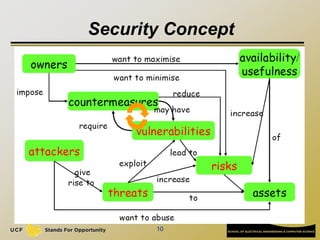
The document discusses software security, detailing its role in both providing and undermining security through various principles, methods, and technologies. It highlights key security concepts such as confidentiality, integrity, and availability (CIA), and emphasizes the importance of understanding threats, stakeholder interests, and implementing robust countermeasures. Furthermore, it illustrates potential vulnerabilities in software development and infrastructure, alongside typical threats faced in systems like email.