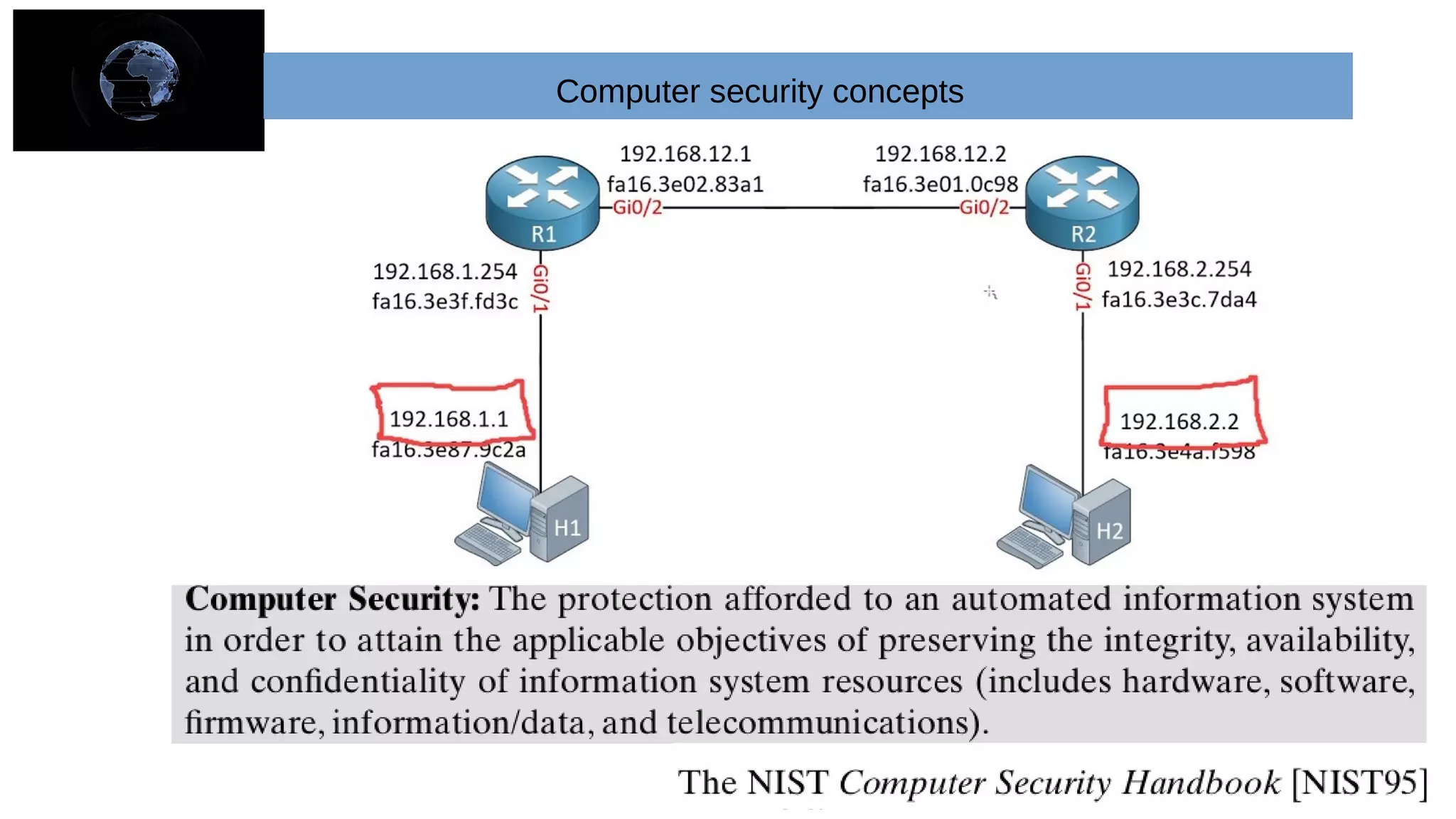
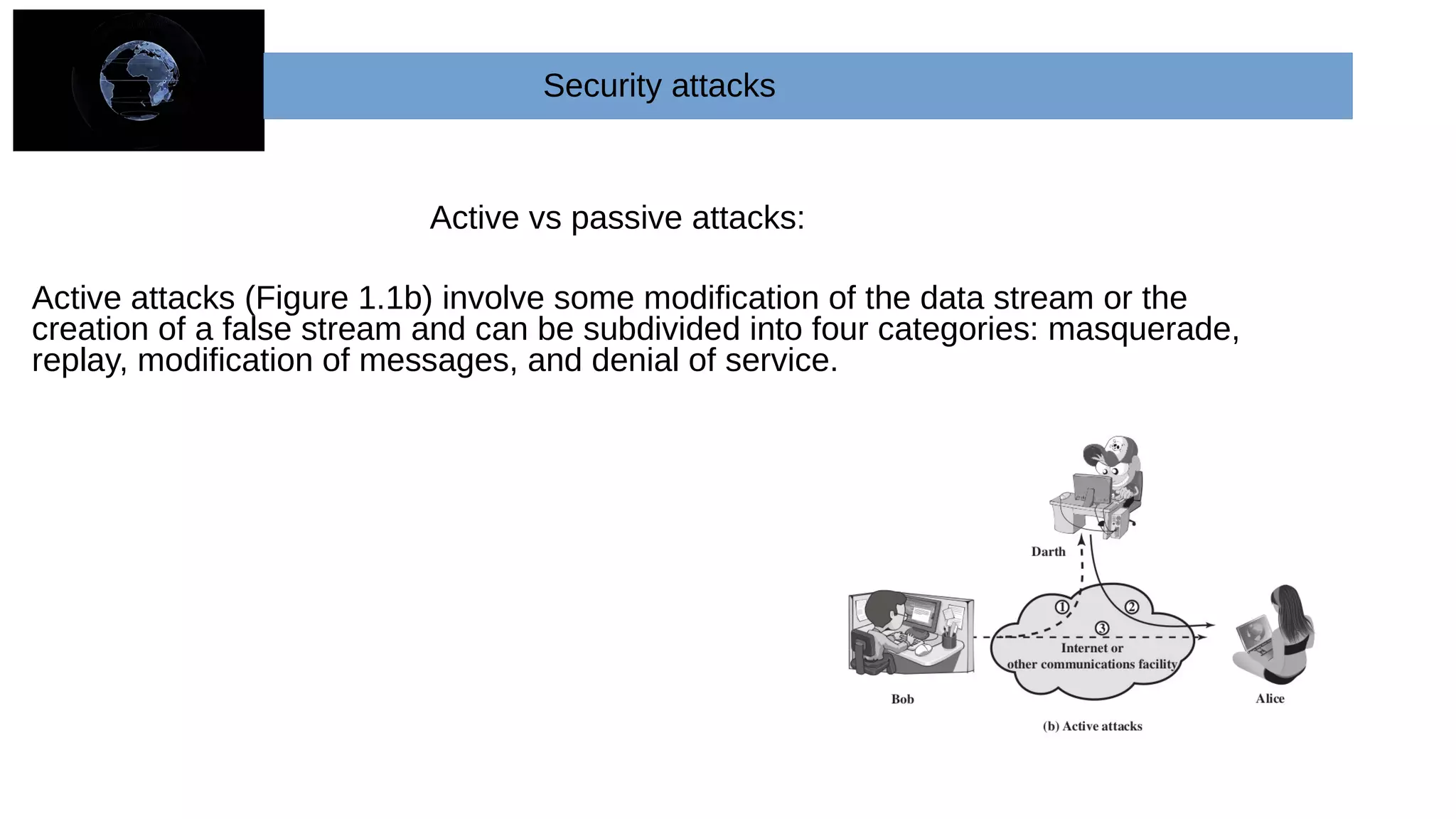
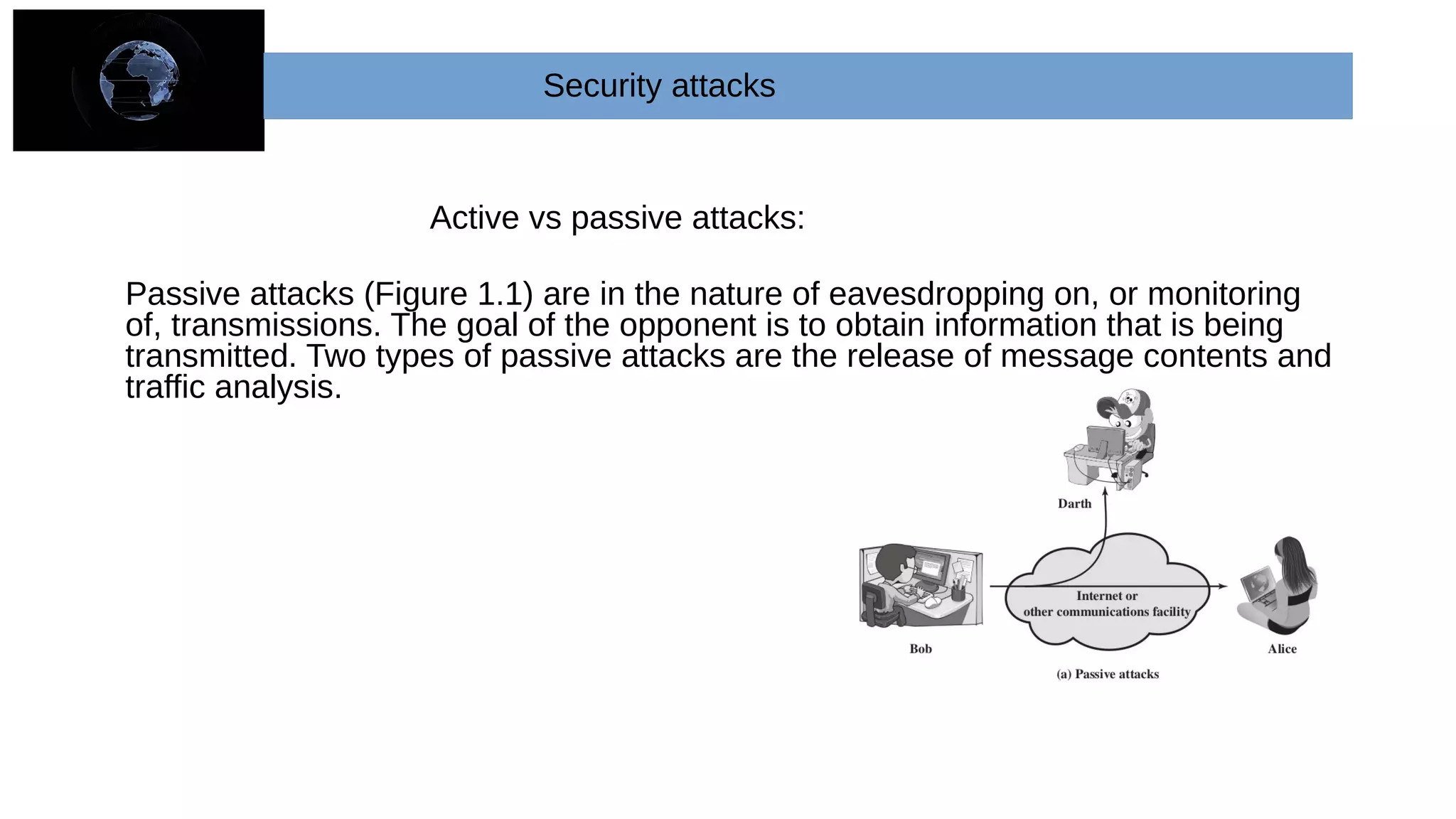
