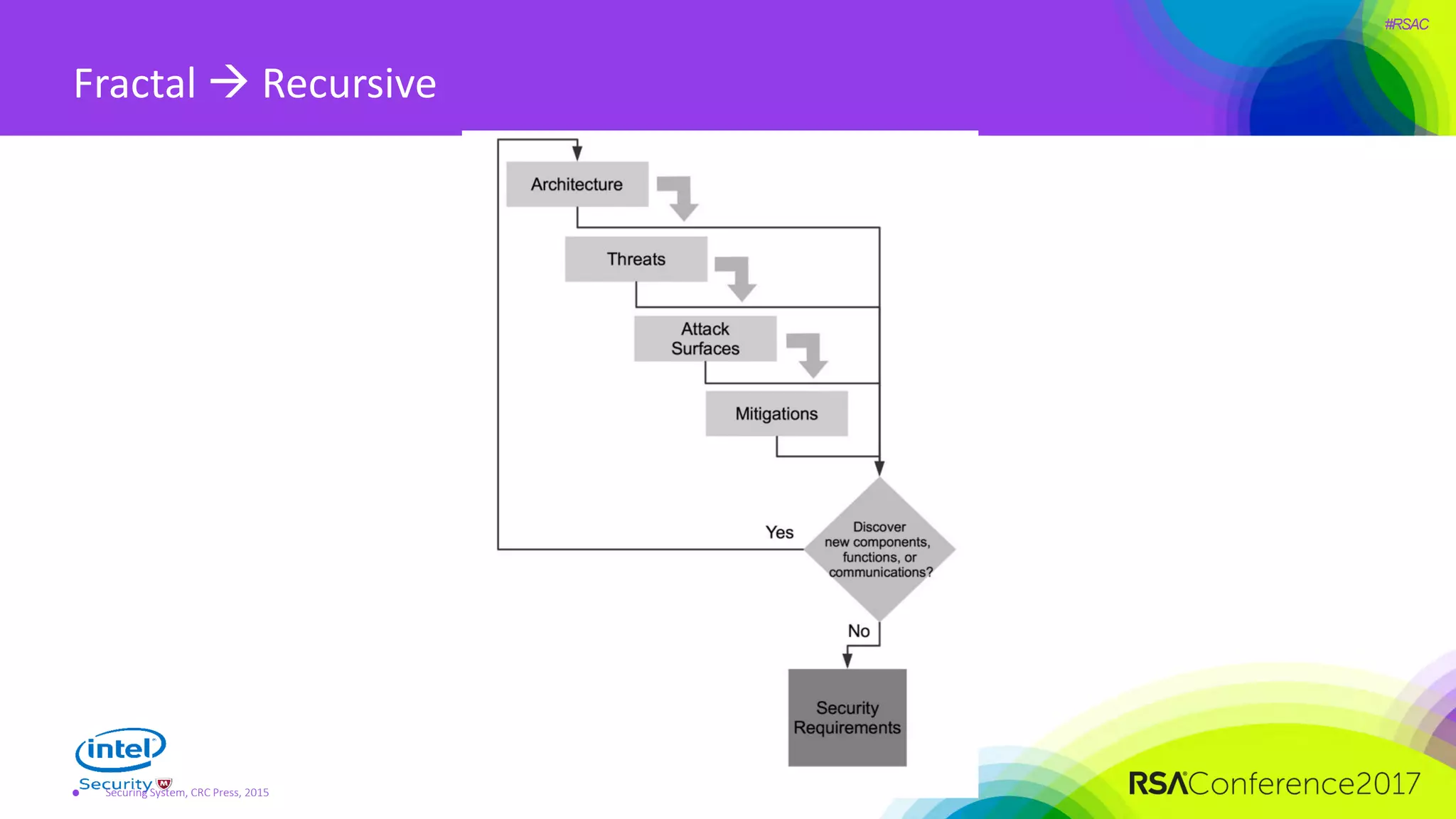
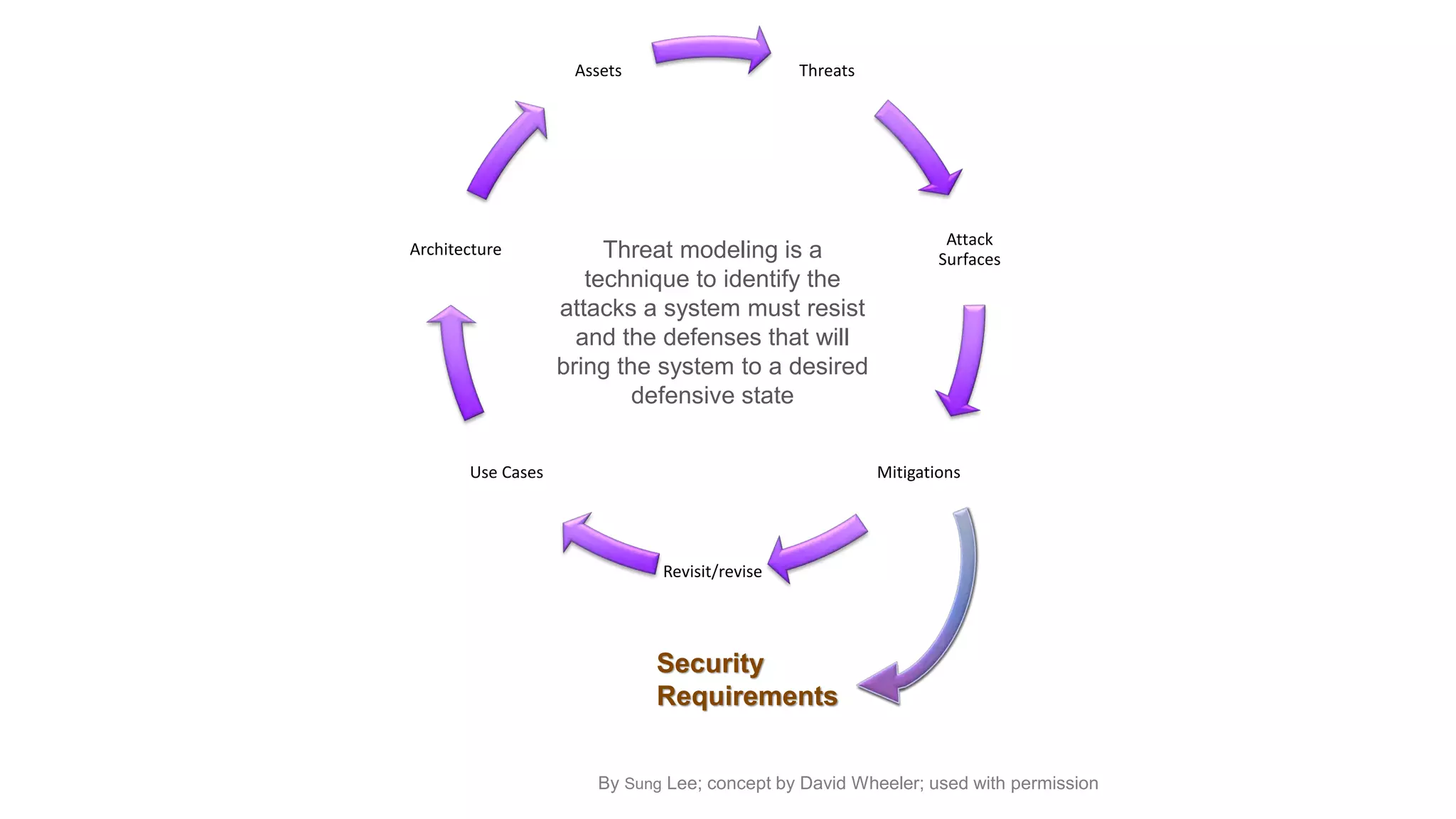
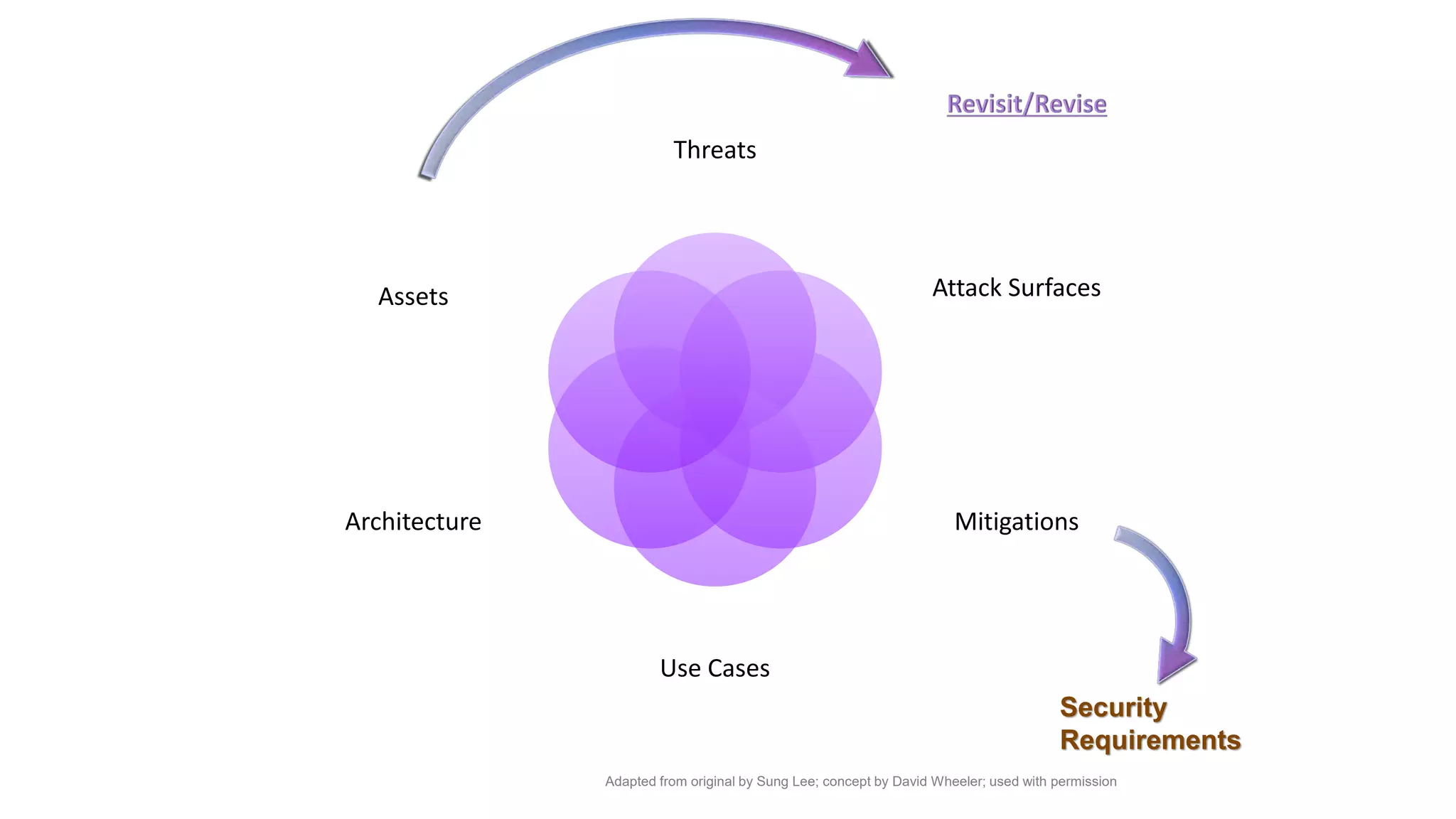
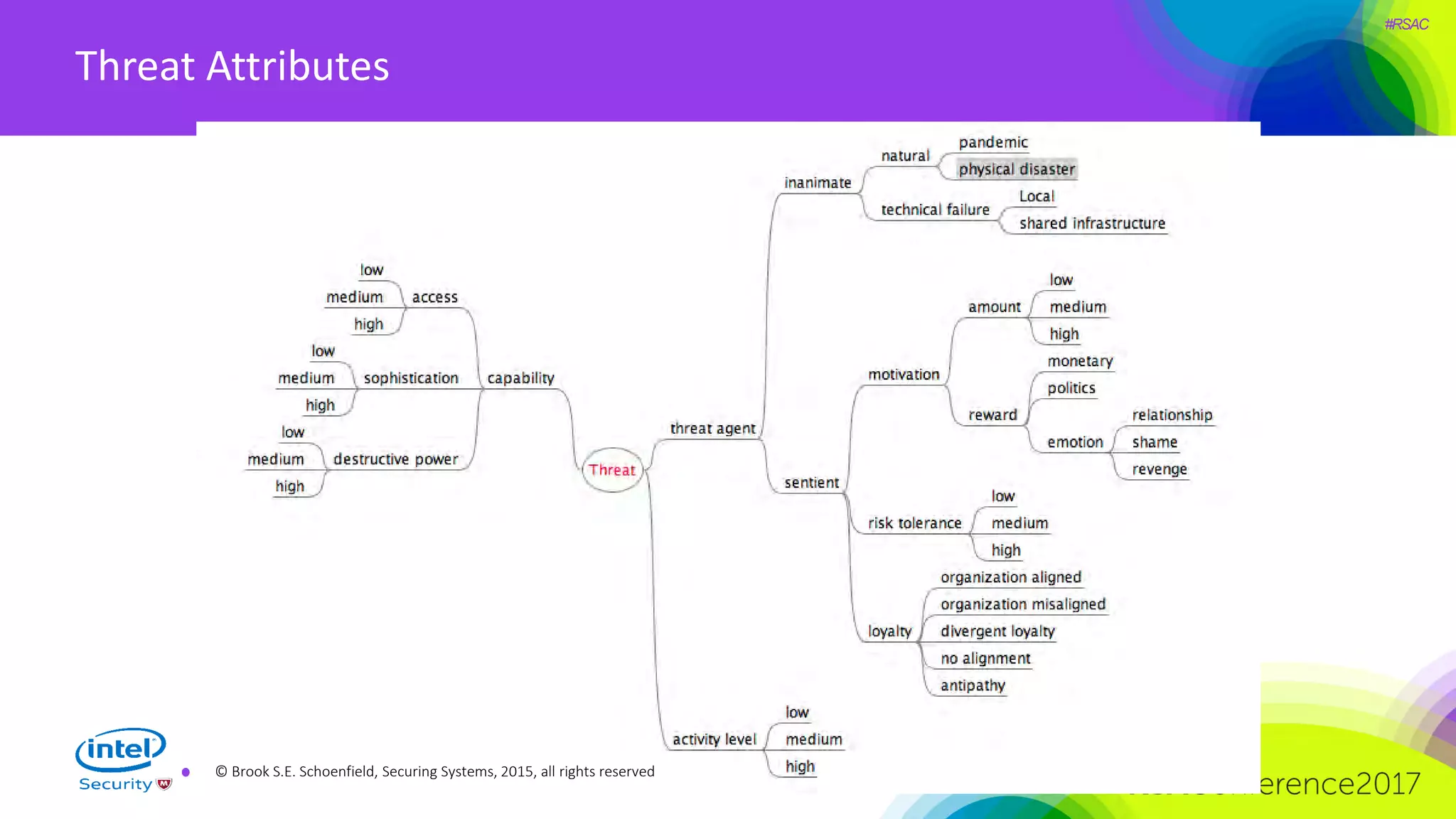
