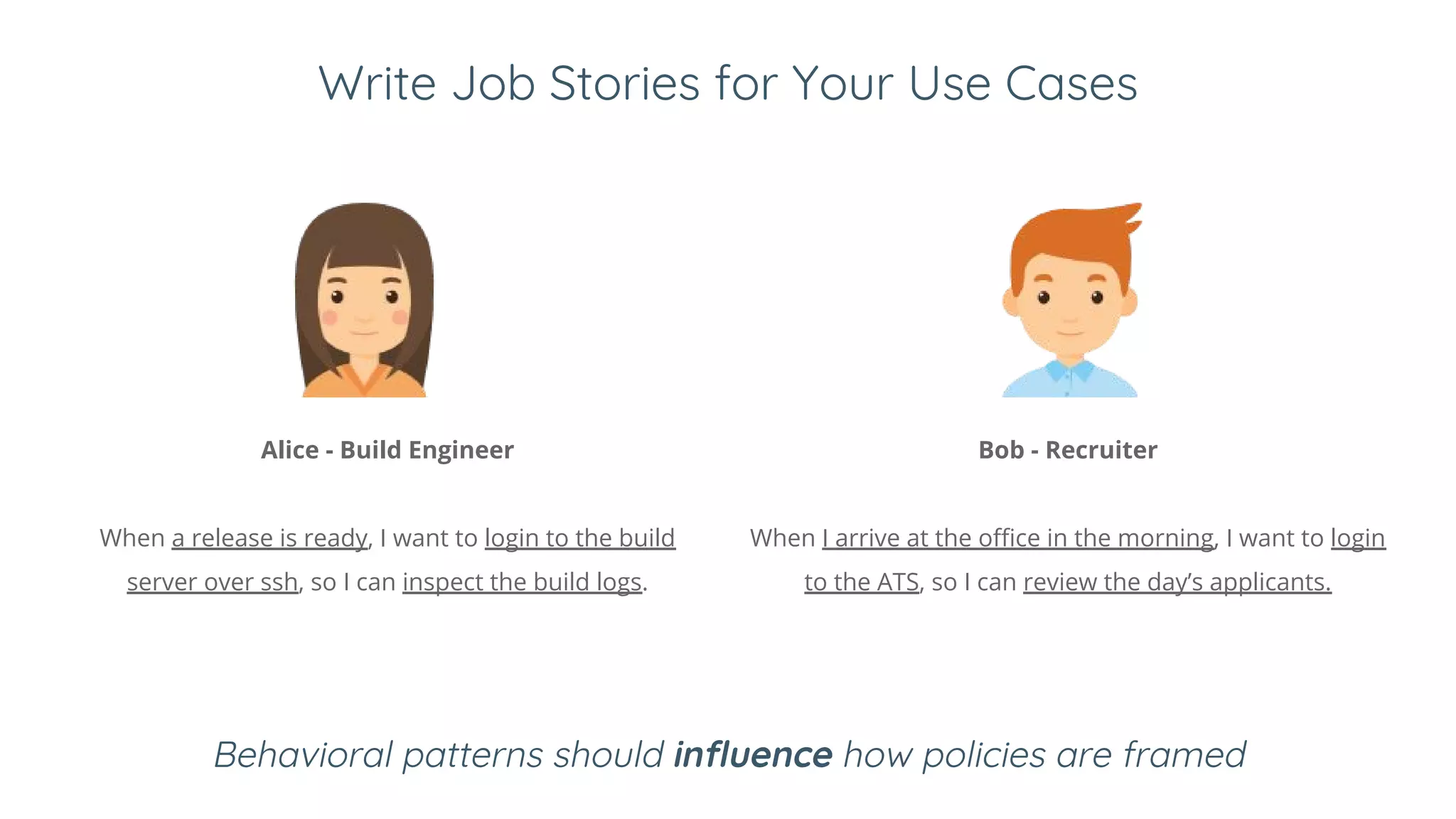
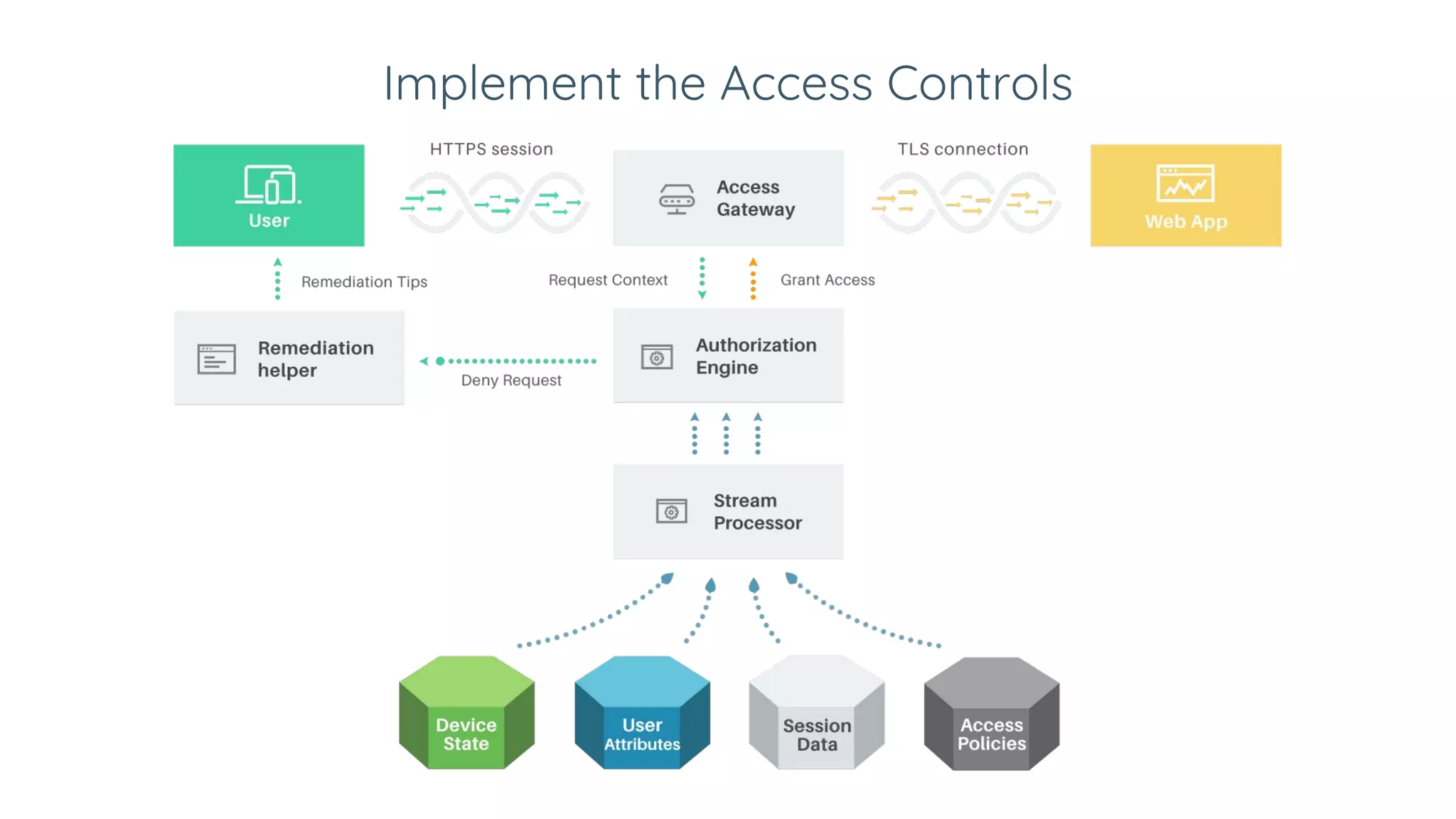
Ivan Dwyer presented on Google's BeyondCorp approach to access management. BeyondCorp moves away from traditional VPN access and instead bases access decisions on multiple factors including who the user is, what device they are using, and the current state of that device. This zero-trust approach grants dynamic, short-lived credentials and makes access decisions in real-time based on over a dozen attributes of the user and device. Implementing BeyondCorp involves taking inventories of users, devices, resources and credentials; defining access policies and trust tiers; and implementing technical controls to enforce the new dynamic, context-aware access model.