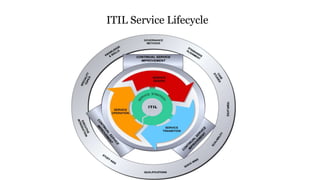
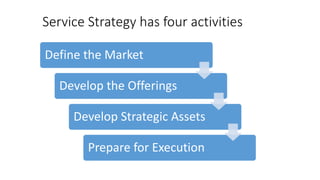
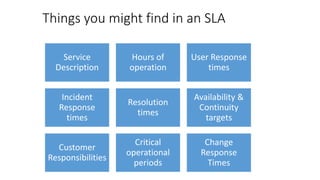
This document provides an overview of ITIL (Information Technology Infrastructure Library) service lifecycle concepts. It discusses the purpose and key activities of Service Strategy, which includes defining the market, developing offerings, strategic assets, and preparing for execution. Service Design processes like availability management and service level management are also summarized. The document explains concepts like service portfolios, service level agreements, capacity management, and ensuring the right IT resources are provided at the right time for the right cost.