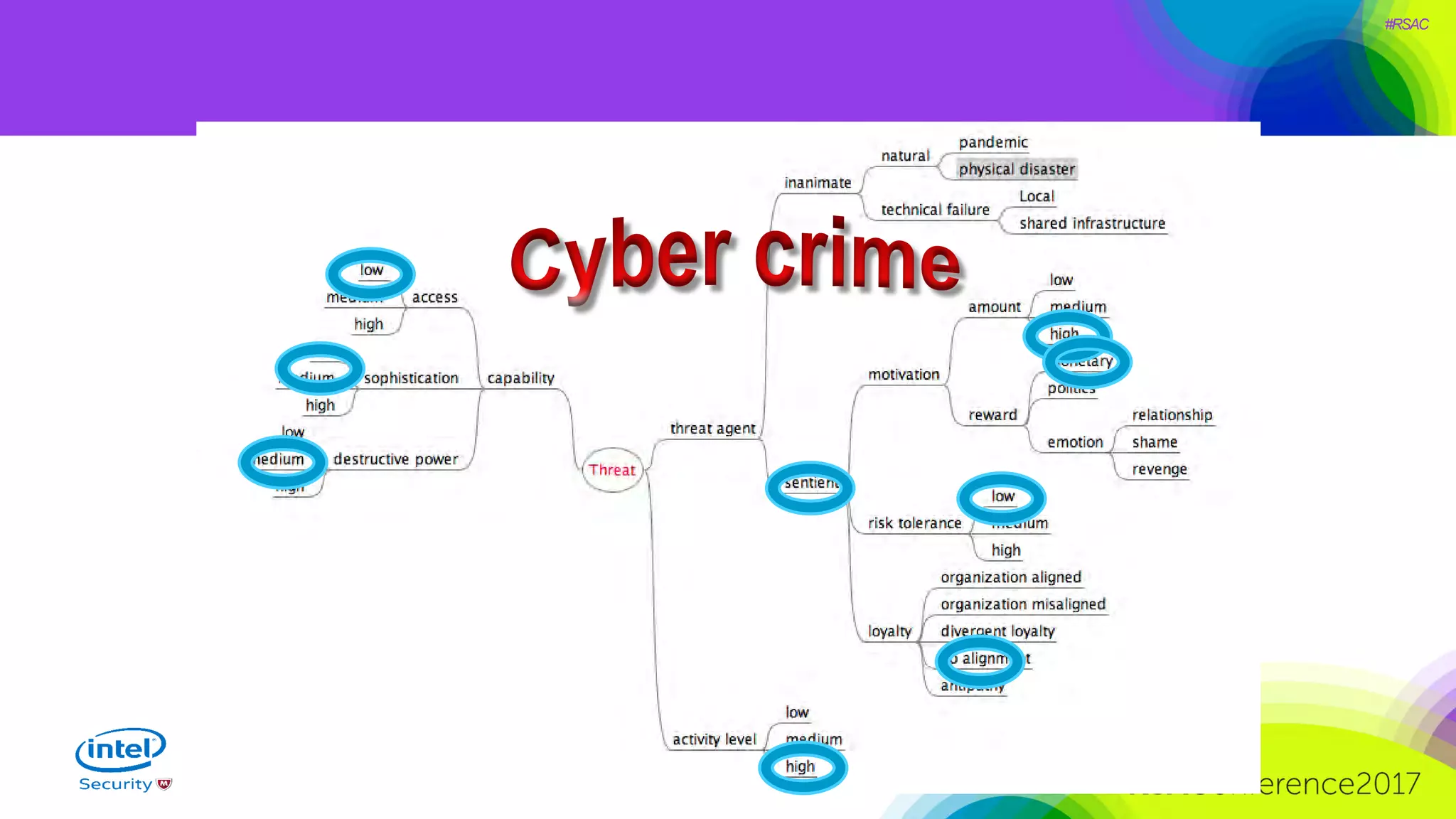
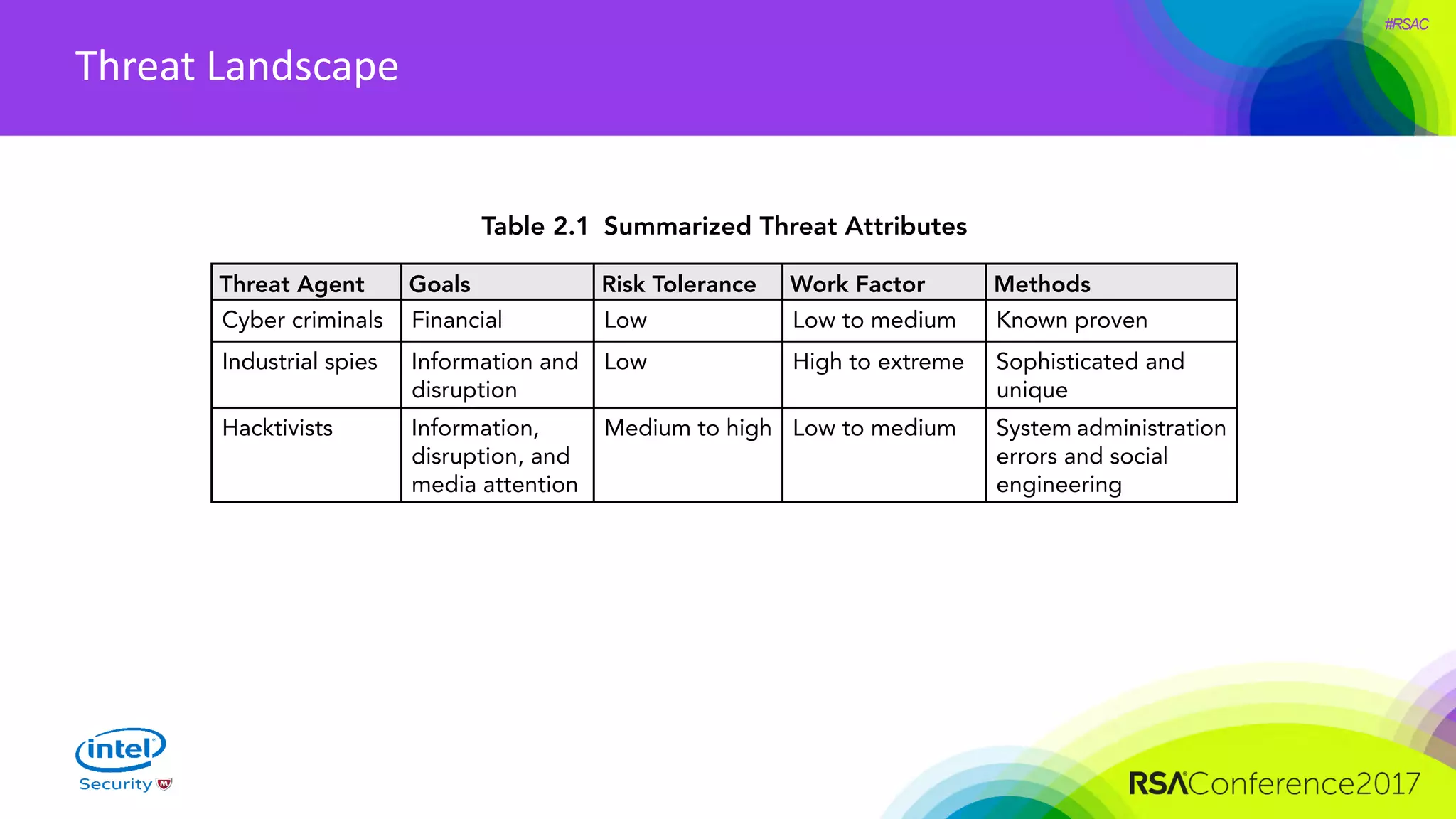
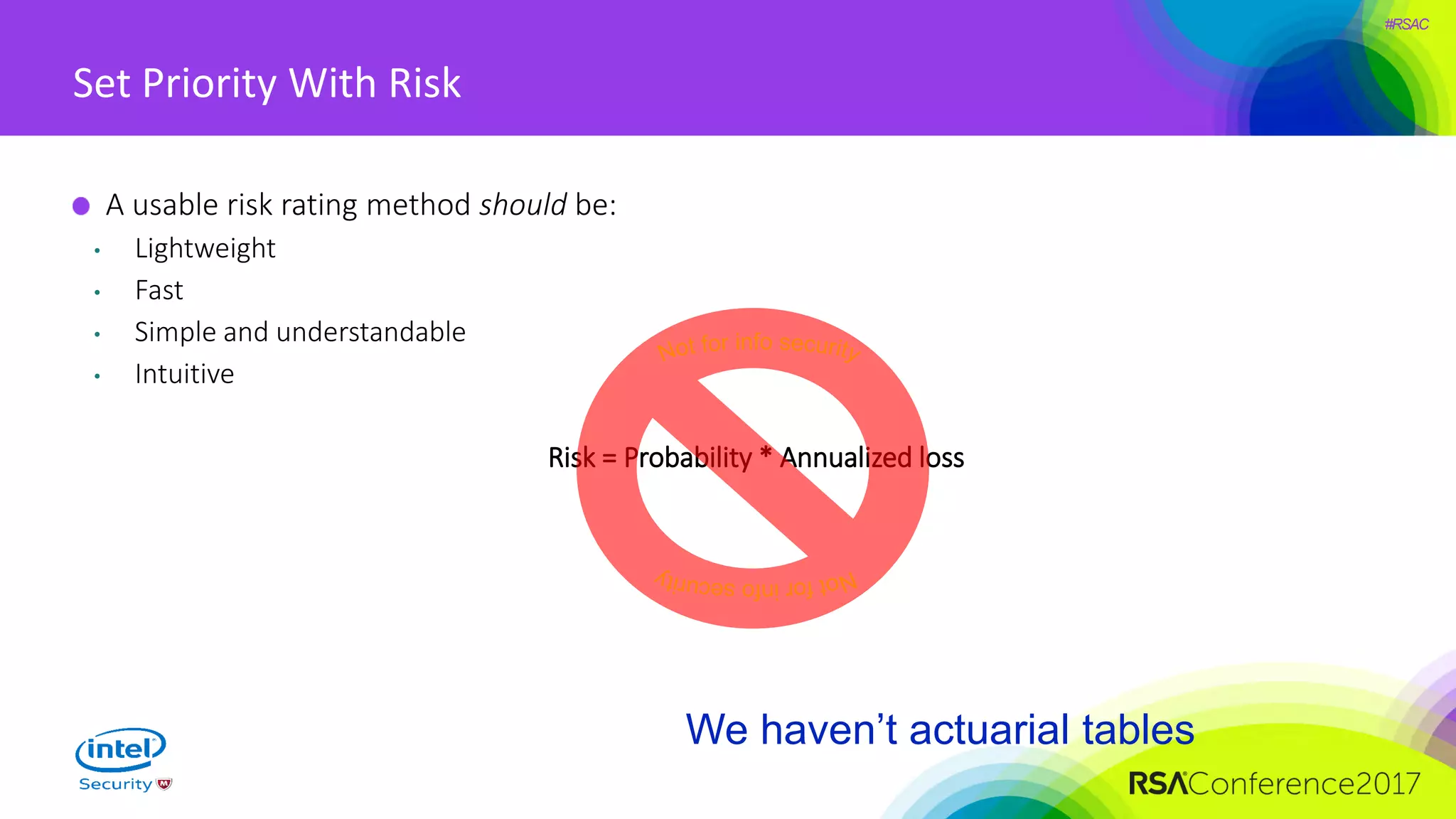
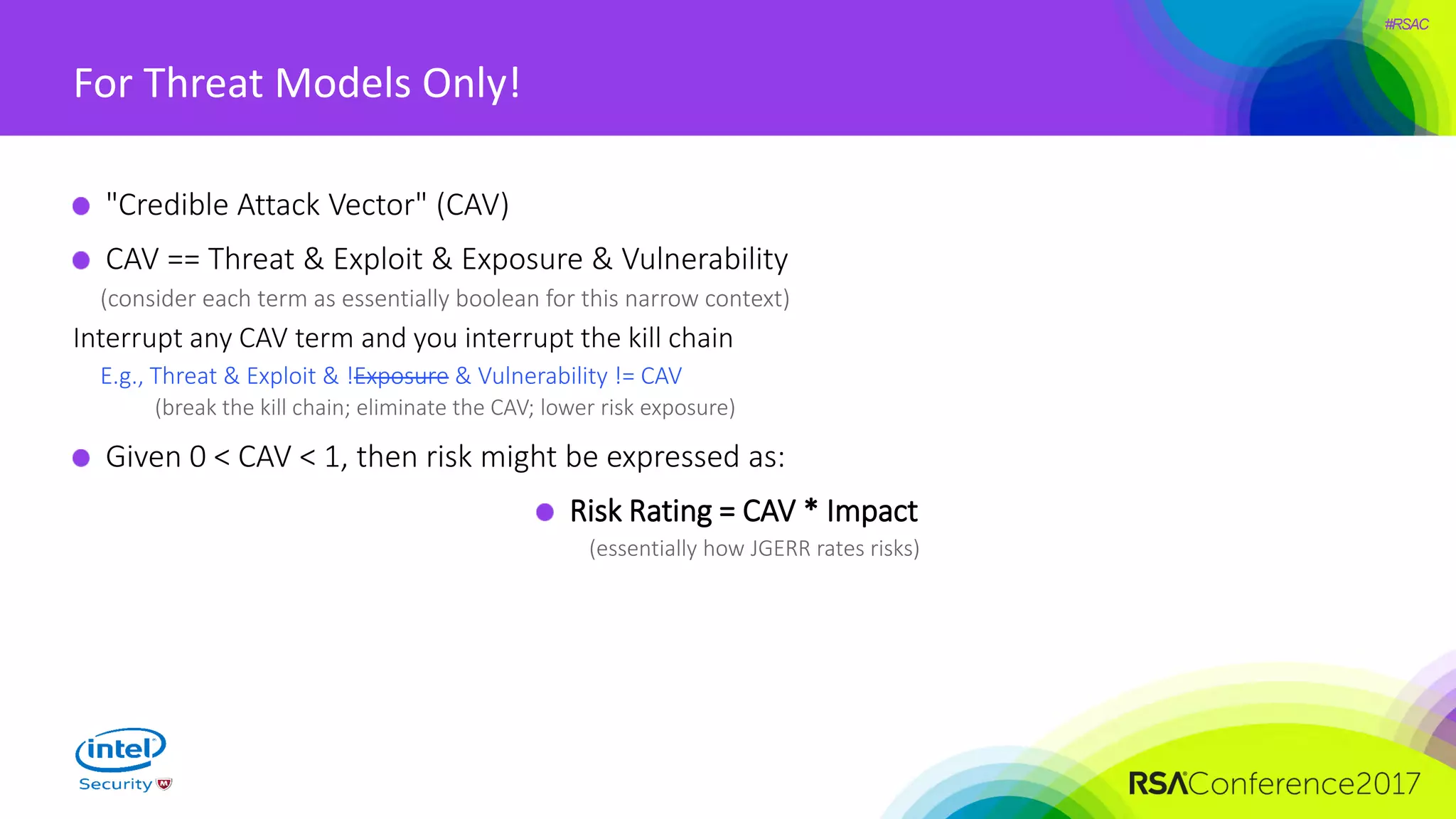
