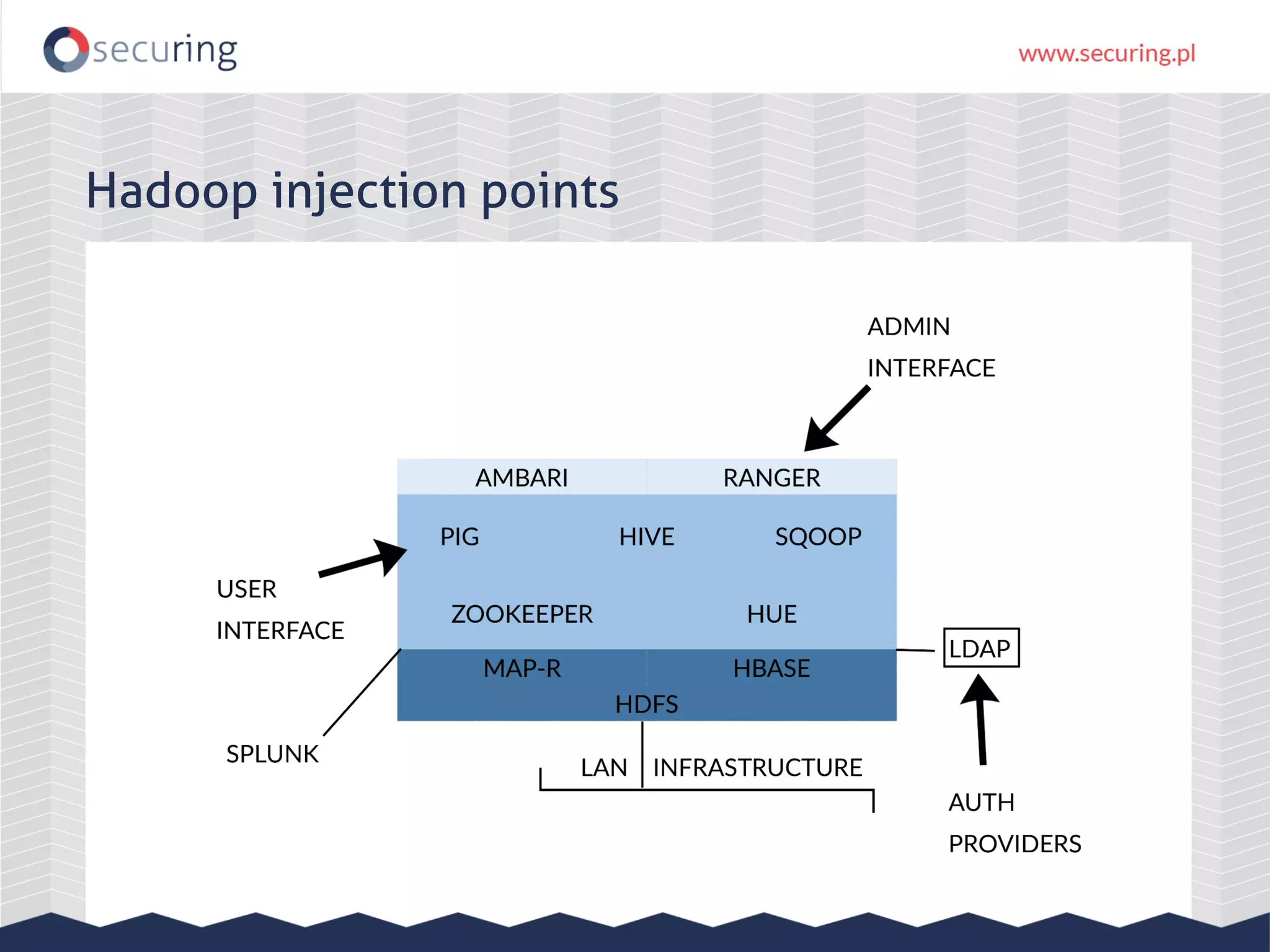
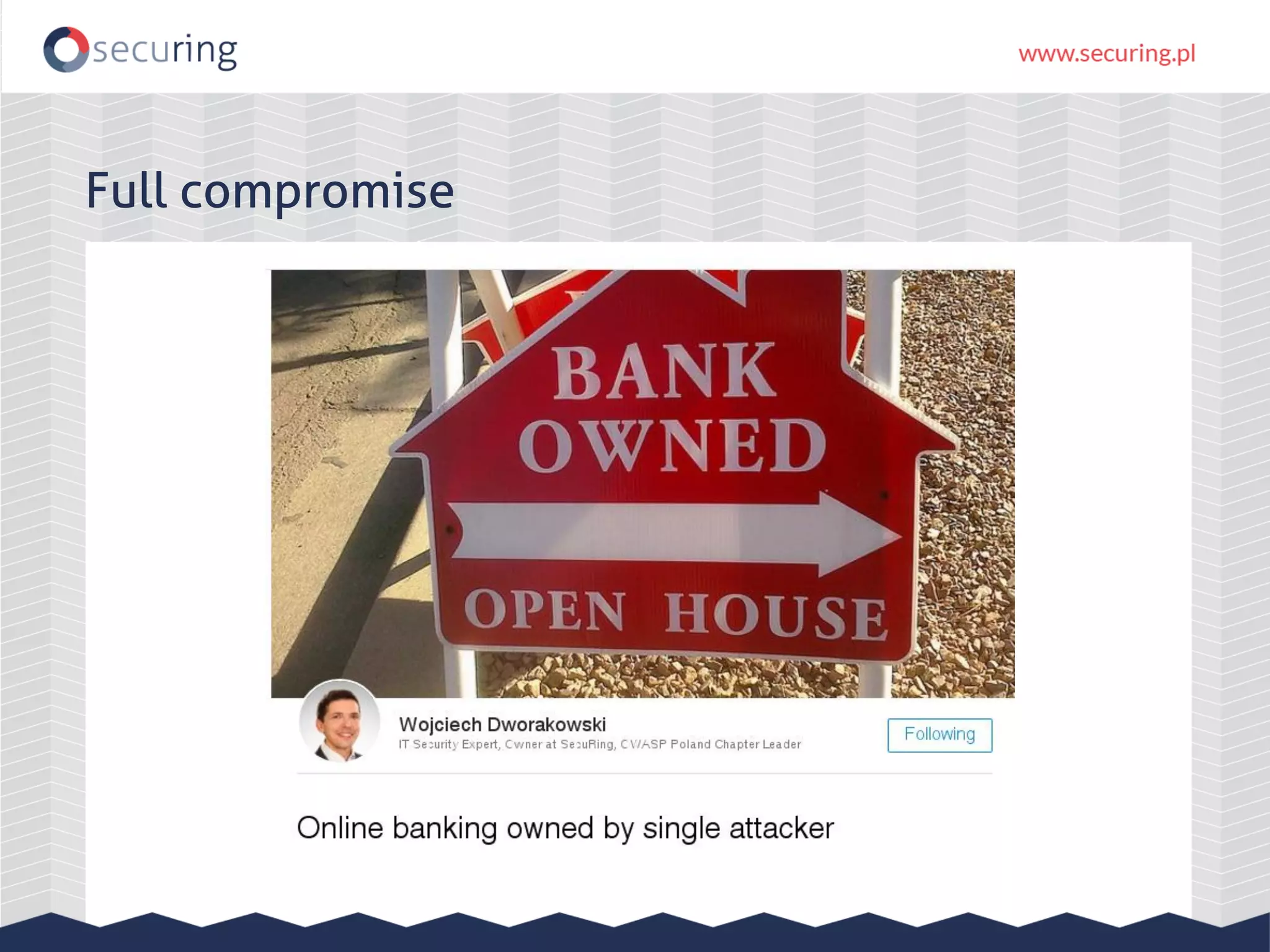
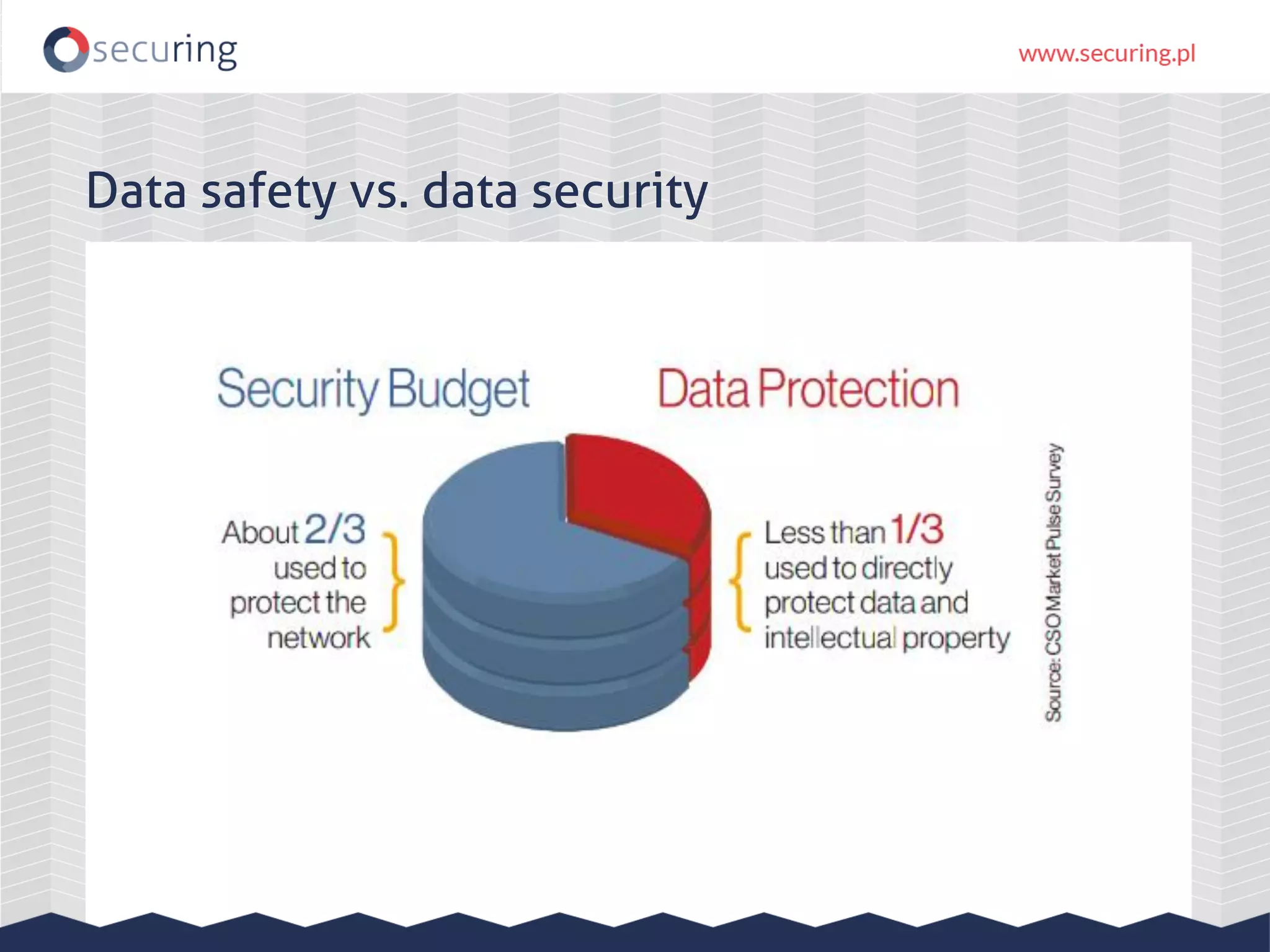
