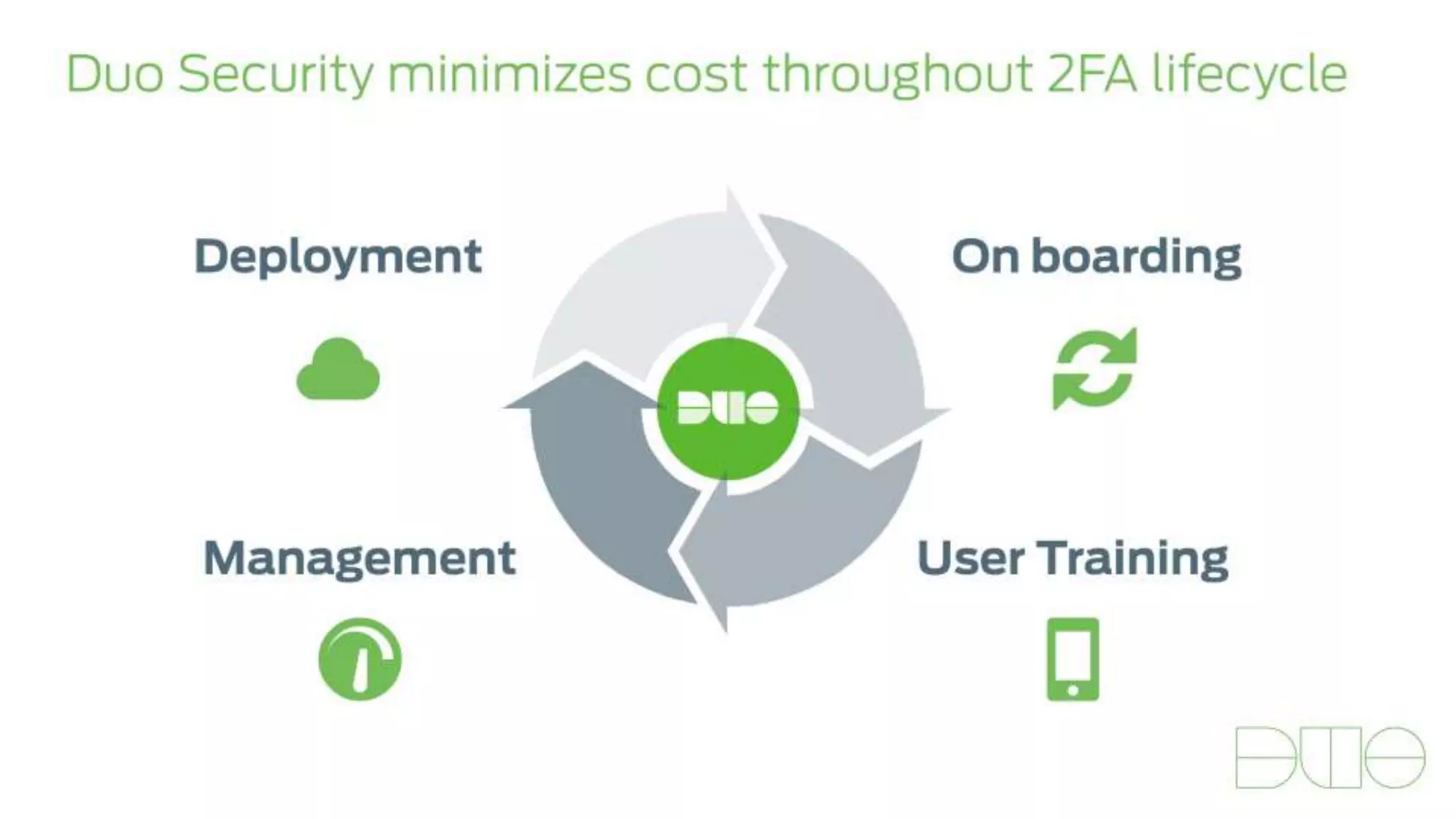
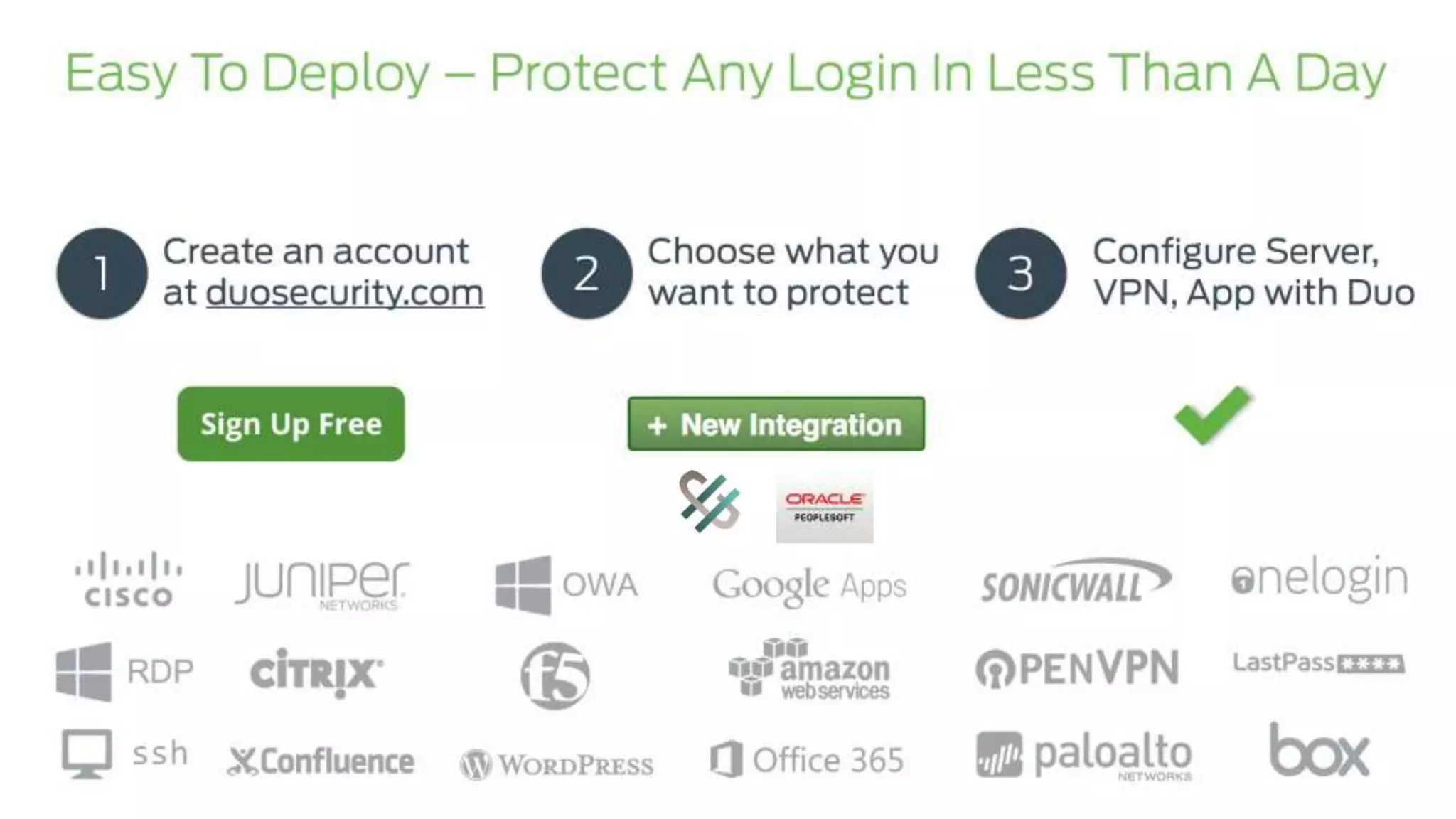
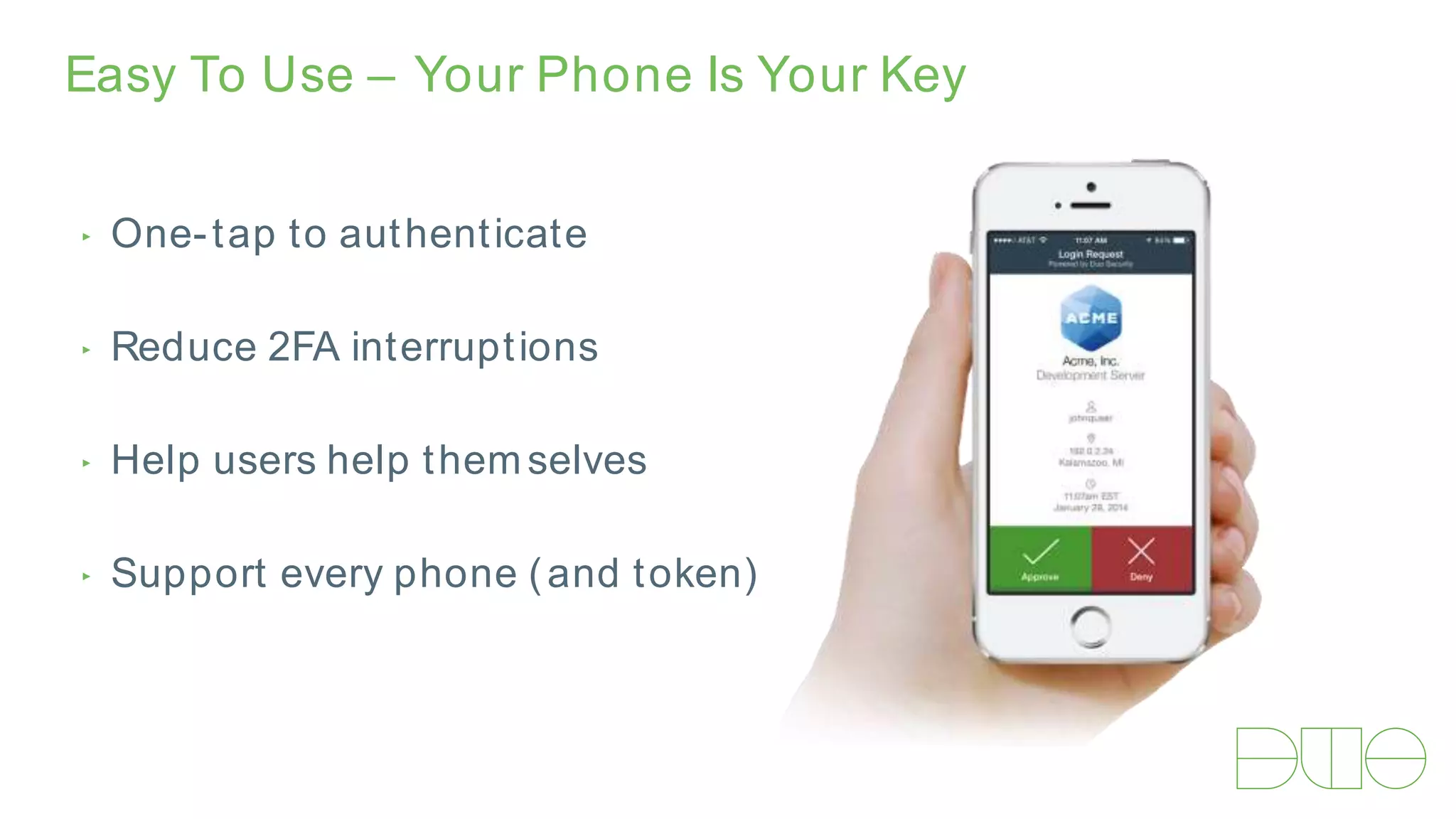
