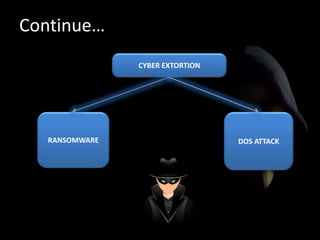
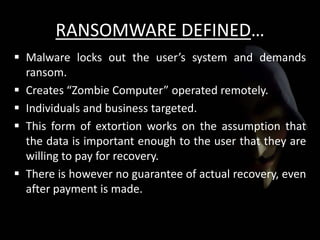
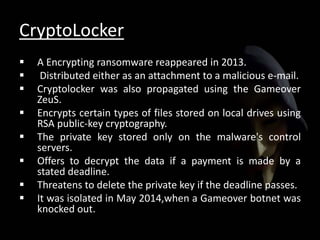
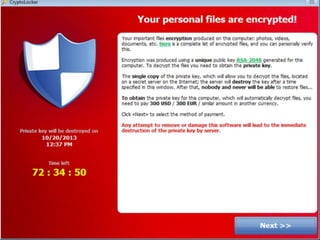
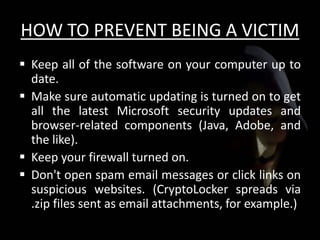
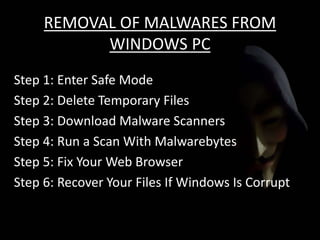
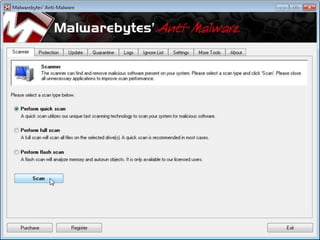
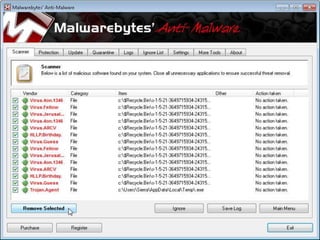
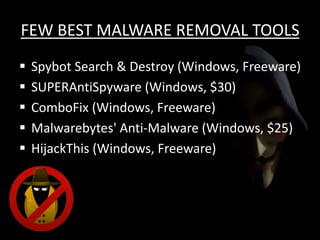
The document discusses cyber extortion, specifically ransomware, which is a form of malware that locks users out of their systems and demands a ransom for access. It outlines the history, types, famous examples of ransomware like Cryptolocker, and prevention strategies for individuals and businesses. The document emphasizes the importance of updating software and exercising caution to mitigate the risks of cyber extortion attacks.







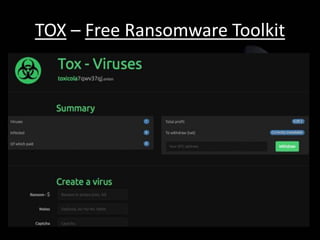
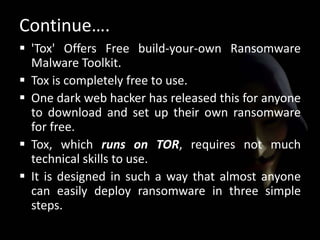
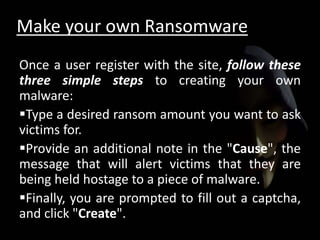
!["This process creates an executable of about 2MB that
is disguised as a .scr file.
Then the Tox [users] distribute and install as they see
fit. The Tox site (runs on the TOR network) will track the
installs and profit. To withdraw funds, you need only
supply a receiving Bitcoin address.“
- McAfee explains..](https://image.slidesharecdn.com/ransomware-150912183645-lva1-app6891/85/Ransomware-26-320.jpg)