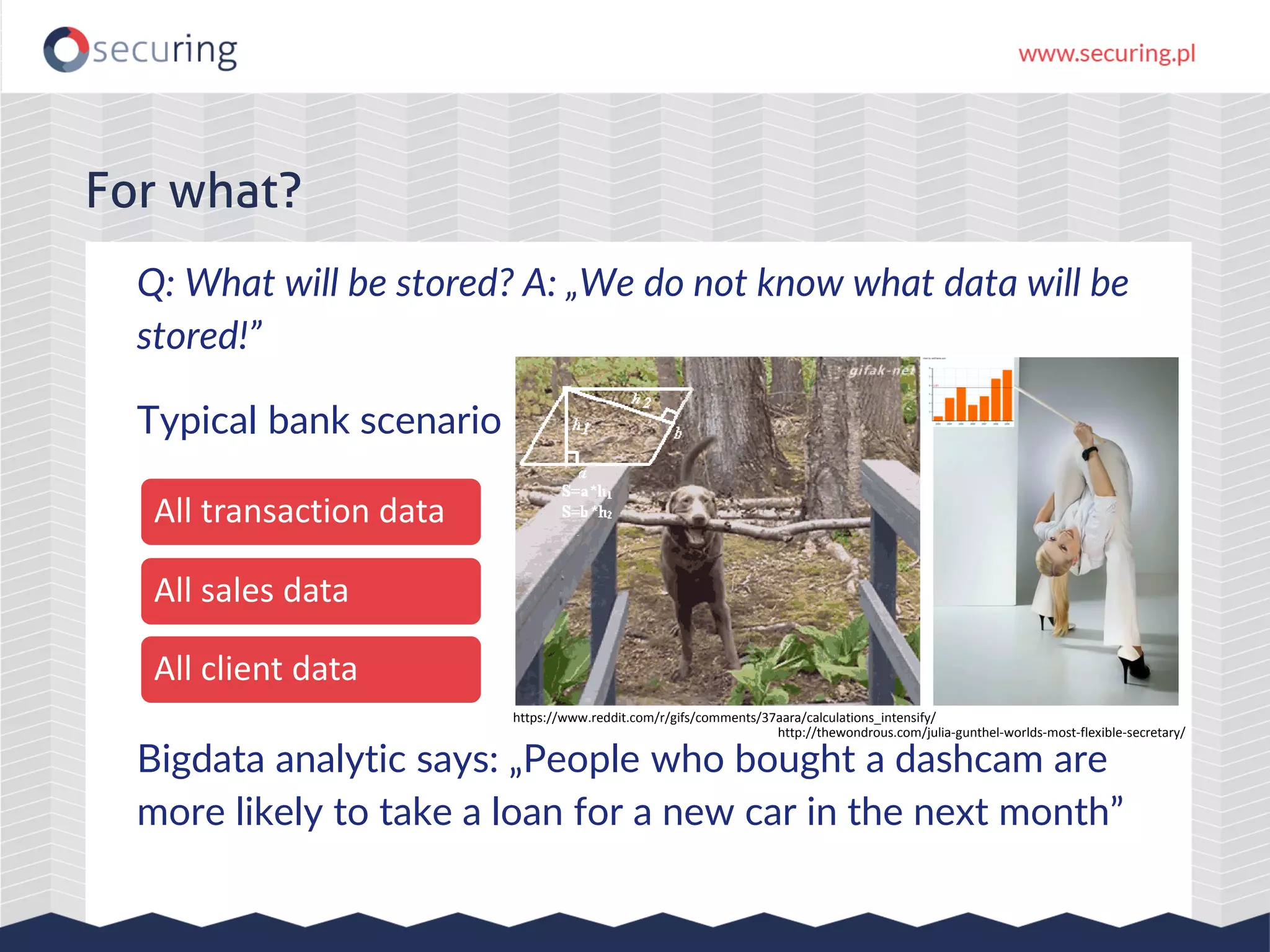
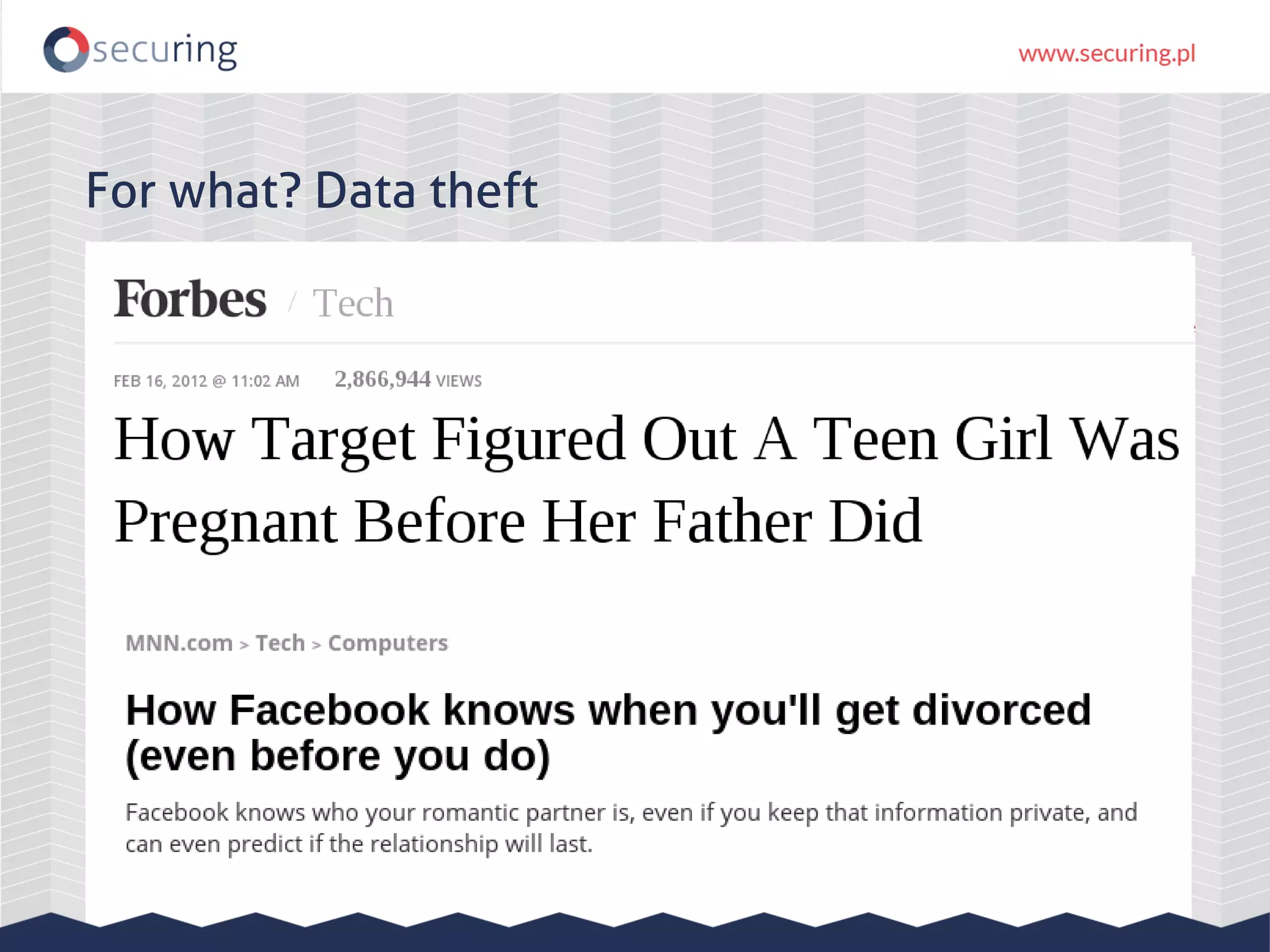
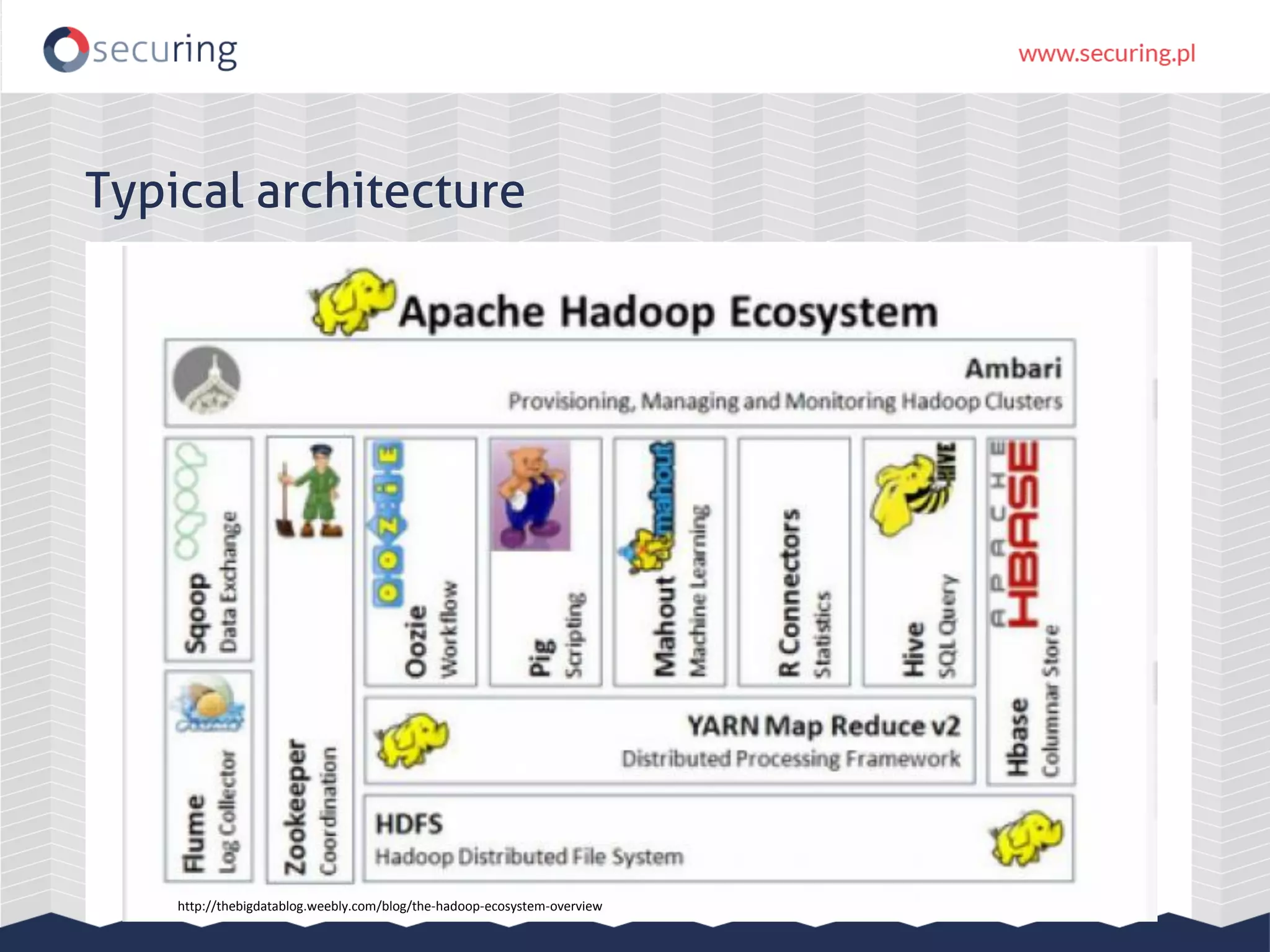
