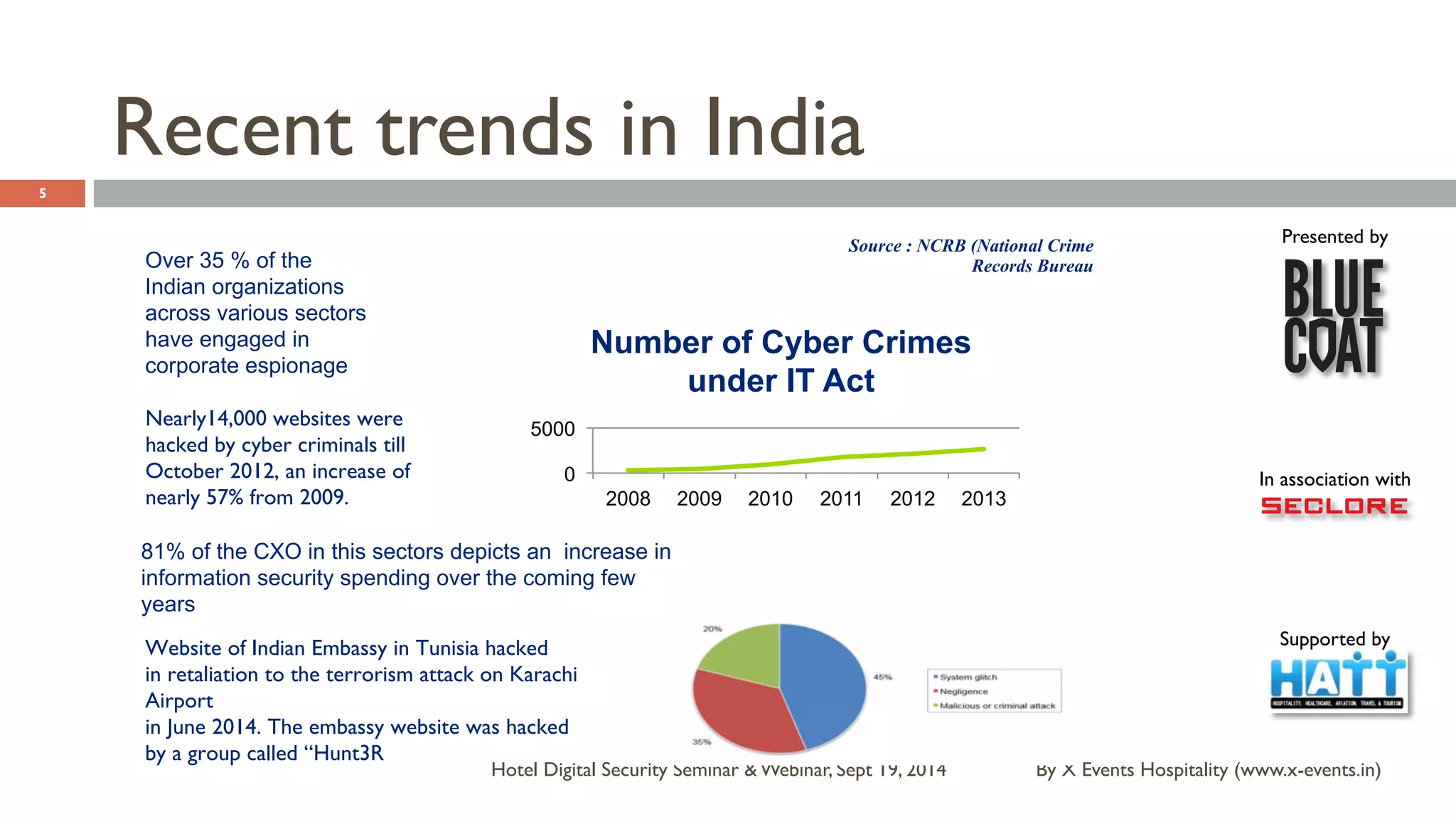
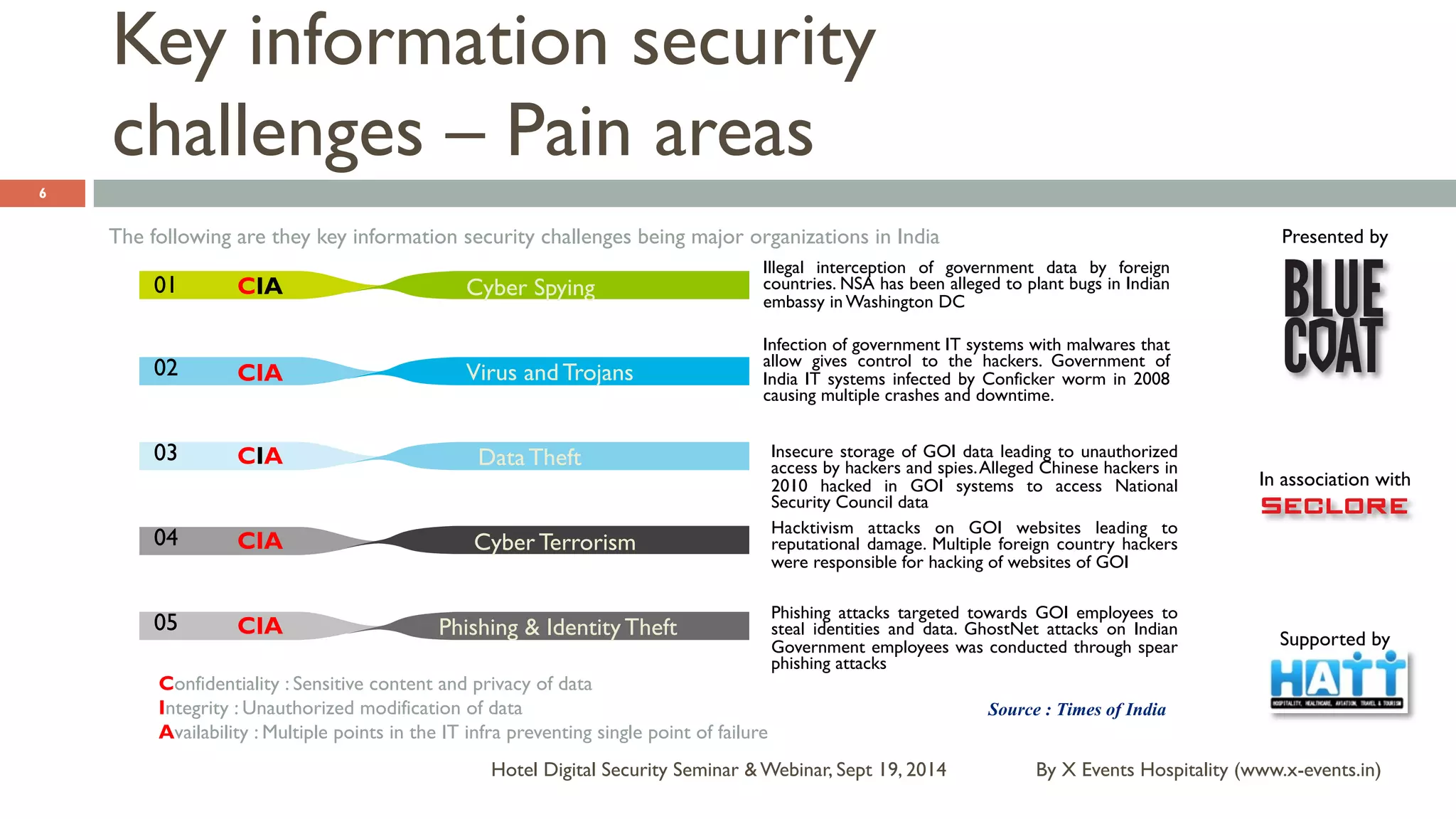
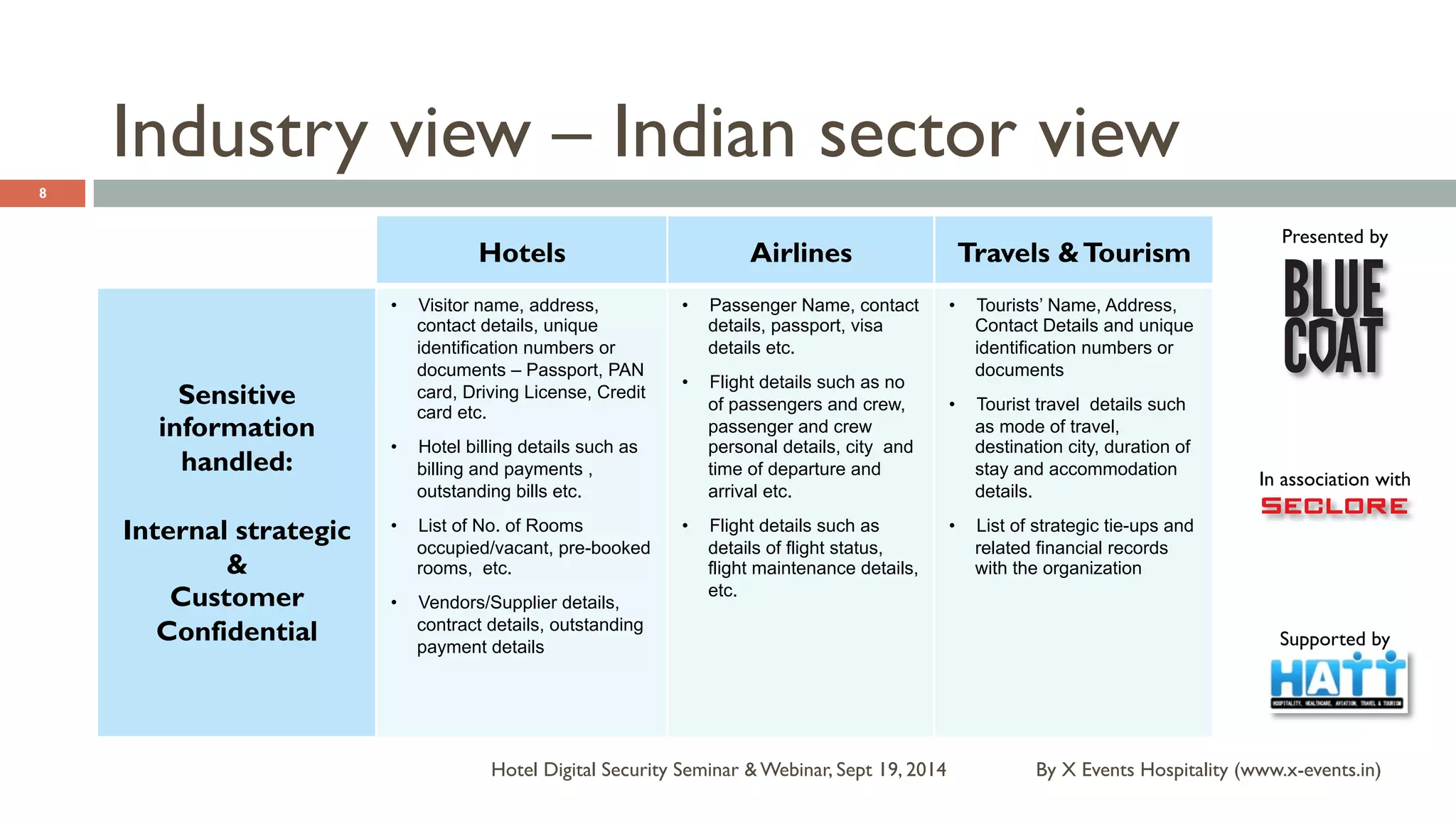