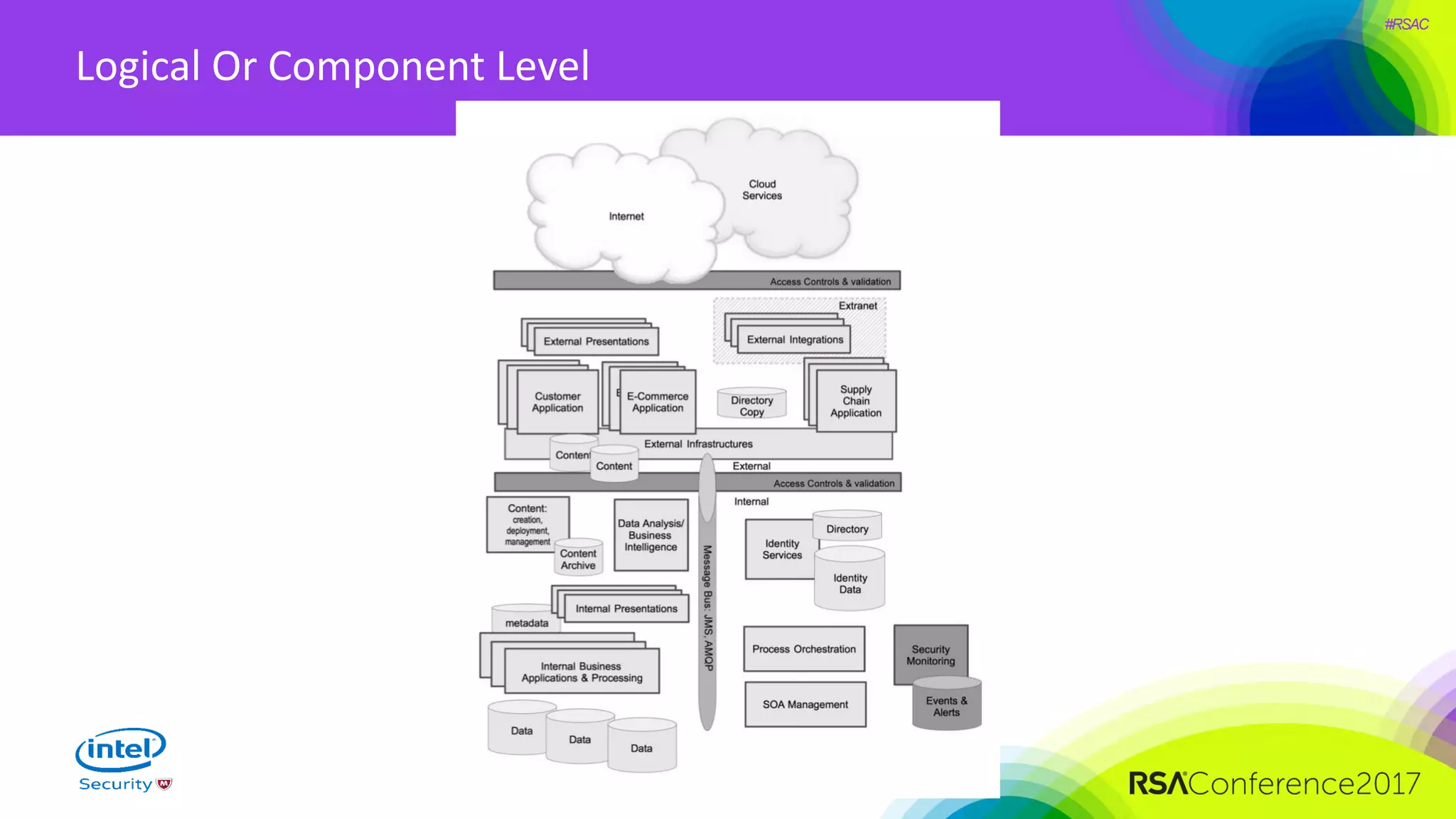
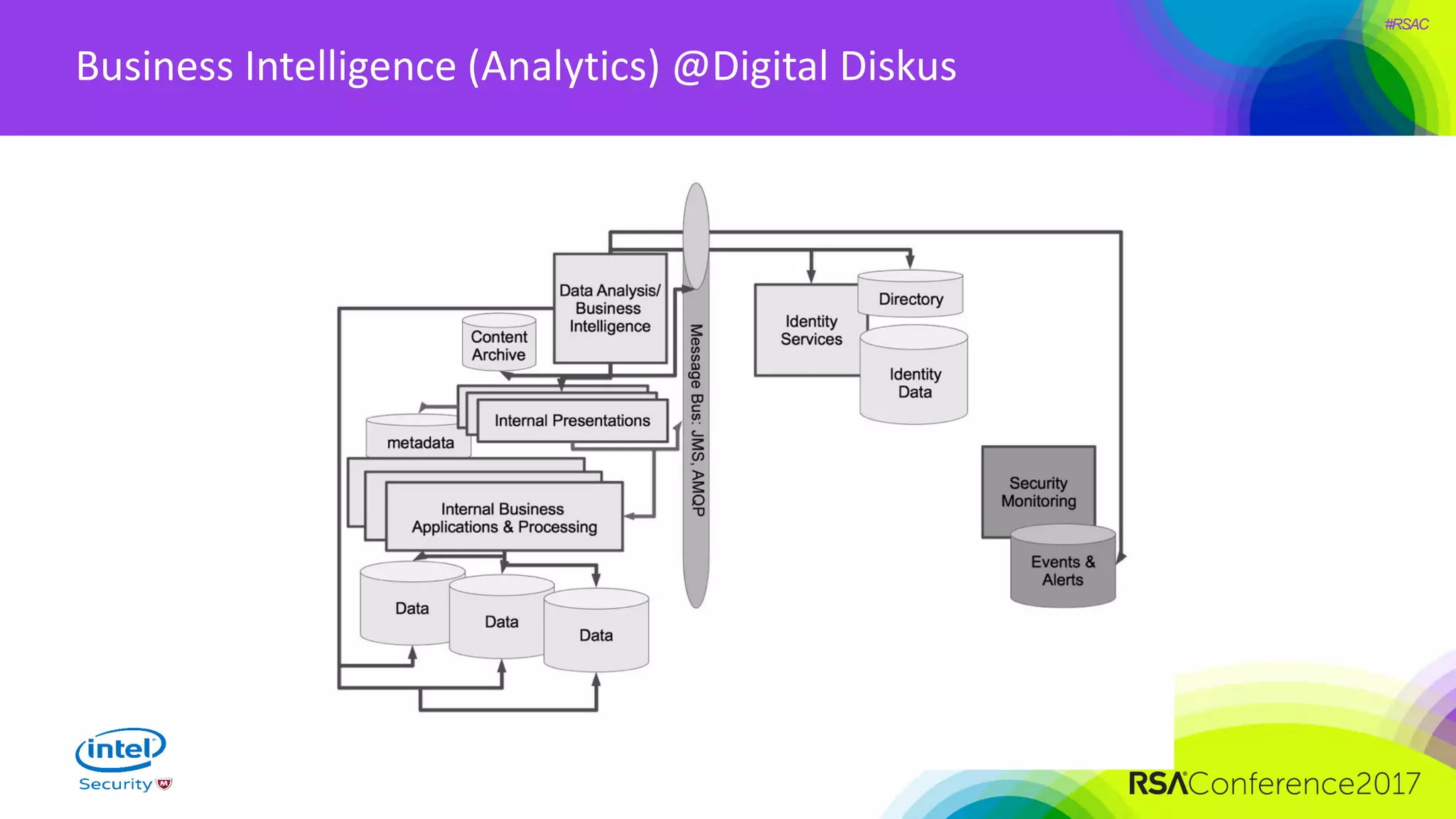
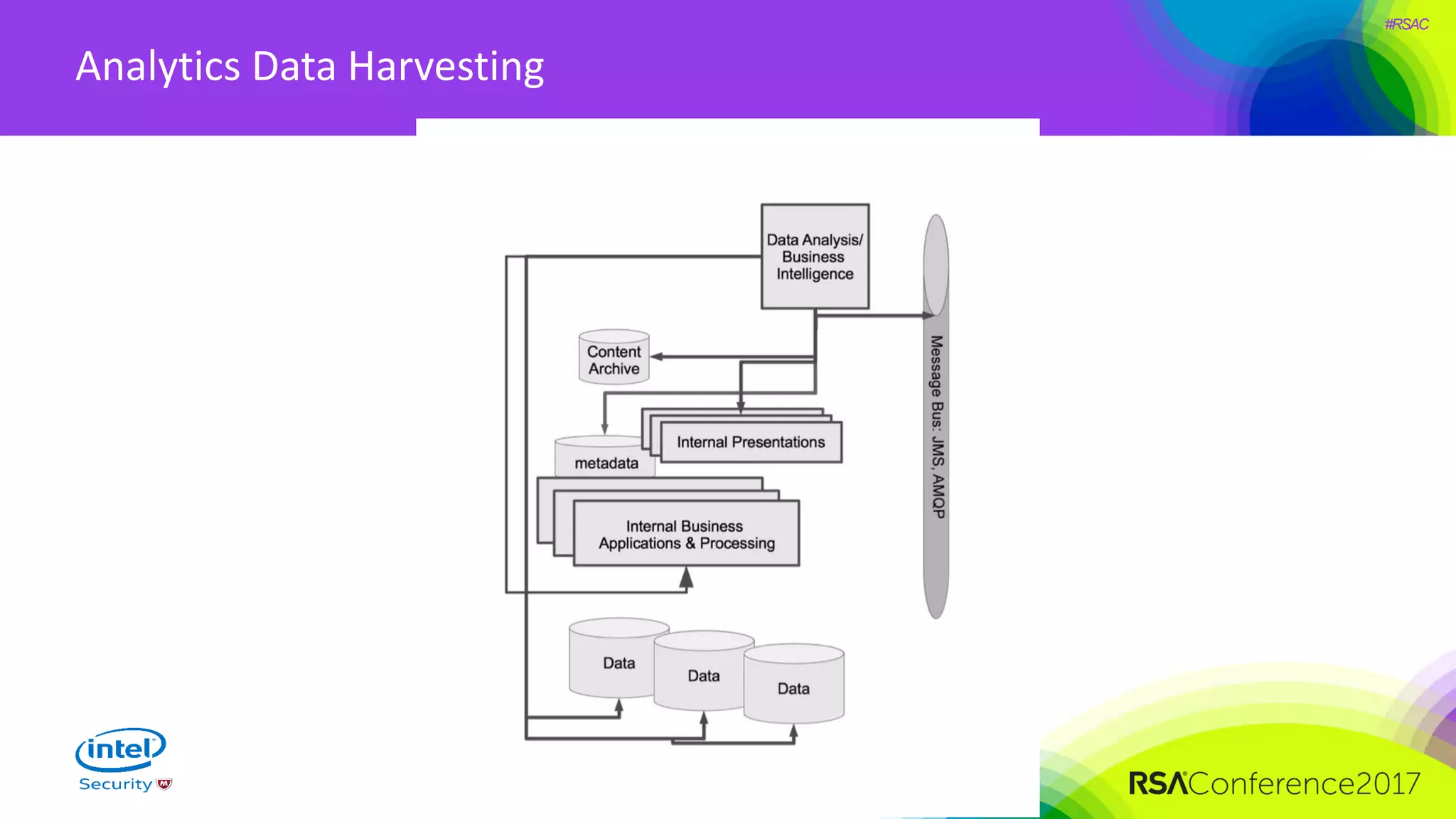
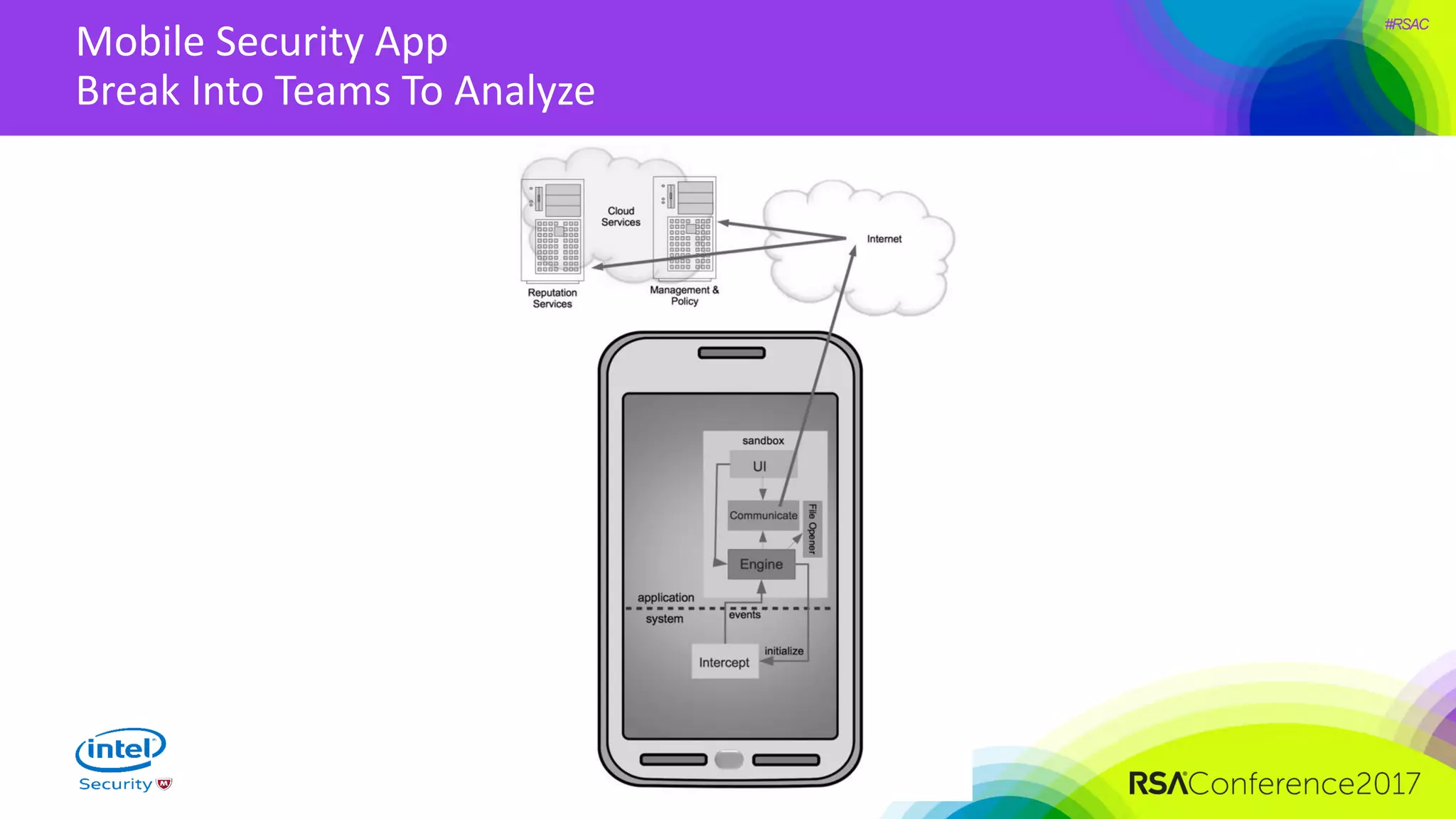