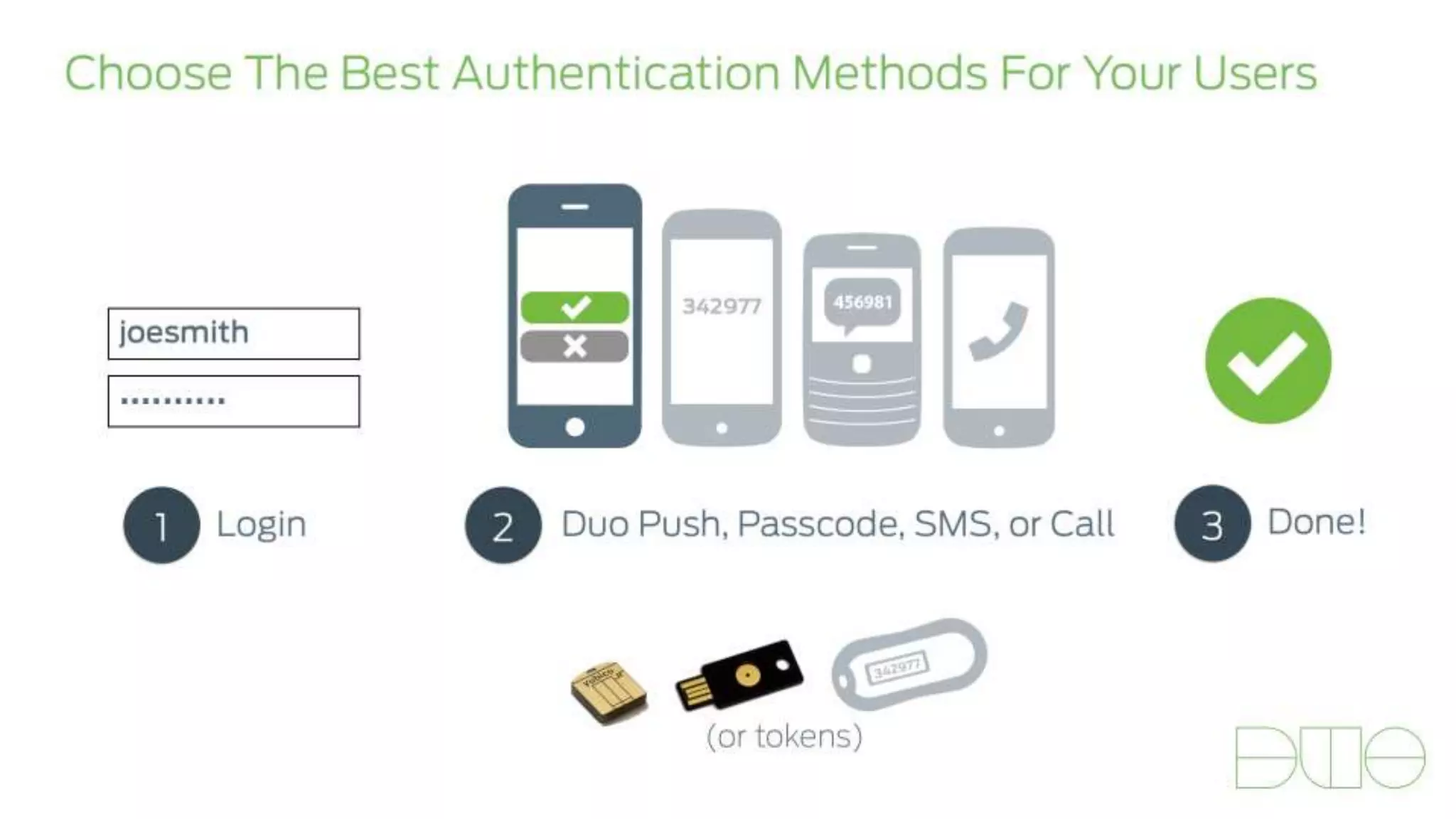
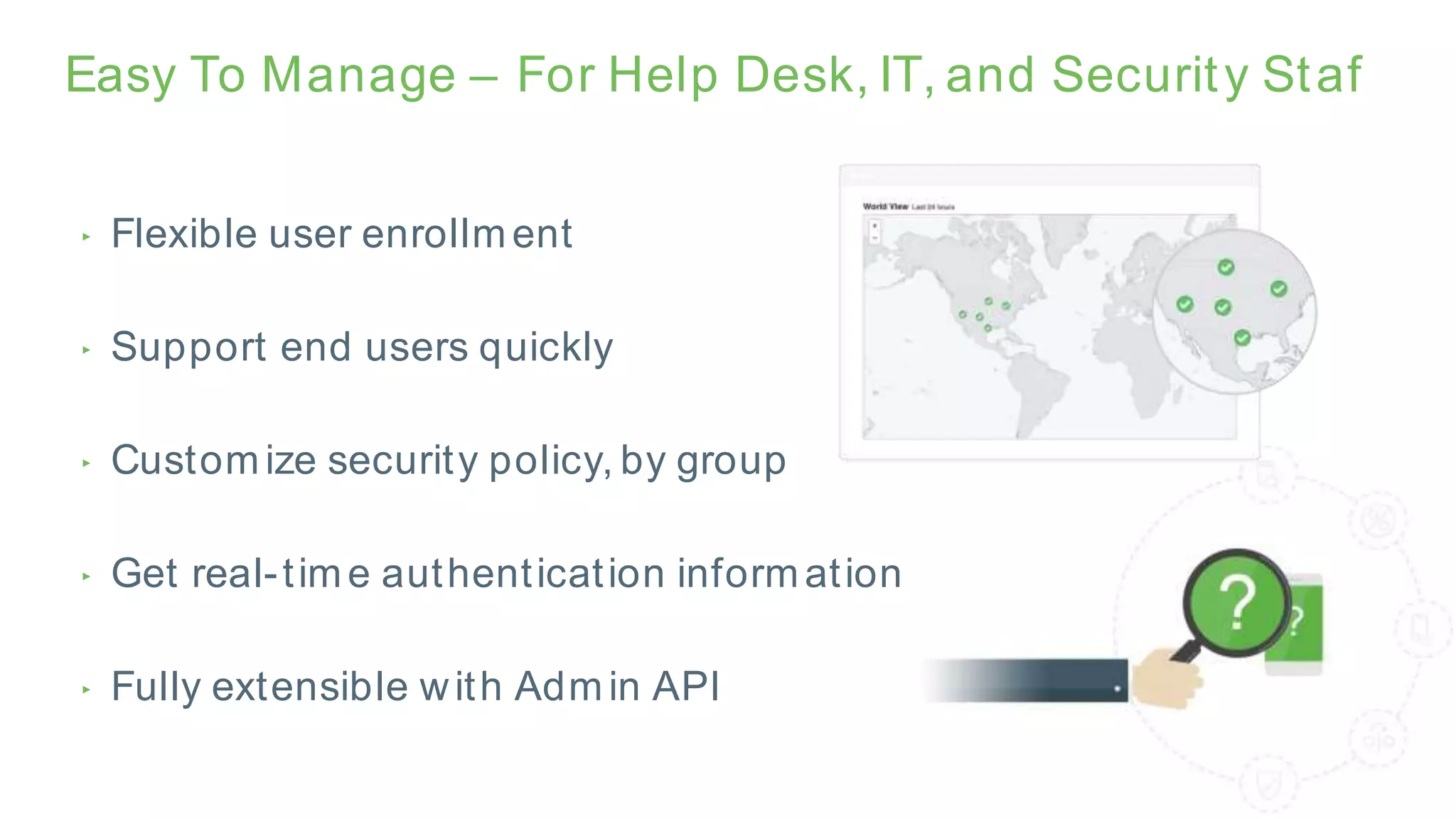
