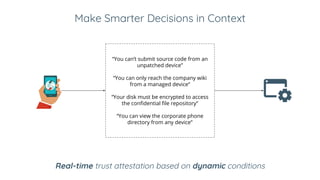
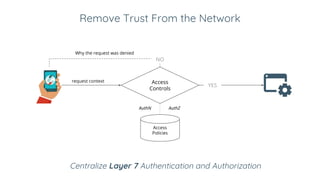
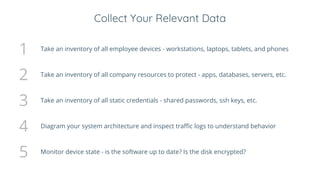
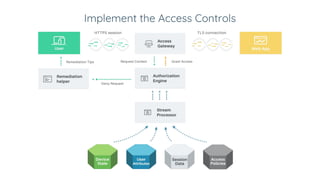
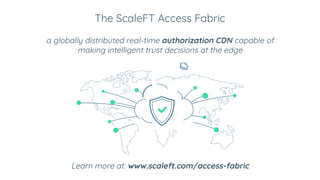
BeyondCorp is Google's zero trust architecture that allows employees to work from untrusted networks without using a VPN. It automates good security practices by making access decisions based on who the user is, what device they're on, and other dynamic factors. This eliminates issues like shared credentials and unpatched devices accessing resources. The key aspects of BeyondCorp are removing network trust, using short-lived credentials, and centralizing authentication and authorization based on real-time trust evaluations of users and their devices. The presentation provides recommendations for organizations to implement their own zero trust architecture, such as taking an inventory, understanding use cases, defining policy frameworks, and starting with simple access controls before getting more granular.