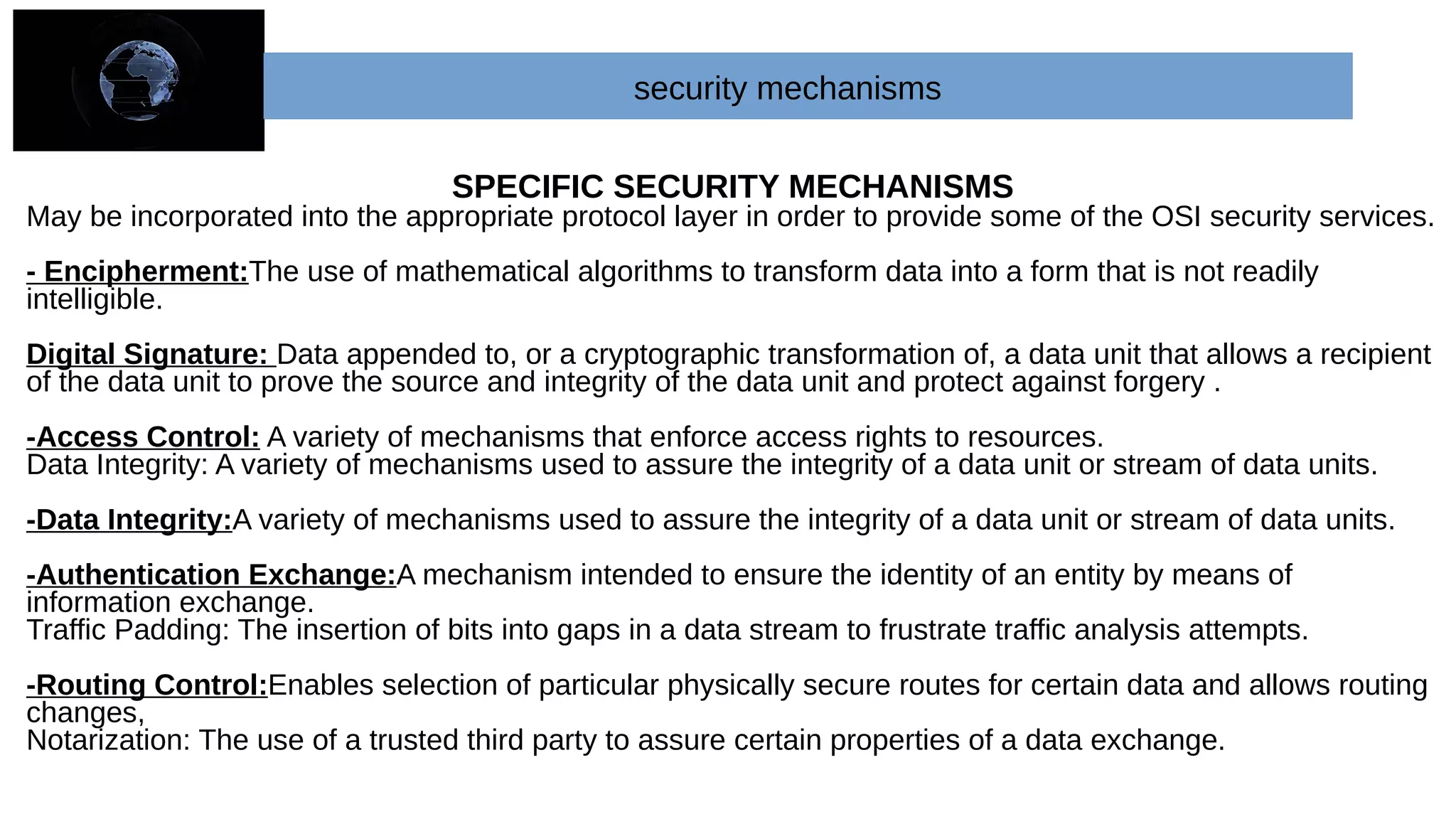
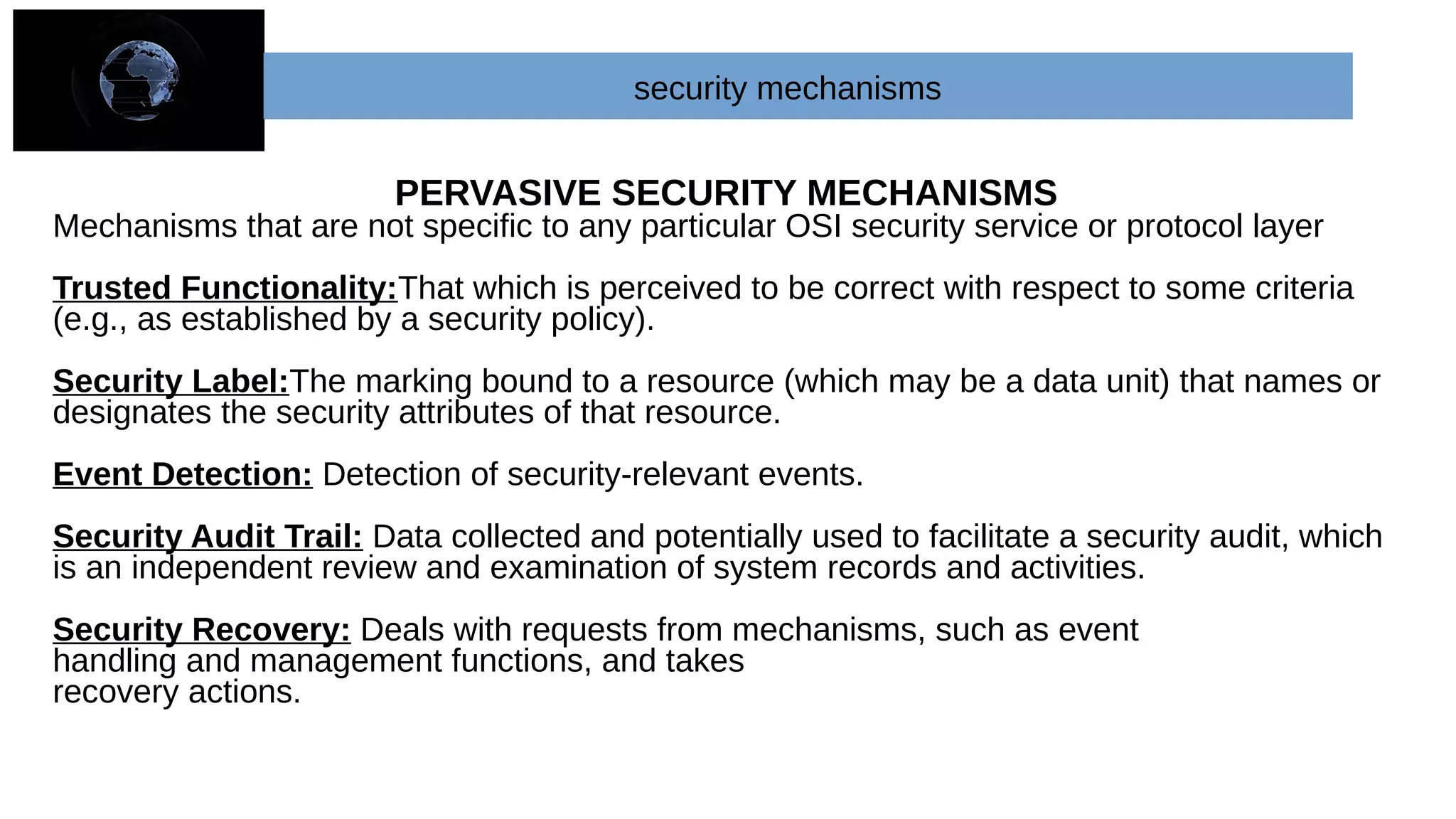
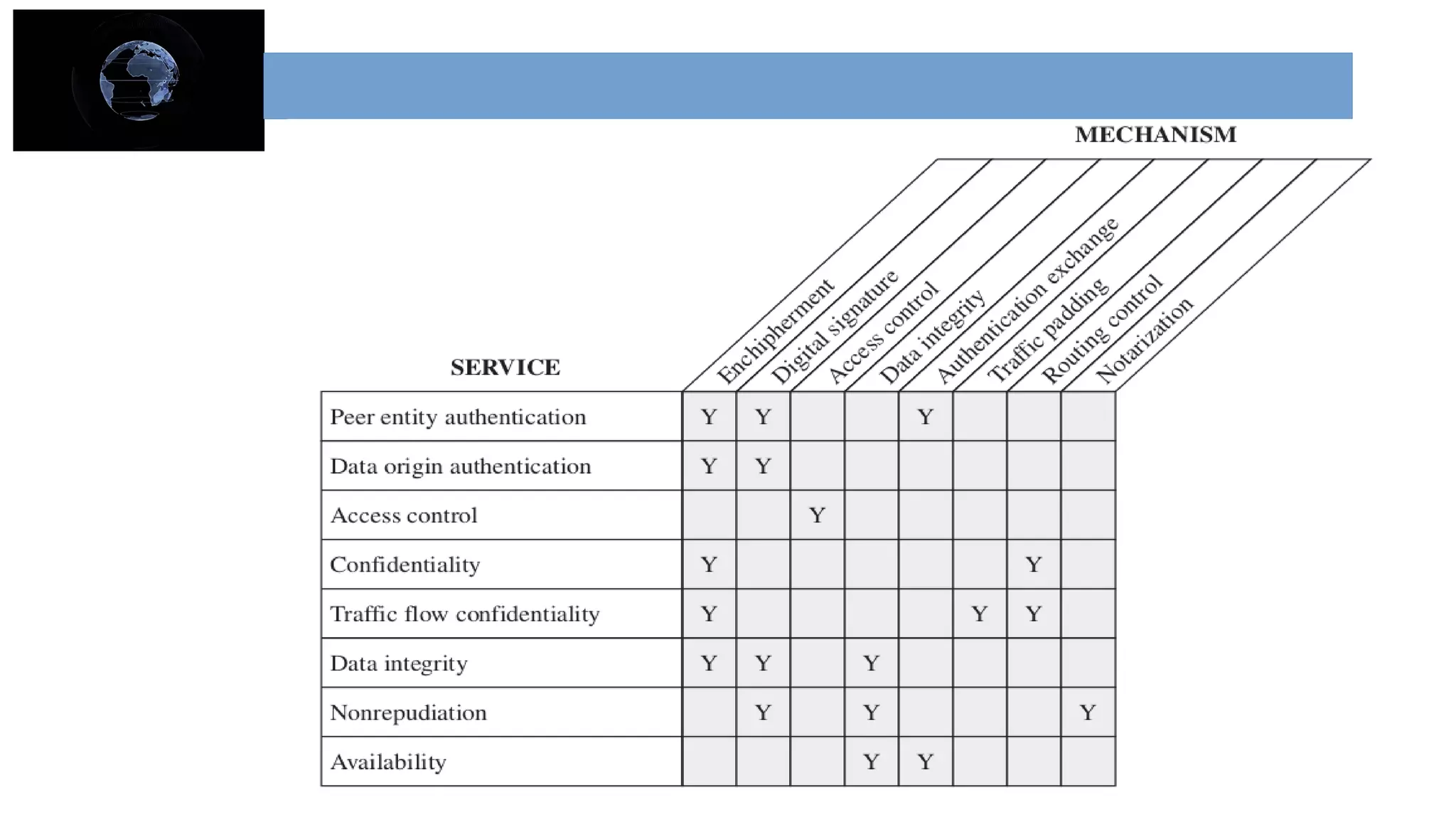