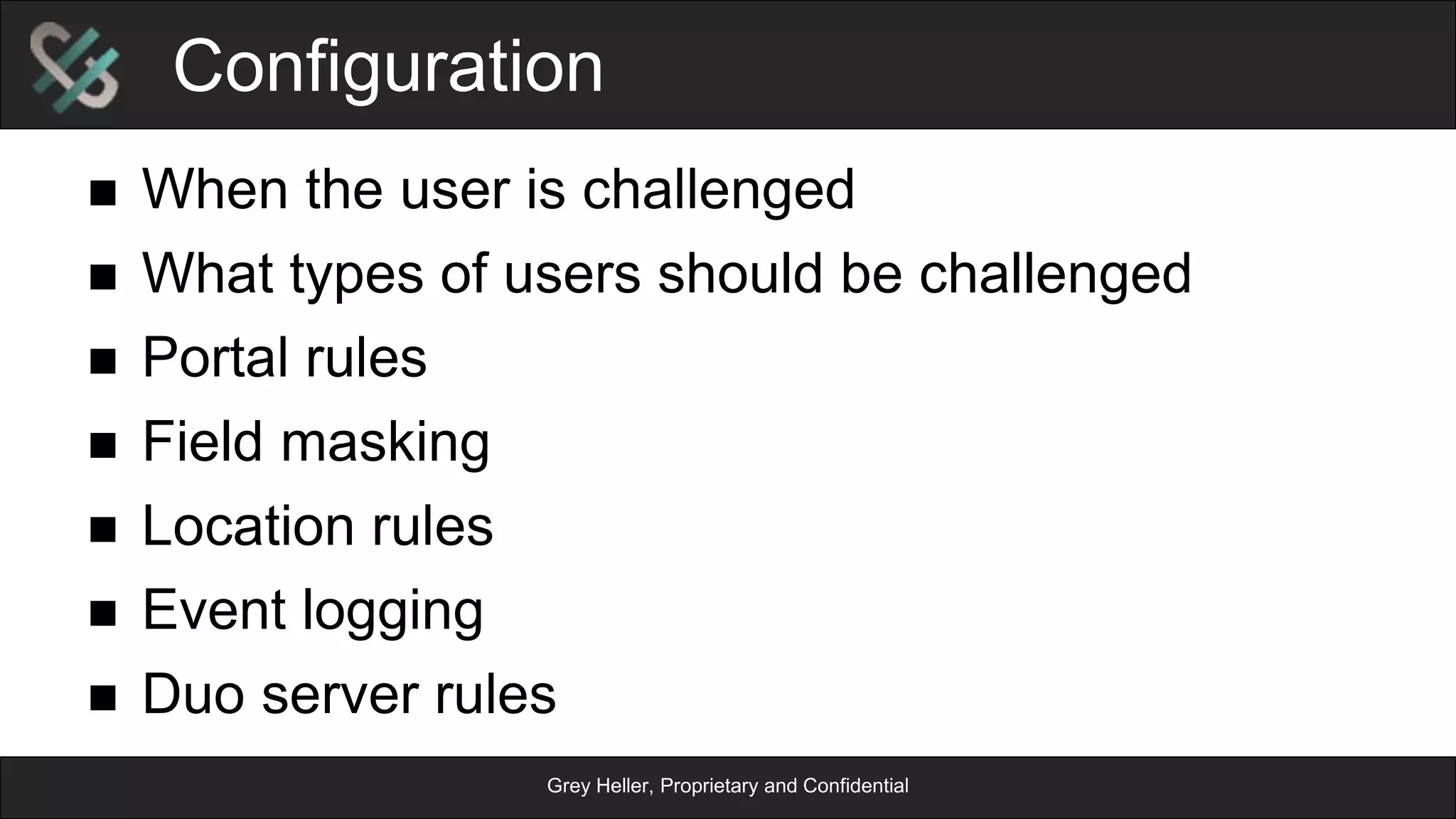
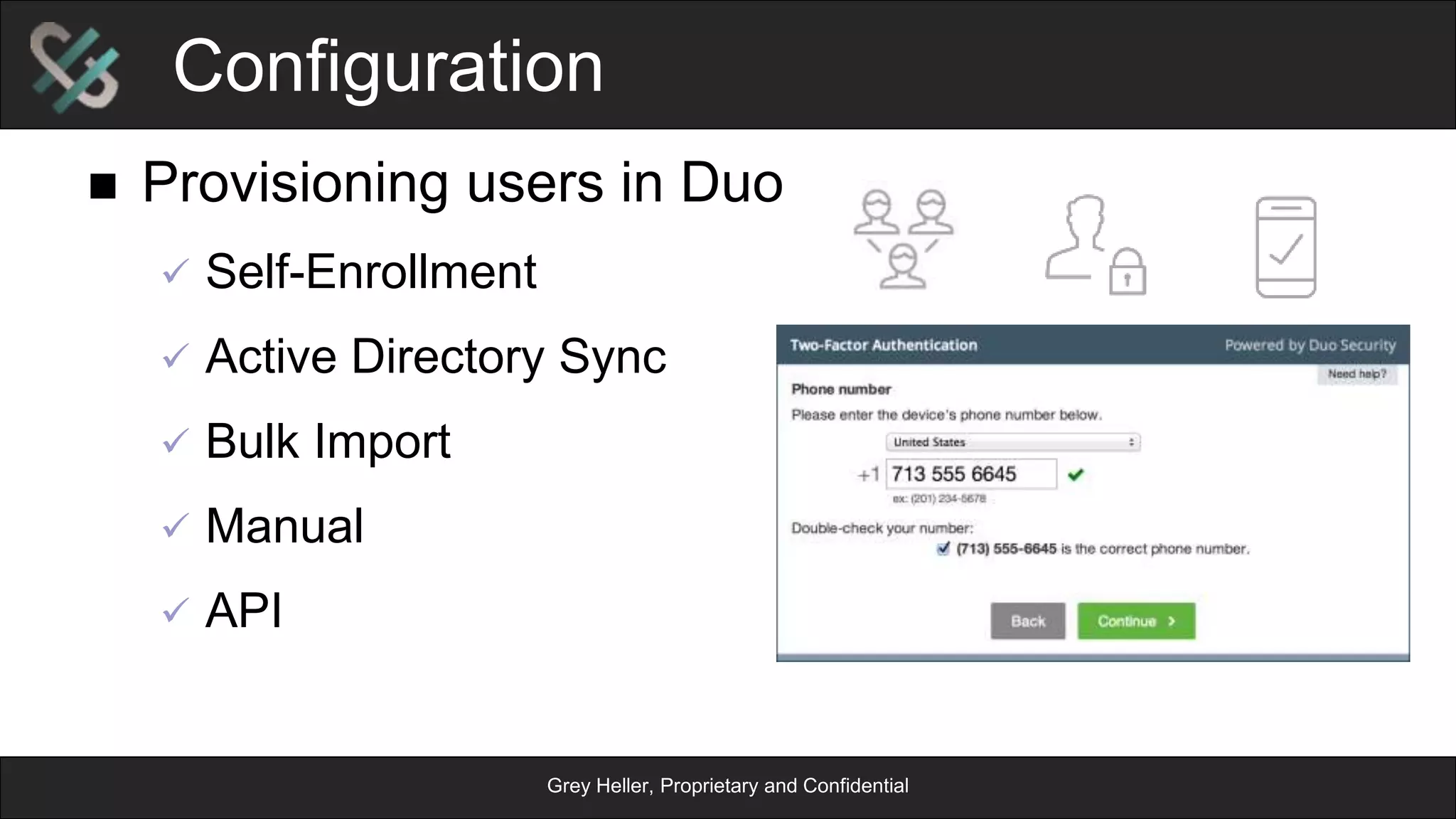
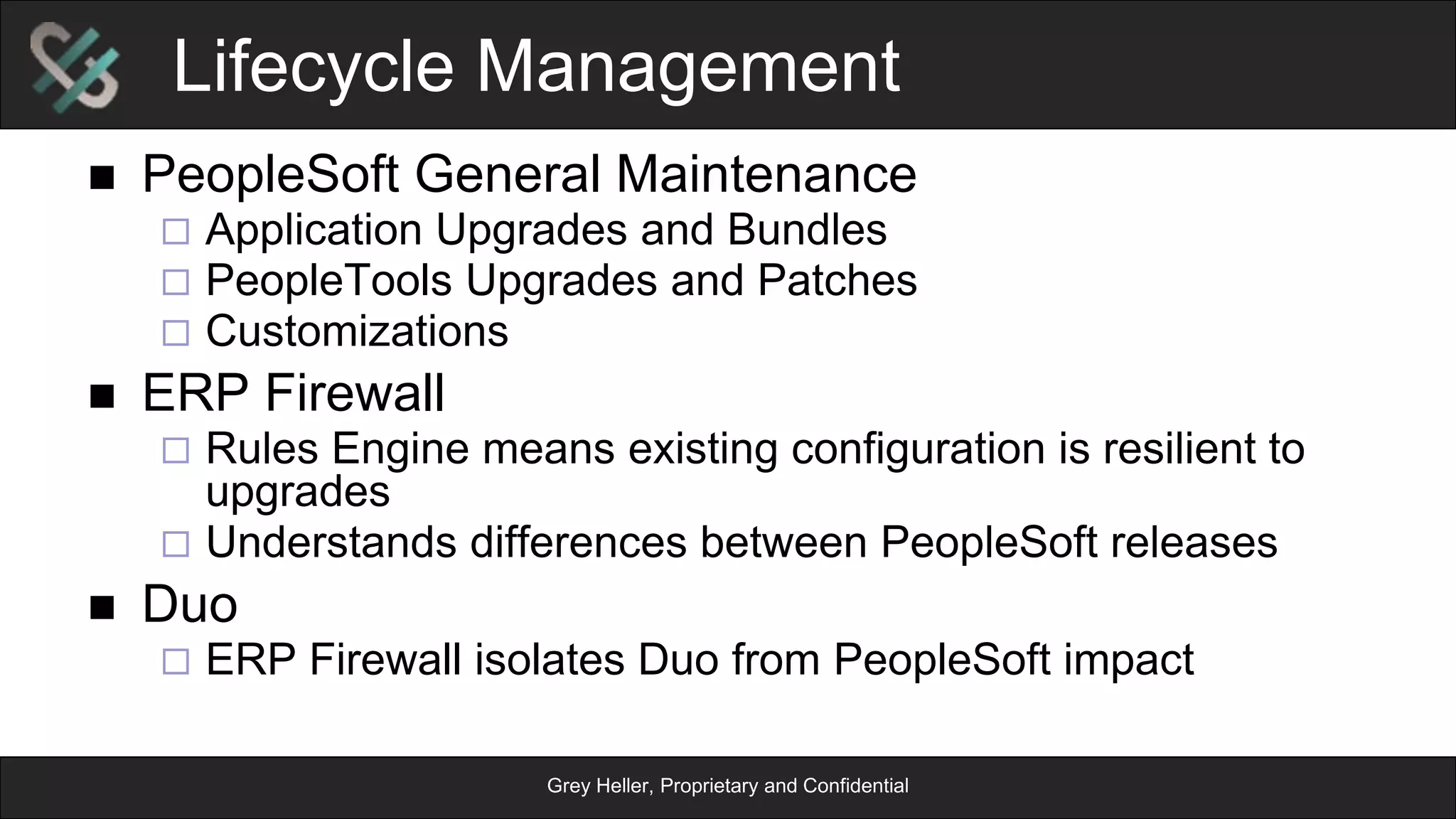