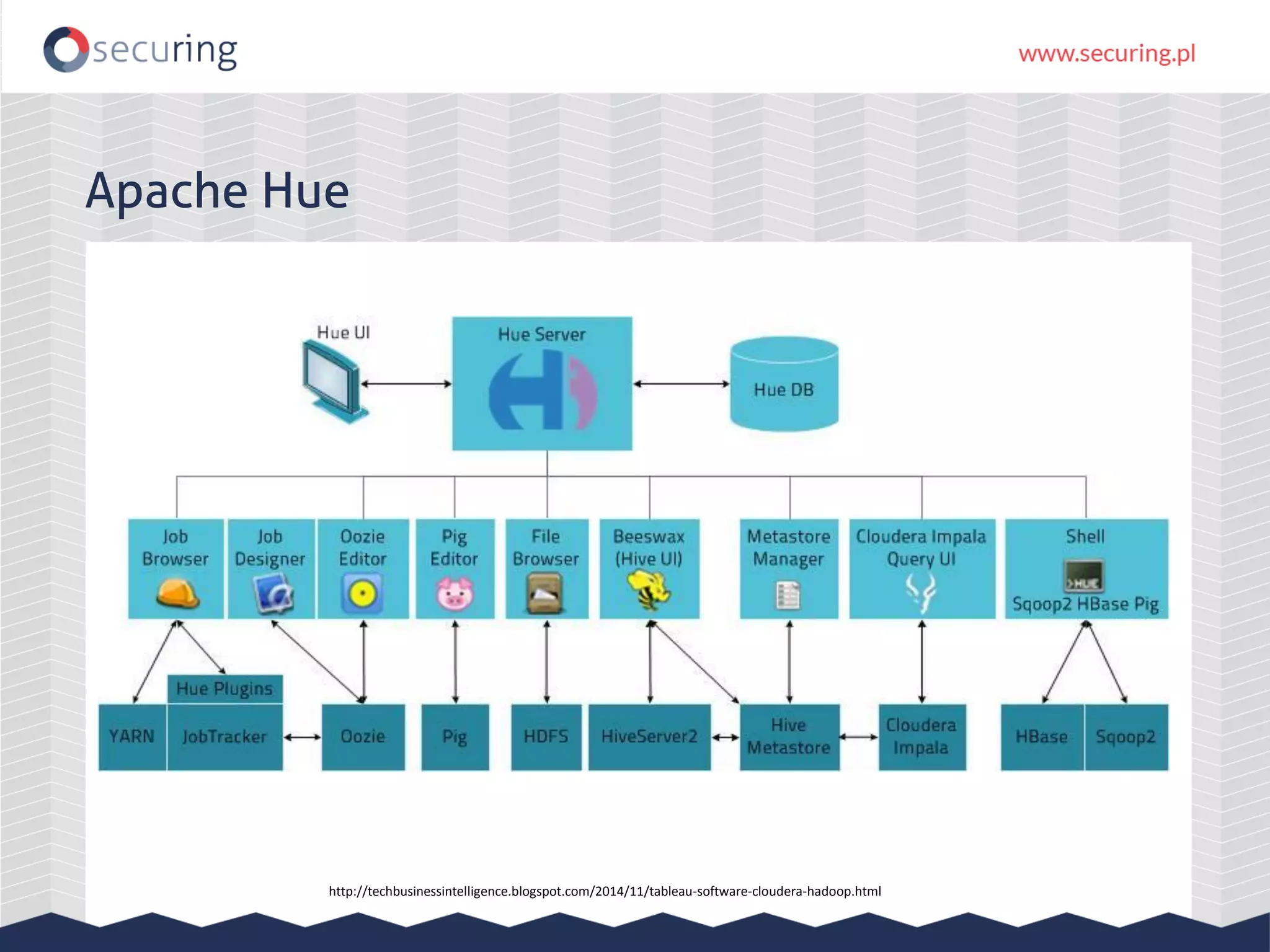
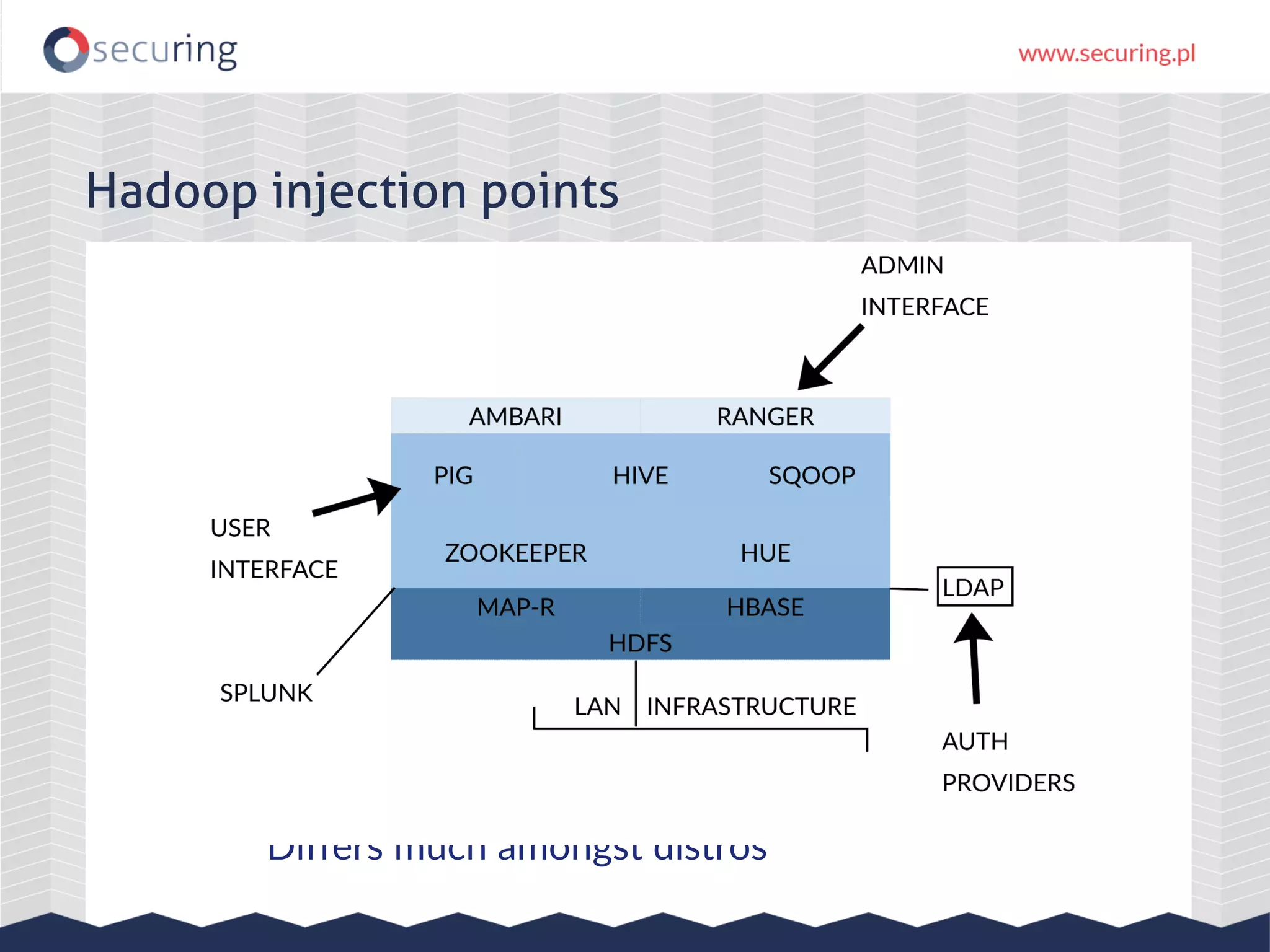
The document discusses the security vulnerabilities within Hadoop and big data environments, focusing on risks such as excessive permissions, outdated software, and common web vulnerabilities. It provides an overview of various Hadoop components and attacks, along with recommendations for safeguarding big data environments through tight network access and regular penetration testing. The author emphasizes the need for thorough risk analysis and proactive measures against potential threats to data integrity and confidentiality.









