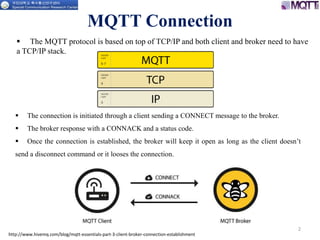
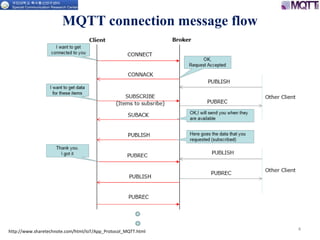
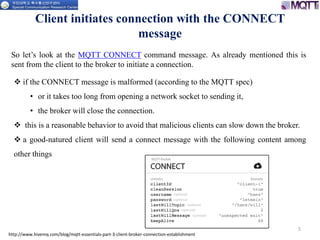
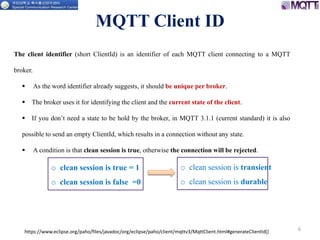
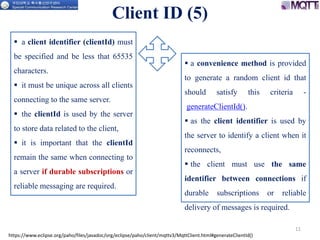
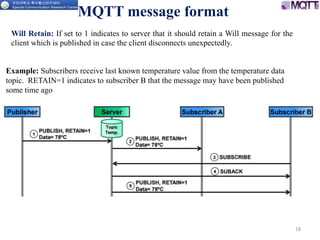
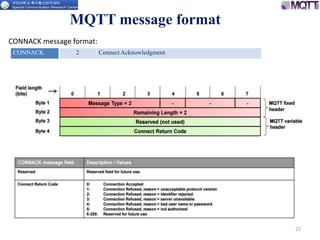
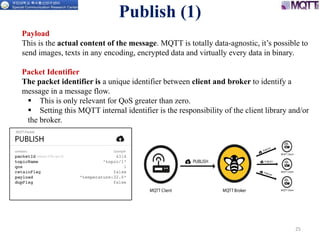
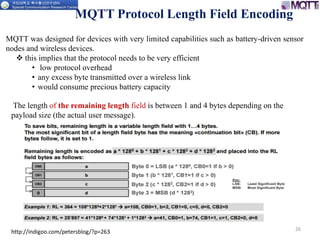
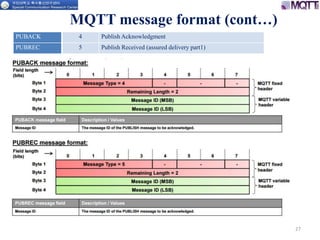
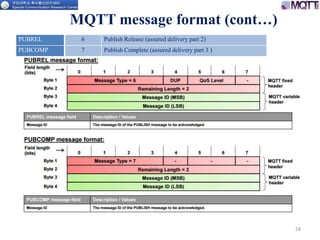
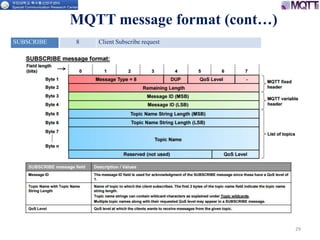
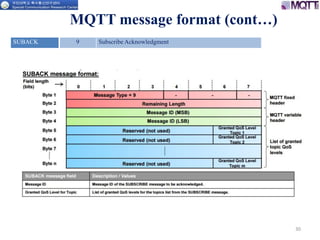
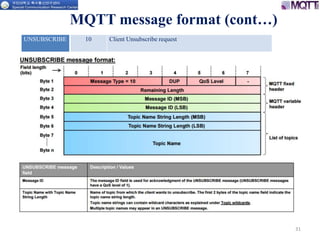
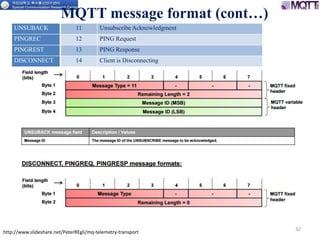
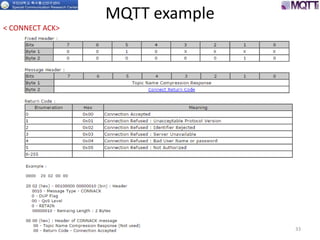
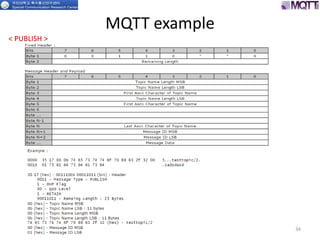
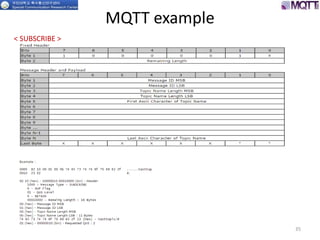
The document discusses the MQTT protocol, focusing on the message format, connection establishment, client identification, and security features. It outlines how MQTT clients communicate with brokers, the importance of unique client identifiers, and the role of clean sessions in message delivery. Additionally, it addresses authentication methods and features like the Last Will and Testament and keep-alive mechanisms for maintaining connections.