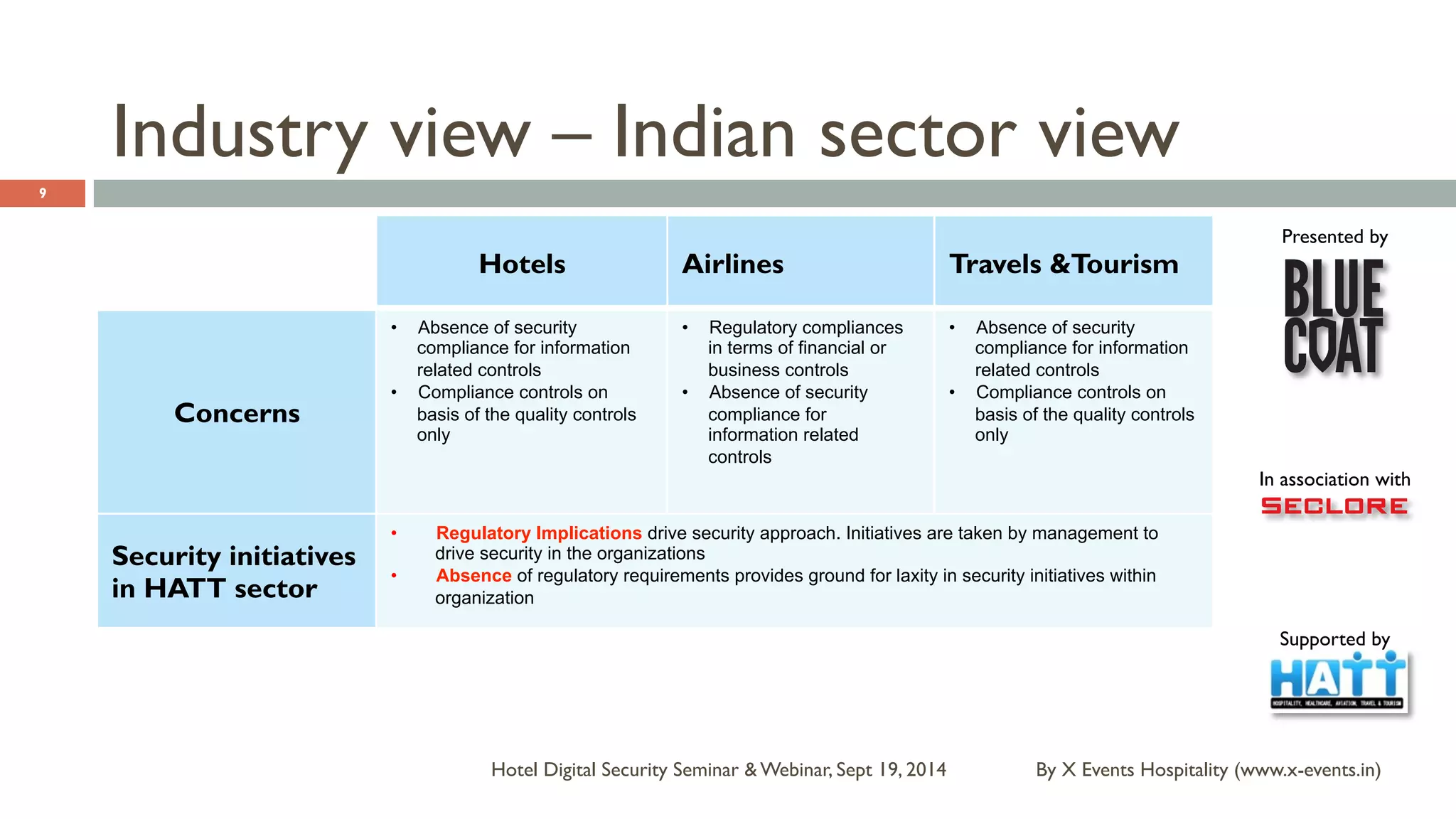
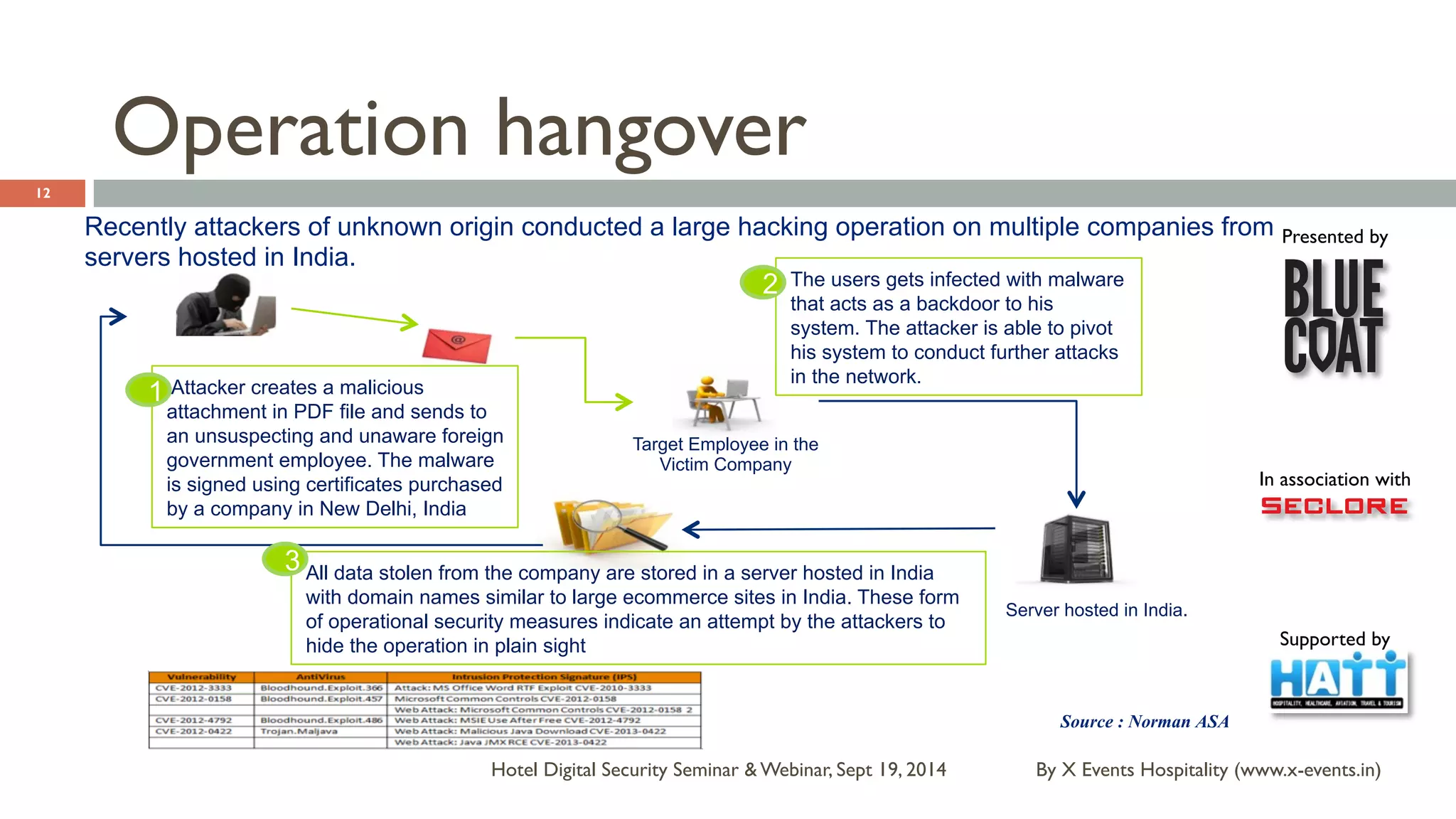
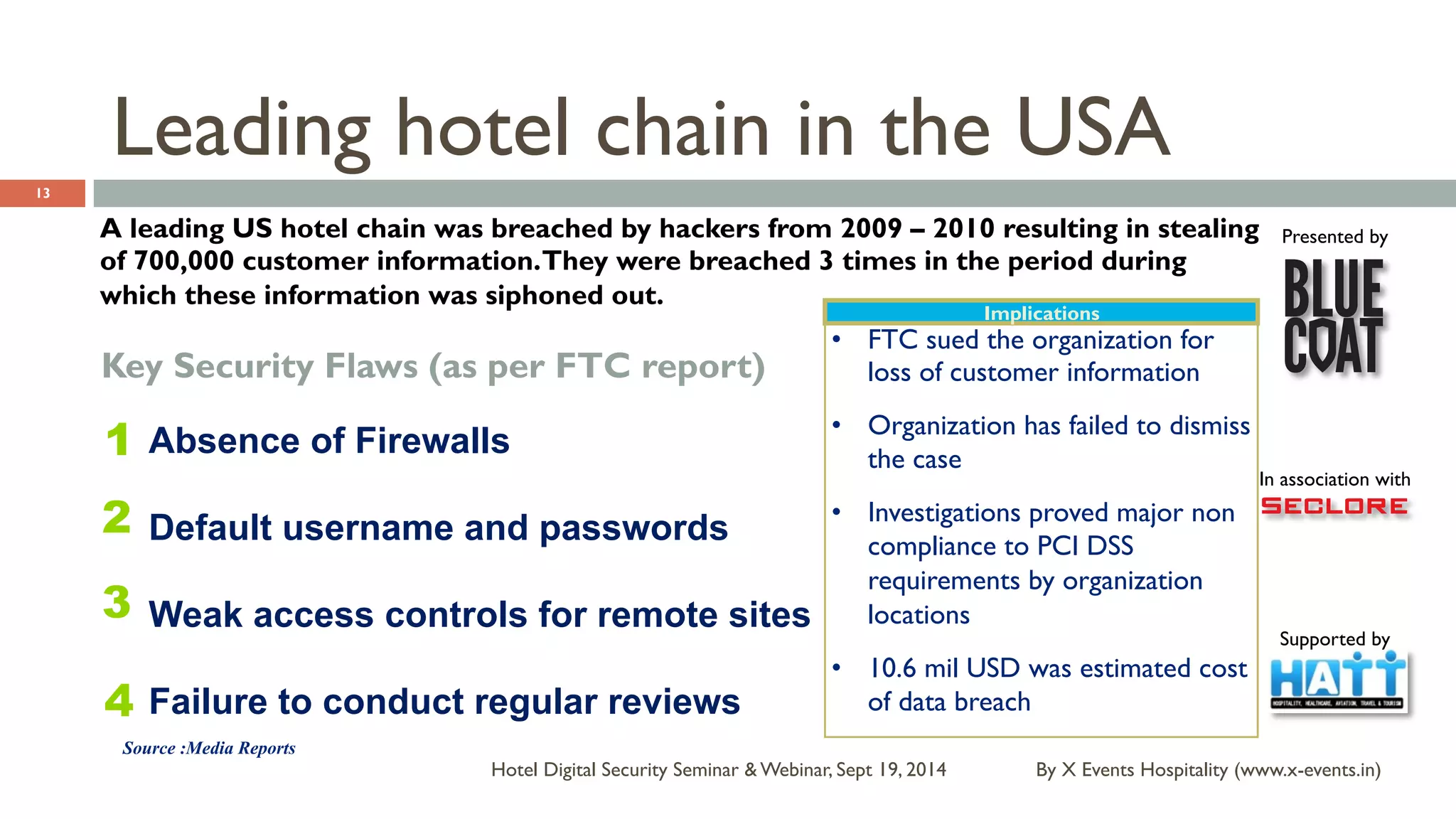
