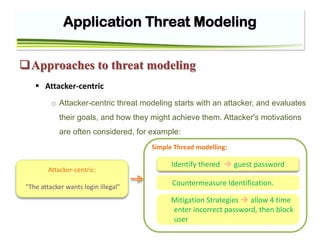
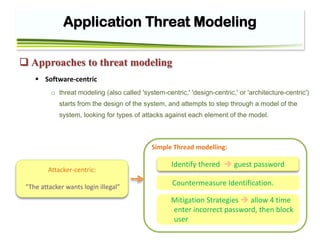
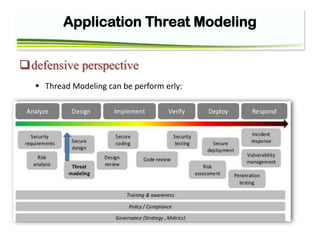
The document discusses application threat modeling for a college library website. It describes decomposing the application into external dependencies, entry points, assets, and trust levels. It then covers determining and ranking threats using STRIDE and ASF categorizations. The document outlines identifying security controls and countermeasures to address vulnerabilities. It provides steps for threat analysis and defining mitigation strategies.