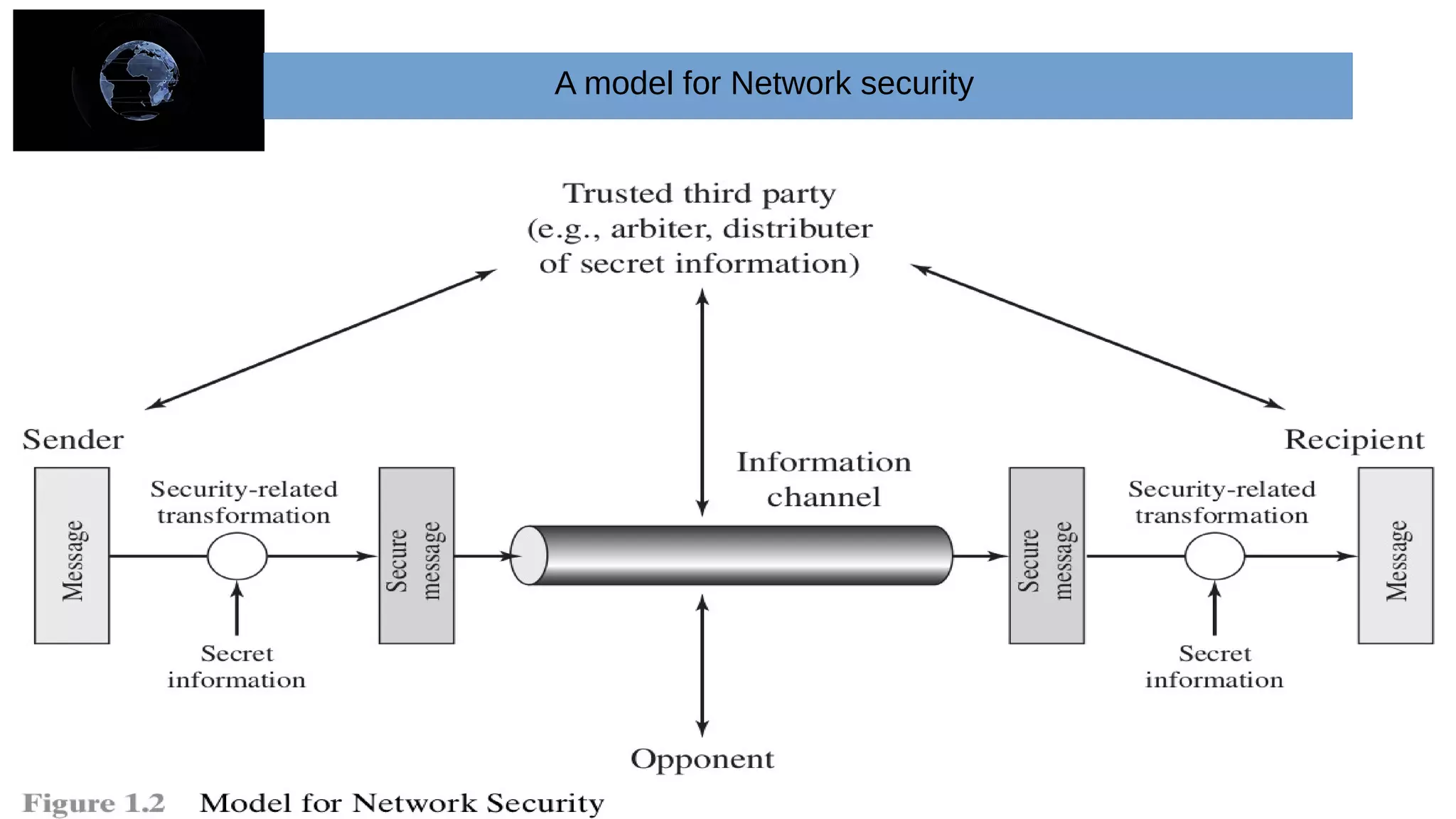
The document provides an overview of cryptography and network security concepts. It describes the key objectives of studying this topic as understanding security requirements like confidentiality, integrity, and availability. It also discusses types of security threats and attacks. The document summarizes the main cryptographic algorithms and security architecture. It defines security services like authentication, access control, data confidentiality, and data integrity. It also discusses security mechanisms, threats, and attacks in network security.