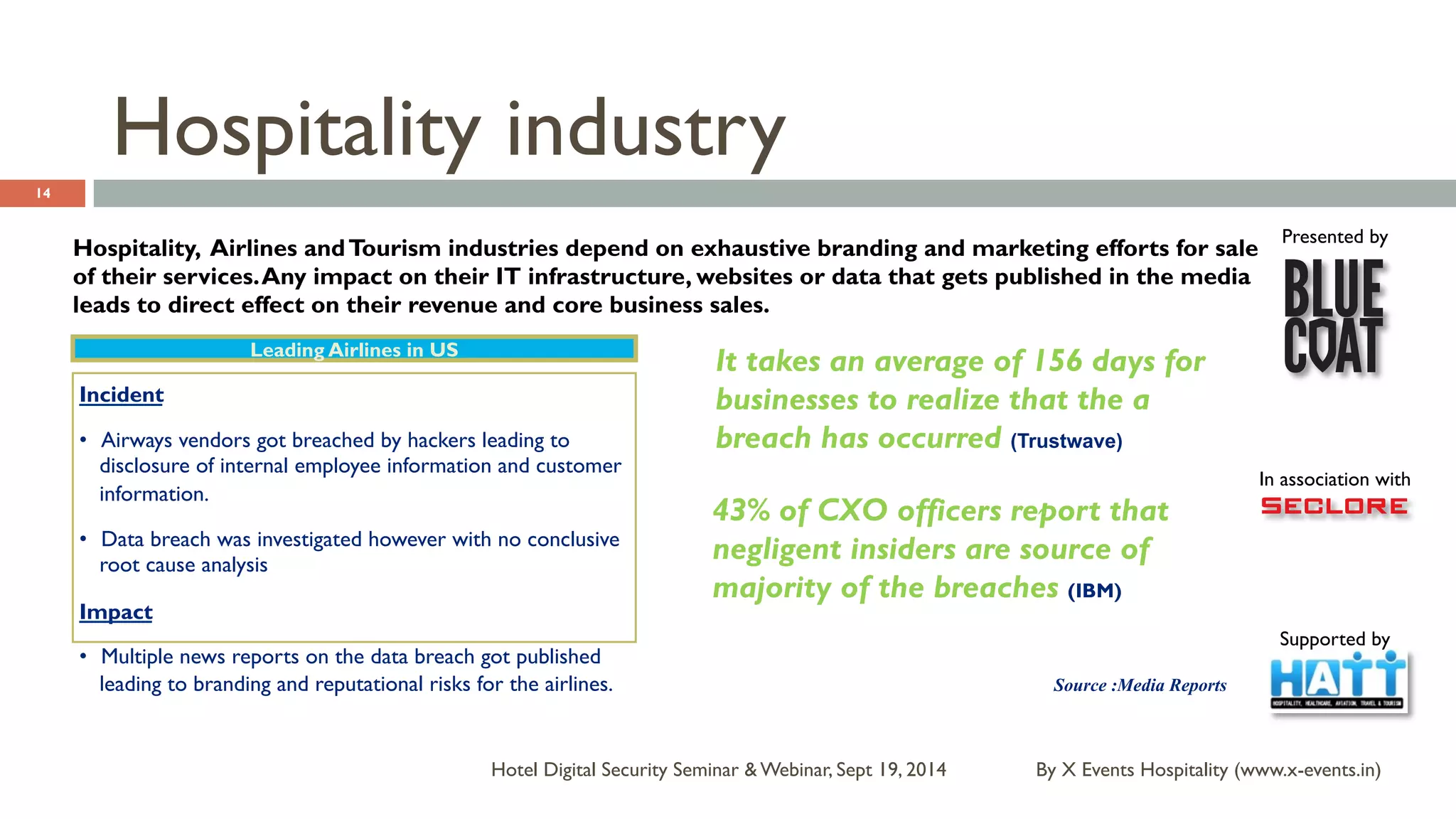
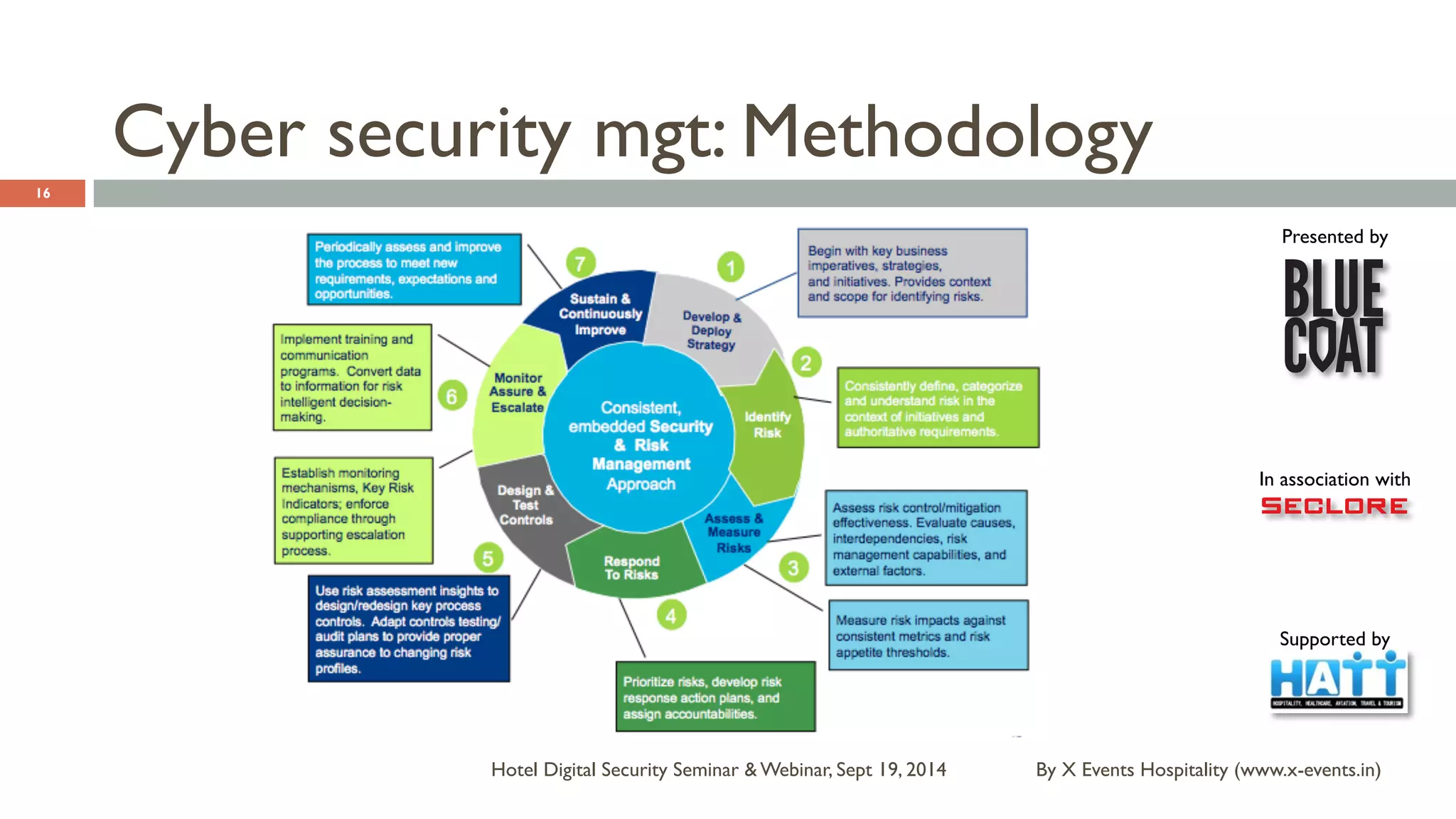
