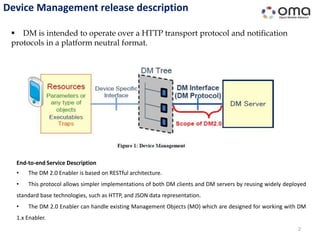
The document outlines requirements for an updated Device Management (DM) enabler. It specifies that the DM 2.0 enabler will:
1) Be based on a RESTful architecture using HTTP and JSON to allow simpler client and server implementations.
2) Support existing Management Objects (MO) designed for the DM 1.x enabler.
3) Specify mechanisms for authentication, authorization, integrity and confidentiality to ensure secure communication between DM clients, servers, and data repositories.