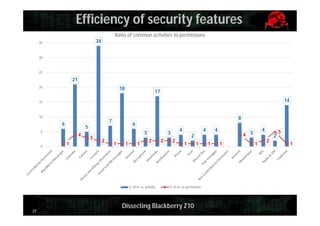
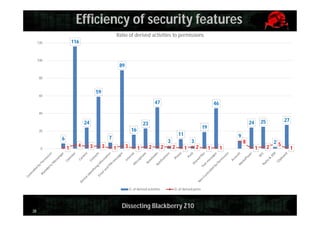
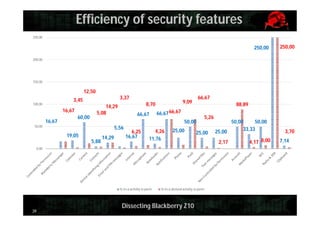
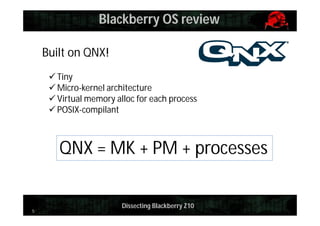
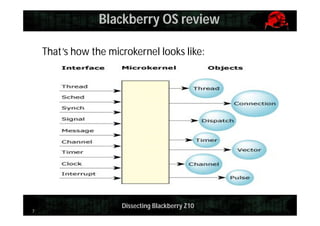
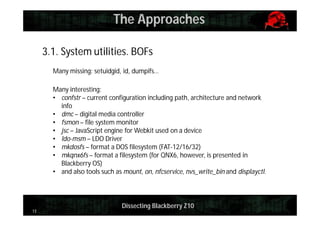
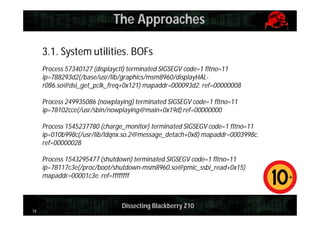
This document provides an overview and agenda for dissecting the security of the Blackberry Z10 mobile device. It begins with a review of the Blackberry OS which is built on QNX. It then discusses gaining shell access, various approaches for analyzing the device such as fuzzing and exploiting system utilities, examining the firmware, analyzing the browser and application-level security. It also covers interacting with APIs and MDM capabilities. Metrics are provided on the efficiency of security features compared to other mobile platforms. The document aims to serve as a guide for further researching the Blackberry Z10.














![Firmware from the inside
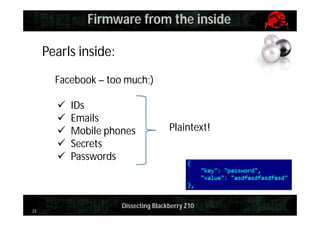
Pearls inside:
Protected tools can be launched now!
persist-tool:
insecure syscalls
can be reproduced
(read/dump data)
21
Bootrom Version: 0x0523001D (5.35.0.29)
DeviceString: RIM BlackBerry Device
BuildUserName: ec_agent
BuildDate: Nov 3 2012
…
IsInsecureDevice: false
HWVersionOffset: 0x000000D4
NumberHWVEntries: 0x00000014
MemCfgTableOffset: 0x000000FC
MemCfgTableSize: 0x00000100
Drivers: 0x00000010 [ MMC ]
LDRBlockAddr: 0x2E02FE00
BootromSize: 0x00080000
BRPersistAddr: 0x2E0AFC00
Dissecting Blackberry Z10](https://image.slidesharecdn.com/28pdf-29-20yury-chemerkin-defcon-2013-140202131751-phpapp01/85/Pdf-yury-chemerkin-def_con_2013-21-320.jpg)