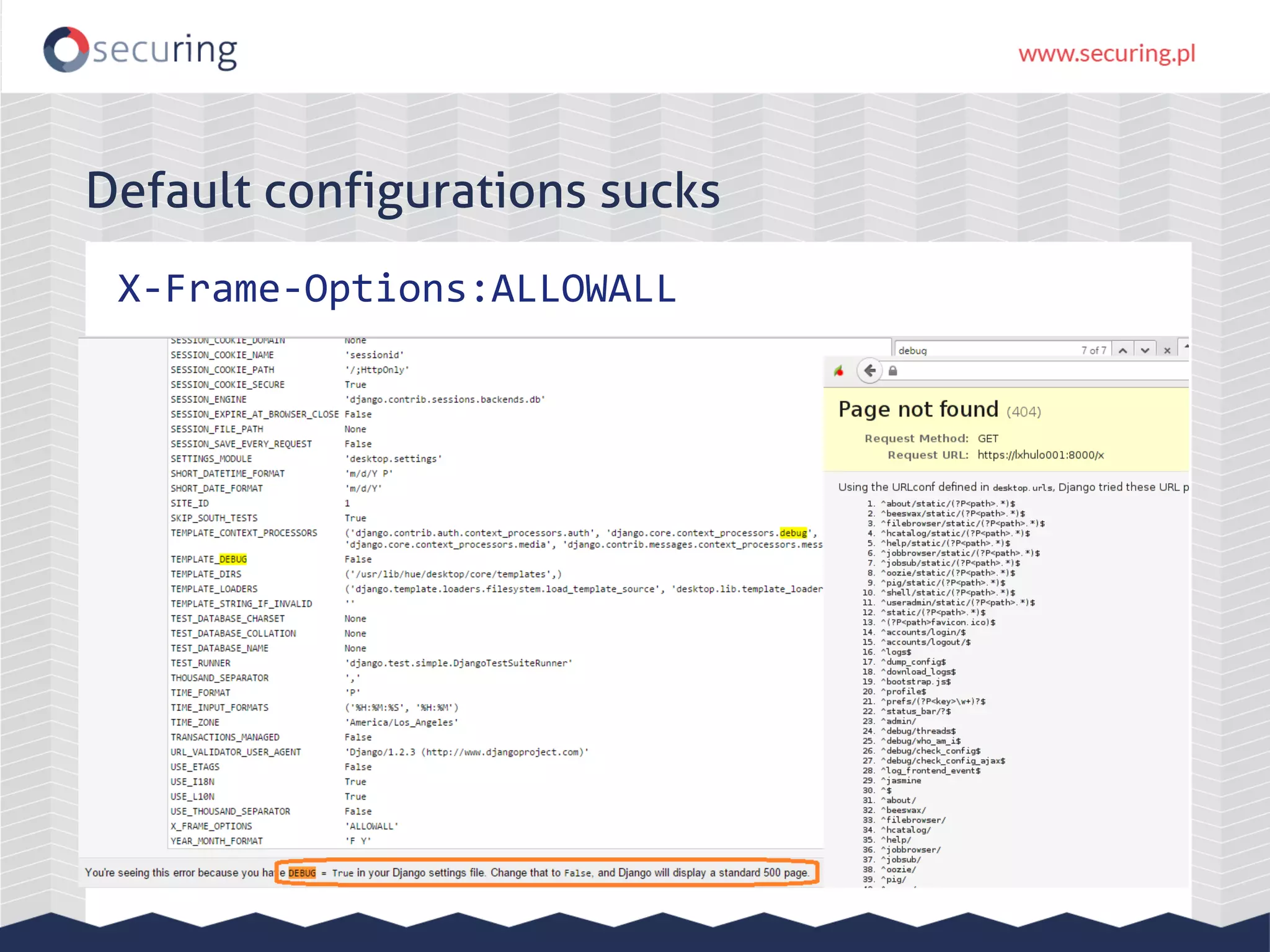
![Apache Hue DOM XSS
var _anchor = $("a[name='" +
decodeURIComponent(window.location.hash.subs
tring(1)) + "']").last();
Payload: URL/help/#<img src="x"
onerror="alert(1)">
H
D
A
E
U](https://image.slidesharecdn.com/zeronights-151205115852-lva1-app6891/75/Zeronights-2015-Big-problems-with-big-data-Hadoop-interfaces-security-44-2048.jpg)