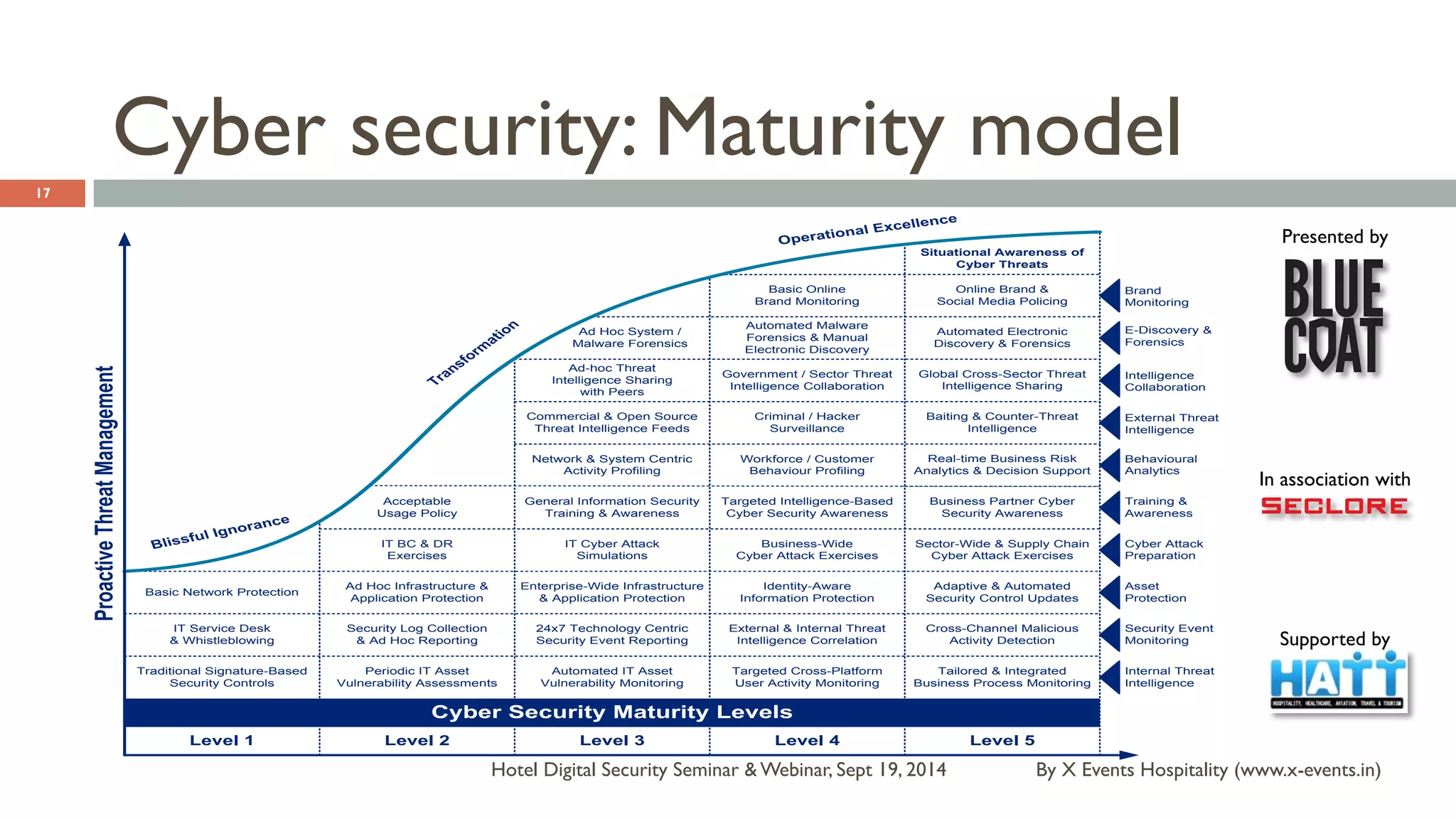
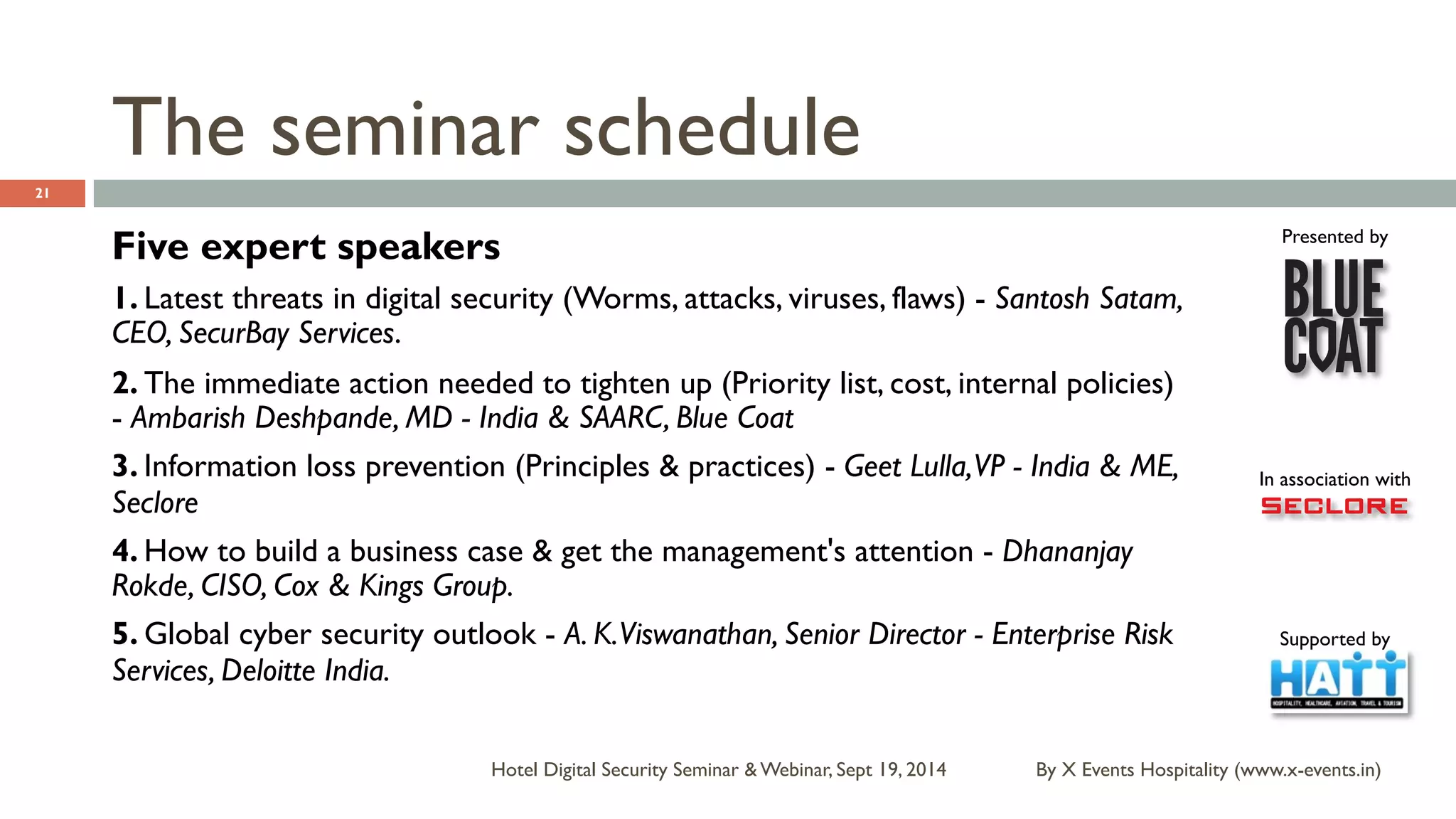
The document discusses the Hotel Digital Security Seminar held on September 19, 2014, highlighting critical cyber security challenges faced by organizations in India, particularly in the hospitality sector. It outlines trends in corporate espionage, the rise of cyber attacks, and emphasizes the importance of building robust cyber security strategies to protect sensitive information. Additionally, it underscores the need for compliance and proactive measures to mitigate risks associated with modern cyber threats.