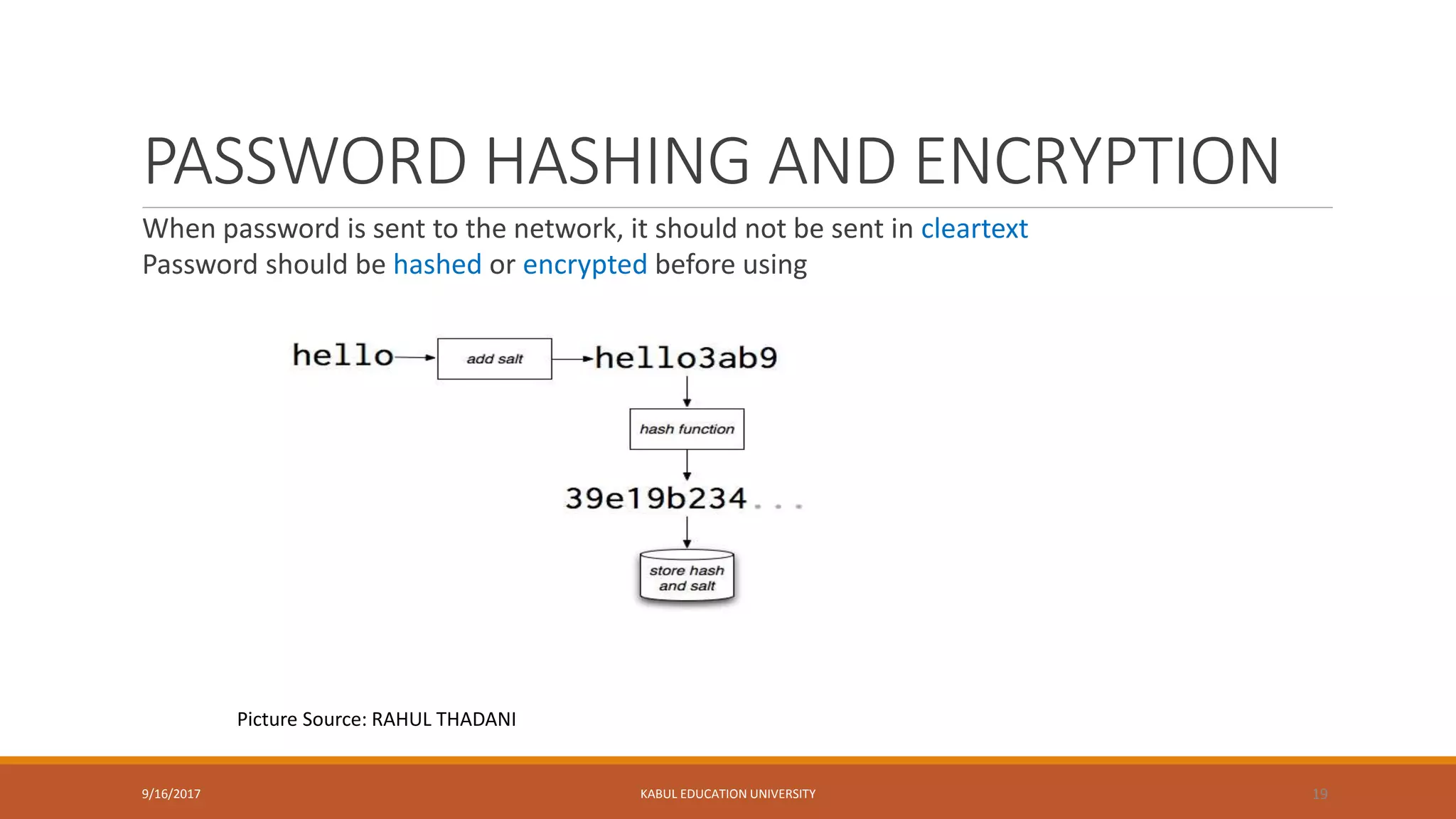
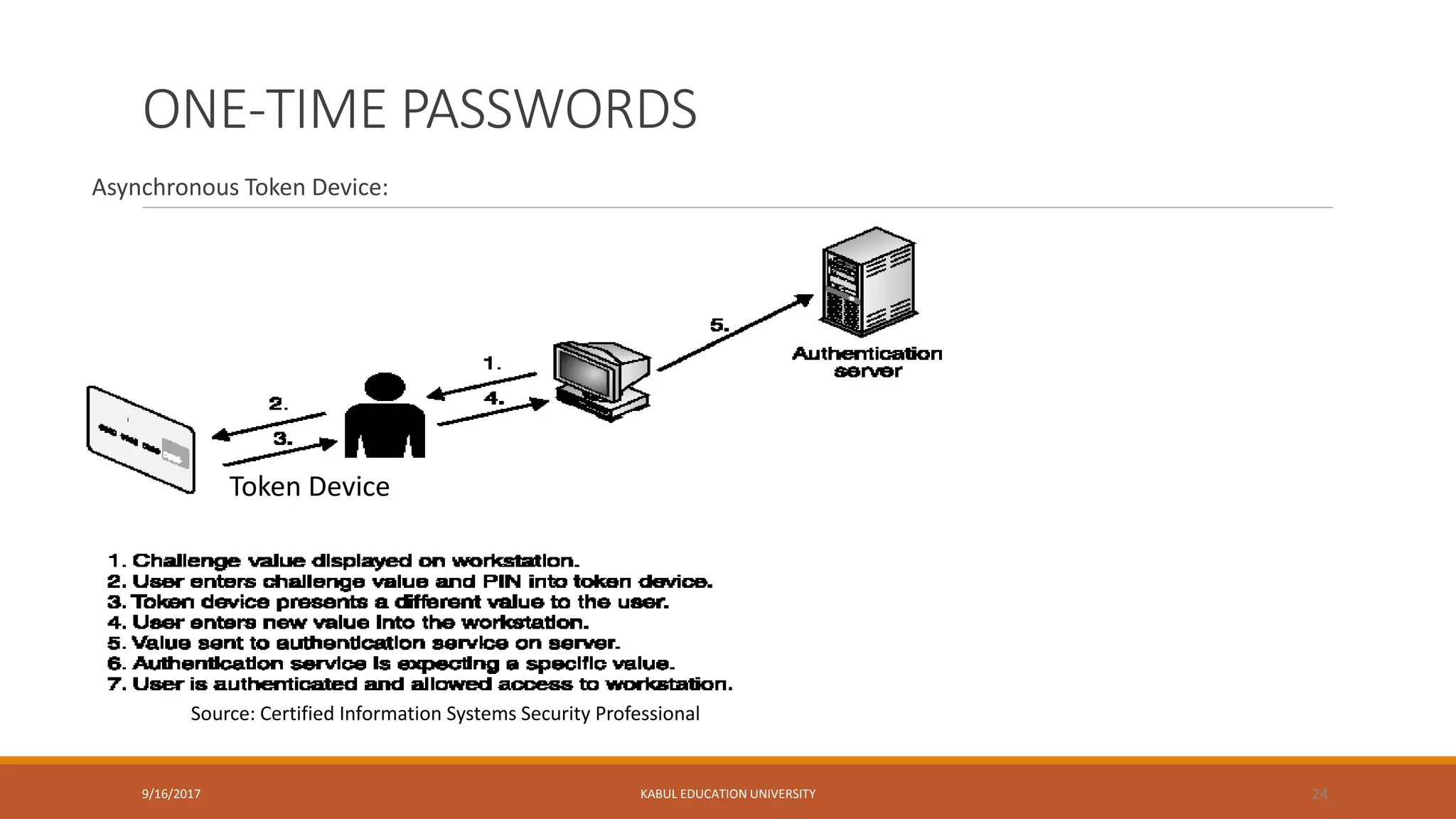
This document outlines a lecture on network security. It discusses key topics like authentication, access control, identification, authorization, and password management. It provides details on security concerns, password hashing and encryption, one-time passwords using token devices, and using cryptographic keys. The document also outlines the class policy, grading evaluation, and course schedule for the network security course.