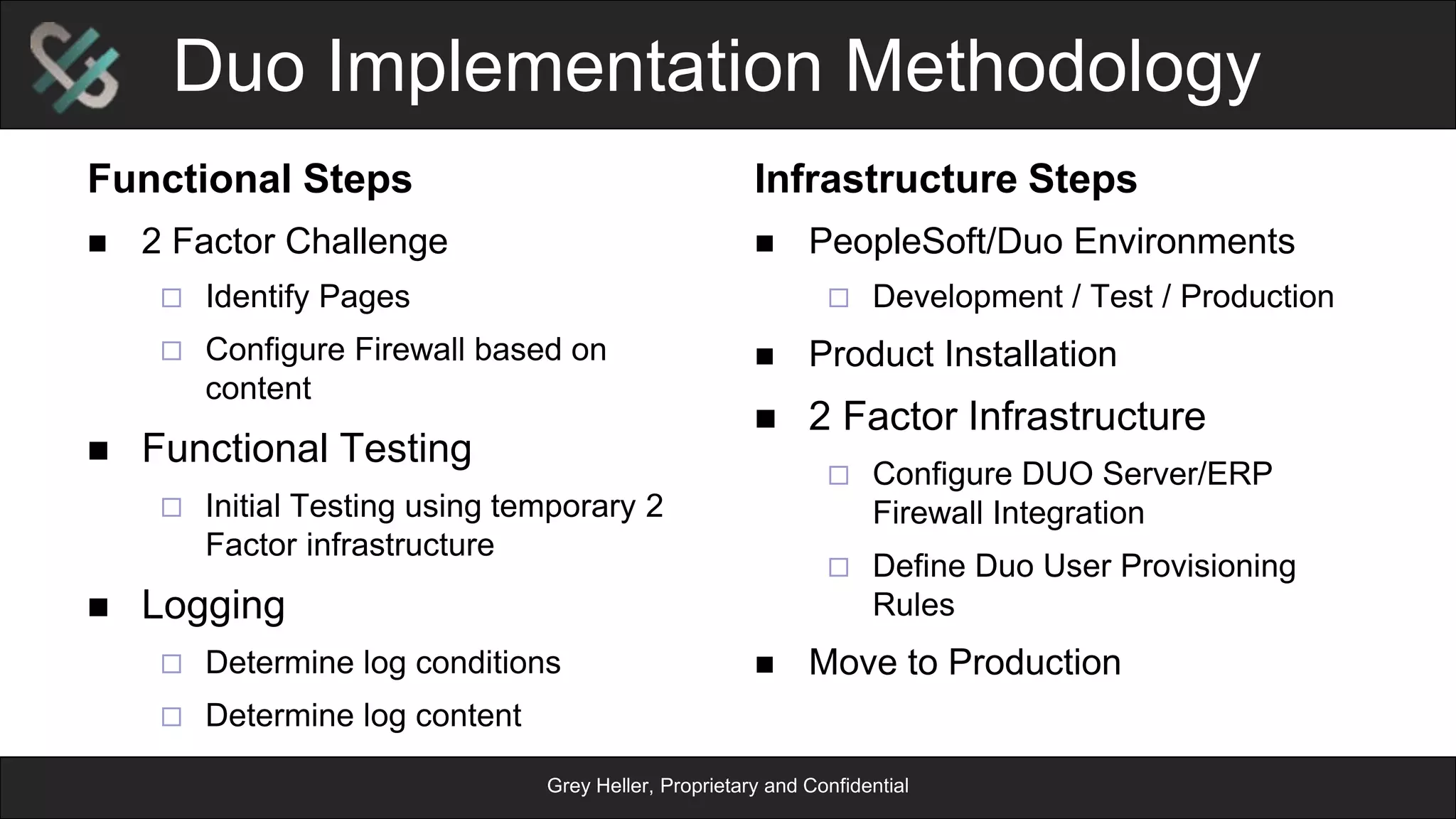
The document provides an overview of Grey Heller and Duo Security, focusing on security challenges and the implementation of two-factor authentication to improve protection against credential theft. It discusses the integration of Duo Security with ERP firewalls to enhance access control, reduce risks for both users and institutions, and offers insights into configuration and lifecycle management. Lastly, it presents the approach for implementing and testing the two-factor authentication system within PeopleSoft environments.