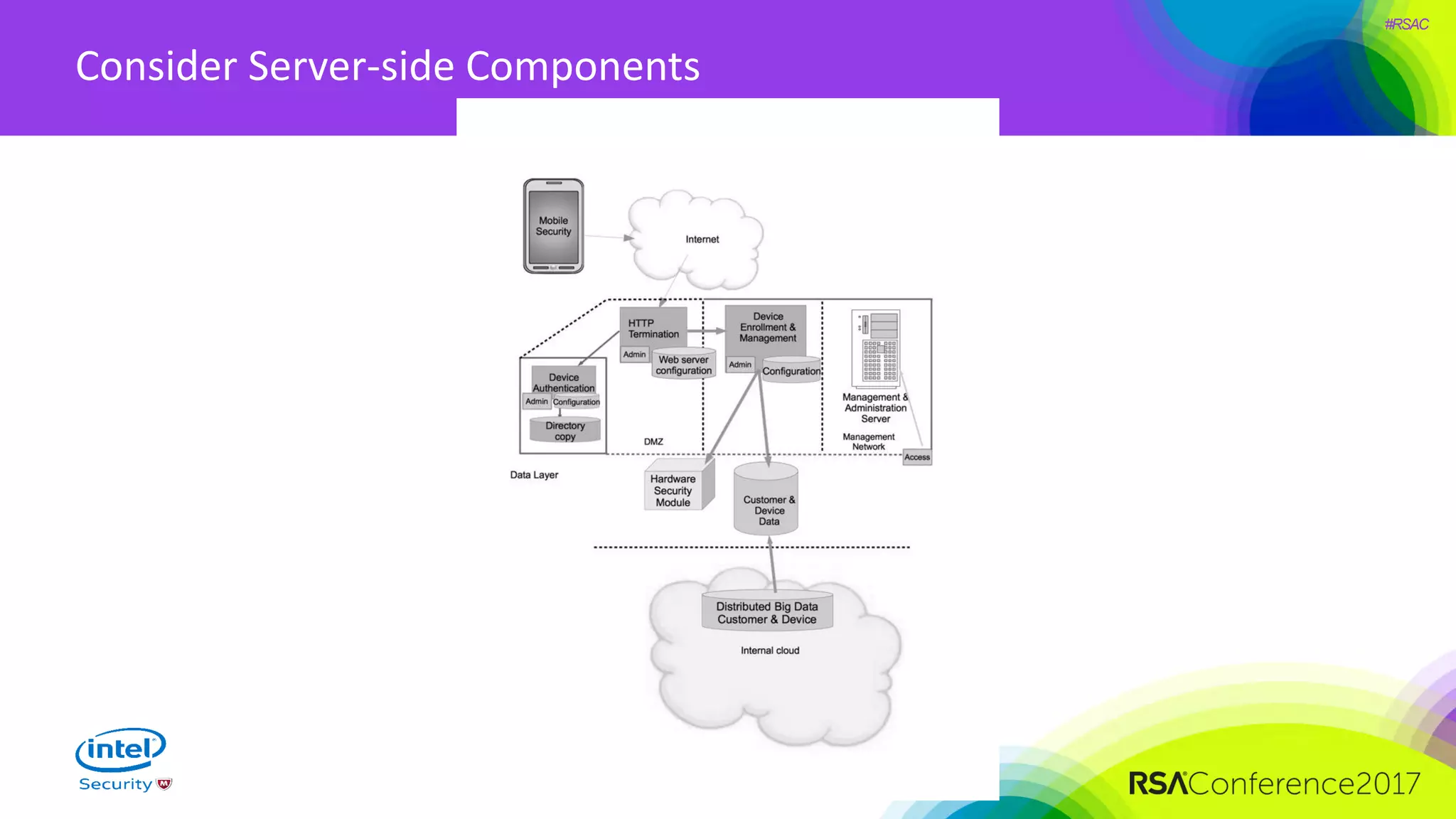
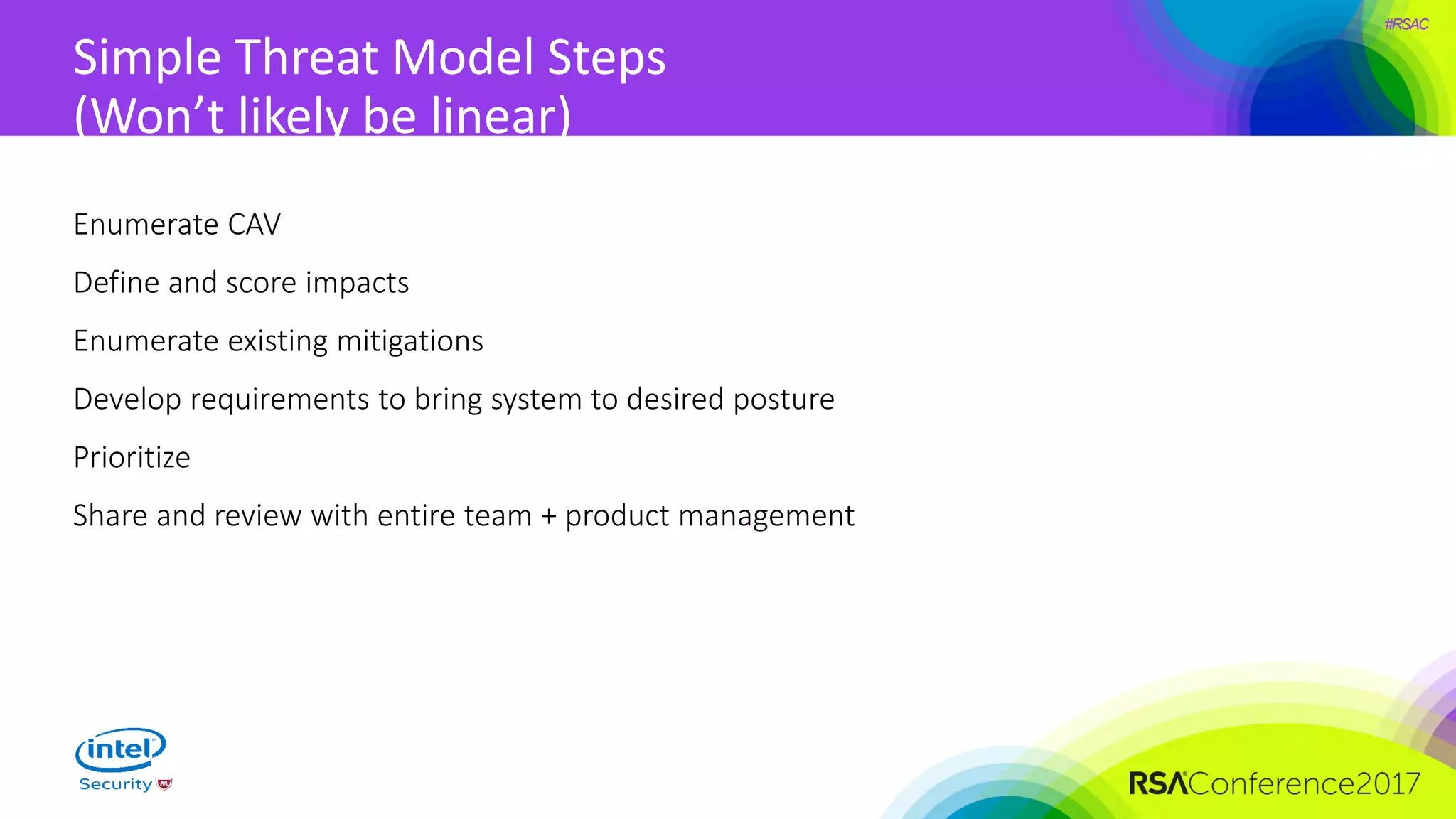
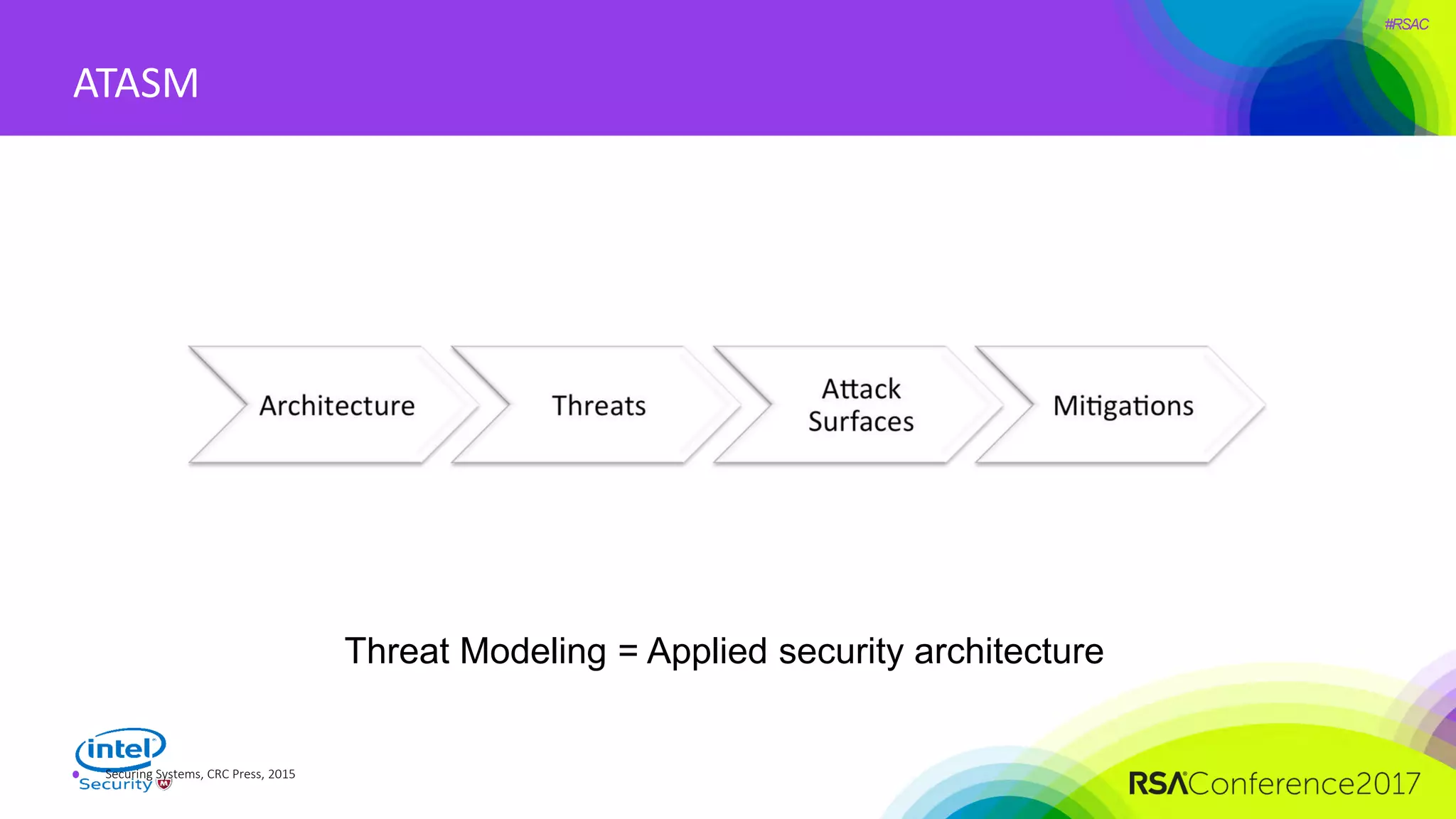
The document focuses on threat modeling as a crucial process in secure software design, emphasizing the need for collaborative involvement from the entire development team. It outlines the importance of understanding the threat landscape, assessing risks, and creating living documents that evolve with system architecture. Through structured analyses and methodologies, including the ATASM framework, the document guides practitioners in identifying security requirements to enhance system defenses against potential attacks.


























![#RSAC
"ISecG ESPT Security Test Plan Report”, April 14, 2014, by Eoin Carroll
Substeps
ISecG ESPT Security Test Plan Report [Product]
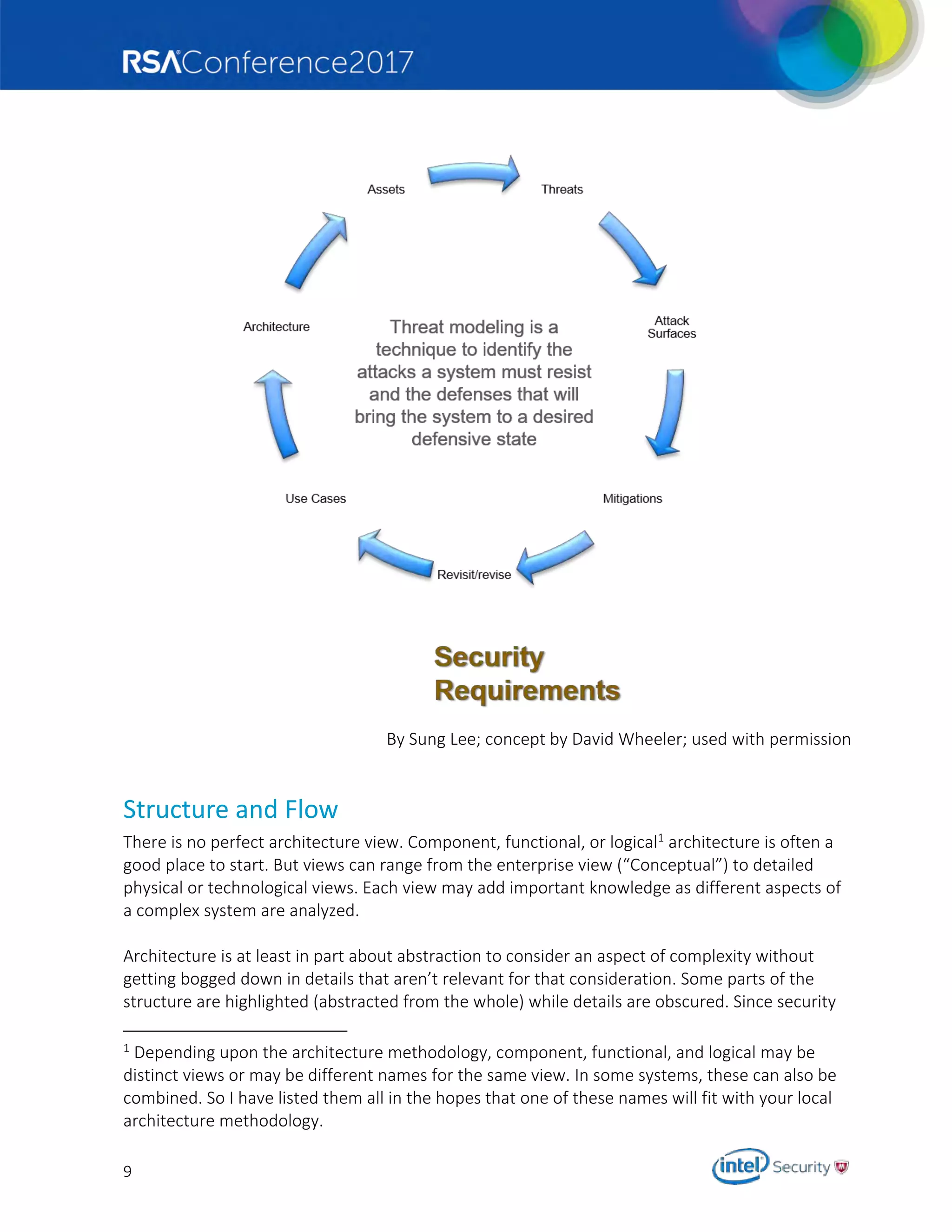
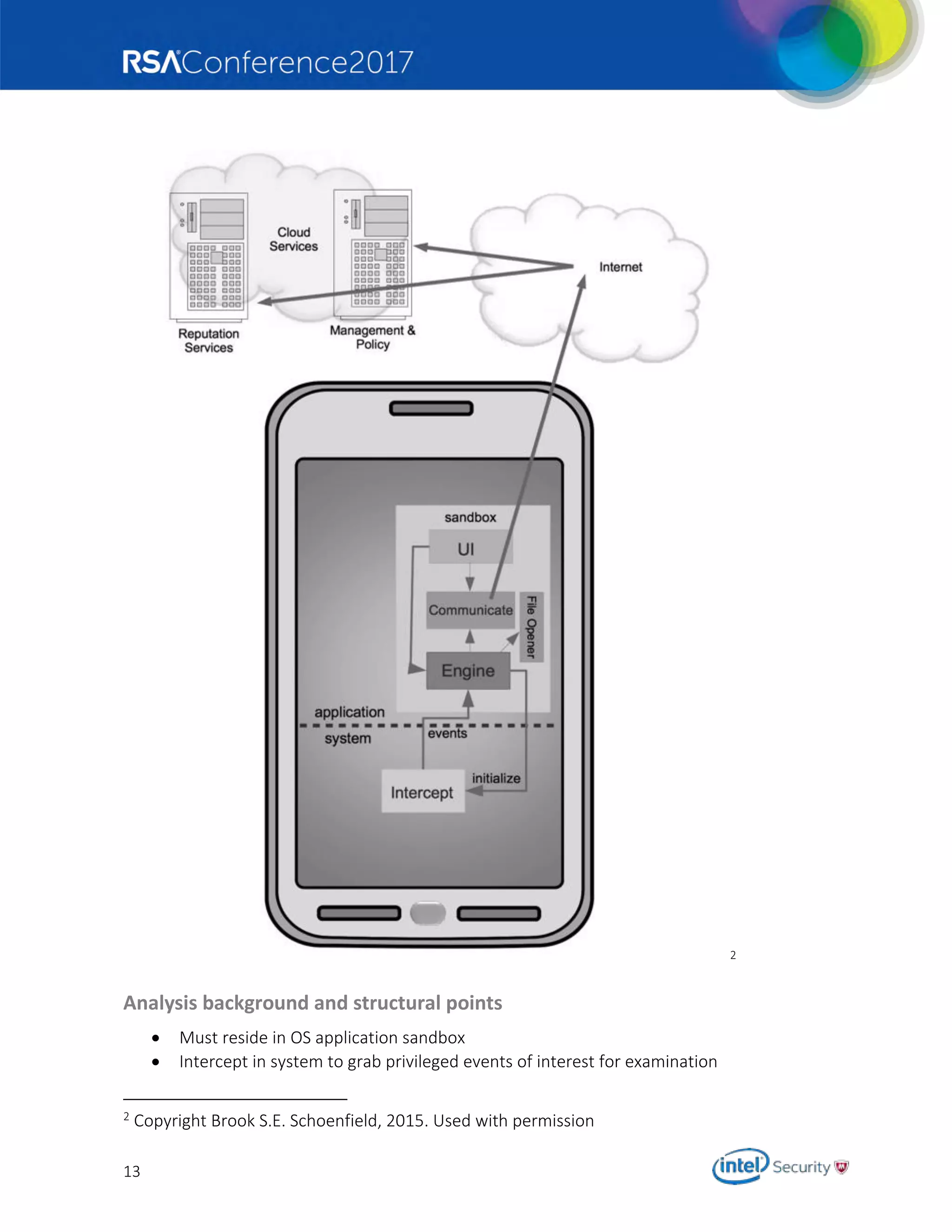
Architecture/Design Review
ATAM
Securing Systems: Applied Security Architecture and Threat Models, Brook S.E Schoenfield [2015]](https://image.slidesharecdn.com/lab3-w04lab3-w04threat-modeling-demystified-170420071317/75/Threat-modeling-demystified-50-2048.jpg)